Rise of the bot: all you need to know about the latest threat online
The article by Danish Raza was published in the Hindustan Times on January 5, 2014. Snehashish Ghosh is quoted.
A bot is a software that mimics human behaviour on the Internet. Bots can be used to create artificial accounts on social media, provide numerous likes on a particular page, send tweets or visit various websites. All this is done without any human involvement.
Bots already constitute a significant percentage of Non Human Traffic (NHT) online, which has, according to some estimates, eclipsed human traffic. Comscore, a US-based Internet technology company noted on its blog that NHT, also known as Artificial Traffic, increased from approximately 6% of the total web traffic in 2011, to 36% in 2012. Last month, a report from Incapsula, a cloud-based security service, which aids the security and performance of websites, stated that more than 60% of web traffic was non-human in 2013. The figure was based on data collected from the 20,000 sites on Incapsula’s network .
Other than bots, NHT on the web includes traffic generated by Internet routers and back end services used by websites to communicate with third parties.
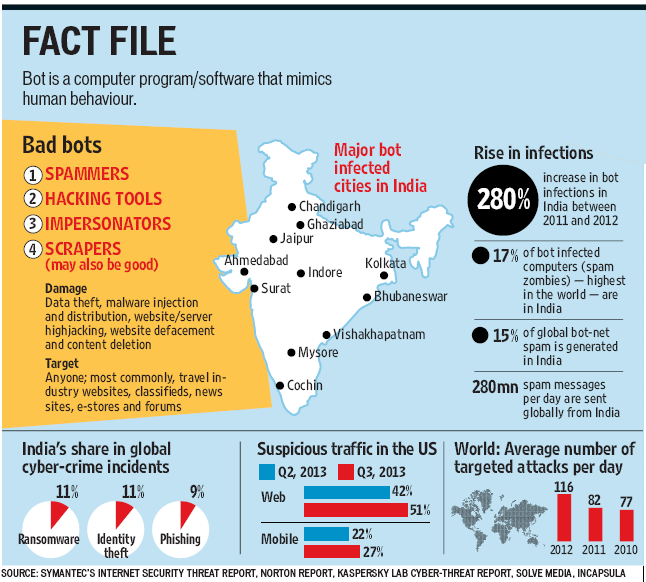
India is not immune to the problem. According to the Symantec Internet Security Threat Report for 2012, there was a 280% increase in bot infections in India between 2011 and 2012. 17% of bot-infected computers, the highest in the world, are in India and 15% of global bot-net spam is generated here. The report also states that 69 Indian cities are prone to bot infections which includes Bhubaneswar, Surat, Cochin, Jaipur, Visakhapatnam, Indore, Kota, Ghaziabad and Mysore.
Bot spotting
How do you spot a bot? When a bot or its friend is at work, the browser directs you to sites other than the ones you intend to visit, you get full-page pop ups and pop unders, and when you quit the browser, it gets relaunched after a few minutes. Chances are your computer is part of a chain of online events which create NHT on the web, the purpose of which may be to attack a site or a server.
Why you should be wary
Malicious traffic, malware, hacking attempts, viruses slow down the Internet and delay legitimate traffic and services. Used to target systems or take down websites, NHT generates fake clicks on advertisements to increase website statistics.
One of the perils of ignoring artificial web traffic is that it gets counted for real impressions for which clients end up paying. For example, a website owner may hire the services of a digital marketing firm to publicise the site. In the guise of increasing page views, the marketing firm can produce a bill for fake impressions, supplementing actual human traffic to the page with bot usage.
“Unless there is a curb on this practice of malicious NHT, one stands at risk of being duped by marketers, agencies and even clients,” said Chiragh Cherian, director, online PR at Perfect Relations, a brand management firm. Recent studies have estimated bot traffic to be between 4 - 31% of total web traffic in the US, which translates to between $650 million and $4.7 billion in wasted marketing spend. According to Miaozhen Systems, a leading Chinese advertising technology company, NHT caused advertisers in China to lose approximately US$ 1.6 billion between July 2012 and June 2013.
How to combat Non-Human Traffic
Most servers have defence mechanisms to tackle spam and cyber attacks. Websites are also now developing mechanisms such as asking for human authentication which is difficult for a bot to execute. “But even personal computers should be equipped with strong Internet security applications such as anti-virus and anti-spyware to prevent hacking and phishing attempts and to prevent being used as slave machines for distributed cyber attacks,” said Chintu Cherian Abraham, a digital media professional. Figures show that we need to watch out where and how we go online. According to Norton Report, 2013, 61% Indians access their social network accounts from unsecured wi-fi connections, while 42% access bank accounts and 44% shop online using unsecured wi-fi connections.
Social media companies are gradually devising mechanisms to filter bots. “When a page and a fan connect on Facebook, we want to ensure that connection involves a real person interested in hearing from a specific page and engaging with that brand’s content. As such, we have recently increased our automated efforts to remove Likes on Pages that may have been gained by means that violate our terms,” mentions Facebook’s site integrity policy.
Agency-client intervention is necessary to ensure that artificial traffic is not presented as real. “It’s also important to make all agencies, advertisers and clients aware of their responsibility to keep the Internet free from malicious NHT,” said Chiragh Cherian.
Government involvement is also needed to control the problem of malicious bots. “A lot needs to be done from the government’s side to tackle bots which can be used to target the country’s critical infrastructure such as banking websites,” said Jiten Jain, a cyber security analyst, adding, “Last year, I highlighted the flaws in HDFC’s net banking website which have been rectified now. They could have been exploited to block the net-banking service.”
Until we have a robust mechanism to filter out bogus traffic from real, it will be difficult to say whether the social media followers of Bansal and other public figures are human or not.
 |
|---|
Know your Bots
Not all bots are used with a negative intent. Some help in research and monitoring.
The Malicious
Bots can be effectively used to impersonate and to hack accounts leading to financial losses and intellectual property theft. “Theft of personal details, username and password to operate one’s bank account is a classic example of how bots can lead to financial losses. It is an organised cyber crime,” explained Commander (Retd) Mukesh Saini, former national information security coordinator, Government of India. In May 2013, cyber criminals broke into the Mumbai-based account of the RPG group and siphoned off `2.4 crore. Three people were arrested in the case.
“The rate at which NHT is increasing is alarming,” says Tinu Cherian Abraham. “Any computer connected to the Internet is vulnerable to such attacks. The user will not get to know about it unless he or she has installed an Internet security application.”
Besides bots, computers also generate other kinds of secondary activities, while the user is surfing the Internet. This activity remains in the background and is never seen by the user, unlike the bot-generated pop ups, observes Comscore. For example, your computer might be being used as a channel to reach a server with the intention of hacking it. And you will never know.
The Good
Not all NHT is bad, though. In fact, good bots such as scrapers can be effectively used to conduct research. “Wikipedia can be scraped to investigate the frequency of edits on a Wikipedia page and track the increase in the number of editors,” explained Snehashish Ghosh, policy associate at the Bangalore-based Centre for Internet & Society.
Good bots are also used by search engines to track content on websites and enhance their search results. Search bots and other good bots formed 31% of total bots, the Incapsula report noted.
The Social
Apart from malicious and good bots, there are social media bots too. “Extensive analysis is done on social media traffic for monitoring, business lead generation, as well as reputation management. This has amounted to a lot of automated or non-human traffic,” said Abraham.
According to Facebook’s filings published in a Forbes report in February 2012, around 83 million of its users are bogus. “It’s a violation of our policies to use a fake name or operate under a false identity, and we encourage people to report any user they suspect of doing this, either through the report links we provide on the site or through the contact forms in our help centre,” a Facebook spokesperson told HT.
Twitter bots have also made its presence felt on the platform. “Twitter has witnessed very interesting bots which have found appreciation from the community for being funny and creative. The microblogging site cracked down on some harmful bots, but still some of the advanced level bots slip through the net,” said Ghosh.
In August 2012, London-based firm Digital Evaluators, which evaluates social media presence of worldwide companies, released an analysis of Twitter followers of the US Presidential Election candidates Barack Obama and Mitt Romney. 21.9% of Barack Obama’s 17.82 million Twitter followers were found to be bogus.
The Big Brother
Ghosh said that the increase in NHT related to the Internet of things, the concept which enables communication between two or more devices, results in privacy issues. “Take a situation where your mobile device is constantly tracking your location for the purpose of switching on the air conditioner at your home before you reach. Such applications produce huge amounts of personal data and there is no clarity whether this data is being stored,” he said.
“As the new networks link data from products, company assets, or the operating environment, they will generate better information and analysis, which can enhance decision making significantly. Some organisations are starting to deploy these applications in targeted areas, while more radical and demanding uses are still in the conceptual or experimental stages,” noted a McKinsey & Company report on Internet of things.




