Biometrics: An ‘Angootha Chaap’ nation?
Introduction
Fingerprints and iris scans. The Unique Identification (UID) Number aims to serve as a proof of identity that can be easily verified and linked to subsidies and to bank accounts. Four years into its implementation, the UID Scheme seems to have the vote of confidence of the public. More than 65 Crore Indians have been granted UID Numbers,[1] and only a few have been concerned enough to seek clarity through Right to Information Requests to the UIDAI about the finances and legal authority backing the scheme.[2] Parallel to the UID scheme, the National Population Register scheme is also under way, with enrolment in some areas, such as Srinagar, Shimla and Panchkula, having reached 100% of the estimated population.[3]
The NPR scheme is an offshoot of the census. It began in census cycle 2010-11, pursuant to the amendment of the Citizenship Act in 2004, under which national identity cards are to be issued. The desired outcome of the NPR scheme is an NPR card with a chip embedded with three bits of information built into a card: (i) biometric information, (ii) demographic information and (iii) UID Number.
Both the UID and NPR schemes aspire to be conduits that subsidies, utilities, and other benefits are routed through. While the UID and NPR schemes are distinct in terms of their legal sanctity, purpose and form, the harmonization of these two schemes is one of the UIDAI’s functions.
There are substantial overlaps in the information collected and the purpose they serve leading to the argument that having two schemes is redundant. The compatibility of the two schemes was questioned and it was initially thought that a merger would be unreasonable. While there has been speculation that the UID scheme may terminate, or that it would be taken over by the Home Ministry, it has been reported that the new government has directed expedited enrolments through the UID scheme. [4]
Both schemes are incomplete and suffer from vagaries, including, but not limited to: their legality, safeguards against misuse of the data, the implementation of the schemes – including the collection and storage of biometric information and their convergence or divergence.
This blog will focus on understanding the process of collecting biometric data in each scheme – calling out similarities and differences – as well as areas in which data collected under one scheme is incompatible with the other scheme. It will look at existing and missing safeguards in the collection of biometrics, overlap in the collection of biometrics by the two schemes, and existing practice in the collection of biometrics. In doing so the blog will highlight the lack of privacy safeguards for the biometric information and conclude that since the policies for data collection and use policy are unclear, the data subjects do not know how their data is being collected, used, and shared between the UID and the NPR schemes.
Unreliability of Biometric Data
Biometric data has been qualified as being unreliable.[5] It cannot always be successfully used to identify a person, especially in India, where manual labour degrades the fingerprint[6] and nutritional deficiencies mar the iris. Even experts working with the UIDAI[7] admit that fingerprints are not always good indicators of identity. If the very identification of a person fails, which is what the UID seeks to do, then the purpose of the UID is defeated.
Biometric Data Collection under the UID Scheme
In the current structure of the scheme, collected biometric information is stored by, and vests with the UIDAI for an undefined period. The data if used only for identification and authentication purposes, as originally intended, could very well fail to serve its intended purpose. But amassing the personal data of the entire country is lucrative, particularly to the service providers who collect the information and are mandated with the task to manually collect the data before it is fed into the UID system and encrypted. Most of the service providers that collect information, including biometric data, for the UID are engaged in information services such as IT or online marketing service providers.[8]
The below chart delineates the process followed for the collection of biometrics under the UID Scheme:
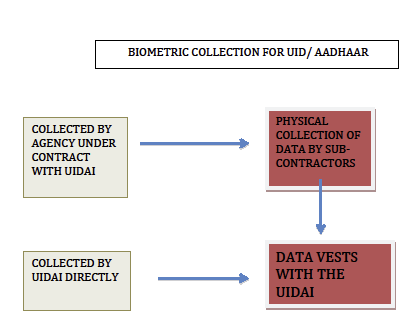 |
|---|
Under the NIAI Bill, all data collected or authenticated by the UIDAI, until the Bill is enacted and the National Identification Authority of India is created, vests with the UIDAI. In practice this means that the UIDAI owns the biometric data of the data-subject, without clear safeguards against misuse of the data.
In the UID scheme, the collection of biometrics at the time of enrollment by the UIDAI is severely flawed for a number of reasons:
1. Lack of clear legal authority and procedure for collection of biometrics: The only legal authority the UIDAI has to collect biometric information is via the notification of its constitution. Even then, the powers of the UIDAI are vague and broad. Importantly, the notification tells us nothing of how biometric data is to be collected and how it is to be used. These standards have only been developed by the UIDAI in an ad-hoc manner when the need arises or after a problem is spotted. The lack of purpose-specification is in violation of the law[9] and prevents the data subject from giving informed consent to data collection. This is discussed at a later stage.
2. The collection of Biometrics is regulated through only a Bill, which delegates the development of safeguards to Rules: The National Identification Authority of India (NIAI) Bill[10] confers the National Information Authority of India (NOT THE UIDAI) with the power to pass rules to collect biometric data and to prescribe standards for collection.[11] This is a rule-making power, which is conferred under a Bill. Neither has the Bill been enacted, nor have rules for the collection of biometrics been framed and notified.
3. Collection of biometric data only with implied consent: Though collection of biometrics is mentioned in the enrolment form, explicit consent for the collection of biometrics is not collected and only implied consent may be inferred. The last line in the enrollment form is titled ‘CONSENT’ and is a declaration that all data, including biometric information, is true.[12]
4. Collection of biometric data outsourced to third party: Collection of biometric information in the UID scheme is outsourced to third parties through tenders. For instance, Accenture has been declared a biometric service provider under a contract with the UID.[13] The third party may be a company, firm, educational institution or an accreditation agency. The eligibility criteria are quite straightforward, they relate to the entity’s structure and previous experiences with small projects.[14] Since the ability to protect privacy of the data subject is entirely absent from the eligibility criteria, a successful bidder may not have adequate procedure in place or sufficient experience in managing confidential data, to ensure the privacy of the data subject. By outsourcing the data collection, the UIDAI has arguably delegated a function it never had the legal authority to perform. Thus, the agency of the data collection is equally defective. To heighten the irregularity, these contract agents can sub-contract the job of physical data collection.[15] This means that the data operator and the ground supervisors, who come into direct contact with the raw data, including biometric data, are not appointed by the government, or the UIDAI, but by a private agency, who is further removed from the chain. The data operator scans the documents submitted for verification and has physical access to the document.[16]
5. Biometric data is admittedly vulnerable to sale and leakage: In an ongoing case in the Supreme Court of India, the national Capital Territory of Delhi has, in its counter-affidavit, admitted that data collected under the UID is vulnerable to sale and leakage.[17] To quote from the counter-affidavit ‘..in any exercise of gathering identities whether it is by census authority… or through the present process… there is always a possibility of leakage. Enumerators can scan and keep copies of all the forms and sell them for a price.- this (sic) it can never be said that the data gathered… is safe.’[18] Anyone who has registered for either UID is therefore a candidate for identity theft or unsolicited commercial information. This is also true for the NPR, as census data is the basis for the NPR.
Data collection under the NPR Scheme
The declaration of courts that it is unnecessary to link the UID number for public utilities and the admission by Delhi in the case that a data subject cannot be compelled to provide biometrics or to obtain a UID Number under the Aadhaar scheme[19] are steps forward in ensuring the voluntariness of UID. However, the UID Number is mandatory by implication. It is a pre-requisite for registration under the National Population Register, which is compulsory, pursuant to S. 14-A of the Citizenship Act. The below diagram delineates the collection of biometric information under the NPR scheme:
DATA FLOW PROCESS
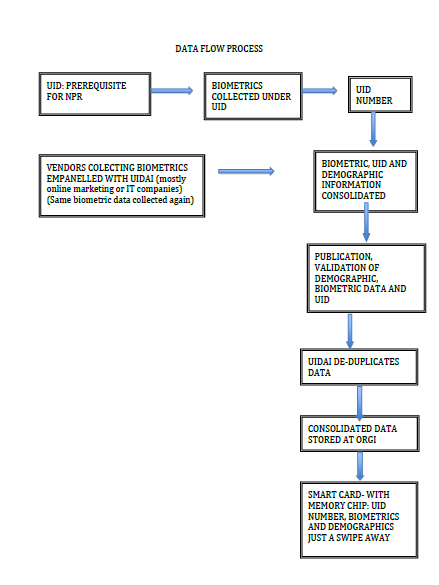 |
|---|
Flaws in the collection of biometric data under the NPR scheme
- Compulsion: Registration in the NPR is legally mandated and individuals who fail to do so can face penalty. As a note, arguably, the compulsion to register for the NPR is untenable, as the Rules prescribe penalty, whereas the Act does not. [20] A word of caution is appropriate here. The penalty under the Rules stands till it is deleted by the legislature or declared void by courts and one may be held liable for refusing to register for the NPR, though the above argument may be a good defense.
- Duplicity: Duplicity is a problem under the NPR Scheme. Biometric data is collected twice before the NPR exercise is completed. Even if one has registered under the UID scheme, they have to give their biometric information again under the NPR scheme. The first instance of collection of biometric information is for the UID number and the second, under the NPR scheme. The latter is necessary even if the data has already been collected for the UID number. Since the parties collecting biometric information for NPR are empanelled by the UIDAI and the eligibility is the same, the data is subject to the same or similar threats of data leakage that may arise when registering for the UID. The multi-level data collection only amplifies the admitted vulnerability of data as unauthorized actors can unlawfully access the data at any stage. This, coupled with the fact that UIDAI has to harmonize the NPR and UID schemes, and that the data comes to the UIDAI for de-duplication, means that the NPR data could be used by the UIDAI, but it may not result in a UID Number. There is no data that disproves this potential. This is a matter of concern, as one who wishes not to register for a UID number, in protection of their privacy, is at peril for their data falls into the hands of the UIDAI.
- Biometric data collectors under the NPR scheme empanelled by the UIDAI: The service providers collecting biometric data under the NPR are selected through bids and need to be empanelled with the UIDAI.[21] Most enrolment agencies that are empanelled with the UIDAI are either IT or online marketing companies[22], making the fear of targeted marketing even more likely.
- Public display and verification: Under the NPR scheme, the biometric and demographic information and UID number of registrants is publicly displayed in their local area for verification.[23] However, it is a violation of privacy to have sensitive personal data, such as biometrics put up publicly. Not only will the demographic information be readily accessible, nothing will prohibit the creation of a mailing list or collection of data for either data theft or for sending unsolicited commercial communication. The publicly available information is the kind of information that can be used for verification (Know Your Customer) and to authorize financial transactions. Since the personal information is displayed in the data subject’s local area, it is arguably a more invasive violation of privacy, since the members of the local area can make complex connections between the data subject and the data.
- Smart Card: The desired outcome of the NPR scheme is an NPR card. This card is to contain a chip, which is embedded with information such as the UID Number, biometrics and the demographic information. It is still unclear as to whether this information will be machine-readable. If so, this information may be just a swipe away. However, this cannot be confirmed without information on the level encryption and how the data will be stored on the chip.
‘Privacy safeguards available under the UID and NPR schemes are ad-hoc and incomplete
The safeguards under both the UID and NPR schemes are quite similar, since the UIDAI and its empanelled biometric service providers are involved in collecting biometric information for both the UID and the NPR.
Pilot studies for the UID scheme, including the use of biometrics, were not conducted in advance to implementation. In line with this, the enactment of a legislation governing the UID and the implementation of policies with respect to data handling and use will be made as and when the need arises. The development of safeguards in relation to the NPR will also be ad-hoc.
Also, the data standards for one will potentially influence that of the other scheme. For instance, the change in privacy standards for handling biometrics under the UID may affect the empanelment of biometric service providers. This will automatically affect the data security level the NPR can seek to achieve.
Being developed ad-hoc and after the fact, there is a risk that these regulations may unreasonably curtail the rights of data subjects.
The existing Indian laws on data protection and privacy are not comprehensive. Certain laws protect privacy only in specific situations. For instance, the IT Act and related rules protect privacy in relation to digital information.
Any body that collects sensitive personal data such as biometric data, or any other data for processing and storage has a legal mandate under the Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal data or Information) Rules, 2011 to make certain disclosures BEFORE OR WHILE THE DATA IS COLLECTED. This includes, inter-alia, disclosures of (i) the purpose of information collection, (ii) the intended recipients of the information and (iii) name and addresses of the collector and of the party retaining the data.[24]
Under the Rules, the data collector has a duty to give the data subject an option to withhold personal sensitive information.[25] A conversation with a data subject shows that this safeguard has not been upheld. The subject also conveyed a lack of knowledge of who the collection agency was. This is a problem of lack of accountability, as the data path cannot be traced and the party responsible for misuse or breach of security cannot be held liable.
Conclusion
The data collection under the NPR and UID schemes shows several vulnerabilities. Apart from the vulnerabilities with biometric information, there is a real risk of misuse of the data and documents submitted for enrolment under these schemes. Since the data collectors are primarily online marketing or IT service providers, there is likelihood that they will use this data for marketing.
We can only hope that in time, data subjects will be able to withdraw their personal data from the UID database and surrender their UID number. We can only wait and watch to see whether (i) the UID Number is a legal prerequisite for the NPR Card and (ii) whether the compulsion to register for NPR is done away with.
[1] https://portal.uidai.gov.in/uidwebportal/dashboard.do accesed: 21 August, 2014
[2] As of January 2013, only 25 RTI requests were made to the UIDAI http://uidai.gov.in/rti/rti-requests.html accessed: 21 August, 2014
[3] DIT-NPR Management Information System accessed: 22 August, 2014 http://nprmis.nic.in/NPRR33_DlyDigitPrgGraph.aspx
[4] Cloud Still Hangs Over Aadhaar’s Future, Business Standard, accessed 28 August, 2014. http://www.business-standard.com/article/current-affairs/cloud-still-hangs-over-aadhaar-s-future-114081401131_1.html
[5] Frost & Sullivan, Best Practices Guide to Biometrics, accessed: 13 August, 2014 http://www.google.co.in/url?sa=t&rct=j&q=&esrc=s&source=web&cd=5&cad=rja&uact=8&ved=0CD8QFjAE&url=http%3A%2F%2Fwww.frost.com%2Fprod%2Fservlet%2Fcpo%2F240303611&ei=6VbsU4m8HcK58gWx64DYDQ&usg=AFQjCNGqan81fX6qtG0S4VV6oh_B5R_QYg&sig2=cOOPm1JJ79AcJq2Gfq1_3Q&bvm=bv.73231344,d.dGc
[6] Malavika Jayaram, “India’s Identity Crisis”, Internet Monitor 2013, reflections of a digital world, accessed: 13 August, 2014 http://papers.ssrn.com/sol3/Delivery.cfm/SSRN_ID2366840_code727672.pdf?abstractid=2366840&mirid=1
[7]M. Vatsa, et.al, “Analyzing Fingerprints of Indian Population Using Image Quality: A UIDAI Case Study” , accessed: 13 August, 2014 https://research.iiitd.edu.in/groups/iab/ICPR2010-Fingerprint.pdf
[8] Prakash Chandra Sao, The Unique ID Project in India: An Exploratory Study, accessed: 21 August, 2014 http://subversions.tiss.edu/the-unique-id-project-in-india-an-exploratory-study/
[9] R. 5(3) of the Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal data or Information) Rules, 2011, accessed: 20 August, 2013 http://deity.gov.in/sites/upload_files/dit/files/GSR313E_10511(1).pdf
[10] National Identification Authority of India Bill, 2010 (Bill No. LXXV of 2010), accessed: 26 August,2014 http://164.100.24.219/BillsTexts/RSBillTexts/asintroduced/national%20ident.pdf
[11] Clause 23 of the NIAI Bill, 2010
[12]The UID Enrollment form, accessed: 26 August, 2014 http://uidai.gov.in/images/uid_download/enrolment_form.pdf
[13] Documents filed and relied on in Puttuswamy v Union of India
[14] Request for empanelment, accessed: 28 August, 2014. http://uidai.gov.in/images/tenders/rfe_for_concurrent_evaluation_of_processoperation_at_enrolment_centers_13082014.pdf
[15] This information is available from the documents filed and relied on in Puttuswamy v Union Of India, which is being heard in the Supreme Court of India
[16] An anonymous registrant observes that the data was scanned behind a screen and was not visible from the registered counter. The registrant is concerned that, in addition to collection of information for the UID, photocopies or digital copies could be taken for other uses and the registrant would not know.
[17] Counter Affidavit filed in the Supreme Court of India on behalf on New Delhi in K. Puttuswamy v Union of India
It is also admitted that the census is equally vulnerable. The information collected through census is used for the NPR exercise.
[18] Para. 48 in the Counter Affidavit filed by NCR Delhi.
[19] Affidavit in K. Puttuswamy v Union of India.
See also: FAQs: Enrollment Agencies, accessed 22 August, 2014 http://uidai.gov.in/faq.html?catid=37
[20] Usha Ramanathan, A Tale of Two Turfs, The Statesman, accessed: 20 August, 2014 http://www.thestatesman.net/news/10497-a-tale-of-two-turfs-npr-and-uid.html?page=3
[21] RFQ for Engaging MSP for Biometric Enrolment for the Creation of NPR, accessed: 26 August, 2014 http://ditnpr.nic.in/pdf/120102_RFQBiometricUrban_rebidding-Draft.pdf
[22] Prakash Chandra Sao, The Unique ID Project in India: An Exploratory Study, accessed: 21 August, 2014 http://subversions.tiss.edu/the-unique-id-project-in-india-an-exploratory-study/
[23] http://censusindia.gov.in/2011-Common/IntroductionToNpr.html, accessed: 26 August, 2014
[24] R. 5(3) of the Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal data or Information) Rules, 2011, accessed: 20 August, 2013 http://deity.gov.in/sites/upload_files/dit/files/GSR313E_10511(1).pdf
[25] R. 5(7) of the Information Technology (Reasonable Security Practices and Procedures and Sensitive Personal data or Information) Rules, 2011.



