IT (Amendment) Act, 2008, 69B Rules: Draft and Final Version Comparison
 |
|---|
 |
 |
 |
 |
 |
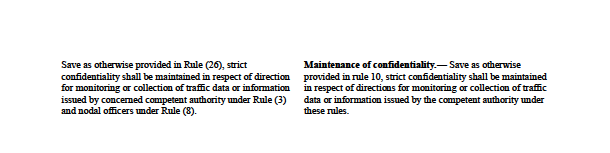 |
There has been a considerable amount of re-arrangement and re-structuring of the various clauses between the 69B Draft Rules and the official Rules, as can be seen in the comparison chart, but very little content has been changed. The majority of the changes made to the official Rules are changes in wording and language that serve to provide some much-needed clarification to the Draft Rules (see the differences between Clause (9) of the Draft Rules and sub-section (4) of Clause (3) of the official Rules as an example). Language redundancies, as well as full clauses (Clause [6] of the Draft Rules) have been thankfully removed in the official Rules.
Aside from the addition of four definitions, including a definition for a “security policy”, a phrase which appears in the Draft Rules without being defined, Clause (2) contains what is most likely one of the more noteable changes between the two definitions: under sub-section (g) in the 69 Rules, the words “or unauthorised use” have been added to the definition of “cyber security breaches”, which significantly increases the scope of what can be considered a cyber security breach under the Rules.
A significant change between the two sets of rules can be found in sub-section (2) of Clause (8) of the official rules, which states that, “save as otherwise required for the purpose of any ongoing investigation, criminal complaint or legal proceedings the intermediary or the person in-charge of computer resource shall destroy records pertaining to directions for monitoring or collection of information”. The section in italics has been added to the original Clause (22) of the Draft Rules, meaning that when the Rules were originally drawn up, no exceptions were to be made for the destructions of the records for the issuing of directions for monitoring and/or the collected information. They would simply have to be destroyed within six months of the discontinuance of the monitoring/collection.
One change that may or may not be significant is the replacement of the words “established violations” in the Draft Rules to simply “violation” in the official Rules in Clauses (19)/(6), which deal with the responsibility of the intermediary. This could be taken to mean that suspected and/or perceived violations may also be punishable under this clause, but this is a hard stance to argue. Most likely the adjustment was made when those superfluous and/or convoluted parts of the Draft rules were being removed.



