Videos
आधार नंबर, नाम, पता, बैंक अकाउंट और दूसरी संवेदनशील जानकारियां लीक: CIS रिपोर्ट
This was published by Aaj Tak on May 4, 2017.
ताजा रिसर्च के मुताबिक सरकार के डेटाबेस से लगभग 135 मिलियन आधान नंबर ऑनलाइन लीक हुए हो सकते हैं. इस रिसर्च दी सेंटर फॉर इंटरनेट एंड सोसाइटी (CIS) ने कराया है. इस एजेंसी ने इस रिसर्च को इनफॉर्मेशन सिक्योरिटी प्रैक्टिस ऑफर आधार के नाम से प्रकाशित किया है.
रिपोर्ट के मुताबिक सरकारी पोर्टल्स ने लगभग 135 मिलियन भारतीय नागरिकों के आधार नंबर ऑनलाइन को पब्लिक कर दिया. यानी कोई भी इसे ऐक्सेस कर सके. जाहिर है ऐसे में आधार नंबर के गलत यूज का भी खतरा होता है.
चार सरकारी वेबसाइट जिनमें मनरेगा, सोशल ऐसिस्टेंस प्रोग्राम, डेली ऑनलाइन पेमेंट रिपोर्ट और चंद्रण बीमा स्कीम वेबसाइट शामिल हैं. रिपोर्ट के मुताबिक इन वेबसाइट्स पर यूजर्स के आधार नंबर और फिनांशियल जानकारी जैसे बैंक अकाउंट डीटेल को पब्लिक कर दिया जिसे कोई भी ऐक्सेस कर सकता है.
रिपोर्ट के मुताबिक नेशनल सोशल ऐसिस्टेंस प्रोग्राम की वेबसाइट पर पेंशन धारकों के जॉब कार्ड नंबर, बैंक अकाउंट नंबर, आधार कार्ड नंबर और अकाउंट की स्थिति जैसी संवेदनशील जानकारियां उपलब्ध होती हैं. लेकिन कमजोर सिक्योरिटी की वजह से यह दुनिया के किसी भी इंसान के लिए उपलब्ध हो गई. सिर्फ कुछ क्लिक से ही तमाम संवेदनशील जानकारियां हासिल की जा सकती हैं.
हाल ही में झारखंड सरकार की एक वेबसाइट पर लाखों आधार कार्ड होल्डर्स की जानकारियां लीक हो गईं. इसके अलावा कई राज्यों की सरकारी वेबसाइट पर स्कॉलरशिप पाने वाले स्टूडेंट्स के आधार कार्ड डीटेल्स लीक हो गए. गूगल सर्च के जरिए सिर्फ कुछ कीवर्ड्स यूज करके डीटेल्स कोई भी ढूंढ कर गलत यूज कर सकता है.
इस रिसर्च रिपोर्ट में कहा गया है आधार नंबर, जाती, धर्म, पता, फोटोग्राफ्स और यूजर की आर्थिक जानकारी इस तरह पब्लिक होना इस बात को दर्शाता है कि इसे कितने लचर तरीके से लागू किया गया है.
हाल ही में मानव संसाधन विकास मंत्रालय की वेबसाइट से ऐसे डेटा ऐक्सेल शीट आसानी से गूगल के जरिए डाउनलोड की जा सकती थी. आप इसे चूक करें या लापरवाही, लेकिन इतने नागरिकों का घर तक का पता किसी के पास भी हो सकता है.
क्या आधार नंबर को पब्लिक करना सही है?
आधार ऐक्ट 2016 के मुताबिक किसी नागरिक का आधार डेटा पब्लिश नहीं किया जा सकता. यानी मंत्रालय की वेबसाइट इन डेटा को सिक्योर रखने में नाकामयाब हो रही हैं.
आधार ऐक्ट 2016 के तहत कलेक्ट किया गया कोई भी आधार नंबर या कोर बायोमैट्रिक इनफॉर्मेशन पब्लिक नहीं किया जा सकता और न ही इसे किसी पब्लिक प्लैटफॉर्म पर पोस्ट किया जा सकता है. हालांकि इसके इस्तेमाल कानून के तहत शामिल की गईं एजेंसियां और संस्थाएं कर सकती हैं.
दी वायर की एक रिपोर्ट के मुताबिक एक महीने पहले डेटा रिसर्चर श्रीनीवास कोडाली ने थर्ड पार्टी वेबसाइट के द्वारा गलती लीक किए गए 5-6 लाख लोगों के पर्सनल डेटा के बारे में बताया था. इस डेटा में आधार नंबर, नाम, कास्ट, जेंडर और फोटोज शामिल थे.
सरकार के हमेशा दावा करती है कि आधार सिक्योर है
सरकार लगातार दावा करती है कि आधार सिक्योर है सेफ है और डेटा लीक नहीं हो रहे हैं. लेकिन ये घटनाएं लागातार उन दावों को खोखला साबित कर रही हैं. सवाल यह है कि अब इस रिपोर्ट के बाद सरकार कोई कठोर कदम उठाती है या फिर पहले की तरह लचर सुरक्षा बनी रहेगी.
'Aadhaar' Of Your Existence Or Card Of Controversy?
This was telecasted by NDTV on May 3, 2017. Amber Sinha was a panelist.
As the Supreme Court questioned the government about this, the centre admitted for the first time that the leaks had taken place but passed the onus on to state governments. It also argued that no technology was a 100 per cent foolproof but that couldn't be the basis for a constitutional challenge. Those who have petitioned against making Aadhar mandatory for filing income tax say no other democratic country has such a requirement and allege that it shows the sinisterness of the government.
Video
Surveillance in India: Policy and Practice
Pranesh presented a narrative of the current state of surveillance law, our knowledge of current surveillance practices (including noting where programmes like Natgrid, CMS, etc. fit in), and charted a rough map of reforms needed and outstanding policy research questions.
Pranesh Prakash
Pranesh Prakash is a Policy Director at - and was part of the founding team of - the Centre for Internet and Society, a non-profit organisation that engages in research and policy advocacy. He is also the Legal Lead at Creative Commons India and an Affiliated Fellow at the Yale Law School's Information Society Project, and has been on the Executive Committee of the NCUC at ICANN. In 2014, he was selected by Forbes India for its inaugural "30 under 30" list of young achievers, and in 2012 he was recognized as an Internet Freedom Fellow by the U.S. government.
His research interests converge at the intersections of technology, culture, economics, law, and justice. His current work focuses on interrogating, promoting, and engaging with policymakers on the areas of access to knowledge (primarily copyright reform), 'openness' (including open government data, open standards, free/libre/open source software, and open access), freedom of expression, privacy, digital security, and Internet governance. He is a prominent voice on these issues, with the newspaper Mint calling him “one of the clearest thinkers in this area”, and his research having been quoted in the Indian parliament. He regularly speaks at national and international conferences on these topics. He has a degree in arts and law from the National Law School in Bangalore, and while there he helped found the Indian Journal of Law and Technology, and was part of its editorial board for two years.
Click here to see the agenda for the brainstorming session on net neutrality.
Video
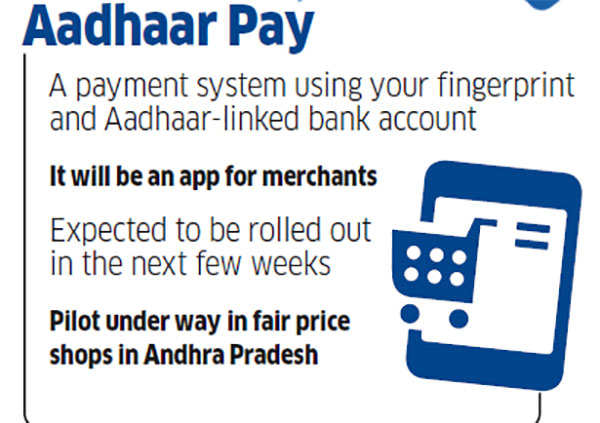
The soon-to-be launched Aadhaar Pay will let you make purchases using your fingerprint
The article by Indulekha Aravind was published in the Economic Times on 15 January 2017. Sunil Abraham was consulted for this.
Ajay Bhushan Pandey, CEO of the Unique Identification Authority of India (UIDAI), says it will be rolling out Aadhaar-enabled payment system, or Aadhaar Pay, for merchants in the next few weeks. This will be an app for merchants that enables them to receive payments through biometric authentication of the customer, provided their bank accounts are linked to their Aadhaar number. "A pilot is under way in fair price shops in Andhra Pradesh where shopkeepers are accepting payments from PDS beneficiaries. The results are very encouraging," says Pandey.
The idea takes off from the existing Aadhaar-enabled payment system (AEPS) used by bank business correspondents (BCs) in rural areas to disburse and accept cash, using micro ATMs. "We are trying to tweak this so that a similar device can be used by a local merchant," says Pandey. Adoption will depend on two factors: merchants’ acceptance of it and whether they can use an app rather than a micro ATM. The biggest advantage through this method of payment, says Pandey, is that the customer will not need a credit or debit card, or even a smartphone.
The limits for transactions using AEPS, such as the number of daily transactions, will be left to the discretion of the banks. In the long term, the AEPS will be migrated to the BHIM (Bharat Interface for Money) platform but the rollout of Aadhaar Pay will happen before that. Post demonetisation, banking BC’s number of transactions using AEPS has leapt from 4-5 lakh to 14-15 lakh, says Pandey. According to Reserve Bank of India data on electronic payment systems, the total volume of such transactions jumped from 671 million in November 2016 to 957 million in December. USSD-based payments, which can be done using a basic feature phone, are among the biggest beneficiaries: the volume rose from just 7,000 in November to 1,02,000 in December, and value of transactions from over Rs 7,000 to over Rs 1 lakh. Prepaid payment instruments — mainly mobile wallets — rose from 59 million to 88 million in the same period (and value from Rs 1,300 crore to Rs 2,100 crore).
While Aadhaar Pay is likely to ride the demonetisation wave if it is launched soon, certain concerns remain, as the list is how secure such a payment system will be. The UIDAI CEO says it is a paramount concern for the organisation, too. "We are using the latest technology to ensure the information stays encrypted end to-end, so that information is not leaked or misused. In the months to come, we will strengthen the security."
Wary About Security
Sunil Abraham, executive director of the Centre for Internet and Society, a think tank that has been analysing the Aadhaar project for six years, outlines several reasons why Aadhaar-based biometrics is inappropriate for authentication in payments, unlike card-based payments that use cryptography.
"With biometrics, there is always an error ratio. It is imprecise matching, whereas with cryptography (smart cards), there is no false positive or negative. You either have the key (PIN) or you don’t. It is also very cheap to defeat biometric authentication — even an unlettered person can do it," says Abraham. It would be easy enough, he says, to replicate someone else’s fingerprint by pressing it against lukewarm wax and filling the mould with glue to get a dummy finger. In contrast, compromising a smart card requires more cost and effort, from tech-savviness to machines such as a skimmer that will read the card. "And once you are compromised,you are compromised forever. You can’t change it, like a debit card PIN."
Using Aadhaar for authentication had proved to be a failure during the exchange of currency notes following demonetisation, he adds, pointing to how the poor and the middle class stood in queues for money while stacks of new currency were recovered from the homes of businessmen and bureaucrats. "When you have bank officials who are corrupt, giving them your biometrics is giving them more ammunition for corruption." To catch the criminals, law enforcement agencies had to resort to CCTV footage,a relatively older technology, he says. Others point out that while it may be secure, certain factors stand in the way of making biometrics-based payment authentication a large-scale success. Amrish Rau, CEO of PayU India, a payment gateway provider, cites a list of reasons why it would inevitably take off but only in 5-10 years.
"For one, the technology is not yet good enough. There are also bandwidth and data constraints in sending biometric data," says Rau. Even in more mature markets, it has yet to find widespread acceptance, he says, pointing to the slow adoption of Apple Pay and Samsung Pay in the US. "It’s not the answer today.” This is in contrast to NITI Aayog CEO Amitabh Kant’s recent remarks that cards and PoS machines would become redundant by 2020 because Indians would be making payments using their thumb (biometrics). "... my view is that in the next two and a half years, India will make all its debit cards, credit cards, all ATM machines, all PoS machines totally irrelevant,” Kant had said at a Pravasi Bharatiya Divas session in Bengaluru.
Seminar on Quality of Services in Telecom and Data Services: Issues, Challenges and Solutions
CUTS and IIT have recently published a report on quality of services in mobile data services, which is available here. The aim of the organizers was to bring together a diverse group of stakeholders to generate a debate on the findings of the study. This will be followed by a broader discussion on the next steps towards achieving better QoS in telecom and data services. For agenda of the meeting, click here.
Video
Fuel Gilt Conference 2016
Technical and other interface strings that fall under the ambit of FUEL are actually a subset of several other localization projects. They can also be used for bettering the corpus of machine translation. And there is a need for collaboration between communities and institutions -- both free and open source, and the proprietary ones -- to help grow their corpus. More and more collaborations in place will help the volunteer localizers even more as the localization suggestions will increase drastically with partnerships are more. Two existing such partnerships could be Pontoon by Mozilla and Content Translation by the Wikimedia Foundation. When the former shows localized strings from memory as suggestion and even include translations by proprietary organizations like Microsoft, the latter helps Wikipedians create Wikipedia articles faster by translation suggestions sourced from the corpus of Apertium and Yandex. Bettering collaboration needs strengthening two major aspects; a) growing professional and mutual bonding with other communities/organizations that are there in the same domain, and b) creating technical infrastructure to address the aforementioned pluralism. In my talk, I will detail about my own experience and best practices from working with several communities beyond borders and lessons learned from from my own work and the work of many others. A larger discussion with other colleagues at the Conference will hopefully shape into creating a manual or a few Open Educational Resources of some kind to help the future localization leaders. For more info, click here.
Video
Talking Point: Futile Battle Against Torrents
Video
This was originally published by Deccan Herald on August 30, 2016
ଇଣ୍ଟରନେଟରେ ଓଡ଼ିଆ ଏନସାଇକ୍ଲୋପିଡ଼ିଆ "ଉଇକିପିଡ଼ିଆ" ବିକାଶ ପାଇଁ ଏକାଠି ହେଲେ ପୁରୀର ଛାତ୍ରଛାତ୍ରୀ
The article that came May 20 on YourStory Odia, is about WikiTungi Puri and highlights a female editor Adyasha Sahu. WikiTungi Puri is a collective of the Odia Wikimedia community members that are based in the city of Puri.
ପୁରୀରେ ଆୟୋଜିତ ଏକ ଉଇକିପିଡ଼ିଆ କର୍ମଶାଳା ପରେ ସେଠାରେ ଆଗରୁ ଗୁଗୁଲ ଡେଭଲପର୍ସ ଗ୍ରୁପରେ ସକ୍ରିୟ ଥିବା ସ୍ୱେଚ୍ଛାସେବୀ କର୍ମୀମାନେ ଉଇକିପିଡ଼ିଆରେ ଯୋଗ ଦେଇ ବିଭିନ୍ନ ବିଷୟରେ ଲେଖିବା ଆରମ୍ଭ କଲେ । କେଇଟା ଦିନ ଭିତରେ ଆଗରୁ ଅବହେଳିତ ବିଭିନ୍ନ ବିଷୟ ଯଥା ମୋବାଇଲ, କମ୍ପ୍ୟୁଟର ଓ ଇଣ୍ଟରନେଟ ସମ୍ବନ୍ଧିତ ଲେଖା, । ଏହି ୧୨ ଜଣିଆ ଦଳରେ ଥିବା ୪ ଜଣ ଝିଅ ଓଡ଼ିଶା ଓ ଓଡ଼ିଶା ବାହାରର ବିଭିନ୍ନ ଜଣାଶୁଣା ନାରୀଙ୍କ ସମ୍ବନ୍ଧରେ ଲେଖାସବୁ ତିଆରିବା ସହିତ ଆଗରୁ ଥିବା ଲେଖାଗୁଡ଼ିକ ଉନ୍ନତ କରିଆସୁଛନ୍ତି । ଏମାନଙ୍କ ଅବଦାନ ଫଳରେ ବିଭିନ୍ନ ଜଣାଅଜଣା ବିଷୟରେ ଉପାଦେୟ ଲେଖାସବୁ ପାଠକମାନଙ୍କ ପାଇଁ ଖୋଲାରେ ଉପଲବ୍ଧ ହେଉଛି । ଆଗକୁ ଛାତ୍ର, ଶିକ୍ଷକମାନେ ବହି ବାହାରେ ଓଡ଼ିଆରେ କିଛି ପଢ଼ିବାକୁ ଚାହିଁଲେ ଏସବୁ ବ୍ୟବହାରରେ ଲାଗିବ ।
ଏମାନଙ୍କ ଭିତରୁ ଜଣେ ଉଇକିଆଳି ଆଦ୍ଯାଶା କହନ୍ତି, "ମୁଁ ପ୍ରଥମେ ଲେଖିବା ଆରମ୍ଭ କଲାବେଳକୁ ରବୀନ୍ଦ୍ରନାଥ ଠାକୁରଙ୍କ ବାବଦରେ ଛୋଟ ଲେଖାଟେ ଥିଲା । ଆଉ ମୋର ତାଙ୍କ ବାବଦରେ ଓଡ଼ିଆରେ କିଛି ପଢ଼ିବା ପାଇଁ ଇଚ୍ଛା ଥିଲେ ବି ଇଣ୍ଟରନେଟରେ କିଛି ଖୋଜି ପାଉଲି ନାହିଁ । ତେଣୁ ନିଜେ ଇଂରାଜୀରୁ ଅନୁବାଦ କରିବା ଆରମ୍ଭ କଲି । ନିକଟରେ ଗୋଟେ ପରୀକ୍ଷାରେ ତାଙ୍କ ବିଷୟରେ ପଡ଼ିଥିଲା ଯେ ମୁଁ ମୋର ନିଜ ଲେଖା ଅନୁଭୂତି କେତେ କାମରେ ଆସିଲା ତାହା ଜାଣିଲି", ବଖାଣନ୍ତି ଆଦ୍ୟାଶା ।
ଆଉ ଜଣେ ମହିଳା ଉଇକିଆଳି ଅଲିଭା ସାହୁ କହନ୍ତି, "ମୁଁ କାକଟପୁର କଲେଜରେ ପଢ଼ିଲା ବେଳେ ବାଦ୍ୟଯନ୍ତ୍ର ଉପରେ ଲେଖାଟିଏ ଥିଲା । ସେତେବେଳେ ମୁଁ ଓଡ଼ିଆରେ ବିଶେଷ କିଛି ପଢ଼ିବାକୁ ପାଇନଥିଲି । ଏମିତି ଖୋଜୁଖୋଜୁ ଦିନେ ସେ ବାବଦରେ ଲେଖାଟିଏ ପାଇଲି । ଇଂରାଜୀ ଲେଖା ଆଉ ହିନ୍ଦୀ ଲେଖା ଦୁଇଟିରୁ ମିଶାଇ ଓଡ଼ିଆକୁ ଅନୁବାଦ କଲି ।"
ଅନୁବାଦ ହେଉ କି ମୌଳିକ ଭାବେ ହେଉ, ଉଇକିପିଡ଼ିଆରେ ବିଭିନ୍ନ ପ୍ରକାଶିତ ଲେଖାର ଆଧାରରେ ଉଇକିଆଳିମାନେ ତିଆରିଚାଲିଛନ୍ତି ଭଳିକି ଭଳି ନୂଆ ଲେଖା ।
Video
ପୁରୀର ଏହି ଉଇକିଆଳିମାନେ ଏକାଠି ହୋଇ ଗଢ଼ିଛନ୍ତି "ଉଇକିଟୁଙ୍ଗି ପୁରୀ" । ପୁରୀରେ ଯୁବପିଢ଼ିଙ୍କୁ ଉଇକିପିଡ଼ିଆ ସମ୍ପର୍କରେ ଅବଗତ କରାଇବା, ପୁରୀ ସାମନ୍ତ ଚନ୍ଦ୍ରଶେଖର ସ୍ୱୟଂଶାସିତ କଲେଜରେ ଉଇକିପିଡ଼ିଆର ପ୍ରଚାର ପ୍ରସାର କରାଇବା, ପୁରୀରେ କର୍ମଶାଳା ଓ ମେଳଣ ଅଧିକରୁ ଅଧିକ ଲୋକଙ୍କୁ ଓଡ଼ିଆରେ ଟାଇପ ଶିଖାଇବା ଓ ସେମାନଙ୍କୁ ନିଜ ଅଞ୍ଚଳ ଓ ଆଗ୍ରହର ବିଷୟ ବାବଦରେ ଲେଖିବା ପାଇଁ ଆଗଭର କରାଇବା ଓ ଓଡ଼ିଆ ଢଗଢମାଳି-ଲୋକକଥା ଆଦିକୁ ଗୋଟେ ସ୍ଥାନରେ ଉପଲବ୍ଧ କରାଇବା ପାଇଁ ଉଇକିକଥା ନାମରେ ଆଉ ଏକ ପ୍ରକଳ୍ପର ବିକାଶ କରାଇବା ହେଉଛି ଏହି ଦଳର ମୁଖ୍ୟ ଲକ୍ଷ୍ୟ ।
ବାକି ଭାରତୀୟ ଓ ଏସୀୟ ଭାଷା ଭିତରୁ ଓଡ଼ିଆ ଏକ ପୁରୁଣା ଭାଷା ହୋଇ ସୁଦ୍ଧା ଓଡ଼ିଆର ଇଣ୍ଟରନେଟରେ ବ୍ୟବହାର ଖୁବ ଊଣା । ଯଦିଓ ଓଡ଼ିଶାରେ ନିୟମିତ ପ୍ରକାଶିତ ଓଡ଼ିଆ ଖବରକାଗଜ ଧୀରେ ଧୀରେ ବଢ଼ି ବଢ଼ି ଚାଲିଛି ସେସବୁ ଏଯାବତ ଇଉନିକୋଡ଼ରେ ଉପଲବ୍ଦ ହେଉନଥିବାରୁ ଲେଖାଗୁଡ଼ିକ ଇଣ୍ଟରନେଟରେ ଖୋଜିଲେ ମିଳୁନାହିଁ । ଆଉ ସବୁ କାଗଜର ପୁରୁଣା ଅଭିଲେଖ ଉପଲବ୍ଧ ହେଉନଥିବାରୁ ଜଣେ ଲୋଡ଼ାପଡ଼ିଲେ ଖବରଟେ ଖୋଜି ପାଇପାରିବ ନାହିଁ । ଏ ଦିଗରେ ପ୍ରକାଶନ ସଂସ୍ଥା, ବ୍ୟକ୍ତିବିଶେଷ ଓ ସରକାର ସଭିଏଁ ଚେଷ୍ଟା କଲେ ଯାଇ ଅଧିକରୁ ଅଧିକ ଲେଖା ଇଣ୍ଟରନେଟରେ ଉପଲବ୍ଧ ହୁଅନ୍ତା । ଏଯାଏ ଗୁଗୁଲର ପ୍ରଧାନ ପୃଷ୍ଠାରେ ଯେ ଓଡ଼ିଆ ଆସୁନାହିଁ ବୋଲି ଅନେକେ ମତ ଦିଅନ୍ତି ତା'ର ମୁଖ୍ୟ କାରଣ ହେଲା ଇଣ୍ଟରନେଟରେ ଓଡ଼ିଆ ଲେଖାର ଘୋର ଅଭାବ । ଏ ଦିଗରେ ଅଣଲାଭକାରୀ ସ୍ୱେଚ୍ଛାସେବୀଙ୍କ ଦ୍ୱାରା ପରିଚାଳିତ ସମୂହ ଉଇକିପିଡ଼ିଆର ଭୂମିକା ଉଲ୍ଲେଖଯୋଗ୍ୟ । ଉଇକିପିଡ଼ିଆ (Wikipedia) ୨୦୦୧ରେ ପ୍ରଥମେ ଇଂରାଜୀରେ ଆରମ୍ଭ ହୋଇ ଧୀରେ ଧୀରେ ବାକି ଭାଷାରେ ଆରମ୍ଭ ହେଲା । ଆନନ୍ଦର ବିଷୟ ଯେ ଓଡ଼ିଆରେ ଉଇକିପିଡ଼ିଆ ୨୦୦୨ ମସିହାରେ ପ୍ରଥମ ଭାରତୀୟ ଭାଷାର ଉଇକିପିଡ଼ିଆ ଭାବେ ଅହମୀୟା, ମାଲାୟାଲାମ ଓ ପଞ୍ଜାବୀ ସହିତ ଗଢ଼ାହେଲା । ଅଧୁନା କେବଳ ଇଂରାଜୀ ନୁହେଁ ୨୮୭ରୁ ଅଧିକ ଭାଷାରେ ଉପଲବ୍ଧ ଏହି ଖୋଲା ଅନଲାଇନ ଏନସାଇକ୍ଲୋପିଡ଼ିଆ । ଅନେକେ ଜାଣି କାବା ହେବେ ଯେ ଓଡ଼ିଆ ଉଇକିପିଡ଼ିଆରେ ଲେଖୁଥିବା ସମ୍ପାଦକ ବା ଉଇକିଆଳିଙ୍କ ସଂଖ୍ୟା ପାଖାପାଖି ୨୫-୩୦ ହେଲେ ହେଁ ଏଥିରେ ଲେଖା ପ୍ରସଙ୍ଗ ସଂଖ୍ୟା ୧୦,୬୦୦ରୁ ଅଧିକ । ପୁରୀର ଉଇକିଆଳିମାନଙ୍କ ଆସିବା ପରେ ଓଡ଼ିଆ ଉଇକିଆଳିଙ୍କ ସଂଖ୍ୟା ପାଖାପାଖି ଦୁଇଗୁଣା ବଢ଼ିଛି ବୋଲି କହିହେବ ।
ଓଡ଼ିଆ ଉଇକିପିଡ଼ିଆରେ ଥିବା ପ୍ରସଙ୍ଗ http://or.wikipedia.org ରେ ପଢ଼ିପାରିବେ । ଏଥିରେ ସଭିଏଁ ଲେଖିପାରିବେ (ଲେଖିବା ବାବଦରେ ଦରକାରୀ ସୂଚନା) ।
ଫଟୋ: ସ୍ନେହାଶିଷ ନାୟକ (CC-BY-SA 4.0)
Facebook Free Basics vs Net Neutrality: The top arguments in the debate
The article was published in the Indian Express on December 31, 2015. Sunil Abraham and Pranesh Prakash were quoted.
Facebook’s Free Basics app, which aims to provide ‘free Internet access’ to users who can’t afford data packs, has run into trouble in India over the last two weeks. After regulator TRAI issued a paper questioning the fairness of zero-rating platforms, it also asked Reliance Communications (the official telecom partner for Free Basics) to put the service on hold.
Facebook on its part has gone for an aggressive campaign, both online and offline, to promote Free Basics and ensure that its platform is not banned permanently. For Net Neutrality activists, zero-rating platforms are in violation of the principle as it restricts access to free, full Internet for users.
On Twitter too, there’s a serious debate unfolding around Free Basics and whether zero-rating platforms should be allowed in India. Here’s a look at some of the prominent voices around this Net Neutrality vs Free Basics debate.
Watch our video
Nikhil Pahwa, founder of news website MediaNama, has been campaigning for quite some time against zero-rating platforms in general and Net Neutrality. On Twitter, Pahwa points out that the problem with the zero-rating apps is that it gives telecos right to play kingmaker, and get into a direct relationship between a website and a user.
Pahwa also wrote a counter-blog to Mark Zuckerberg’s column in The Times of India questioning why Facebook is going with this restricted version of the web on Free Basics, rather than giving access to all websites.
He posted recently on Twitter, “Why hasn’t Facebook tried any model other than on which gives it a competitive advantage?”
Pahwa adds, “With zero rating, telcos insert themselves into a previously direct relationship between a site and user. Some sites made cheaper versus others. Said it earlier, saying it again. Problem with zero rating is that it gives telcos the right to play kingmaker through pricing. So Net Neutrality battle isn’t just about Facebook. It’s about telcos lobbying for differential pricing+revenue share from Internet companies.”
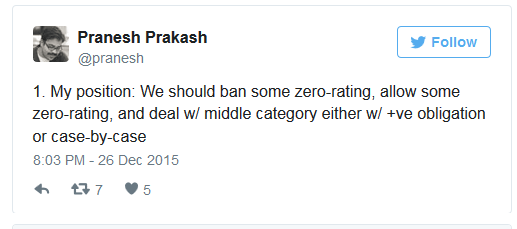
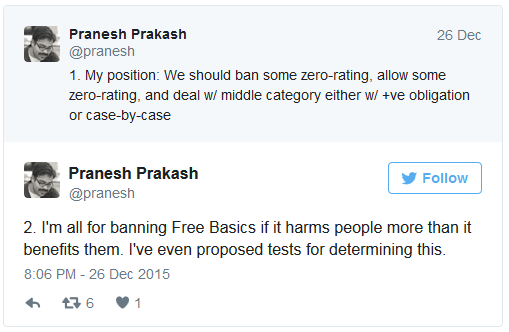
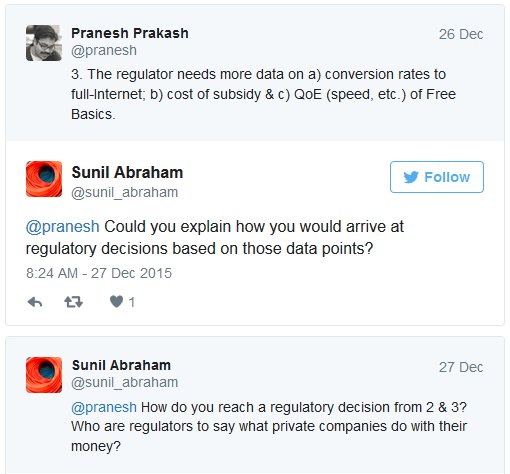
Pranesh Prakash, the director for policy at Centre for Internet and Society (CIS) in Bangalore, has said that a total ban might not be the ideal solution and one should look at the platforms on a case by case basis.
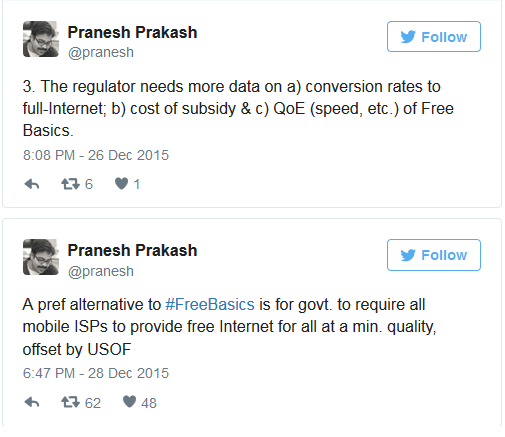
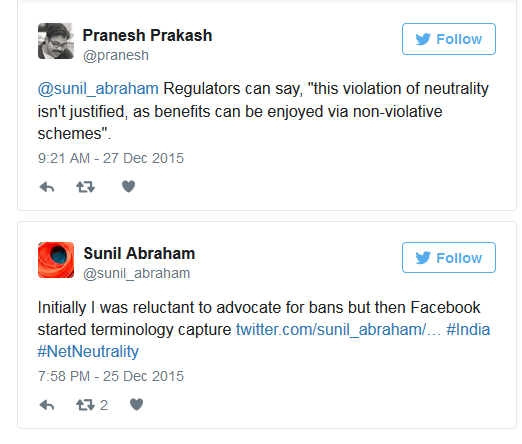
He writes on Twitter, “My position: We should ban some zero-rating, allow some zero-rating, and deal w/ middle category either w/ +ve obligation or case-by-case. I’m all for banning Free Basics if it harms people more than it benefits them. I’ve even proposed tests for determining this. The regulator needs more data on a) conversion rates to full-Internet; b) cost of subsidy & c) QoE (speed, etc.) of Free Basics.”
Check out Pranesh's tweets below
Sunil Abraham, executive director at Centre for Internet and Society, has however questioned Free Basics on Twitter. He also posted counter-points to Pranesh’s tweets about data on conversion being used to create regulations around zero-ratings. He’s also called for a ban on Free Basics.
Check out his tweets below
Take-away from the I&J Project Workshop at the UN Internet Governance Forum 2015
This was published on Internet & Jurisdiction website.
The 4-day conference convened over 2000 high-level participants from states, major global Internet companies, technical Internet operators, international organizations, civil society groups and academia.
Video
The workshop organized by the I&J Project discussed how to address the tension between the cross-border nature of the Internet and a patchwork of national jurisdictions by enabling multi-stakeholder cooperation. Sunil Abraham, the Director of CIS India, stressed the limits of traditional modes of inter-state legal cooperation on the Internet:
The MLAT system is completely broken […] both from the demand side and also from the supply side.
The US Cyber Coordinator of the State Department, Christopher Painter, stated the need to streamline procedures of Mutual Legal Assistance Treaties, but also highlighted the importance of pursuing in parallel more innovative approaches, such as the Internet & Jurisdiction process:
MLATS are not always the right answer. There are other answers between law enforcement channels in terms of joint investigations and there are also creative solutions that might take some of the burden off that MLAT process and I think that those are worthy of exploration.
Representing the Canadian ccTLD .ca, Mark Bull reflected upon how to develop such solutions to maintain the global nature of the Internet.
We are talking about incredibly complex issues here and I believe that complexity necessitates a multi-stakeholder process to identify solutions. And that is what I think the beauty of the Internet & Jurisdiction Project is. And it’s why because of the multi-stakeholder structure, that’s why we believe it is the best and the most effective form for discussing issues this complex.
Panelist Eileen Donahoe, the Director of Global Affairs at Human Rights Watch applauded the progress the Internet & Jurisdiction process made since 2012:
Let me say that the work of the I&J Project has been relentless and it is really important. This is one of the most complex spaces in Internet governance
The jurisdiction topic has become one of the most pressing Internet governance challenges, as I&J Project Director and Co-Founder Bertrand de La Chapelle pointed out:
There is a real element of urgency. The jurisdiction issue is at the core of many Internet governance problems. And it has been said in many workshops here in the IGF, but also outside of it. The problem is really getting worse. The jurisdiction problem is probably one of the biggest threats to the fabric of the Internet as we know it.
The objective of the workshop was to gather participants in the global Internet & Jurisdiction process from different stakeholder groups to report on progress and achievements. Furthermore, the workshop deepened the understanding of how to address jurisdictional tensions around the Internet and establish innovative legal cooperation mechanisms to prevent its fragmentation along national territorial boundaries.Council of Europe’s Elvana Thaci reminded participants of the importance to develop harmonized procedures across borders, as
Harmonization of substance is very difficult because the understanding of unlawfulness of content is very diverse.
Facebook’s Head of Policy Development, Matt Perault, talked about the need for appropriate procedures:
I am here because I believe the I&J Project is devoted to figuring out how to think about mechanisms for a race to the top on the issue of jurisdiction.
The pioneering Internet & Jurisdiction process has engaged more than 100 key entities around the world, creating a unique neutral space to build trust and catalyze operational solutions. As Will Hudson, Google’s Senior Advisor for International Policy, said:
We need to find solutions that work for all parties. It is one of the great strengths of the I&J Project, that it is looking at this challenge head on. We need to do things in this multi-stakeholder manner, and talk as a community because everyone has a stake in this and we cannot do this alone.
Participants
- ANNE CARBLANC, Head of Division, Directorate for Science, Technology and Industry, OECD
- BYRON HOLLAND, President and CEO, CIRA (Canadian ccTLD)
- CHRISTOPHER PAINTER, Coordinator for Cyber Issues, US Department of State
- EILEEN DONAHOE, Director Global Affairs, Human Rights Watch
- EVANA THACI, Administrator, Council of Europe
- MATT PERAULT, Head of Policy Development, Facebook
- SUNIL ABRAHAM, Executive Director, CIS India
- WILL HUDSEN, Senior Advisor for International Policy, Google
Tulu Wikipedia Tutorial
Tutorial video on starting with Tulu Wikipedia which is in incubation:
Tutorial video explaining how to start with Tulu Wikipedia which is in incubator:
Tutorial video explaining how to add new article to Tulu Wikipedia:
Tutorial video explaining how to type in Tulu Wikipedia:
Tutorial video explaining how to format articles in Tulu Wikipedia:
The people behind these videos:
- Prof. Vishwanatha Badikana for Script
- Lasya Shetty for Voice
- Abhishek Shetty, Saarang Community radio at St Aloysius College Mangaluru for Audio Recording
- Soundarya Shetty for Mixing and Editing
- Dr. U.B. Pavanaja for Conception, Direction, Mixing and Editing
2nd National Language Conference, Bhubaneswar
I spoke briefly about the issues with Odia being used massively on the Internet and gaining popular with Odia speaking netizens. Odia Wikimedia community and CIS-A2K's efforts has resulted growth in online Odia content. I also shared the potential projects that people could get involved and how collective effort will yield more diversification of the language and its use by today's generation.
The talk is available on Wikimedia Commons under a Creative Commons Share-Alike 4.0 license.
Video
Odia Wikisource workshop at New Delhi
Participants of the Odia Wikisource workshop (by Subhashish Panigrahi, Creative Commons Attribution-Share Alike 4.0 International license).
The seminar was on the Relevance of Bhagabat Tungi in the evolution of Odia language from Buddha era to digital age. After attending the event one of the participants Pankajmala Sarangi took great interest in Odia Wikisource which was then an incubator project. Since then she has digitized three books and is now proofreading Odia Bhagabata, an Odia language classic from the 14th century. Having the highest number of edits in Odia Wikisource, Ms. Sarangi took interest to build a community in Delhi. Another Odia Wikilibrarian Sitikantha Kheti also joined in to organise the first Odia Wikisource workshop in Delhi. These Wikimedians, a Delhi based group The Intellects and CIS-A2K collaboratively conducted a workshop.
The Intellect's president Debendra Rout addressed the participants and broadly spoke about the goal of the workshop and long term plans in Delhi. Both the Wikilibrarians shared their experience on Odia Wikisource. The workshop started with self introduction of the participants followed by screening of a documentary "Odia: Silalekharu Mobile".
Video
A handbook with details on the project, Odia input and keyboard layout was distributed among all. Subhashish Panigrahi demonstrated Odia input and the process of digitization of books on Wikisource. Plans for more workshops and digitization sprints were also charted out.
Privacy vs. Transparency: An Attempt at Resolving the Dichotomy
With feedback and inputs from Sumandro Chattapadhyay, Elonnai Hickok, Bhairav Acharya and Geetha Hariharan. I would like to apologize for not providing proper citation to Julian Assange when the first version of this blog entry was published. I would also like to thank Micah Sifry for drawing this failure to his attention. The blog post originally published by Omidyar Network can be read here. Also see http://newint.org/features/2015/01/01/privacy-transparency/
In other countries where privacy is not yet an explicit or implicit right, harm to the individual is mitigated using older confidentiality or secrecy law. After the Snowden affair, the rise of social media and the sharing economy, some corporations and governments would like us to believe that “privacy is dead”. Privacy should not and cannot be dead, because that would mean that security is also dead. This is indeed the most dangerous consequence of total surveillance as it is technically impossible to architect a secure information system without privacy as a precondition. And conversely, it is impossible to guarantee privacy without security as a precondition.
The right to transparency [also known as the right to information or access to information] – while unavailable in international law – is increasingly available in national law. Over the last twenty years this right has become encoded in national laws – and across the world it is being used to hold government accountable and to balance the power asymmetry between states and citizens. Independent and autonomous offices of transparency regulators have been established. Apart from increasing government transparency, corporations are also increasingly required to be transparent as part of generic or industry specific regulation in the public interest. For instance, India’s Companies Act, 2013, requires greater transparency from the private sector. Other areas of human endeavor such as science and development are also becoming increasingly transparent though here it is still left up to self-regulation and there isn’t as much established law. Within science and research more generally, the rise of open data accompanied the growth of the Open Access and citizen science movement.
So the question before us is: Are these two rights – the right to transparency and the right to privacy – compatible? Is it a zero-sum game? Do we have to sacrifice one right to enforce the other? Unfortunately, many privacy and transparency activists think this is the case and this has resulted in some conflict. I suggest that these rights are completely compatible when it comes to addressing the question of power. These rights do not have to be balanced against one another. There is no need to settle for a sub-optimal solution. Rather this is an optimization problem and the solution is as follows: privacy protections must be inversely proportionate to power and as Julian Assange says transparency requirements should be directly proportionate to power.[*]
In most privacy laws, the public interest is an exception to privacy. If public interest is being undermined, then an individual privacy can be infringed upon by the state, by researchers, by the media, etc. And in transparency law, privacy is the exception. If the privacy of an individual can be infringed, transparency is not required unless it is in the public interest. In other words, the “public interest” test allows us to use privacy law and transparency law to address power asymmetries rather than exacerbate them. What constitutes “public interest” is of course left to courts, privacy regulators, and transparency regulators to decide. Like privacy, there are many other exceptions in any given transparency regime including confidentiality and secrecy. Given uneven quality of case law there will be a temptation by the corrupt to conflate exceptions. Here the old common-law principle of “there is no confidence as to the disclosure of iniquity” – which prevents confidentiality law from being used to cover malfeasance or illegality – can be adopted in appropriate jurisdictions.
Around 10 years ago, the transparency movement gave birth to yet another movement – the open government data movement. The tension between privacy and transparency is most clearly seen in the open government data movement. The open government data movement in some parts of the world is dominated by ahistorical and apolitical technologists, and some of them seem intent on reinventing the wheel. In India, ever since the enactment of the Right to Information Act, 2003, 30 transparency activists are either killed, beaten or criminally intimidated every year. This is the statistic from media coverage alone. Many more silently suffer. RTI or transparency is without a doubt one of the most dangerous sectors within civil society that you could choose to work in. In contrast, not a single open data activist has ever been killed, beaten or criminally intimidated. I suspect this is because open data activists do not sufficiently challenge power hierarchies. Let us look a little bit closely at their work cycle. When a traditional transparency activist asks a question, that is usually enough to get them into trouble. When an open data activist publishes an answer [a dataset nicely scrubbed and machine readable, or a visualization, or a tool] they are often frustrated because nobody seems interested in using it. Often even the activist is unclear what the question is. This is because open data activist works where data is available. Open data activists are obsessed with big datasets, which are easier to find at the bottom of the pyramid. They contribute to growing surveillance practices [the nexus between Internet giants, states, and the security establishment] rather that focusing on sousveillance [citizen surveillance of the state, also referred to as citizen undersight or inverse surveillance]. They seem to be obsessed only with tools and technologies, rather than power asymmetries and injustices.
Finally, a case study to make my argument easier to understand – Aadhaar or UID, India’s ambitious centralized biometric identity and authentication management system. There are many serious issues with its centralized topology, proprietary technology, and dependence on biometrics as authentication factors – all of which I have written about in the past. In this article, I will explain how my optimization solution can be applied to the project to make it more effective in addressing its primary problem statement that corruption is a necessary outcome of power asymmetries in India.
In its current avatar – the Aadhaar project hopes to assign biometric-based identities to all citizens. The hope is that, by doing authentication in the last mile, corruption within India’s massive subsidy programmes will be reduced. This, in my view, might marginally reduce retail corruption at the bottom of the pyramid. It will do nothing to address wholesale corruption that occurs as subsidies travel from the top to the bottom of the pyramid. I have advocated over the last two years that we should abandon trying to issue biometric identities to all citizens, thereby making them more transparent to the state. Let us instead issue Aadhaar numbers to all politicians and bureaucrats and instead make the state more transparent to citizens. There is no public interest in reducing privacy for ordinary citizens – the powerless – but there are definitely huge public interest benefits to be secured by increasing transparency of politicians and bureaucrats, who are the powerful.
The Indian government has recently introduced a biometric-based attendance system for all bureaucrats and has created a portal that allows Indian citizens to track if their bureaucrats are arriving late or leaving early. This unfortunately is just bean counting [for being corrupt and being punctual are not mutually exclusive] and public access to the national portal was turned off because of legitimate protests from some of the bureaucrats. What bureaucrats do in office, who they meet, and which documents they process is more important than when they arrive at or depart from work. The increased transparency or reduced privacy was not contributing to the public interest.
Instead of first going after small-ticket corruption at the bottom of the pyramid, maximization of public interest requires us to focus on the top, for there is much greater ROI for the anti-corruption rupee. For example: constructing a digital signature based on audit trails that track all funds and subsidies as they move up and down the pyramid. These audit trails must be made public so that ordinary villagers can be supported by open data activists, journalists, social entrepreneurs, and traditional civil society in verification and course correction.
I hope open data activists, data scientists, and big data experts will draw inspiration from the giants of the transparency movement in India. I hope they will turn their attention to power, examine power asymmetries and then ask how the Aadhaar project can be leveraged to make India more rather than less equal.
Videos
|
Open Up? 2014: Risky Business: Transparency, Technology, Security, and Human Rights |
|---|
| Open Up? 2014: Data Collection and Sharing: Transparency and the Private Sector |
The videos can also be watched on Vimeo:
- Open Up? 2014: Risky Business: Transparency, Technology, Security, and Human Rights
- Open Up? 2014: Data Collection and Sharing: Transparency and the Private Sector
[*].http://prospect.org/article/real-significance-wikileaks “Transparency should be proportional to the power that one has.”
Read the presentation on Risky Business: Transparency, Technology, Security and Privacy made at the Pecha Kucha session here. (ODP File, 35 kb)
Disclaimer: The views, opinions, and positions expressed by the author(s) of this blog are theirs alone, and do not necessarily reflect the views, opinions, or positions of Omidyar Network. We make no representations as to accuracy, completeness, timeliness, suitability or validity of any information presented by individual authors of the blogs and will not be liable for any errors, omissions, or delays in this information or any losses, injuries or damages arising from its display or use.
Odia Littérateur Ramakrushna Nanda's 4 Books Now Available Under a Creative Commons License
His poetry “Ahe Dayamaya Biswa Bihari” has been sung in every school in Odisha. His work around Odia poetry, language and grammar, essays and encyclopaedia have been greatest resources for children for quite a few decades. CIS-A2K is honored to now bring four of his books under Creative Commons Share Alike (CC-by-SA 4.0) license:
- Biswa Parihay (Encyclopaedia)
- Lekhanira Pathasala (Grammar)
- Bhabi Dekhantu (Compilation of essays)
- Pausa Sandhyara Gapa (Compilation of stories)
The larger plans after this is to bring these books online on Odia Wikisource by scanning and digitizing them.
Video
| Ramakrushna Nanda's son Prabhat Kumar Nanda and daughter-in-law Anasuya Nanda, speak about the journey of the children's magazine the “Sansar” and way forward for Odia Wikisource for today's generation. |
Bharat Majhi Writings Now Available Under a Creative Commons License
Dr. Sailen Routray, Director, Kalinga Institute of Social Sciences (KISS) (also an institutional partner of CIS-A2K) played a key role in initiating a dialog with Mr. Majhi. Five of his books are now available under Creative Commons Share Alike 4.0 (CC-by-SA 4.0) license:
- Agadhu Duari
- Saralarekhaa
- Murtikaara
- Mahanagara Padya
- Highwayre Kuhudi
Bharat Majhi is a known name in Odia literary circle. His writings on societal structures in rural Odisha, the people, their life, aspiration and suffering have been critically acclaimed. These books also become the first Odia modern poetry books to be available under a CC-by-SA license and Mr. Majhi takes another leap of being the first Odia poet to release his literary work under CC-by-SA 4.0 license.
| Video |
|---|
In this video, Odia-language poet Bharat Majhi reciting a poem from his first book Agadhu Duari. He recently released 5 of his books under CC-by-SA 4.0 license by the efforts of Centre for Internet and Society's Access To Knowledge (CIS-A2K) and Kalinga Institute of Social Sciences (KISS).He also tells Subhashish Panigrahi about his dreams of poetry becoming a performing art coming true by it becoming more open. After other Odia author and poet Dr Jagannath Mohanty, Majhi is the first Odia poet to release poem online under CC-by-SA license and his poetry earn the title of the first Odia modern poetry under the same license.
Anvar v. Basheer and the New (Old) Law of Electronic Evidence
Read the original published by Law and Policy in India on September 25, 2014.
The case
On 18 September 2014, the Supreme Court of India delivered its judgment in the case of Anvar v. P. K. Basheer (Civil Appeal 4226 of 2012) to declare new law in respect of the evidentiary admissibility of the contents of electronic records. In doing so, Justice Kurian Joseph, speaking for a bench that included Chief Justice Rajendra M. Lodha and Justice Rohinton F. Nariman, overruled an earlier Supreme Court judgment in the 1995 case of State (NCT of Delhi) v. Navjot Sandhu alias Afsan Guru(2005) 11 SCC 600, popularly known as the Parliament Attacks case, and re-interpreted the application of sections 63, 65, and 65B of the Indian Evidence Act, 1872 (“Evidence Act”). To appreciate the implications of this judgment, a little background may be required.
The hearsay rule
The Evidence Act was drafted to codify principles of evidence in the common law. Traditionally, a fundamental rule of evidence is that oral evidence may be adduced to prove all facts, except documents, provided always that the oral evidence is direct. Oral evidence that is not direct is challenged by the hearsay rule and, unless it is saved by one of the exceptions to the hearsay rule, is inadmissible. In India, this principle is stated in sections 59 and 60 of the Evidence Act.
The hearsay rule is both fundamental and complex; a proper examination would require a lengthy excursus, but a simple explanation should suffice. In the landmark House of Lords decision in R v. Sharp [1988] 1 All ER 65, Lord Havers – the controversial prosecutor who went on to become the Lord Chancellor – described hearsay as “Any assertion other than one made by a person while giving oral evidence in the proceedings is inadmissible as evidence of any fact or opinion asserted.” This definition was applied by courts across the common law world. Section 114 of the United Kingdom’s (UK) Criminal Justice Act, 2003, which modernised British criminal procedure, uses simpler language: “a statement not made in oral evidence in the proceedings.”
Hearsay evidence is anything said outside a court by a person absent from a trial, but which is offered by a third person during the trial as evidence. The law excludes hearsay evidence because it is difficult or impossible to determine its truth and accuracy, which is usually achieved through cross examination. Since the person who made the statement and the person to whom it was said cannot be cross examined, a third person’s account of it is excluded. There are a few exceptions to this rule which need no explanation here; they may be left to another post.
Hearsay in documents
The hearsay rule is straightforward in relation to oral evidence but a little less so in relation to documents. As mentioned earlier, oral evidence cannot prove the contents of documents. This is because it would disturb the hearsay rule (since the document is absent, the truth or accuracy of the oral evidence cannot be compared to the document). In order to prove the contents of a document, either primary or secondary evidence must be offered.
Primary evidence of the contents of a document is the document itself [section 62 of the Evidence Act]. The process of compelling the production of a document in court is called ‘discovery’. Upon discovery, a document speaks for itself. Secondary evidence of the contents of a document is, amongst other things, certified copies of that document, copies made by mechanical processes that insure accuracy, and oral accounts of the contents by someone who has seen that document. Section 63 of the Evidence Act lists the secondary evidence that may prove the contents of a document.
Secondary evidence of documentary content is an attempt at reconciling the hearsay rule with the difficulties of securing the discovery of documents. There are many situations where the original document simply cannot be produced for a variety of reasons. Section 65 of the Evidence Act lists the situations in which the original document need not be produced; instead, the secondary evidence listed in section 63 can be used to prove its content. These situations arise when the original document (i) is in hostile possession; (ii) has been stipulated to by the prejudiced party; (iii) is lost or destroyed; (iv) cannot be easily moved, i.e. physically brought to the court; (v) is a public document of the state; (vi) can be proved by certified copies when the law narrowly permits; and (vii) is a collection of several documents.
Electronic documents
As documents came to be digitised, the hearsay rule faced several new challenges. While the law had mostly anticipated primary evidence (i.e. the original document itself) and had created special conditions for secondary evidence, increasing digitisation meant that more and more documents were electronically stored. As a result, the adduction of secondary evidence of documents increased. In the Anvar case, the Supreme Court noted that “there is a revolution in the way that evidence is produced before the court”.
In India before 2000, electronically stored information was treated as a document and secondary evidence of these electronic ‘documents’ was adduced through printed reproductions or transcripts, the authenticity of which was certified by a competent signatory. The signatory would identify her signature in court and be open to cross examination. This simple procedure met the conditions of both sections 63 and 65 of the Evidence Act. In this manner, Indian courts simply adapted a law drafted over one century earlier in Victorian England. However, as the pace and proliferation of technology expanded, and as the creation and storage of electronic information grew more complex, the law had to change more substantially.
New provisions for electronic records
To bridge the widening gap between law and technology, Parliament enacted the Information Technology Act, 2000 (“IT Act”) [official pdf here] that, amongst other things, created new definitions of “data”, “electronic record”, and “computer”. According to section 2(1)(t) of the IT Act, an electronic record is “data, record or data generated, image or sound stored, received or sent in an electronic form or micro film or computer generated micro fiche” (sic).
The IT Act amended section 59 of the Evidence Act to exclude electronic records from the probative force of oral evidence in the same manner as it excluded documents. This is the re-application of the documentary hearsay rule to electronic records. But, instead of submitting electronic records to the test of secondary evidence – which, for documents, is contained in sections 63 and 65, it inserted two new evidentiary rules for electronic records in the Evidence Act: section 65A and section 65B.
Section 65A of the Evidence Act creates special law for electronic evidence:
65A. Special provisions as to evidence relating to electronic record. – The contents of electronic records may be proved in accordance with the provisions of section 65B.
Section 65A of the Evidence Act performs the same function for electronic records that section 61 does for documentary evidence: it creates a separate procedure, distinct from the simple procedure for oral evidence, to ensure that the adduction of electronic records obeys the hearsay rule. It also secures other interests, such as the authenticity of the technology and the sanctity of the information retrieval procedure. But section 65A is further distinguished because it is a special law that stands apart from the documentary evidence procedure in sections 63 and 65.
Section 65B of the Evidence Act details this special procedure for adducing electronic records in evidence. Sub-section (2) lists the technological conditions upon which a duplicate copy (including a print-out) of an original electronic record may be used: (i) at the time of the creation of the electronic record, the computer that produced it must have been in regular use; (ii) the kind of information contained in the electronic record must have been regularly and ordinarily fed in to the computer; (iii) the computer was operating properly; and, (iv) the duplicate copy must be a reproduction of the original electronic record.
Sub-section (4) of section 65B of the Evidence Act lists additional non-technical qualifying conditions to establish the authenticity of electronic evidence. This provision requires the production of a certificate by a senior person who was responsible for the computer on which the electronic record was created, or is stored. The certificate must uniquely identify the original electronic record, describe the manner of its creation, describe the device that created it, and certify compliance with the technological conditions of sub-section (2) of section 65B.
Non-use of the special provisions
However, the special law and procedure created by sections 65A and 65B of the Evidence Act for electronic evidence were not used. Disappointingly, the cause of this non-use does not involve the law at all. India’s lower judiciary – the third tier of courts, where trials are undertaken – is vastly inept and technologically unsound. With exceptions, trial judges simply do not know the technology the IT Act comprehends. It is easier to carry on treating electronically stored information as documentary evidence. The reasons for this are systemic in India and, I suspect, endemic to poor developing countries. India’s justice system is decrepit and poorly funded. As long as the judicial system is not modernised, India’s trial judges will remain clueless about electronic evidence and the means of ensuring its authenticity.
By bypassing the special law on electronic records, Indian courts have continued to apply the provisions of sections 63 and 65 of the Evidence Act, which pertain to documents, to electronically stored information. Simply put, the courts have basically ignored sections 65A and 65B of the Evidence Act. Curiously, this state of affairs was blessed by the Supreme Court in Navjot Sandhu (the Parliament Attacks case), which was a particularly high-profile appeal from an emotive terrorism trial. On the question of the defence’s challenge to the authenticity and accuracy of certain call data records (CDRs) that the prosecution relied on, which were purported to be reproductions of the original electronically stored records, a Division Bench of Justice P. Venkatarama Reddi and Justice P. P. Naolekar held:
According to Section 63, secondary evidence means and includes, among other things, “copies made from the original by mechanical processes which in themselves ensure the accuracy of the copy, and copies compared with such copies”. Section 65 enables secondary evidence of the contents of a document to be adduced if the original is of such a nature as not to be easily movable. It is not in dispute that the information contained in the call records is stored in huge servers which cannot be easily moved and produced in the court. That is what the High Court has also observed at para 276. Hence, printouts taken from the computers/servers by mechanical process and certified by a responsible official of the service-providing company can be led into evidence through a witness who can identify the signatures of the certifying officer or otherwise speak to the facts based on his personal knowledge.
Flawed justice and political expediency in wiretap cases
The Supreme Court’s finding in Navjot Sandhu (quoted above) raised uncomfortable questions about the integrity of prosecution evidence, especially in trials related to national security or in high-profile cases of political importance. The state’s investigation of the Parliament Attacks was shoddy with respect to the interception of telephone calls. The Supreme Court’s judgment notes in prs. 148, 153, and 154 that the law and procedure of wiretaps was violated in several ways.
The Evidence Act mandates a special procedure for electronic records precisely because printed copies of such information are vulnerable to manipulation and abuse. This is what the veteran defence counsel, Mr. Shanti Bhushan, pointed out in Navjot Sandhu [see pr. 148] where there were discrepancies in the CDRs led in evidence by the prosecution. Despite these infirmities, which should have disqualified the evidence until the state demonstrated the absence of mala fide conduct, the Supreme Court stepped in to certify the secondary evidence itself, even though it is not competent to do so. The court did not compare the printed CDRs to the original electronic record. Essentially, the court allowed hearsay evidence. This is exactly the sort of situation that section 65B of the Evidence Act intended to avoid by requiring an impartial certificate under sub-section (4) that also speaks to compliance with the technical requirements of sub-section (2).
When the lack of a proper certificate regarding the authenticity and integrity of the evidence was pointed out, this is what the Supreme Court said in pr. 150:
Irrespective of the compliance of the requirements of Section 65B, which is a provision dealing with admissibility of electronic records, there is no bar to adducing secondary evidence under the other provisions of the Evidence Act, namely, Sections 63 and 65. It may be that the certificate containing the details in sub-section (4) of Section 65B is not filed in the instant case, but that does not mean that secondary evidence cannot be given even if the law permits such evidence to be given in the circumstances mentioned in the relevant provisions, namely, Sections 63 and 65.
In the years that followed, printed versions of CDRs were admitted in evidence if they were certified by an officer of the telephone company under sections 63 and 65 of the Evidence Act. The special procedure of section 65B was ignored. This has led to confusion and counter-claims. For instance, the 2011 case of Amar Singh v. Union of India (2011) 7 SCC 69 saw all the parties, including the state and the telephone company, dispute the authenticity of the printed transcripts of the CDRs, as well as the authorisation itself. Currently, in the case of Ratan Tata v. Union of India Writ Petition (Civil) 398 of 2010, a compact disc (CD) containing intercepted telephone calls was introduced in the Supreme Court without following any of the procedure contained in the Evidence Act.
Returning sanity to electronic record evidence, but at a price
In 2007, the United States District Court for Maryland handed down a landmark decision in Lorraine v. Markel American Insurance Company241 FRD 534 (D. Md. 2007) that clarified the rules regarding the discovery of electronically stored information. In American federal courts, the law of evidence is set out in the Federal Rules of Evidence. Lorraine held when electronically stored information is offered as evidence, the following tests need to be affirmed for it to be admissible: (i) is the information relevant; (ii) is it authentic; (iii) is it hearsay; (iv) is it original or, if it is a duplicate, is there admissible secondary evidence to support it; and (v) does its probative value survive the test of unfair prejudice?
In a small way, Anvar does for India what Lorraine did for US federal courts. In Anvar, the Supreme Court unequivocally returned Indian electronic evidence law to the special procedure created under section 65B of the Evidence Act. It did this by applying the maxim generalia specialibus non derogant (“the general does not detract from the specific”), which is a restatement of the principle lex specialis derogat legi generali (“special law repeals general law”). The Supreme Court held that the provisions of sections 65A and 65B of the Evidence Act created special law that overrides the general law of documentary evidence [see pr. 19]:
Proof of electronic record is a special provision introduced by the IT Act amending various provisions under the Evidence Act. The very caption of Section 65Aof the Evidence Act, read with Sections 59 and 65B is sufficient to hold that the special provisions on evidence relating to electronic record shall be governed by the procedure prescribed under Section 65B ofthe Evidence Act. That is a complete code in itself. Being a special law, the general law under Sections 63 and 65 has to yield.
By doing so, it disqualified oral evidence offered to attest secondary documentary evidence [see pr. 17]:
The Evidence Act does not contemplate or permit the proof of an electronic record by oral evidence if requirements under Section 65B of the Evidence Act are not complied with, as the law now stands in India.
The scope for oral evidence is offered later. Once electronic evidence is properly adduced according to section 65B of the Evidence Act, along with the certificate of sub-section (4), the other party may challenge the genuineness of the original electronic record. If the original electronic record is challenged, section 22A of the Evidence Act permits oral evidence as to its genuineness only. Note that section 22A disqualifies oral evidence as to the contents of the electronic record, only the genuineness of the record may be discussed. In this regard, relevant oral evidence as to the genuineness of the record can be offered by the Examiner of Electronic Evidence, an expert witness under section 45A of the Evidence Act who is appointed under section 79A of the IT Act.
While Anvar is welcome for straightening out the messy evidentiary practice regarding electronically stored information that Navjot Sandhuhad endorsed, it will extract a price from transparency and open government. The portion of Navjot Sandhu that was overruled dealt with wiretaps. In India, the wiretap empowerment is contained in section 5(2)of the Indian Telegraph Act, 1885 (“Telegraph Act”). The Telegraph Act is an inherited colonial law. Section 5(2) of the Telegraph Act was almost exactly duplicated thirteen years later by section 26 of the Indian Post Office Act, 1898. When the latter was referred to a Select Committee, P. Ananda Charlu – a prominent lawyer, Indian nationalist leader, and one of the original founders of the Indian National Congress in 1885 – criticised its lack of transparency, saying: “a strong and just government must not shrink from daylight”.
Wiretap leaks have become an important means of discovering governmental abuse of power, corruption, and illegality. For instance, the massive fraud enacted by under-selling 2G spectrum by A. Raja, the former telecom minister, supposedly India’s most expensive corruption scandal, caught the public’s imagination only after taped wiretapped conversations were leaked. Some of these conversations were recorded on to a CD and brought to the Supreme Court’s attention. There is no way that a whistle blower, or a person in possession of electronic evidence, can obtain the certification required by section 65B(4) of the Evidence Act without the state coming to know about it and, presumably, attempting to stop its publication.
Anvar neatly ties up electronic evidence, but it will probably discourage public interest disclosure of inquity.
Video
Re-Wiring Women's Rights Debates in the Digital Age
Website:
http://www.itforchange.net/ITfC_Course_Re-wiring_womens_rights/index.php/Agenda
Speakers List:
http://www.itforchange.net/ITfC_Course_Re-wiring_womens_rights/index.php/Session_speakers
Video
Region as Frame: Politics, Presence, Practice
Sunil Abraham is a speaker in the following panels:
- Governing Digital Spaces: Issues of Access, Privacy and Freedom (Friday, July 18, 2014, 11.00 - 12.30)
- UNESCO panel debate (Friday, July 18, 2014, 12.30 - 14.00)
- Special Session on Research Paths In and Outside of the Academy (Friday, July 18, 2014, 14.00 - 15.30)
Click to download the brochure of the event here (PDF 7.33 Mb)
Video
The Future of Cyber Governance
Global Governance Reform Initiative
The Global Governance Reform Initiative (GGRI) seeks to overcome the challenges of global governance in three important domains – cyberspace, oceans and migration – by improving the efficiency, effectiveness and legitimacy of collective actions undertaken by relevant stakeholders.
The current focus of the GGRI is the governance of cyberspace. How cyberspace is governed has significant implications for a range of critical issues, from national security to the protection of individuals’ rights and freedoms. Yet, the governance of cyberspace is highly contested. Tensions exist between those who favour private sector-led, decentralized forms of governance, and those who favour state-led, centralized forms of governance. There is, therefore, a pressing need for practicable policies which can help balance competing demands effectively.
The conference is a platform for 17 outstanding academics and professionals representing a range of countries and sectors to present papers addressing key issues related to the governance of cyberspace. The authors were selected through a competitive application process which sought to balance the candidates’ professional and geographic backgrounds in a manner that would maximize the quality and policy-relevance of the research.
During the conference, the participants will present their papers to a select group of seasoned experts on cyber governance. These experts will provide the participants with constructive feedback on their research findings and policy recommendations. The aim of the conference is to allow the participants to engage in a rigorous analysis of the selected governance challenges in order to craft practicable policy recommendations aimed at improving the governance of cyberspace. The authors of the best papers will be invited to present their work at the 2014 India Conference on Cyber Security and Cyber Governance, organized by the Observer Research Foundation, New Delhi.
The Hague Institute undertakes this project in collaboration with the Netherlands Ministry of Foreign Affairs, the Observer Research Foundation (New Delhi), and the Netherlands Institute of International Relations – Clingendael.
See the full details of the programme here.
Video
Document Actions




