Blog
Wherever you are, whatever you do
Privacy activists are up in arms again, at Facebook’s recent launch of a new location-based service called Places. But what’s the new issue here? For years, telecom operators have been able to roughly locate you by triangulating the signal strength between the three nearest cell towers. In India, geo-location is part of the call logs maintained by the operator. That is how the police was able to determine that Bangalore resident Sathish Gupta killed his wife Priyanka. He took her mobile with him during a jog with his friend and then faked a phone call as an alibi. He knew that the time-stamps on the call logs would corroborate his lies. But the location-data nailed him. So, in short, the state and telecom operators know where you are even if you don’t have a smartphone with GPS support.
For those who can afford it? GPS support provides greater accuracy and reliability, independent of telecom signal strength. The immediate and future benefits are huge. For parents, MyKidIsSafe.com, allows them to create a geo-fence and receive automatic notification when the child leaves the safety zone. In combination with RFID, businesses are able to provide their customers with accurate updates regarding status of deliveries. The Karnataka police is able to verify that the police inspector issuing the challan using a Blackberry for a traffic violation is not doing it from home. Seven hundred and fifty thousand gay men from 162 countries use a geo-social network called Grindr to find love. In the future, most car-pooling services will be GPS-enabled. Geo-location-based crowd-sourcing will be used to predict and avoid traffic jams by measuring the density and velocity of mobile phones on various routes.
Privacy advocates worry that after helping the police solve crimes and fight terrrorism, telecom companies retain the logs instead of deleting, anonymising or obfuscating them. Especially so in India, given the lack of privacy laws, telecom operators, web and mobile service providers could retain the logs for customer profiling or worse still, sell the raw data or analysis to third parties. Cyber-stalkers, child molesters and rapists benefit. Cat burglars will know when you are away and be able to clean out your house in a more relaxed fashion. Geo-surveillance by a state, obsessed with terrorism, will have negligible benefits while extracting a huge social cost and significantly undermining national security.
So why this particular outcry against the world’s most successful social networking website? There are three reasons that come immediately to mind. First, Facebook has a terrible record with privacy. In the last five years, the default settings have moved from one where no personal data was available for anonymous access to one with anonymous access to everything except birthday and contact information. And these are settings that affect the majority of the half a billion people who don’t bother changing default settings. So there is no guarantee that Facebook will not get more intrusive with its default geo-location privacy settings.
Second, a friend can geo-tag you without requiring you to approve or confirm this. Once you are geo-tagged, all your common friends will be notified through the friend-feed system. This is similar to the current system of photo sharing. A friend can upload a inappropriate photograph and tag you almost instantly all your work-mates who also happen to be your Facebook friends get a notification via the feed. Of course, you can always untag the photo, change the settings and defriend the culprit but by then the damage is usually done.
Third, the Facebook user-interface for privacy settings is notoriously complex and cumbersome. Many users will think that they have managed to bolt down the security settings when in fact their personal data will remain all up for grabs. The half a million third-party products available today on the Facebook platform only compounds this problem.
Read the original in the Indian Express
No UID Campaign in New Delhi - A Report
Since 2009, when the UID Bill was presented to the general public by Nandan Nilekani, the project has been characterized as a landmark initiative that will transform India, bring in good governance, and provide relief and basic services for the poor. The scheme is rapidly being put in place; the draft Bill has been put before the Parliament of India and the resident numbers and data have been collected.
The UID proposes to take the finger prints and iris scans of every resident of India for authentication of each individual. J. T. D'Souza, an expert in free software technology exposed the flaws of the entire technical aspect of the UID project. He presented the risks and loopholes that technology such as iris and fingerprint scanners pose, and the risks in using a biometric system as a form of identification system. Contrary to the claim of the UID authority, that a scheme based on biometrics is foolproof, he explained how fingerprints are not unchanging, both fingerprints and iris scans can be easily spoofed (with a budget of only $10), and there are many ways in which the technology can break, be inconsistent, or be inaccurate.
From a human rights perspective the lack of democracy in the entire project was stressed. Usha Ramanathan reiterated the fact that no white paper was issued, the Bill has not gone through the Parliament and yet citizens’ data is being collected, citizens were given only a two week period to comment on the Bill, and in practice the UID number will not be voluntary for individuals.
The UID authority has posited the scheme as bringing benefits to the poor, plugging leakages in the Public Distribution System and the Mahatma Gandhi National Rural Employment Guarantee Scheme (MGNREGS), as well as enabling inclusive growth by providing each citizen with a verifiable and portable identity. These claims were debunked. An identity number will not fix the waste of grain that takes place every day, the portability of the number raises new problems of accessibility and distribution of resources, and the MGNREGS system is already working to be financially inclusive with a majority of its members already having a bank account.
In response to hearing the presentations of the speakers and the comments by the audience, senior Member of Parliament of the Revolutionary Socialist Party of India (RSP), Abani Roy called for the launching of a massive campaign to resist this expensive and dangerous project through which several companies will gain massive contracts from the public exchequer.
The campaigners for No UID plans to hold further meetings across the country and lobby Parliamentarians in the coming months.
For more information contact: Mathew Thomas (Bangalore) [email protected], Elonnai Hickok (Bangalore) [email protected] , Sajan Venniyoor (Delhi): +91-9818453483 - Bobby Kunhu (Delhi): +91-9654510398
Summary of UID Public Meeting, August 25 2010
The Meeting and Project
On August 25, 2010 in Delhi, a public meeting was organized by civil society groups from Mumbai, Bangalore, and Delhi to discuss and answer questions surrounding the UID, and to present the concerns of the public to members of parliament. The meeting was successful, with many important concerns raised by both the speakers and the audience. An action plan was developed, and MPs were able to come, listen, and share their opinions.
The Project
The UID is a project that is supported by the government of India, and is led by Nandan Nilekani, the former CEO of Infosys. The project is being presented as a cure to the PDS system, as a mechanism to bring benefits to the poor, and as a project that will make India an inclusive society by providing every citizen with a verifiable identity. The draft National Identification Authority of India Bill will be placed before the Lok Sabha in the current session. If the Bill is approved by parliament, the official implementation of the Bill will take place in Winter 2010 -2011.
Technological Flaws
Speaking first, Jude D'Souza, a free software professional, presented the entire technical aspect of the UID scheme. He became involved with the UID project through his work on biometrics, and he expressed shock that the UID scheme would rely on a deeply flawed system such as biometrics. Flaws in such a system include -- but are not limited to -- duplication, verification problems, and the lack of infrastructure needed to collect biometrics properly. Explaining in detail how fingerprint and iris scanners work, he showed how both are actually very simple technologies. An iris scanner is essentially a camera coupled with auto-focusing. The camera focuses on one’s eye, takes a snapshot, and then divides the eye into concentric segments, conducts a type of numbering scheme for each segment, and then generates a number that represents the pattern. A fingerprint scanner works in a similar manner. First a picture is taken of your finger-print, the system then generates an inverted image of the finger, with darker areas representing more reflected light and lighter areas representing less reflected light. The image is then compared against the stored fingerprint. Both technologies are easily spoofed. Iris scanners cannot detect contact lenses, and a scientist in Japan found that fingerprint scanners can be “tricked” easily with materials costing under 10 dollars. D'Souza explained how all identification systems go through an enrollment and authentication process which includes: the capturing of the image, the processing of the image, extraction of features, the creation of a template, encryption, duplication and storage of the information. If a step in either the enrollment or authentication process goes wrong, the whole process is brought back to square one – manual recording of information. For instance, if a fingerprint is swiped, and the machine cannot read it because it has changed with age, or the machine is malfunctioning, or the fingerprint is logged with water (something that is not uncommon in India) – the person would either have to re-enroll, and then re-verify who they are manually. If this scenario applies to, say, someone coming into a hospital, the consequences of his/her fingerprints not being read are grave.
Another concern is the compromising of the system. Bogus templates can easily be created and switched with the real template, key duplication is possible, or the system could be hacked and a virus introduced. In general, it is dangerous when any database containing personal information is compromised; a database that contains biometrics is twice as dangerous. D'Souza closed his presentation by making the point that biometrics cannot be withdrawn – if your password (biometrics) is compromised, you are still stuck with it for life. Once you leave your footprint through biometrics, it is irrevocable.
Civil Rights
The second speaker of the day was Usha Ramanathan, an internationally recognized expert on law and poverty, who spoke on human rights and the UID. From the beginning of her presentation she challenged the audience to think deeply about the question “Why would the government want to put this project in place?” She brought to the table many points about how the project violates human rights, including the fact that no type of feasibility study has been done on the technology or the financial cost of the project; a white paper was never issued at the genesis of the project; and Nandan Nilekani and other members of the authority refused directly to answer the concerns brought forth to them when they were approached. To her, the corporatization of the project is also very clear. From the marketing of the scheme, to the implementation of the scheme, to the fact that the convergence of databases will allow business and corporate powers to network using individual’s data that they obtain from the database – the issuance of a Unique Identification Number provides opportunities for huge profits to be made by corporations and the government. What makes the consequences of a UID number even more powerful is the fact that even though the Authority says that the number is voluntary, businesses, shop owners, banks and hospitals have the ability to deny access if one does not have number. In this way, the number is at least de-facto compulsory. This number also threatens violations to an individual’s privacy.
Benefits to the Poor
When analyzing the benefits to the poor that the number promises, the picture begins to look less and less beneficial. The Authority has been stressing the benefit of the portability of a Unique Identification Number. The positive aspects of having a portable ID stem from the idea that a person living in one village could be traveling and would still be able to collect his or her rations from the Free Trade Shop in the location he or she is visiting. No longer would people have to return home to collect their rations. Though this seems to be a useful benefit indeed, problems begin to arise if the Free Trade Shop in that village does not have enough grain in stock to provide for the unexpected visitor or if the biometric data malfunction. Other complications that the poor might have with a unique ID number is that to enroll you must know your address and name, and be able to spell them correctly. When looking at if the UID will plug the leakages of the PDS system, it will perhaps make the delivery of grain more efficient – theoretically it could stop the use of fake ration cards etc, but it does not stop the waste of grain, and at the end of the day – it still only a number, it does not regulate the person authenticating the individual and distributing the grain. Other difficulties the rural populations face are power outages: what if the power goes out – no one can be authenticated, what if the notice that benefits are available are electronically transmitted and do not arrive? What if data are lost during power outages?
Response of the Audience
After lunch the floor was opened up to discussion about steps that need to be taken in the future. It was determined that academics need to be consulted, the NO UID campaign needs to be presented in a language that everyone can understand and relate to, more political leaders need to be contacted, volunteers from Universities need to be recruited, petitions need to be written, and emails and contact information shared for open communication amongst each other. Another response from the audience was that privacy is an issue for the elite – the poor are concerned with surviving day to day. What is interesting, though, is how untrue that is. The issuance of a UID number brings privacy of the poor into the limelight. Privacy is a question of a person’s ability to control individual information, to know how it is being used, and by whom. A Unique Identification Number given to the poor suddenly places all of his or her personal data on the grid. It places it into networks, business databases, and governmental data banks. The current lack of data protection and lack of control an individual has over these data under the scheme creates a privacy crisis for anyone who has a number. And, given the ability to deny services to someone who does not have a number, it creates a crisis for those who opt out as well.
The Opinion of the MPs
Many of the MPs were unable to come, but the two who did were in opposition to the UID. MP Syed Azeez Pasha (CPI) commented on the need for a campaign to have started earlier, while Senior Member of Parliament from the Revolutionary Socialist Party of India (RSP) Abani Roy called for the launching of a massive campaign to resist this expensive and dangerous project through which several companies will gain massive contracts from the public exchequer.
Conclusion
As the UID project continues to unroll, it seems that that Nandan Nilekani has imagined a new India – one that looks to technology as its solution to its political and social problems. If this is the case, a UID number that will work to shift the entire population onto a digital database could just be the beginning of many other changes to come. Indian citizens should carefully consider if this is the India that they have imagined.
Resources from the Meeting
Beyond Access as Inclusion
One of the most attractive characteristics of the Internet – and perhaps also one of the most debated ones – is its empowering, democratising potential. In expositions in favour of access to the Internet for all, this potential certainly often plays a central role: as the Internet can help us to make our societies more open, more inclusive, and more democratic, everybody should be able to reap the fruits of this technology, it is argued. In other words, in debates on access to the Internet, most of us take as our starting point the desirability of such access, for the above reasons. But how justified is such a stance? Is an Internet-induced democratic transformation of our societies what is actually happening on the ground?
I would like to move away, in this blog post, from the more traditional approaches to the issue of access, where debates mostly veer towards issues of infrastructure (spectrum, backbones, last mile connectivity, …) or, under the banner of “diversity”, towards the needs of specific, disadvantaged communities (especially linguistic minorities and the disabled). To remind us more sharply of the issues at stake and of the wide range of human rights that need our active attention to make our dreams a reality, I would like to take a step back and to ask two fundamental questions regarding access: why might access be important? And what do we actually have access to?
Let me start, then, by exploring the first question: why, actually, is Internet access important? In his canonical work on the information age, and especially in the first volume on the rise of the network society, Manuel Castells (2000) has perhaps provided the most elaborate and erudite description of the ways in which new technologies are restructuring our societies and our lives. We are all all too familiar with the many and deep-seated ways in which the Internet changes the manner in which we learn, play, court, pay, do business, maintain relationships, dream, campaign. And yet, the exact nature of the divide created by the unequal distribution of technical infrastructure and access, despite being so very real, receives relatively little attention: this divide is not simply one of opportunities, it is crucially one of power. If in traditional Marxist analysis the problem was that the oppressed did not have access to the means of production, today, one could well argue, the problem is that they do not have access to the means of communication and information.
Indeed, the Internet is not something that is simply happening to us: there are people who are responsible for these new evolutions. And so it becomes important to ask: who is shaping the Internet? Who is creating this new world? Let us, by way of example, consider some figures relating to Internet use in India. So often hailed as the emerging IT superpower of the world, there are, by the end of 2009, according to official government figures, in this country of 1 billion 250 million people slightly more than 15 million Internet connections. Of these, only slightly more than half, or almost 8 million, are broadband connections – the rest are still dial-up ones (TRAI 2010). The number of Internet users is of course higher – one survey estimates that there are between 52 million and 71 million Internet users in urban areas, where the bulk of users is still located (IAMAI 2010). But while this is a considerable number, it remains a fraction of the population in a country so big. What these figures put in stark relief, then, is that the poor and marginalised are not so much excluded from the information society (in fact, many have to bear the consequences of new evolutions made possible by it in rather excruciating fashion), but rather, that they are fundamentally excluded from shaping the critical ways in which our societies are being transformed.
To have at least the possibility to access the Internet is, then, of central significance in this context for the possibility of participation it signals in the restructuring of our societies at the community, national and global level, and this in two ways: in the creation of visions of where our societies should be going, and in the actual shaping of the architecture of our societies in the information age.
If we agree that access attains great significance in this sense, then a second question poses itself, and that is: in practice, what exactly are we getting access to? This query should be of concern to all of us. With the increasing corporatisation of the Internet and the seemingly growing urges of governments on all continents to survey and control their citizens, new challenges are thrown up of how to nurture the growth of open, inclusive, democratic societies, that all of us are required to take an interest in.
Yet it is in the case of poor and marginalised people that the challenges are most pronounced. Efforts to include them in the information society are disproportionately legitimised on the basis of the contribution these can make to improving their livelihoods. Initiatives, often using mobile technology, that allow farmers to get immediate information about the market prices of the produce they are intending to sell, are perhaps the most well-known and oft-cited examples in this category. Other efforts aim to improve the information flow from the government to citizens: India has set up an ambitious network of Common Service Centres, for example, that aim to greatly facilitate the access of citizens to particular government services, such as obtaining birth or caste certificates – and going by first indications, this also seems to be succeeding in practice. Only rarely, however, do initiatives to “include” the poor in the information society address them as holistic beings who do not only have economic lives, but political, emotional, creative and intellectual existences as well. This is not to say that economic issues are not of importance. But by highlighting only this aspect of poor people's lives, we promote a highly impoverished understanding of their existences.
The focus on a limited aspect of the poor's identity - important as that aspect may be - has a function, however: it makes it possible to hide from view the extremely restrictive terms on which poor people are currently being integrated into the information society. Even initiatives such as the Common Service Centres are in fact based on a public-private-partnership model that explicitly aims to “align [..] social and commercial goals” (DIT 2006: 1), and in effect subordinates government service design to the requirements of the CSC business model (Singh 2008). The point is not simply that we need strong privacy and data protection policies in such a context – although we clearly do. There is a larger issue here, which is that efforts to include the poor in the information society, in the present circumstances, really seem to simply integrate them more closely into a capitalist system over which they have little control, or to submit them to ever greater levels of government and corporate surveillance. Their own capacity to give shape to the system in which they are “included”, despite the oft-heralded capacities of the Internet to allow greater democratic participation and to turn everybody into a producer and distributor, as well as a consumer, remains extremely limited.
Such tendencies have not gone unnoticed. For example, unlike in many other parts of the world, social movements in India fighting against dams, special economic zones or mining operations in forest areas - all initiatives that lead to large-scale displacement – have not embraced technology as enthusiastically as one might have expected. There are various reasons for this. Within Indian nationalism, there have always been strands deeply critical of technology, with Gandhi perhaps their most illustrious proponent. But for many activists, technology often also already comes with an ideological baggage: an application such as Twitter, for example, in so many of its aspects is clearly manufactured by others, for others, drawing on value sets that activists often in many ways are reluctant to embrace. And such connotations only gain greater validity because of the intimate connections that exist in India between the IT boom and neoliberalism: technology has great responsibility for many of the trends and practices these activists are fighting against. While the Internet might have made possible many new publics, most movements do not – as movements – recognise these publics as their own (Kovacs, forthcoming).
To some extent, these are of course questions of the extent of access that people are granted. But they also raise the important issue of the value structure of the Internet. Efforts at inclusion always take for granted a standard that is already set. But what if the needs and desires of the many billions that still need to be included are not served by the Internet as it exists? What if, for it to really work for them, they need to be able to make the Internet a different place than the one we know today? While it is obvious that different people will give different answers in different parts of the world, such debates are complicated tremendously by the fact that it is no longer sufficient to reach a national consensus on the issues under discussion, as was the case in earlier eras. The global nature of the Internet's infrastructure requires that the possibility of differing opinions, too, needs to be facilitated at the global level. What are the consequences of this for the development of democracy?
For access to the Internet to be substantively
meaningful from a human rights perspective in the information age, it
is crucial, then, that at a minimum, the openness of the Internet is
ensured at all levels. Of course, openness can be considered a value
in itself. But perhaps more importantly, at the moment, it is the
only way in which the possibility of a variety of answers to the
pressing question of what shape our societies should take in the
information age can emerge. Open standards and the portability of
data, for example, are crucial if societies are to continue to decide
on the role corporations should play in their public life, rather
than having corporations de facto rule the roost. Similarly,
under no circumstances should anyone be cut off from the Internet, if
people are to participate in the public life of the societies of
which they are members. And these are not just concerns for
developing countries: if recent incidents from France to Australia
are anything to go by, new possibilities facilitated by the Internet
have, at least at the level of governments, formed the impetus for a
clear shift to the right of the political spectrum in many developed
countries. In the developed world, too, the questions of access and
what it allows for are thus issues that should concern all. In the
information age, human rights will only be respected if such respect
is already inscribed in the very architecture of its central
infrastructure itself.
List of References
Castells, Manuel (2000). The Rise of the Network Society, 2nd edition. Oxford: Blackwell.
Department of Information Technology (DIT) (2006). Guidelines for the Implementation of Common Services Centers (CSCs) Scheme in States. New Delhi: Department of Information Technology, Government of India.
Internet and Mobile Association of India (IAMAI) (2010). I-Cube 2009-2010: Internet in India. Mumbai: Internet and Mobile Association of India.
Kovacs, Anja (forthcoming). Inquilab 2.0? Reflections on Online Activism in India (working title). Bangalore: Centre for Internet and Society.
Singh, Parminder Jeet (2008). Recommendations for a Meaningful and Successful e-Governance in India. IT for Change Policy Brief, IT for Change, Bangalore.
Telecom Regulatory Auhority of India (TRAI) (2010). The Indian Telecom Services Performance Indicators, October-December 2009. New Delhi: Telecom Regulatory Auhority of India.
Moldova Online: An Interview with Victor Diaconu
SR: After the 2009 elections, there was some talk of reform in Moldova and greater transparency, but now one also hears contradictory reports of increasing authoritarian tendencies. Is this ambivalence evident in the way the internet is regulated and used here?
VD: I would not say the tendencies are authoritarian. The constitution says that the President should be voted in by a majority of 61 out of 101 members of the Parliament. If not, Parliament should be dissolved and re-elected. Well, this should happen twice a year at the most, and as such, after a second failed attempt to vote the President the authority of the Parliament and Government is somewhat questionable. The current Parliament has tried to change the rules of voting in the President - to make it by popular vote, for instance, but this is met with resistance from the Communist Party.
As to transparency - I would say it has improved. Though, one should not expect too many changes from a Government with questionable authority and with so many systemic flaws inherited from the previous government. At the moment we've got a coalition government. As such, there are frictions and these are indeed visible. This gives a sense of comfort and truthfulness since it is normal to have frictions in any human endeavour. While the communist party was ruling - everything was "nice and dandy" both in media and in political affairs and one could not get anything but "fake" - fake news, fake results, fake improvements.
Internet control and filtering do not happen. In fact, we did have a "small revolt" on April 7, 2009, when it seemed the communist party had tried to steal the vote for the parliament. At that moment a few .md sites were blocked by the national Telecom operator, but most other sites were still available. In fact, news about the event was best available on twitter (might still be available under "pman" tags). There also were a few attempts to stifle free speech when authorities requested names/IP addresses of commenters on some forums. However, this is no longer conceivable ...
SR: Given that the press and television are largely in the hands of the state and criticism of the state is considered defamation (and leads to the arrest of press people), does the internet play a special role as a space for alternative media and political blogs? Are these prevalent and influential?
VD: Yes, national TV is largely state owned and it was worse before the change in power. Now it seems to have improved. There are a series of smaller TV stations but these have reduced coverage - mostly in bigger cities. I understand that they've started rolling out IP TV with packages of 50+ TV channels - local and international. The national Telecoms operator provides very good Internet coverage. Dial-up Internet at reasonable prices is available everywhere in the country. Broadband availability even in rural areas is very good. And it's not too expensive. As to the role of Internet - indeed its influence is increasing. A series of media portals are frequented by many, including me. http://unimedia.md/; http://m.protv.md/; http://jurnaltv.md/; http://forum.md/to mention a few. The news here is conveyed tersely but I do my own editorializing if need be. Also, I can read the comments if I want to get a feeling about how others feel about some specific event.
SR: Can you tell us about some of the popular bloggers and blogging platforms in Moldova? Live Journal is popular in Russia; can the same be said of Moldova?
VD: I'm not aware of any significant blogger, more so, political blogger. I'd say we still need to wait for someone whose commentary is mature enough for people to care about him or her... As to the platform - those blogging attempts that I've seen were indeed on major blogging portals like Live Journal.
SR: What can you tell us about the presence of social media in Moldova? Does Moldova prefer its own versions of global digital platforms, or are FB, My Space, Twitter popular here? What is the role of the diaspora in this space?
VD: Global platforms are widely used. There are a few Russian popular platforms in wide use too, such as odnoklassniki.ru. We have up to 1 million Moldovans working in European countries, Russia and other places, since the pay is significantly higher over there. These people left a few years back and most of them intend to return. And they, indeed, rely on the available platforms to relate back to relatives and friends.
SR: Lastly, can you tell us about the linguistic landscape of Moldovan new media; I imagine the most widely used language on the internet is Moldovan/Romanian. Is Russian prevalent or is new media here a platform to assert their exclusive Moldovan identity?
VD: The rules for language are that media should have at least 60-70% of content in "state" language and the law was often changed so that sometimes 'state language’ included Russian too. In fact, in Moldova we are very comfortable with the Russian language, at least those a bit older (30+ years) since we were supposed to speak it well in the Soviet era.
SR (with many thanks to Victor Diaconu and Sunil Abraham)
About Sudha Rajagopalan
Sudha Rajagopalan is the deputy editor of Digital Icons: Studies in Russian, Eurasian and Central European New Media and co-blogger at Russian Cyberspace. Sudha is also a Research Affiliate with the Media Studies Group at the University of Utrecht in the Netherlands. Her current research is on audience and fan communities on Runet (the Russian-language internet), with a special interest in identity, performativity and affect in online practices. Sudha obtained her PhD in Russian History from Indiana University, Bloomington (2005). She is the author of 'Leave Disco Dancer Alone: Indian Cinema and Soviet Movie-going after Stalin,' Yoda Press, 2008 ('Indian Films in Soviet Cinemas: The Culture of Movie-going after Stalin,' Indiana University Press, 2009).
Presentation of the UID project by Ashok Dalwai – A Report
Privacy Concerns in Whole Body Imaging: A Few Questions
What is Whole Body Imaging?
Whole Body Imaging is an umbrella term that includes various technologies that can produce images of the body without the cover of clothing. The purpose of WBI technology is to screen travellers visually in order to detect weapons, explosives and other threat items more thoroughly, without the cover of clothing. Examples include: Ultrasonic Imaging Technology, Superconducting Quantum Interference Device, T-ray Technology, Millimeter Wave Technology, MM-wave Technology, and X-ray Scanning Systems. The two main types of scanners used for security screening are: Millimeter Wave and Backscatter machines. The Millimeter Wave machines send radio waves over a person and produce a three-dimensional image by measuring the energy reflected back. Backscatter machines use low-level x-rays to create a two-dimensional image of the body. The machines show what a physical pat-down would potentially reveal as well, but what a metal detector would not find – for example, they will detect items such as chemical explosives and non-metallic weapons.
How are These Technologies Being Used - Two News Items to Ponder:
News Item One
In 2009-2010 a Nigerian attempted to blow up a Detroit-bound aircraft in the United States. In response to this attempt, in addition to the heightened security concerns in light of 9/11, the United States has pushed for the greater use of full-body scanners among other initiatives. The hope is that the scanners will bring a heightened level of security and stop potential attacks from occurring in the future.
Also, in response to the attempted attack on the U.S, the Mumbai Terrorist attacks, and many other incidents, India has likewise considered the implementation of full-body scanners in airports. According to an article published on 2 January 2010 in The Times of India, soon after the incident in the United States, the Indian Intelligence Bureau submitted a comprehensive airport review that spoke about the need for full-body scanners. On 6 July 2010, the Times of India issued a story on how full-body scanners will not be used at the two Dubai airports. The story went on to explain in detail how the airports in Dubai have decided against the use of full-body scanners as a security measure, because they ‘contradict’ Islam, and because the government respects the privacy of individuals and their personal freedom. The head of the Dubai police department was quoted as saying “The scanners will be replaced with other inspection systems that reserve travelers' privacy.” At airports that utilize the scanners, not everyone is required to go through a full-body scanner at the security checkpoint (I myself have never been in one), but instead the authority will randomly select persons to be scanned. An individual has the option to opt out of the scan, but if they choose to do so, they must undergo a thorough body pat-down search. During the scan, the officer zoomed over parts of the image for a better look, if any portion of the image appears suspicious. Once a scan is completed, the passenger waits while the scan is sent to and reviewed by another officer elsewhere. The officers are connected by wireless headsets. If no problems are found, the image is supposed to be erased. If a problem is found, the officer tells the checkpoint agent where the problem is, and the image is retained until the issue is resolved, and then it is erased. The wireless transmission of the image by a computer to another officer for analysis is a built-in safeguard, because the agent who sees the image never sees the passenger and the officer who sees the passenger never sees the image.
Despite this, the machines are controversial because they generate images of a passengers' entire body, which raises concerns as to the possible privacy violations that could occur. Besides the physical invasion that the scanners pose, privacy concerns have centered on the fact that the actual implementation of the procedures for retention and deletion of images is unclear. For instance, in Florida, images from a scanner at a courthouse were found to have been leaked and circulated. In 2008, the US Department of Homeland Security did a report on the privacy of whole-body imaging and its compliance with the Fair Information Practice Principles. Among other safeguards, the report concluded that the image does not provide enough details for personal identification, the image is not retained, and the machine could in fact work to protect the privacy of an individual by sparing the person the indignity of a pat-down.
News Item Two
In October this year, Fox News came out with a story that told how the use of x-ray scanners, similar to the ones used in airports, are now being placed in vans that can see into the inside of the vehicles around them. The vans are used to detect car bombs, drugs, radioactivity and people hiding. The vans have been used at major crowd events like the Super Bowl. According to the Department of Homeland Security, the vans have led to the seizure of 89,000 pounds of narcotics and $4 million worth of currency. In vans the technology used is the backscatter x-ray machine. The cars are more controversial than the scanners at airports, because it is not possible to obtain consent from the target vehicle, and a person in a car does not have the option to opt out for a thorough car search. Furthermore, images are not sent to another authority to be analyzed, but are instead analyzed by the authority in the car. Reactions to the vans have been mixed. Some worry about the invasion to privacy that the vans pose, the lack of consent that an individual gives to having his car scanned, and the fact that these scans are conducted without a warrant. Others believe that the security the vans can provide far outweighs the threats to privacy. In airports, if evidence is found against a person, it is clear that airport authorities have the right to stop the individual and proceed further. This right is given by an individual‘s having chosen to do business at the airport, but a person who is traveling on a public street or highway has not chosen to do business there. It is much more difficult to conclude that by driving on a road an individual has agreed to the possible scanning of his/her car.
Questions at the Heart of the WBI Debate:
Whole Body Imaging raises both simple and difficult questions about the dilemma of security vs. privacy, and privacy as a right vs. privacy as protection. If privacy is seen as a constitutional right, as it is in the European Union under the Convention on Human Rights, then Whole Body Imaging raises questions about the human body — its legal and moral status, its value, its meaning, and the dignity that is supposed to be upheld by the virtue of an individual’s privacy being a right. If Whole Body Imaging threatens the dignity of an individual, is it correct to permit the procedure at airports and allow vans with x-ray machines to roam the streets? This question segues into a deeper question about security over privacy. The security appeal of WBI technology is its pro-active ability to provide intelligence information about potential threats before anything actually happens. Does the security that these machines bring trump the right to privacy that they could be violating? Isn’t this particularly true given that airport scanning is of only a randomly-selected portion of travelers? Is the loss of privacy that occurs proportional to the need and the means met? What is the purpose of security in these contexts? All privacy legislation must work to strike a balance between security and privacy. Typically, in terms of governments and security, restrictions are placed on the amount of unregulated monitoring that governments can do through judicial oversight. Warrantless monitoring is typically permitted only in the case of declared national emergencies. Should WBI technology be subject to the same restrictions as, say, wiretapping? or would this defeat the purpose of the technology, given that the purpose is to prevent an event that could lead into a declared national emergency. Furthermore, how can legislation and policy, which has traditionally been crafted to be reactive in nature, adequately respond to the pro-active nature of the technology and its attempt to stop a crime before it happens?
How Have Other Countries Responded to Whole Body Imaging and How Should India Respond?
Countries around the world have responded differently to the use of whole body imaging. In the EU, full-body scanners are used only in the UK, and their use there is being protested, with the Human Rights Charter being used to argue that full-body imaging lowers human dignity and violates a person’s right to privacy. In EU countries such as Germany, there has been a strong backlash against full-body image scanners by calling them ‘Naked Scanners’. Nonetheless, according to an ABC report, in 2009 the Netherlands announced that scanners would be used for all flights heading from Amsterdam's airport to the United States.
In the US, where scanners are being used, EPIC is suing the TSA on the grounds that the TSA should have enacted formal regulations to govern their use. It argues that the body scanners violate the Fourth Amendment, which prohibits unreasonable searches and seizures. Canada has purchased 44 new imaging scanners but has suggested using image algorithms to protect the individuals’ privacy even further. A Nigerian leader also pledged to use full-body scanners.
Though India has not implemented the use of WBI technology, it has considered doing so twice, in 2008 and again in 2010. Legally, India would have to wrestle with the same questions of security vs. privacy that the world is facing. From the government’s demand for the Blackberry encryption keys and the loose clauses in the ITA and Telegraph Act that permit wiretapping and monitoring by the government, it would appear that the Government of India would advocate the tight security measures with few restrictions, and would welcome the potential that monitoring has to stop terror from occurring. But this would have to be balanced against the concerns raised by the police officers’ observation in the Times of India that the use of scanners, was “against Islam, and an invasion of personal freedom.” It is not clear which value would be given priority.
The variation in responses and the uneven uptake of the technology around the world shows how controversial the debate between security and privacy is, and how culture, context, and perception of privacy all contribute to an individual’s, a nation’s, and a country’s willingness or unwillingness to embrace new technology. The nature of the debate shows that privacy is not an issue only of data protection, that it is much more than just a sum of numbers. Instead, privacy is something that must be viewed holistically and contextually, and that must be a factor when assessing new policies.
DSCI Information Security Summit 2010 – A Report
Day one commenced with keynote address given by Jeffery Carr, Principal, GreyLogic, US who spoke about the gravity and risk that businesses and countries are facing in the digital age. A prominent theme in every presentation throughout the day was that India is facing both serious changes and challenges in light of evolving technology and global standards. A few specific challenges addressed were: encryption standards, the cloud, and securing business transactions. During the panel on encryption standards it was pointed out that India desperately needs a clear and comprehensive policy on encryption standards. Not only will this serve to facilitate transactions in India, but it will increase trade as foreign countries will have an enforced policy to ensure them that India is a safe destination to export to. The panel addressing the cloud focused on the challenges that businesses are facing in terms of the cloud in the Indian context. The three main challenges to the Cloud are:
- data security and privacy
- compliance requirements
- legal and contractual requirements
It was pointed out that in particular the Indian legal environment is serving as an obstacle to businesses wishing to move to the cloud, because of policies such as 40 bit encryption, and the Indian Telecom licensing policy which do not permit data transfer outside the cloud. Discussed also were measures that organisations have adopted to address data protection challenges in the cloud including: Including security & privacy clauses in the contractual agreement, making the Cloud service provider liable for a data breach, and auditing the services of Cloud service providers. Further information about the Cloud in the Indian context can be found in the DSCI report on Data Protection Challenges in Cloud Computing: An Indian Perspective. In the session on Securing Business Transactions, the challenge of protecting data and transactions was addressed. Many approaches were presented which explained how securing systems has moved away from using security enables software to security embedded hardware. The first day concluded with a presentation of DSCI Study Reports, including their recent study on the State of Data Security and Privacy in the Indian BPO Industry, Service Provider Assessment Framework – A Study Report, and the DSCI Security Framework.
The second day included presentations and panel discussions on privacy, the economics of security, and security technologies. The presentation on privacy presented many different viewpoints which ranged from the stance that India has been taking the right steps towards securing individuals privacy, and in contrast, that India has seen a dilution of privacy standards in the recent years. Contributing to the panel on privacy, Vakul Sharma, Supreme Court Advocate created a timeline of privacy in India, dispelling the popular belief that India does not have a history of privacy. Mr. Sharma closed his presentation with a challenge to those who believe that India does not have adequate privacy protections - to return to the clauses in the ITA, see if they are indeed being followed, and then assess if India does not have adequate privacy protection. The panel on the Economics of Security spoke about the rising costs of security in the wake of cyber crime, and the rising cost of not adequately protecting one’s business. In the session on Technology Challenges to Fight Data Breaches and Cyber Crimes a debate evoked on current measures taken by industry and government to fight cyber crime, and steps that still need to be taken. Opening the session was a presentation by Mr. West, member of the National Cyber Forensics Training and Alliance. His presentation introduced a new approach taken by the States in which key stakeholders including students and local law enforcement were engaged when tracking down cyber criminals. Mr. West demonstrated the success of the program, and explained how such an approach could be easily adapted in India. From different comments made by the panel and audience it was clear from this session that there is a need for the Indian government to be more invested in funding and supporting smaller cybercrime initiatives. Closing the day was a panel on E-Security for the next five years including the application and enforcement of DSCI’s best practices for a Security and Privacy Framework.
The event was sponsored by: Trusted Computing Group, Computer Associates, McAfee, Verizon Business, Tata Consultancy Services, Deloitte, (ISC)2, BlackBerry, ACS, CSC, Microsoft, RSA, and Intel.
Jurisdictional Issues in Cyberspace
Google Policy Fellowship Program: Asia Chapter
Offered for the first time in Asia Pacific, the Google Policy Fellowship offers successful applicants the opportunity to develop research and debate on issues relating to freedom of expression for a minimum of ten weeks from June to August 2011. The applicants will be selected in Australia, India and Hong Kong respectively.
The Centre for Internet and Society will select the India Fellow, and is accepting applications for the position before March 27, 2011. Google is providing a USD 7,500 stipend to the India Fellow, who will be selected by April 18, 2011.
To apply, please send to [email protected] the following materials:
- Statement of Purpose: A brief write-up outlining about your interest and qualifications for the programme including the relevant academic, professional and extracurricular experiences. As part of the write-up, also explain on what you hope to gain from participation in the programme and what research work concerning free expression online you would like to further through this programme. (About 1200 words max).
- Resume
- Three references
More information about the focus of the work that the Google Policy Fellow will take on is described below1. More information about the Google Policy Fellowship program is available in the FAQ2.
Research Agenda Outline
The research proposals, and the fellowship itself, are to be anchored in the reality of the growing threat to civil liberties in cyberspace, with the consequent curbs on free expression that arise. The aim of the research is to chart out a comprehensive map of the legal and policy frameworks relating to free expression within the Asia-Pacific region and also examine people’s attitudes and ground-level movements relating to the same. This second component will necessarily involve some amount of empirical research: the fellows across different regions (for 2011, there will be fellows from India, Australia and Hong Kong) will be expected to use a survey on similar lines, so that the results could be adequately contrasted.
The research would involve but not necessarily be limited to the following areas:
Understanding Dissent
This component would involve looking at how dissent is negotiated in the region by the legal system and the ways in which governments seek to stifle and control online dissent. Specific points of interrogation would include:
- The extent to which the constitution and other laws in the region protect freedom of expression and the extent to which they are enforced.
- Judicial decisions relating to free expression, censorship and dissent. Have they examined how speech and other activities on the Internet should be afforded free speech protection?
- The kind of material deemed objectionable and subject to censorship and/or penalization.
- The kind of penalties placed on writers, commentators and bloggers for posting objectionable materials on the Internet.
- Understanding the economic environment in which free expression operates: chains of media ownership, state restrictions on the means of journalistic production and distribution, and the levels of state control through allocation of advertising or subsidies would be part of this question.
- Further, what are the laws relating to encryption and telecom security, as well as to intermediary liability, and how do they affect free expression?
Understanding Free Expression
To be examined here is the question of how freedom of expression is perceived by people. What is the extent to which people believe the right is available to them — as balanced by conceivably conflicting rights such as privacy?
- One part of proceeding on this would be to track a set of activist bloggers, gauging their take on various issues.
- Another part would include tracking public opinion through comments pages on articles relating to free speech issues; taking a survey or coordinating focus group research. However, this is by no means the most reliable way to gauge the same and is, in particular, one area that will require an appropriate methodology to be developed by the fellows in consultation with the partner organizations.
Both these components are essential in being able to proceed with the third aspect, mentioned below.
Understanding and Facilitating Movements
This final aspect will involve looking at how free expression advocates come together, or fail to do so.
- Is there a defined activist community in the region?
- If not, what are the possible reasons behind failure of collaboration or organization? Have there been attempts towards the same?
Frequently Asked Questions
What is the Google Policy Fellowship program?
The Google Policy Fellowship program offers students interested in Internet and technology related policy issues with an opportunity to spend their summer working on these issues at the Centre for Internet and Society at Bangalore. Students will work for a period of ten weeks starting from June 2011. The research agenda for the program is based on legal and policy frameworks in the region connected to the ground-level perception of free expression.
Applications for the Fellowship should carry these:
- Statement of Purpose: A brief write-up outlining about your interest and qualifications for the programme including the relevant academic, professional and extracurricular experiences. As part of the write-up, also explain on what you hope to gain from participation in the programme and what research work concerning free expression online you would like to further through this programme. (About 1200 words max).
- Resume
- Three references
Important Dates
What is the program timeline?
| March 27, 2011: |
Student application deadline; applications must be received by midnight 00:00 GMT. |
| April 18, 2011: |
Student applicants are notified of the status of their applications. |
| June 2011: |
Students begin their fellowship with the host organization (start date to be determined by students and the host organization); Google issues initial student stipends. |
| July 2011: |
Mid-term evaluations; Google issues mid-term stipends. |
| August 2011: |
Final evaluations; Google issues final stipends. |
EligibilityI am an International student can I apply and participate in the program?
Yes. You must be 18 years of age or older by 1 January 2011 to be eligible to participate in Google Policy Fellowship program in 2011.
For the time being, we are only accepting students eligible to work in India (e.g. Indian citizens, permanent residents of India, and individuals presently holding an Indian student visa. Google cannot provide guidance or assistance on obtaining the necessary documentation to meet the criteria.
In order to participate in the program, you must be a student. Google defines a student as an individual enrolled in or accepted into an accredited institution including (but not necessarily limited to) colleges, universities, masters programs, PhD programs and undergraduate programs. Eligibility is based on enrollment in an accredited university by 1 January 2011.
In order to participate in the program, you must be a student (see Google's definition of a student above). You must also be eligible to work in India (see section on citizen requirements for fellowship above). Google cannot provide guidance or assistance on obtaining the necessary documentation to meet this criterion.
As long as you are enrolled in a college or university program as of 1 January 2011, you are eligible to participate in the program.
As long as you are enrolled in a college or university program as of 1 January 2011, you are eligible to participate in the program.
Payments, Forms, and Other Administrative Stuff
- Accepted students in good standing with their host organization will receive a USD 2,500 stipend payable shortly after they begin the Fellowship in June 2011.
- Students who receive passing mid-term evaluations by their host organization will receive a USD 1,500 stipend shortly after the mid-term evaluation in July 2011.
- Students who receive passing final evaluations by their host organization and who have submitted their final program evaluations will receive a USD 3,500 stipend shortly after final evaluations in August 2011.
Students should be prepared, upon request, to provide Google or the host organization with transcripts from their accredited institution as proof of enrollment or admission status. Transcripts do not need to be official (photo copy of original will be sufficient).
Yes. If you need documentation from Google to provide to your school for course credit, you can contact Google. We will not provide documentation until we have received a final evaluation from your mentoring organization.
Host Organizations
Google provides the funding and administrative support for individual fellows directly. Google and the Centre for Internet and Society are not partners or affiliates. The Centre for Internet and Society does not represent the views or opinions of Google and cannot bind Google legally.
CIS Para-wise Comments on Draft Reasonable Security Practices Rules, 2011
A. Specific Objections
Rule 3
Sensitive personal data or information.— Sensitive personal data or information of a person shall include information collected, received, stored, transmitted or processed by body corporate or intermediary or any person, consisting of :
Password;
...
Call data records;
Comment
We suggest that this list be expanded to include information such as sexual orientation, religion and caste. In addition, “electronic communication records” including emails, chat logs and other communications using a computer should be designated sensitive personal information.
Rule 4
Body Corporate to provide policy for privacy and disclosure of information.— (1) The body corporate or any person who on behalf of body corporate collects, receives, possess, stores, deals or handle shall provide a privacy policy for handling of or dealing in user information including sensitive personal information and ensure that the same are available for view by such providers of information who has provided such information under lawful contract. Such policy shall provide for:
Type of personal or sensitive information collected under sub-rule (ii) of rule 3;
Purpose, means and modes of usage of such information;
Disclosure of information as provided in rule 6
Comment
We recommend that the privacy policy be made available for view to all individuals to whom the information held by the body corporate pertains. Currently the privacy policy will only be disclosed to the “providers of information” who may not be the individual concerned directly.
Rule 5
Collection of information.—
(1) Body corporate or any person on its behalf shall obtain consent of the provider of the information regarding purpose, means and modes of uses before collection of such information.
Comment
We recommend the substitution of the term “individual to whom the data pertains” instead of the phrase “provider of the information”.
(2) Body corporate or any person on its behalf shall not collect sensitive personal information unless—
the information is collected for a lawful purpose connected with a function or activity of the agency; and
the collection of the information is necessary for that purpose.
Comment
We recommend a blanket prohibition of collection of biometric data unless a heightened security interest is demonstrated.
(3) While collecting information directly from the individual concerned, the body corporate or any person on its behalf shall take such steps as are, in the circumstances, reasonable to ensure that the individual concerned is aware of.
Comment
We recommend a simpler phrase like “The body corporate.. shall take reasonable steps to inform the individual concerned” instead of the current complex phrasing. Reasonableness has generally been interpreted by courts contextually. For instance, the Supreme Court has remarked, “`Reasonable’ means prima facie in law reasonable in regard to those circumstances of which the actor, called upon to act reasonably, knows or ought to know. See Gujarat Water Supply and Sewage Board v. Unique Erectors (Guj) AIR 1989 SC 973.
(4) Body corporate or any person on its behalf holding sensitive personal information shall not keep that information for longer than is required for the purposes for which the information may lawfully be used.
Comment
We recommend that this be converted into a mandatory obligation to delete or anonymise the information collected within a stipulated period (say 6 months) after the expiry of use for which it was collected.
(6) Body corporate or any person on its behalf shall permit the users to review the information they had provided and modify the same, wherever necessary.
Comment
Individuals should have the right to review and modify information pertaining to them whether or not they themselves had provided the information to the body corporate. This right should be provided to them wherever the information that pertains to them is incorrect.
(7) Body corporate or any person on its behalf shall provide an option to the provider of the information to opt-in or opt-out.
Comment
We recommend that the wording be changed to “individual to whom the data pertains” instead of “provider of information”.
CIS Para-wise Comments on Cyber Café Rules, 2011
A. General Objections
These rules have no nexus with their parent provision, namely s.79(2). Section 79(1) provides for exemption from liability for intermediaries. Section 79(2) thereupon states:
79. Intermediaries not to be liable in certain cases—
(2) The provisions of sub-section (1) shall apply if—
(a) the function of the intermediary is limited to providing access to a communication system over which information made available by third parties is transmitted or temporarily stored or hasted; or
(b) the intermediary does not—(i) initiate the transmission,
(ii) select the receiver of the transmission, and
(iii) select or modify the information contained in the transmission;(c) the intermediary observes due diligence while discharging his duties under this Act and also observes such other guidelines as the Central Government may prescribe in this behalf.
Therefore, by not observing any of the provisions of the Rules, the intermediary opens itself up for liability for actions of its users. However, the provisions contained in these rules have no rational nexus with due diligence to be observed by the intermediary to absolve itself from liability for third-party actions.
While the government may have authority to regulate cybercafes, that regulation should not be promulgated as rules under s.79(2). Doing so would be ultra vires s.79(2) itself.
Recommendation
These rules should be deleted in toto.
B. Specific Objections
These specific objections are in addition to the above-stated general objection, and do not detract from out recommendation that these rules should be deleted in their entirety.
Rule 2(c)
(c) “Cyber Cafe” means cyber café as defined in clause (na) of sub-section (1) of section 2 of the Act
Comment
The Act defines a cyber cafe as meaning “any facility from where access to the internet is offered by any person in the ordinary course of business to the members of the public”. This would include internet access provided in airports, in restaurants, and in many other places where the provisions of these rules (such as those about height of partitions, etc.) just will not be practicable. Thus, this provision will have unintended consequences.
Rule 3
Agency for issuance of license: Appropriate government will notify an agency to issue license to cyber cafes.
Comment
Rule 3 requires the issuing of a license for the establishment of a cyber café. We believe this is unwarranted since cybercafes, like most commercial establishments are already subject to registration and licensing under the “Shops and Establishments Acts” which have been enacted in all states. These Acts already specify an elaborate procedure for the application, registration and monitoring of all establishments and there is no need to multiply the levels of permission a cyber café must obtain. The current rules do not specify an application procedure, fee, and a maximum or minimum time frame within which such a license must be granted or denied nor does it specify the criterion on which such license applications will be evaluated. We think that in the absence of such legislative guidance, this provision is likely to be abused.
Cyber cafes in India contribute greatly to India’s increasing internet penetration and inserting a licensing regime would greatly impede access to the internet.
We believe that cyber cafes should be allowed to be established in the same manner as other shops and establishments, without the requirement of a special license.
Rule 4(2)
...When an user cannot establish his/her identify to the satisfaction of the Cyber Café as per sub-rule (1), he/she may be photographed by the Cyber Café using a web camera installed on one of the computers in the Cyber Café for establishing the identity of the user.
Comment
Sub-Rule 4 (2) Requires that if an individual is unable to establish identity, their photograph must be taken if they wish to use cyber café facilities. We believe that an individual’s photograph should be taken only as a last resort, where identity has been established.
Rule 4(3)
Children without photo identity card shall be accompanied by an adult with any of the documents as prescribed in sub-rule (1).
Comment
We recommend that children below 18 years should be specifically exempt from proving their identities to cyber café owners. Children are usually the quickest to adopt technology, and the requirement of possessing a valid identity might prove to be a deterrent to their developing computer skills. Likewise, being accompanied by an adult is also an onerous obligation since children’s access to the internet would depend on the availability of an adult/parent who may be too busy to accompany the child on every occasion the child wishes to access the internet or use a computer.
To reiterate, we feel that the current provision specially and adversely targets children from poorer classes (since they are most likely to routinely access internet through cyber cafes) and denies them the opportunity of developing their computer skills which are crucial for the growth of the “knowledge economy” that India is trying to head towards.
In addition, we believe that children are more susceptible to exploitation and consequently have a heightened privacy expectation which must be honoured. We recommend that the current sub-rule be deleted and replaced with a clause which specifically exempts children from proving their identity and forbids taking photographs of them under any circumstance.
Rule 5(1)
... Log Register: After the identity of the user has been established as per sub-rule (1) of rule 4 above, the Cyber Café shall record and maintain the required information of each user in the log register for a minimum period of one year. Also, Cyber Café may maintain an online version of the log register.
Comment
Rule 5(1) Provides a minimum period of one year that Cyber Cafes must retain their log registers. The rule does not specify the details which the log register must provide. In the interests of minimising threats to privacy, we recommend that these details recorded be confined only to the name and duration of use.
In addition, we believe that there should also be a coinciding mandatory deletion clause for the log register requiring details to be purged after the minimum retention period.
Rules 5(3)and 6(2)
5(3): “The cyber café owner shall be responsible for storing and maintaining following backups of logs and computer resource records for at least six months for each access or login by any user :
· History of websites accessed using computer resource at cyber cafe
· Logs of proxy server installed at cyber café
· Mail server logs
· Logs of network devices such as router, switches, systems etc. installed at cyber café
· Logs of firewall or Intrusion Prevention/Detection systems, if installed.”
6(2): “The screen of all computers, installed other than in Partitions or Cubicles, shall face ‘outward’, i.e. they shall face the common open space of the Cyber Café.”
Comment
We recommend deletion of this rule since it is an unreasonable intrusion into a person’s privacy and an indirect attempt to censor content which users may wish to access. There are many uses of the internet for which a user may legitimately require privacy: For instance, patients, including HIV patients and those with mental illness, may wish to obtain information about their condition. Similarly sexuality minorities may wish to seek support or reach out to a larger community. Enforcing the architecture stipulated in this rule would discourage their access to such vital information. In addition, this architecture would make it easier for cyber crimes such as identity theft to take place since it would be easier to observe the login details of other users at the cyber café.
Rule 7(1)
Inspection of Cyber Café : “An officer, not below the rank of Police Inspector as authorised by the licensing agency, is authorized to check or inspect cyber café and the computer resource or network established therein at any time for the compliance of these rules. The cyber café owner shall provide every related document, registers and any necessary information to the inspecting officer on demand.
Comment
We recommend this clause be omitted since it confers unfettered and unsupervised powers on any Police Inspector to examine any cyber café premises he may choose without any restriction on time.
Additionally, the provisions of Shops and Establishments Acts of most states already prescribe a procedure for inspection of establishments and examination of records. The current rules merely add another layer of supervision to the existing laws without adequate safeguards.
Comment
Sub-Rule 5(3) holds cyber café owners responsible for the storage and maintenance of back up logs concerning the following information: history of websites, logs of proxy servers, mail server logs, logs of network devices, logs of firewalls installed. We believe that the maximum length for retention of this data should be defined and a mandatory deletion clause should be inserted requiring cyber café owners to delete these logs periodically. We further believe that access to the history of websites and mail server logs is a serious invasion of a person’s privacy, and should be omitted from the back up logs.
This is especially so when currently there is no requirement that cyber café owners maintain their logs under conditions of utmost secrecy and confidence.
CIS Para-wise Comments on Intermediary Due Diligence Rules, 2011
A. General Objections
A number of the provisions under these Rules have no nexus with their parent provision, namely s.79(2). Section 79(1) provides for exemption from liability for intermediaries. Section 79(2) thereupon states:
79. Intermediaries not to be liable in certain cases—
(2) The provisions of sub-section (1) shall apply if—
(a) the function of the intermediary is limited to providing access to a communication system over which information made available by third parties is transmitted or temporarily stored or hasted; or
(b) the intermediary does not—
(i) initiate the transmission,
(ii) select the receiver of the transmission, and
(iii) select or modify the information contained in the transmission;
(c) the intermediary observes due diligence while discharging his duties under this Act and also observes such other guidelines as the Central Government may prescribe in this behalf.
Therefore, by not observing any of the provisions of the Rules, the intermediary opens itself up for liability for actions of its users. However, many of the provisions of the Rules have no rational nexus with due diligence to be observed by the intermediary to absolve itself from liability.
B. Specific Objections
Rule 2(b), (c), and (k)
(b) “Blog” means a type of website, usually maintained by an individual with regular entries of commentary, descriptions of events, or other material such as graphics or video. Usually blog is a shared on-line journal where users can post diary entries about their personal experiences and hobbies;
(c) “Blogger” means a person who keeps and updates a blog;
(k) “User” means any person including blogger who uses any computer resource for the purpose of sharing information, views or otherwise and includes other persons jointly participating in using the computer resource of intermediary
Comments
It is unclear why it is necessary to specifically target bloggers as users, leaving out other users such as blog commenters, social network users, microbloggers, podcasters, etc. It makes the rules technologically non-neutral.
Recommendation
We recommend that these 3 sub-rules be deleted.
Rule 3(2)
3. Due Diligence observed by intermediary.— The intermediary shall observe following due diligence while discharging its duties.
(2) The intermediary shall notify users of computer resource not to use, display, upload, modify, publish, transmit, update, share or store any information that : —
(a) belongs to another person;
(b) is harmful, threatening, abusive, harassing, blasphemous, objectionable, defamatory, vulgar, obscene, pornographic, paedophilic, libellous, invasive of another’s privacy, hateful, or racially, ethnically or otherwise objectionable, disparaging, relating or encouraging money laundering or gambling, or otherwise unlawful in any manner whatever;
(c) harm minors in any way;
(d) infringes any patent, trademark, copyright or other proprietary rights;
(e) violates any law for the time being in force;
(f) discloses sensitive personal information of other person or to which the user does not have any right to;
(g) causes annoyance or inconvenience or deceives or misleads the addressee about the origin of such messages or communicates any information which is grossly offensive or menacing in nature;
(h) impersonate another person;
(i) contains software viruses or any other computer code, files or programs designed to interrupt, destroy or limit the functionality of any computer resource;
(j) threatens the unity, integrity, defence, security or sovereignty of India, friendly relations with foreign states, or or public order or causes incitement to the commission of any cognizable offence or prevents investigation of any offence or is insulting any other nation.
Comments
Firstly, such ‘standard’ terms of use [1] might make sense for one intermediary, but not for all. For instance, an intermediary such as site with user-generated content (e.g., Wikipedia) would need different terms of use from an intermediary such as an e-mail provider (e.g., Hotmail), because the kind of liability they accrue are different. This is similar to how the liability that a newspaper publisher accrues is different from that accrued by the post office. However, forcing standard terms of use negates this difference. Thus, these are impractical.
Secondly, read with the legal obligation of the intermediary to remove such information (contained in rule 3(3)), they vest an extraordinary power of censorship in the hands of the intermediary, which could easily lead to the stifling of the constitutionally guaranteed freedom of speech online. Analogous restrictions do not exist in other fields, e.g., against the press in India or against courier companies, and there is no justification to impose them on content posted online. Taken together, these provisions make it impossible to publish critical views about anything without the risk of being summarily censored.
Thirdly, while it is possible to apply Indian law to intermediaries, it is impracticable to require all intermediaries (whether in India or not) to have in their terms of use India-specific clauses such as rule 3(2)(j). Instead, it is better to merely require them to ask their users to follow all relevant laws.
Individual instances of how these rules are overly broad are contained in an appendix to this submission.
Recommendation
We strongly recommend the deletion of this sub-rule, except clause (e).
Rule 3(3)
(3) The intermediary shall not itself host or publish or edit or store any information or shall not initiate the transmission, select the receiver of transmission, and select or modify the information contained in the transmission as specified in sub-rule (2).
Comments
This sub-rule is ultra vires s.79 of the IT Act, which does not require intermediaries not to “host or publish or edit or store any information”. If fact, s.79(2) merely states that by violating the provisions of s.79(2), the intermediary loses the protection of s.79(1). It does not however make it unlawful to violate s.79(2), as rule 3(3) does. This makes rule 3(3) ultra vires the Act.
Recommendation
This sub-rule should be deleted.
Rule 3(4)
(4) The intermediary upon obtaining actual knowledge by itself or been brought to actual knowledge by an authority mandated under the law for the time being in force in writing or through email signed with electronic signature about any such information as mentioned in sub-rule (2) above, shall act expeditiously to work with user or owner of such information to remove access to such information that is claimed to be infringing or to be the subject of infringing activity. Further the intermediary shall inform the police about such information and preserve the records for 90 days
Comments
This rule is also ultra vires s.69A of the IT Act as well as the Constitution of India. Section 69A states all the grounds on which an intermediary may be required to restrict access to information [2]. It does not allow for expansion of those grounds, because it has been carefully worded to maintains its constitutional validity vis-a-vis Articles 19(1)(a) and 19(2) of the Constitution of India. The rules framed under s.69A prescribe an elaborate procedure before such censorship may be ordered. The rules under s.69A will be rendered nugatory if any person could get content removed or blocked under s.79(2).
This rule requires an intermediary to immediately take steps to remove access to information merely upon receiving a written request from “any authority mandated under the law”. Thus, for example, any authority can easily immunize itself from criticism on the internet by simply sending a written notice to the intermediary concerned. This is directly contrary to, and completely subverts the legislative intent expressed in Section 69B which lays down an elaborate procedure to be followed before any information can be lawfully blocked.
If any person is aggrieved by information posted online, they may seek their remedies—including the relief of injunction—from courts of law, under generally applicable civil and criminal law. Inserting a rule such as this one would take away the powers of the judiciary in India to define the line dividing permissible and impermissible speech, and vest it instead in the whims of each intermediary. This can only have a chilling effect on debates in the public domain (of which the Internet is a part) which is the foundation of any democracy.
Recommendation
This rule should modified so that an intermediary is obliged to take steps towards removal of content only when (a) backed by an order from a court or (b) a direction issued following the procedure prescribed by the rules framed under Section 69A.
Rule 3(5) & (7) & (8) & (10)
(5) The Intermediary shall inform its users that in case of non-compliance with terms of use of the services and privacy policy provided by the Intermediary, the Intermediary has the right to immediately terminate the access rights of the users to the site of Intermediary;
(7) The intermediary shall not disclose sensitive personal information;
(8) Disclosure of information by intermediary to any third party shall require prior permission or consent from the provider of such information, who has provided such information under lawful contract or otherwise;
(10) The information collected by the intermediary shall be used for the purpose for which it has been collected.
Comments
These sub-rules have no nexus with intermediary liability or non-liability under s.79(2). For instance, it is unreasonable to say that an intermediary may be held liable for the actions of its users if it does not inform its users about its right to terminate access by the user to its services. Furthermore, not all intermediaries need be websites, as sub-rule 5 assumes. An intermediary can even be an “internet service provider” or a “cyber cafe” or a “telecom service provider”, as per rule 2(j) read with s.2(1)(w) of the IT Act.
The requirements under sub-rules (7), (8), and (10) are rightfully the domain of s.43A and the rules made thereunder, and not s.79(2) nor these rules.
Recommendation
These sub-rules should be deleted, and sub-rules (7), (8), and (10) may placed instead in the rules made under s.43A.
Rule 3(9)
(9) Intermediary shall provide information to government agencies who are lawfully authorised for investigative, protective, cyber security or intelligence activity. The information shall be provided for the purpose of verification of identity, or for prevention, detection, investigation, prosecution, cyber security incidents and punishment of offences under any law for the time being in force, on a written request stating clearly the purpose of seeking such information.
Comments
This provision is ultra vires ss.69 and 69B. Rules have already been issued under ss.69 and 69B which stipulate the mechanism and procedure to be followed by the government for interception, monitoring or decrypting information in the hands of intermediaries. Thus under the Interception Rules 2009 framed under Section 69, permission must first be obtained from a “competent authority” before an intermediary can be directed to provide access to its records and facilities. The current rule completely removes the safeguards contained in s.69 and its rules, and would make intermediaries answerable to virtually any request from any government agency. This is contrary to the legislative intent expressed in Section 69.
Recommendation
We recommend this sub-rule be deleted.
Rule 3(12)
(12) The intermediary shall report cyber security incidents and also share cyber security incidents related information with the Indian Computer Emergency Response Team.
Comments
The rules relating to how and when the Indian Computer Emergency Response Team may request for information from intermediaries is rightfully the subject matter of s.70B(5) [3] and the rules made thereunder by virtue of the rule making power granted by s.87(2)(yd). The subject matter of rule 3(12) is not liability of intermediaries for third-party actions, hence there is no nexus between the rule-making power, and the rule.
Recommendations
We recommend that this sub-rule be deleted.
Rule 3(14)
(14) The intermediary shall publish on its website the designated agent to receive notification of claimed infringements.
Comments
It is unclear what “infringements” are being referred to in this sub-rule. Neither s.79 nor these rules provide for “infringements”. The same reasoning applied for rule 3(4) would also apply here. It would be better to require the intermediary to publish on its website a method of providing judicial notice.
Recommendations
Delete, and replace with a requirement for the intermediary to publish on its website a method of providing judicial notice.
Footnotes
-
For instance, the Section B(1) of the World of Warcraft Code of Conduct “When engaging in Chat, you may not: (i) Transmit or post any content or language which, in the sole and absolute discretion of Blizzard, is deemed to be offensive, including without limitation content or language that is unlawful, harmful, threatening, abusive, harassing, defamatory, vulgar, obscene, hateful, sexually explicit, or racially, ethnically or otherwise objectionable.
-
It is only “in the interest of sovereignty and integrity of India. defence of India, security of the State, friendly relations with foreign States or public order or for preventing incitement to the commission of any cognizable offence relating to above” that intermediaries may be issued directions to block access to information.
-
70B(5) sates that the The manner of performing functions and duties of the agency referred to in sub-section (1) shall be such as may be prescribed.
RTI Applications on Blocking of Websites
While under the law (i.e., s.69A of the Information Technology Act), the Department of Information Technology (DIT) has the power to order blocks (via the 'Designated Officer'), in some cases it has been noted that the ISPs have noted that the order to block access to the websites have come from the Department of Telecom (DoT). Due to this, we have sent in RTI applications to both the DIT and the DoT.
RTI Application to Department of Information Technology
To
Shri
B.B.Bahl,
Joint
Director and PIO (RTI)
Office
of PIO (RTI)
Room
No 1016, Electronics Niketan
Department
of Information Technology (DIT)
Ministry
of Communications and Information Technology
6,
CGO Complex, New Delhi
Dear Sir,
Subject: Information on Website Blocking Requested under the Right to Information Act, 2005
1.
Full Name of the Applicant:
Pranesh
Prakash
2.
Address of the Applicant:
E-mail
Address:
pranesh[at]cis-india.org
Mailing
Address:
Centre
for Internet and Society
194,
2-C Cross,
Domlur
Stage II,
Bangalore
– 560071
3. Details of the information required:
It has come to our attention that Airtel Broadband Services (“Airtel”) has recently blocked access to a blog host called TypePad (http://www.typepad.com) (“TypePad”) for all its users across the country. In this regard, we request information on the following queries under Section 6(1) of the Right to Information Act, 2005:
-
Did the Department order Airtel to block TypePad under s.69A of the Information Technology Act (“IT Act”), 2000 read with the Information Technology (Procedures and Safeguards for Blocking Access of Information by Public) Rules, 2009 (“Rules”) or any other law for the time being in force? If so, please provide a copy of such order or orders. If not, what action, if at all, has been taken by the Department against Airtel for blocking of websites in contravention of s.69A of the IT Act?
-
Has the Department ever ordered a block under s.69A of the IT Act? If so, what was the information that was ordered to be blocked?
-
How many requests for blocking of information has the Designated Officer received, and how many of those requests have been accepted and how many rejected? How many of those requests were for emergency blocking under Rule 9 of the Rules?
-
Please provide use the present composition of the Committee for Examination of Requests constituted under Rule 7 of the Rules.
-
Please provide us the dates and copies of the minutes of all meetings held by the Committee for Examination of Requests under Rule 8(4) of the Rules, and copies of their recommendations.
-
Please provide us the present composition of the Review Committee constituted under rule 419A of the Indian Telegraph Rules, 1951.
-
Please provide us the dates and copies of the minutes of all meetings held by the Review Committee under Rule 14 of the Rules, and copies of all orders issued by the Review Committee.
4.
Years to which the above requests pertain:
2008-2011
Shri
B.B.Bahl,
Joint
Director and PIO (RTI)
Office
of PIO (RTI)
Room
No 1016, Electronics Niketan
Department
of Information Technology (DIT)
Ministry
of Communications and Information Technology
6,
CGO Complex, New Delhi
To the best of my belief, the details sought for fall within your authority. Further, as provided under section 6(3) of the Right to Information Act (“RTI Act”), in case this application does not fall within your authority, I request you to transfer the same in the designated time (5 days) to the concerned authority and inform me of the same immediately.
To
the best of my knowledge the information sought does not fall within
the restrictions contained in section 8 and 9 of the RTI Act, and any
provision protecting such information in any other law for the time
being in force is inapplicable due to section 22 of the RTI Act.
Please provide me this information in electronic form, via the e-mail address provided above.
This to certify that I, Pranesh Prakash, am a citizen of India.
A fee of Rs. 10/- (Rupees Ten Only) has been made out in the form of a demand draft drawn in favour of “Pay and Accounts Officer, Department of Information Technology” payable at New Delhi.
Date:
Monday, February 28, 2011
Place:
Bengaluru, Karnataka
(Pranesh Prakash)
RTI Application to Department of Telecom
To
Shri
Subodh Saxena
Central
Public Information Officer (RTI)
Director
(DS-II)
Room
No 1006, Sanchar Bhawan
Department
of Telecommunications (DoT)
Ministry
of Communications and Information Technology
20,
Ashoka Road, New Delhi — 110001
Dear Sir,
Subject: Information on Website Blocking Requested under the Right to Information Act, 2005
1.
Full Name of the Applicant:
Pranesh
Prakash
2.
Address of the Applicant:
E-mail
Address:
pranesh[at]cis-india.org
Mailing
Address:
Centre
for Internet and Society
194,
2-C Cross,
Domlur
Stage II,
Bangalore
– 560071
3. Details of the information required:
It has come to our attention that Airtel Broadband Services (“Airtel”) has recently blocked access to a blog host called TypePad (http://www.typepad.com) (“TypePad”) for all its users across the country. Airtel subscribers trying to access this website receive a message noting “This site has been blocked as per request by Department of Telecom”. In this regard, we request information on the following queries under Section 6(1) of the Right to Information Act, 2005:
-
Does the Department have powers to require an Internet Service Provider to block a website? If so, please provide a citation of the statute under which power is granted to the Department, as well as the the safeguards prescribed to be in accordance with Article 19(1)(a) of the Constitution of India.
-
Did the Department order Airtel to block TypePad or any blog hosted by TypePad? If so, please provide a copy of such order or orders. If not, what action, if at all, has been taken by the Department against Airtel for blocking of websites?
-
Has the Department ever ordered the blocking of any website? If so, please provide a list of addresses of all the websites that have been ordered to be blocked.
-
Please provide use the present composition of the Committee constituted under rule 419A of the Indian Telegraph Rules, 1951.
-
Please provide us the dates and copies of the minutes of all meetings held by the Committee constituted under rule 419A of the Indian Telegraph Rules, 1951, and copies of all their recommendations.
4.
Years to which the above requests pertain:
2005-2011
5.
Designation and Address of the PIO from whom the information is
required:
Shri
Subodh Saxena
Central
Public Information Officer (RTI)
Director
(DS-II)
Room
No 1006, Sanchar Bhawan
Department
of Telecommunications (DoT)
Ministry
of Communications and Information Technology
20,
Ashoka Road, New Delhi — 110001
To the best of my belief, the details sought for fall within your authority. Further, as provided under section 6(3) of the Right to Information Act (“RTI Act”), in case this application does not fall within your authority, I request you to transfer the same in the designated time (5 days) to the concerned authority and inform me of the same immediately.
To the best of my knowledge the information sought does not fall within the restrictions contained in section 8 and 9 of the RTI Act, and any provision protecting such information in any other law for the time being in force is inapplicable due to section 22 of the RTI Act.
Please provide me this information in electronic form, via the e-mail address provided above.
This to certify that I, Pranesh Prakash, am a citizen of India.
A fee of Rs. 10/- (Rupees Ten Only) has been made out in the form of a demand draft drawn in favour of “Pay and Accounts Officer (HQ), Department of Telecom” payable at New Delhi.
Date:
Monday, February 28, 2011
Place:
Bengaluru, Karnataka
(Pranesh
Prakash)
Policy for Government's Presence in Social Media - Recommendations
1. Data Retention
The Government's communication to citizens via social media should follow the same data retention policy as its communication through other electronic and non-electronic channels.
Data portability compliance varies from one social media platform to another. Hence, privileged access may be mandated by the Government along the same lines “take down notices” and “information requests” currently being sent to social media and other platforms for intellectual property rights infringement and other offences.
2. Privacy
Yochai Benkler has famously stated that privacy is the protection of the weak from scrutiny by the powerful while transparency is the exposure of the powerful to scrutiny by the weak.1
It is critical that social media policy for the Government is compliant with existing law governing data protection and privacy.2 As Benkler said, privacy protection should be a function of power – ordinary citizens should be afforded greater protection than Government personnel. Each department of the Government may be recommended to publish their own set of additional protections to safeguard privacy of citizens while maintaining highest levels of transparency of Government bodies.
3. Certifying Official Accounts
Some social media platforms have the ability to certify or validate an official account. Such validation must be made mandatory for all Government presence across various social media platforms. The mere existence of official Government social media accounts does not mean that the Government officers cannot use their own personal unofficial social media accounts. However, there must be a very clear and discernable distinction between a Government officer's personal (individual) social media presence and the official social media presence of a Government department or Ministry.
While individual officers are encouraged to set up their own personal social media presences, the official accounts must be in the format: Ministry/Department (Acronym) along with Designation (Acronym) of the official, so that the fans/followers/friends accumulated during the tenure of a particular official can be handed over to the next person who takes the same office. In order that this process of handing over is smooth and uniform across various Government departments, it is recommended that the protocol for handing over of social media presences be clearly laid down and communicated to all the Government departments.
4. Social Media Integration with Government Portals
Social media must be integrated with the official websites. Ideally, the websites should use Free and Open Source Software (FOSS) content management system with full compliance with web accessibility guidelines such as W3C's Web Content Accessibility Guidelines (WCAG) so that the RSS feeds of newly added content can be broadcast via multiple social media presences. Therefore, social media is seen as an additional benefit accruing from already existing efforts and investments of the Governments in electronic publishing.
In fact, it would be greatly beneficial for citizens if a constitutent relationship management software with tracking number is used for all social media and email communication by the Government. This will bring about a higher level of transparency and accountability on part of the Government.
5. Security
Social media presences will be the target of malicious elements online. Government social media presences are, in fact, at a greater risk of being subject to such attacks. Therefore, Government security standards must be adhered to including change of passwords regularly for Government social media accounts.
6. Mass Outreach
In order to neutralise the pro-elite bias of social media, a special outreach to non-elites via mobile phones must be an integral part of the Government's social media strategy. Digitally enabled middle class activism can undermine true participatory democracy and this must be resisted.
7. Rude Accountability
Occasionally, citizens may resort to the use of inflammatory language and tone with Government authorities to claim public services and to sanction service failures. Such communications referred to as 'rude accountability' accompanied by trolling are common phenomena which the Government can expect around its social media presences. It is recommended that these incidents be ignored at the first instances instead of penalising them. The Department of Information Technology (DIT) should prescribe protocol for escalation in case of systemic trollers. It is to be noted that the lower threshold for freedom of speech as prescribed by the Information Technology Act and Information Technology Rules should not serve as the yardstick on Government social media presences for characterising citizens' behaviour as offences. It is important that the Government allows a greater space for citizens to communicate with the Government and exercise their freedom of expression.
8. Managing Expectations
Each Government Ministry/Department/Official should publicly manage expectations for their social media presences in the form of an explicit, published “social media” policy in which expectations surrounding integral aspects of communication with the public such as public comments, speed of response and procedure for escalation are clearly documented. This will ensure that citizens have fewer undue expectations from the social media presence of a particular Government authority.
9. Brevity of Communications
Social media particularly, micro blogging and SMS is based on brevity of communications. Therefore, when a social media presence is branded or named, it must be ensured that the name takes up least number of characters so that it enables viral propagation.
In order to standardise on the spellings employed for SMS slang common in micro blogging and SMSes, it is recommended that Government officials use modern clients with in-built support for such functionality to avoid being embarrassed online.
10. Official Logo
The official logo of the Government Ministry/Department should be an integral part of Government social media presences. The logo may also be published where applicable so that it could be the Public key. A link to the official website should be employed wherever appropriate in order to establish credibility of the social media presence.
11. Proactive Information Disclosure
Social media should be used as a means to uphold RTI obligations for proactive information disclosure and to drive traffic to the website which should ideally be an archive of such comprehensive proactive disclosures.
12. Alternative Open Platforms
Wherever free and open/ non-proprietary/ community-owned social media infrastructure exists, the Government will be obliged to use the alternative social media platform in addition to mainstream platforms. For instance, for every Government authority's presence on Twitter, the Government is obliged to ensure that such authority also has a presence on status.net.
13. Uniformity of Communication
Social media can only be used by the Government to communicate existing Government information and propagate official policy terms to the public. Great care must be taken to avoid propagation of unverified facts and frivolous misleading rumours which tend to circulate often through miscreants on social media platforms. It is recommended that any information published by the Government on a social media platform should be published only when such information can also be published through other existing Government channels.
If the Government has to be a good neighbour in social media, it should also contribute to viral dissemination of relevant public information by way of re-tweeting, commenting and liking. Considering that the Government might lend its credibility to dubious causes through such endorsement, a protocol should be in place as part of social media policy for the Government to ensure that baseless and dubious claims are not vouched for by the Government.
1See Yochai Benkler, “A Free Irresponsible Press: Wikileaks and the Battle over the Soul of the Networked Fourth Estate” (2011), forthcoming Harvard Civil Rights – Civil Liberties Law Review available at http://bit.ly/e84QhK.
2Existing laws covering data protection and privacy would include the Information Technology Act, the Information Technology Rules, The Telegraph Act and the Constitution of India.
The Draft Electronic Delivery of Services Bill, 2011 – Comments by CIS
- Accessibility
The Bill does not make it mandatory for all Government services to be accessible to all including persons with disabilities. The Bill refers to the term “access”, as defined in Section 2(1)(a) from the prespective of merely gaining physical access to the services or availability of such services1 rather than from the perspective of catering to the ability of a person with print (or other) disbilities from gaining access to the services in the normal format. It is very important that the electronic services are delivered in a format which is accessible to all persons including persons with disbilities, elderly persons etc. It should be mandatory for the Government to comply with Web Content Accessibility Guidelines (WCAG) and National Informatics Centre (NIC) guidelines for web accessibility. It is also important to ensure accessibility of all documents produced during service delivery by Government agencies. - Linguistic Accessibility
Section 5(2)(b) of the Bill requires the Government to prescribe a framework for all its agencies to ensure web presence or enablement which refers to rendering electronic services in the language chosen by the user. In pursuance of the same, it is important for delivery of services to be available in all national languages of India to begin with in addition to the content being encoded in Unicode font for all languages. It is important to note that there are not many open fonts available for Indian languages. Hence, it must be ensured that the Government allocates sufficient funds to ensure linguistic accessbility of the services delivered, while ensuring implementation of the provisions of the Bill. - Public Scrutiny
In order to ensure transparency of Government services and process of service delivery, it is essential that the Bill incorporates a provision to enable citizens to gain access to information provided by the Government as part of the service delivery process unless disclosing such information would amount to violation of any applicable law. Similarly, provision should be made for making public all RTI applications filed with the Government and responses to them. - Use of Free and Open Source Software
Considering that electronic service delivery by Government agencies is effected through public money, it is important that Governments are urged to use Free and Open Source Software (FOSS) for service delivery. This cuts costs to a great extent and also make the process more transparent and capable of customisation to varied needs of different departments. It is important to insert a provision requiring the Government to use FOSS as far as possible and in the event of any use of proprietary software, the Government should clearly explain the reason for such use, the costs incurred for the same, the additional benefit derived out of its use and other relevant details. - Open Standards
The Bill must stress on use of open standards for all computer resources and service delivery systems by Government agencies. As is the case with FOSS, such use brings down operation costs drastically and makes the service delivery process transparent and available for all to use. Use of ODF formats for documents, HTML for websites, ISA standards for hardware is recommended. It is also useful to ensure compliance with W3C guidelines by the concerned Government departments during implementation of the Bill. - Whistleblower Exception
The Bill does not contain any safeguards to ensure free and fearless disclosure of any wilful violation of the law impacting larger public interest. It is important to include a provision protecting any person exposing any violation of the provisions of the Bill or blowing the cover off any scam or farudulent activity decieving the public committed by service providers under the Bill. Such protection can be given by ensuring that the actions of such whistleblower, to the extent required for the exposure, does not constitute an offence under the provisions of the Bill. - Penalties for Offences
- Chapter 4 of the Bill gives a detailed list of acts constituting an offence under the Act including Section 15 which specifically relates to offences by companies. It is critical to ensure that the punishment and penalities for offences extend not only to citizens and companies but also to Government officials who misuse information they are privy to under the provisions of the Bill. In fact, a separate provision specifically applicable to the various offences which could be committed by Government officials under the Bill can reduce misuse of its provisions by the Government.
- It is to be noted that several provisions listed under Chapter 4 of the Bill covering offences and penalties are a reproduction of the provisions for the same under the Information Technology Act, 2000 (“IT Act”). Such reprodution is unnecessary and acts which are already deemed to be offences and have punishments prescribed for them under the IT Act (or any other legislation for the time being in force in India) need not be covered again in the Bill. This will avoid duplication and confusion in the legislations.
- Section 19(1) of the Bill provides that no alleged offence under the Bill can be tried in a court of law unless the Central Electronic Delivery of Services Commissioner (“Central Commissioner”) or the State Electronic Delivery of Services Commissioner (“State Commissioner”) authorises the same by issuing a complaint in this regard to the relevant court. This provision directly conflicts with a citizen's constitutional right to seek legal redress since it takes away his freedom to approach a court of law for redressal of his grievance without the permission of the Commissioners. It is recommended that the provision be either deleted or suitably modify so that it is not in violation of this constitutional right.
- Bottoms up Approach
A decentralised approach should be adopted along the lines of the Panchayati Raj system giving the citizen a greater say in the framework and implementation of service delivery by Government agencies. Implementation can be at the Panchayat and District levels apart from State levels. Citizens must be able to access and update their information. Furthermore, they should be able to define to a certain extent, access control to their information. This will automatically make them eligible or ineligible for various government services. - Charges for service delivery
Section 4 of the Bill authorises the Government to allow service providers to collect charges for electronic service delivery while Section 3(2) provides for the Government to regulate the manner and method of payment of such charges. It is critical to ensure that such charges levied under the provisions of the Bill do not exceed the charges levied by the Government agency for manual delivery of services. Charges for manual service delivery may include charges for photocopy, printing, paper, postage etc., all of which are totally eliminated during service delivery through electronic means. Thus, levying the same charges, let alone greater charges for electronic service delivery is totally unnecessary and places an additional burden on the citizen ultimately defeating the very purpose of the Bill. - Security in payment of charges
Section 3(2) of the Bill provides for the Government to regulate the manner and method of payment of charges for delivery of services.It is important that each transaction that takes place is done securely and without the exposure of an individuals confidential details. There are many ways to structure the transaction of payment of fees to achieve this goal. We reccommend that the SCOSTA smart card structure is used for completing and processing a transaction. - Data Security and Privacy
Section 5(1)(e) of the Bill requires the Government to ensure integrity, security and confidentiality of data collected, preserved and retained. We recommend that in addition to this, the Government also ensures integrity, security and confidentiality of data or information that is transferred, accessed or deleted. We also recommend that the Bill requires the Government to prescribe a framework under Section 5(2) for agency privacy policies to ensure that they are interoperable and consistent between different departments of the Government. - Functions of the Central Commissioner
Section 8 of the Bill grants the Central Commissioner the power to perform any or all of the functions listed in the provision including Section 8(f) which refers to the power of the State Commissioner in conducting the work of the State Government agencies. A Central Government authority may not have a say in all matters under the purview of the State Governments. This aspect has been left out for consideration while drafting this provision and hence it needs to be relooked at. - Cut-off Date for Implementation
While the Bill mandates a cut off period of 180 days for the Government to finalise on the scope, framework and manner of service delivery under its provisions, it states that the Government “may” prescribe a framework for implementation of the provisions. It is recommended, for the purpose of ensuring speedy implementation of the provisions, that the term “may” in Section 5(2) be replaced by “shall”. - Transparency of Government Agencies
Transparency and accountability of the Government towards the citizen is as important as the transparency of the citizen towards the Government. Therefore, the provisions of the Bill must ensure that the Government activities are transparent to the citizens by making available to the citizens, details of the responsible officials under the Bill, manner of service delivery and other relevant information in this regard.
Say 'Password' in Hindi
On skype the other day, a friend narrated an incident that made the otherwise familiar terrains of the internet, uncanny. His grandmother, who had recently acquired a taste for Facebook, had signed off on a message saying “Love, Granny”. For people of the xoxo generation, this sounds commonplace, in fact it might even be archaic. However, for my friend, who had never thought of his emotions for his grandmother as “love”, it produced a moment of sheer strangeness.
In Gujarati, it would have been silly to think of your emotions for family as “love”. There are better nuances. The emotional connect between lovers is different from the affective relationship with parents. The fondness for siblings is different from the bond with friends. And it was unnerving, for him, to have this range of emotions suddenly condensed into “love”. Like many of us polyglots who work in the rapidly digitising world of the World Wide Web, he was experiencing the gap between the mother tongue and the other tongue. It is an experience that is quite common to non-native speakers of English, who have to succumb to de facto English language usage on the global web and often find themselves at sea about how to translate emotions, histories and experiences into a language which does not always accommodate them.
This experience only becomes more intense for people who are fluent neither in the English language nor in international online English. This question of localisation of language remains one of the biggest gating factors of the internet. It also remains, after literacy and skills, the biggest impediment to including people from non-mainstream geopolitics in discussions online. Several global linguistic majorities have dealt with this by producing different language webs. Spanish, Chinese, Japanese and German are among the largest non-English language internets which are in operation now. However, in post-colonial countries like India, where linguistic diversity is the order of the day, the efforts at localisation have been sporadic and not very popular.
There are many facets to the implementation of localisation practices. It requires developing local language fonts so that people don’t have to merely transliterate local words using an English language script. These fonts further need to be made translatable into other languages, identified by machine translations. Keyboards and hardware infrastructure, which grants ease of access to the users need to be built. Tool kits to de-Anglify the computer language, code, browser signs etc. are being developed. There are many attempts being made by public and private bodies in the country to produce this ecology of localisation, both at the level of hardware and software.
And yet, adoption of localisation tools, despite a growing non-urban user base, remains low. Most people engage with the digital and online services through English, even though their fluency with the language might be low. One of the reasons why localisation of Indic language content is facing so much resistance is because of a narrow understanding of localisation as linguistic translation. Most attempts at localisation in the country merely think of translating English terms like “browser”, “code”, or “password” into the regional languages. In many instances, the term is merely rewritten in the local script.
Such an approach to localisation ignores the fact that the language of technology does not only produce new expressions and words, but also new ways of thinking. While localising the English language content, care also has to be given to translating the contexts, which the words and phrases carry. Do a simple exercise. Take the word “Password”. Try and translate this into your local language so that it makes complete sense to a native speaker. You will realise that just saying “Password” doesn’t mean much and that it requires background information to make that word intelligible to a community.
The second is that localisation is not merely about giving rights to generate content online. While the Web 2.0 wave of user-generated content is ruling the internet now, we must realise that most people come online to consume as much, if not more than, what they generate. Policies that promote local language information production, translation projects etc. need to be in place so that the minimum threshold of information is available online in languages other than English. Government documents, state records, public artifacts, etc. need to be digitised and made available in local languages so that people can access data online.
Localisation is not only about language and translations. It is about changing the top-down approach; instead of forcing existing concepts on to material realities which don’t always fit them, it is time to see that the true power of digital technologies is in building bottom-up models where everyday practice can be captured through localised vocabularies that allow for users to say, “I love you,” to anybody, in a language, and meaning that makes sense to them.
Do You Want to be Watched?
Privacy is a necessary but not sufficient condition for security. A bank safe is safe only because the keys are held by a trusted few. No one else can access these keys or has the ability to duplicate them. The 2008 Amendment of the Information Technology (IT) Act and their associated rules notified April 2011 proposes to eliminate whatever little privacy Indian netizens have had so far. Already as per the internet service provider (ISP) license, citizens using encryption above 40-bit were expected to deposit the complete decryption key with the Ministry of Communications and Information Technology. This is as intelligent as citizens of a neighbourhood making duplicates of the keys to their homes and handing them over at the local police station. With the IT Act’s latest rules things get from bad to worse. (For an analysis of the new rules under the IT Act, see the In Parliament section of this issue).
Now imagine my daughter visits the neighborhood cybercafe, the manager would now be entitled to scan her ID document and take a photograph of her using his own camera. He would also be authorised to capture her browser history including unencrypted credentials and authentication factors. He would then store this information for a period of one year and provide them to any government entity that sends him a letter. He could continue to hold on to the files as there would be no clear guidelines or penalties around deletion. The ISP that provides connectivity to the cybercafe would store a copy of my daughter’s Internet activities for two years. None of our ISPs publish or provide on request a copy of their data retention policies.
Now suppose my daughter used an online peer-production like Wikipedia or social-media platform like MySpace to commit an act of blasphemy by drawing fan-art for her favorite Swedish symphonic black metal band. A neo-Pentecostal Church sends a takedown notice to the website hosting the artwork. Unfortunately, this is a fringe Web 2.0 platform run by Indian entrepreneur who happens to be a friend of yours. When the notice arrived, our entrepreneur was in the middle of a three-week trek in the Himalayas. Even though he had disabled anonymous contributions and started comprehensive data retention of user activity on the site, unfortunately he was not able to delete the offending piece of content within 36 hours. If the honourable judge is convinced, both your friend and my daughter would be sitting in jail for a maximum of three years for the newly christened offence of blasphemous online speech.
You might dismiss my misgivings by saying “after all we are not China, Saudi Arabia or Myanmar”, and that no matter what the law says we are always weak on implementation. But that is completely missing the point. The IT Act appears to be based on the idea that the the Indian public can be bullied into self-censorship via systemic surveillance. Employ tough language in the law and occasionally make public examples of certain minor infringers. There have been news reports of young men being jailed for using expletives against Indian politicians or referring to a head of state as a “rubber stamp.” The message is clear—you are being watched so watch your tongue.
Surveillance capabilities are not a necessary feature of information systems. They have to be engineered into these systems. Once these features exists, they could potentially serve both the legally authorised official and other undesirable elements. Terrorists, cyber-warriors and criminals will all find systems with surveillance capabilities easier to compromise. In other words, surveillance compromises security at the level of system design. There were no internet connections or phone lines in the bin Laden compound—he was depending on store and forward arrangement based on USB drives. Do we really think that registration of all USB drives, monitoring of their usage and the provision of back doors to these USBs via master key would have lead the investigators to him earlier? Has the ban on public wi-fi and the current ID requirements at cyber-cafes led to the arrest of any terrorists or criminals in India? Where is the evidence that resource hungry blanket surveillance is providing return on investment? Intelligence work cannot be replaced with resource-hungry blanket surveillance. Unnecessary surveillance distracts the security with irrelevance.
Increase in security levels is not directly proportional to increase in levels of surveillance. A certain amount of surveillance is unavoidable and essential. But after the optimum amount of surveillance has been reached, additional surveillance only undermines security. The multiple levels of data retention at the cybercafe, by the ISP and also by the application service provider does not necessarily make Indian cyberspace more secure. On the contrary, redundant storage of personal sensitive information only acts as multiple points of failure and leaks—in the age of Niira Radia and Amar Singh one does not have be reminded of authorised and unauthorised surveillance and their associated leaks.
Finally, there is the question of perception management. Perceptions of security does not only depend on reality but on personal and popular sentiment. There are two possible configurations for information systems—one, where the fundamental organising principle is trust or second, where the principle is suspicion. Systems based on suspicion usually gives rise to criminal and corrupt behavior. If the state were to repeatedly accuse its law-abiding citizens of being terrorists and criminals, it might end up provoking them into living up to these unfortunate expectations. If citizens realise that every moment of their digital lives is being monitored by multiple private and government bodies—they will begin to use anonymisation and encryption technology round the clock even when it is not really necessary. Ordinary citizens will be forced to visit the darker and nastier corners of the internet just to download encryption tools and other privacy enabling software. Like the prohibition, this will only result in further insecurity and break-down in the rule of law.
Read the original here
Snooping Can Lead to Data Abuse
THE NATGRID, aiming to link databases of 21 departments and ministries for better counter- terror measures, adopts blunt policy approach, subjecting every citizen to the same level of blanket surveillance, instead of a targeted approach that intelligently focuses on geographic or demographic areas that are currently important.
All you manage to do with the current approach help software, hardware and biometric equipment vendors achieve their sales targets. It is quite unlikely that security agencies will learn anything insightful by putting everybody under the same degree of surveillance. There is no scientific evidence to show that we will be a safer nation if the government eavesdropped into all aspects of a citizen’s life. Targeted surveillance, on the other hand, is like good old- fashioned detective work. Put a particular section — of potential troublemakers — under surveillance and leave the others alone.
With round- the- clock, 100- per cent, 360- degree surveillance, all the data is scrutinised all the time. The more effective approach is to sample and collect data while maintaining data trails. If anything suspicious is noticed, the rest of the trail can be dug up. Blanket surveillance only leads to leaks and abuse and tremendous distraction. The surveillance infrastructure will be overburdened as 99 per cent of the records and files scanned will be of no interest terms of fighting terrorism, etc.
The 21 databases need to be opened only when there is anything suspicious in any of the extracted and scrutinised samples or subsets. If there is a suspicious pattern, it should lead to opening of subsets in all the databases. Obviously, there should be ways in which the databases can talk to each other — demand for a particular subset, and not for all the records to be available to agencies all the time.
The NATGRID has to be able to let investigators selectively go in and out of the necessary subsets data. No one should be able to have a 360 degree view of all activities of all Indians. AS OF now, the NATGRID design does not appear to have a safeguard for data abuse. And no matter what you see Hollywood movies, this configuration does not exist in Europe or the US. Two important forms of protections that should be available in democracies with robust privacy laws are missing in India. The first is breach notification.
If intelligence agencies and the police have looked up your files, you have a right to be informed. Secondly, you can request for a copy of the information that is maintained on you and request modifications if the data is inaccurate, so as to prevent harassment. Such checks and balances are necessary an intelligent and appropriate surveillance regime.
Merging all 21 databases for 1.2 billion people into a single system only provides a juicy target for any internal or external enemy. From the perspective national security, it is a foolish thing to do. Terrorist groups will be able to target a single failure point destroy over a billion lives. Since the current configuration of the NATGRID only undermines national security, one is forced conclude that national security is a false pretext.
This explains the deep scepticism among many the intelligence agencies involved. The real purpose of the project is to scare citizens in the age of Arab springs. The NATGRID is a disciplinary measure aimed at social engineering of citizens’ behaviour. Unfortunately, our media has been misled by the corporate cheerleaders of this humongous waste of money.
The writer is executive director at the Centre for Internet and Society in Bangalore.
( As told to Max Martin)
Privacy and Security Can Co-exist
TODAY, the national discourse around the “ right to privacy” posits privacy as antithetical to security.
Nothing can be farther from the truth. Privacy is a necessary but not sufficient condition for security. A bank safe is safe only because the keys are held by a trusted few. No one else can access these keys or has the ability to duplicate them. The 2008 amendment of the IT Act and their associated rules notified April 2011 propose to eliminate whatever little privacy Indian netizens have had so far. Already as per the Internet Service Provider ( ISP) licence, citizens using encryption above 40- bit were expected to deposit the complete decryption key with the Ministry of Communications and Information Technology. This is as intelligent as citizens of a neighbourhood making duplicates of the keys to their homes and handing them over at the local police station.
Surveillance
Surveillance in any society is like salt in cooking — essential in small quantities but completely counter- productive even slightly in excess. Blanket surveillance makes privacy extinct, it compromises anonymity, essential ingredients for democratic governance, free media, arts and culture, and, most importantly, commerce and enterprise. The Telegraph Act only allowed for blanket surveillance as the rarest of the rare exception. The IT Act, on the other hand, mandates multitiered blanket surveillance of all lawabiding citizens and enterprises.
When your mother visits the local cybercafe to conduct an e- commerce transaction, at the very minimum there are two levels of blanket surveillance. According to the cyber- cafe rules, all her transaction logs will be captured and stored by the operator for a period of one year. This gentleman would also have access to her ID document and photograph. The ISPs would also store her logs for two years to be in compliance with the ISP licence ( even though none of them publish a data- retention policy). Some e- commerce website, to avoid liability, will under the Intermediary Due Diligence rules also retain logs.
Data retention at the cyber- cafe, by the ISP and also by the application service provider does not necessarily make Indian cyberspace more secure. On the contrary, redundant storage of sensitive personal information only opens up multiple points of failure and leaks — in the age of Nira Radia and Amar Singh no sensible bank would accept such intrusion into their core business processes.
Surveillance capabilities are not a necessary feature of information systems.
They have to be engineered into these systems. Once these features exist they could potentially serve both the legally authorised official and undesirable elements.
Terrorists, cyber- warriors and criminals will all find systems with surveillance capabilities easier to compromise.
In other words, surveillance compromises security at the level of system design. There were no Internet or phone lines in the Bin Laden compound — he was depending on a store and forward arrangement based on USB drives. Do we really think that registration of all USB drives, monitoring of their usage and the provision of back doors to these USBs via a master key would have led the investigators to him earlier?
Myth
Increase in security levels is not directly proportional to an increase in levels of surveillance gear. This is only a myth perpetuated by vendors of surveillance software and hardware via the business press. You wouldn't ask the vendors of Xray machines how many you should purchase for an airport, would you? An airport airport with 2,000 X- ray machines is not more secure than one with 20. But in the age of UID and NATGRID, this myth has been the best route for reaching salestargets using tax- payers’ money.
Surveillance must be intelligent, informed by evidence and guided by a scientific method. Has the ban on public WiFi and the current ID requirements at cyber- cafes led to the arrest of terrorists or criminals in India? Where is the evidence that more resource hungry blanket surveillance is going to provide a return on the investment? Unnecessary surveillance is counter- productive and distracts the security agenda with irrelevance.
Finally, there is the question of perception management. Perceptions of security do not only depend on reality but on personal and popular sentiment. There are two possible configurations for information systems — one, where the fundamental organising principle is trust and second, where the principle is suspicion.
Systems based on suspicion usually give rise to criminal and corrupt behaviour.
Perception
If the state were to repeatedly accuse its law- abiding citizens of being terrorists and criminals it might end up provoking them into living up to these unfortunate expectations. If citizens realise that every moment of their digital lives is being monitored by multiple private and government bodies, they will begin to use anonymisation and encryption technology round the clock even when it is not really necessary. Ordinary citizens will be forced to visit the darker and nastier corners of the Internet just to download encryption tools and other privacy enabling software. Like prohibition this will only result in further insecurity and break- down of the rule of law.
The writer is executive director of the Bangalore- based Centre for Internet and Society.
Read the original published in Mail Today here
You Have the Right to Remain Silent
In March 2011, Indian media - both social and traditional - was ablaze with fears that a new set of rules, proposed to complement the IT (Amendment) Act 2008, would thwart the freedom of expression of India's bloggers: contrary to standard international practice, the Intermediary Due Dilligence Rules seemed intent on making bloggers responsible for comments made by readers on their site. Only a few weeks earlier, the threat of online censorship had manifested itself in a different form: although the block was implemented unevenly, mobile applications market space Mobango, bulk SMS provider Clickatell, hacking-related portal Zone-H.com and blogs hosted on Typepad were suddenly no longer accessible for most Indian netizens, without warning or explanation.
Censorship in India is nothing new. At the time of Independence, there was widespread fear among its lawmakers that unrestricted freedom of expression could become a barrier to the social reforms necessary to put the country on Nehru's path to development – particularly as the memory of Partition continued to be vivid. Although freedom of expression is guaranteed by the Constitution, it is therefore subject to a fairly extensive list of so-called "reasonable" restrictions: the sovereignty and integrity of India, the security of the State, friendly relations with foreign States, public order, decency or morality, or in relation to contempt of court, defamation or incitement to an offence. But while this long list might have made sense at the time of Partition, in the mature democracy that India has now become, its existence, and the numerous opportunities for censorship and surveillance that it has enabled or justified, seems out of place. Indeed, though all these restrictions in themselves are considered acceptable internationally, there are few other democratic states that include all of them in the basic laws of their land.
An appetite for censorship does not only exist among India's legislature and judiciary, however. Especially since the early nineties, instances of vigilante groups destroying art, preventing film screenings, or even attacking offending artists, writers and editors have become noteworthy for their regularity. But it is worth noting that even more progressive sections of society have not been averse to censorship: for example, section of the Indian feminist movement have voiced strong support for the Indecent Representation of Women Act that seeks to censor images of women which are derogatory, denigrating or likely to corrupt public morality.
What connects all these efforts? A belief that suppressing speech and opinions makes it possible to contain the conflicts that emanate from India's tremendous diversity, while simultaneously ensuring its homogenous moral as much as political development. But if the advent of satellite television already revealed the vulnerabilities of this strategy, the Internet has made clear that in the long term, it is simply untenable. It is not just that the authors of a speech act may not be residents of India; it is that everybody can now become an author, infinitely multiplying the number of expressions that are produced each year and that thus could come within the Law's ambit. In this context, even if it may still have a role, suppression clearly can no longer be the preferred or even dominant technology of choice to manage disagreements. What is urgently needed is the building of a much stronger culture of respectful disagreement and debate within and across the country's many social groups. If more and more people are now getting an opportunity to speak, what we need to make sure is that they end up having a conversation.
Yet the government of India so far has mostly continued on the beaten track, putting into place a range of legislations and policies to meticulously monitor and police the freedom of expression of netizens within its borders. Thus, for example, section 66F(1)(B) of the IT (Amendment) Act 2008 defines "cyberterrorism" so broadly as to include the unauthorised access to information on a computer with a belief that that information may be used to cause injury to...decency or morality. The suggested sentence may extend to imprisonment for life. The proposed Intermediary Due Dilligence Rules 2011 privatise the responsibility for censorship by making intermediaries responsible for all content that they host or store, putting unprecedented power over our acts of speech into the hands of private bodies. The proposed Cyber Cafe Rules 2011 order that children who do not possess a photo identity card need to be accompanied by an adult who does, constraining the Internet access of crores of young people among the less advantaged sections of society in particular. And while the US and other Western countries continue to debate the desireability of an Internet Kill Switch, the Indian government obtained this prerogative through section 69A of the IT (Amendment Act) 2008 years ago.
Such measures are given extra teeth by being paired with unprecedented systems of surveillance. For example, there are proposals on the table that make it obligatory for telecommunication carriers and manufacturers of telecommunications equipment to ensure their equipment and services have built-in surveillance capabilities. While at present, records are only kept if there is a specific requirement by intelligence or security agencies, the Intelligence Bureau has proposed that ISPs keep a record of all online activities of all customers for at least six months. The IB has also suggested putting into place a unique identification system for all Internet users, whereby they would be required to submit some form of online identification every time they go online.
Proponents of such legislation often point to the new threats to safety and security that the Internet poses to defend these measures, and it is indeed a core obligation of any state to ensure the safety of its citizens. But the hallmark of a democracy is that it carefully balances any measures to do so with the continued guarantee of its citizens' fundamental rights. Despite the enormous changes and challenges that the Internet brings for freedom of expression everywhere, such an exercise seems to sadly not yet have been systematically undertaken in India so far.
The recent blocking of websites with which we started this article reflects the urgent need to do so. In response to RTI applications by the Centre for Internet and Society and Medianama, the Department of Information Technology, which is authorised to order such blocks, admitted to blocking Zone-H, but not any of the other websites affected earlier this year. In an interview with The Hindu, the Department of Telecommunication too had denied ordering the blocking of access, despite the fact that some users trying to access Typepad had reported seeing the message "this site has been blocked as per request by Department of Telecom" on their screen. In the mean time, Clickatell and Mobango remain inaccessible for this author at the time of writing. That we continue to be in the dark as to why this is so in the world's largest democracy deserves to urgently become a rallying point.
i4D Interview: Social Networking and Internet Access
Mechanism of Self-Governance Needed for Social Networks
Should social networking sites be governed, and if yes, in what way?
 A
call for either monitoring or censoring Social Networking Sites has
long been proved ineffectual, with the users always finding new ways of
circumventing the bans or the blocks that are put into place. However,
given the ubiquitous nature of SNS and the varied age-groups and
interests that are represented there, governance, which is
non-intrusive and actually enables a better and more
effective experience of the site, is always welcome. The presumed
notion of governance is that it will set processes and procedures in
place which will eventually crystallise into laws or regulations.
However, there is also another form of governance - governance as
provided by a safe-keeper or a guardian, somebody who creates symbols
of caution and warns us about being cautious in certain areas. In the
physical world, we constantly face these symbols and signs which remind
us of the need to be aware and safe. Creation of a vocabulary of
warnings, signs and symbols that remind us of the dangers within SNS is
a form of governance that needs to be worked out. This can be a
participatory governance where each community develops its own concerns
and addresses them. What is needed is a way of making sure that these
signs are present and garner the attention of the user.
A
call for either monitoring or censoring Social Networking Sites has
long been proved ineffectual, with the users always finding new ways of
circumventing the bans or the blocks that are put into place. However,
given the ubiquitous nature of SNS and the varied age-groups and
interests that are represented there, governance, which is
non-intrusive and actually enables a better and more
effective experience of the site, is always welcome. The presumed
notion of governance is that it will set processes and procedures in
place which will eventually crystallise into laws or regulations.
However, there is also another form of governance - governance as
provided by a safe-keeper or a guardian, somebody who creates symbols
of caution and warns us about being cautious in certain areas. In the
physical world, we constantly face these symbols and signs which remind
us of the need to be aware and safe. Creation of a vocabulary of
warnings, signs and symbols that remind us of the dangers within SNS is
a form of governance that needs to be worked out. This can be a
participatory governance where each community develops its own concerns
and addresses them. What is needed is a way of making sure that these
signs are present and garner the attention of the user.
How do we address the concerns that some of the social networking spaces are not "child safe"?
The question of child safety online has resulted in a raging debate. Several models, from the cybernanny to monitoring the child's activities online ,have been suggested at different times and have more or less failed. The concerns about what happens to a child online are the same as those about what happens to a child in the physical world. When the child goes off to school, or to the park to play, we train and educate them about things that they should not be doing -- suggesting that they do not talk to strangers, do not take sweets from strangers, do not tell people where they live, don't wander off alone -- and hope that these will be sufficient safeguards to their well being. As an added precaution, we also sometimes supervise their activities and their media consumption. More than finding technical solutions for safety online, it is a question of education and training and some amount of supervision to ensure that the child is complying with your idea of what is good for it. A call for sanitising the internet is more or less redundant, only, in fact, adding to the dark glamour of the web and inciting younger users to go and search for material which they would otherwise have ignored.
What are the issues, especially around identities and profile information privacy rights of users of social networking sites?
The main set of issues, as I see it, around the question of identities, is the mapping of the digital identities to the physical selves. The questions would be : What constitutes the authentic self? What is the responsibility of the digital persona? Are we looking at a post-human world where online identities are equally a part of who we are and are sometimes even more a part of who we are than our physical selves? Does the older argument of the Original and the Primary (characteristics of Representation aesthetics) still work when we are talking about a world of 'perfect copies' and 'interminable networks of selves' (characteristics of Simulation)? How do we create new models of verification, trust and networking within an SNS? Sites like Facebook and Orkut, with their ability to establish looped relationships between the users, and with the notion of inheritance (¨friend of a friend of a friend of a friend¨), or even testimonials and open 'walls' and 'scraps' for messaging, are already approaching these new models of trust and friendship.
How do we strike a balance between the freedom of speech and the need to maintain law and order when it comes to monitoring social networking sites?
I am not sure if the 'freedom of speech and expression' and the 'maintaining of law and order' need to be posited as antithetical to each other. Surely the whole idea of 'maintaining law and order' already includes maintaining conditions within which freedom of speech and expression can be practiced. Instead of monitoring social networking sites to censor and chastise (as has happened in some of the recent debates around Orkut, for example), it is a more fruitful exercise to ensure that speech, as long as it is not directed offensively towards an individual or a community, needs to be registered and heard. Hate speech of any sort should not be tolerated but that is a fact that is already covered by the judicial systems around the world.
What perhaps, is needed online, is a mechanism of self-governance where the community should be able to decide the kinds of actions and speech which are valid and acceptable to them. People who enter into trollish behaviour or hate speak, automatically get chastised and punished in different ways by the community itself. To look at models of better self-governance and community mobilisation might be more productive than producing this schism between freedom of speech on the one hand and the maintenance of law and order on the other.
An Open Letter on Internet Governance to the UN Internet Governance Forum
This open letter brings up concerns of democratic deficit in internet governance worldwide, and is addressed to the UN Internet Governance Forum (IGF). It will be delivered at the IGF's 3rd Annual Meeting at Hyderabad, India, from 3rd to 6th December, 2008.
The letter includes an information sheet exemplifying some of the problems of democratic deficit in internet governance.
The text of the letter is as follows:
-------------------------------------------------------------
The IGF must ACT NOW against the threat to the public-ness and the egalitarian nature of the Internet
The undersigned wish to express their deep concern that the UN Internet Governance Forum (IGF), created by the World Summit on the Information Society in 2005 as an Internet ‘policy dialogue’ forum, is largely failing to address key public interest and policy issues in global Internet governance – including that of democratic deficit.
Who shapes the Internet, as the Internet shapes our new social context?
The Internet represents the single most important technical advance of our society in a long time, so much so that it defines a new emerging social paradigm. The basic characteristics of the Internet determine the contours of the emerging social order in many important ways. The Internet was conceived as, and still largely is, an extensive communication system which is democratizing, and has little respect for established social hierarchies. Interactions and associations built over this new ‘techno-social’ system have, therefore, held the promise of a more egalitarian society.
The era of innocence of the Internet however appears to be fast approaching its end. Today, the Internet of the future – the very near future – is being shaped insidiously by dominant forces to further their interests. (See the fact-sheet on the following page for some illustrations of this.) Unfortunately, global policy forums have largely failed to articulate, much less act on, crucial Internet policy issues, which concern the democratic possibilities for our societies.
The IGF needs to act now!
As the Internet Governance Forum convenes for its third annual meeting, between 3rd and 6th December, 2008, in Hyderabad, India, it must take immediate steps to anchor and discuss important global public interest and policy issues involved in Internet governance. If it does not act now, it may get seen as a space that only provides an illusion of a public policy dialogue, and, consequently, as being co-opted in furthering the agenda of dominant forces that are shaping the Internet as per their narrow interests. We therefore strongly urge the IGF to directly address the following key global public interest and policy issues:
- Increasing corporatisation of the Internet
- Increasing proprietisation of standards and code that go into building the Internet
- Increasing points of control being embedded into the Internet in the name of security and intellectual property violations
- Huge democratic deficit in global Internet governance
We exhort the IGF to adopt clear directions for engaging with these crucial public policy issues. The IGF should come out with a clear work plan at its forthcoming meeting in Hyderabad to address the four key areas listed above.
The global community – comprising not only people who currently have access to the Internet, but also the un-connected billions who are being impacted by it nevertheless – will judge the meaningfulness and legitimacy of the IGF in terms of what progress it is able to make on these issues.
Alternative Law Forum, Bangalore
Centre for Internet and Society, Bangalore
Delhi Science Forum, New Delhi
Free Software Foundation - India
IT for Change, Bangalore
Knowledge Commons, New Delhi
Information Sheet
How the Public-ness and Egalitarian Nature of the Internet is Threatened
– Some Examples
Corporatisation of the Internet
Largely unsuspected by most of its users, the Internet is rapidly changing from being a vast ‘public sphere’, with a fully public ownership and a non-proprietary nature, to a set of corporatised privately-owned networks.
On the one hand, telecom companies are carving out the Internet into privately-owned networks – controlling the nature of transactions over these networks. They seek to differentially charge content providers, while also building wholly private networks offering exclusive content relay services. Developments like video/TV over Internet Protocol and the provision of controlled and selective Internet services over mobiles are contributing to increasing network-operators’ control over the Internet, with a corresponding erosion of its public-ness.
On the other hand, the commons of the Internet is also being overwhelmed and squeezed out by a complete domination of a few privately owned mega-applications such as Google, Facebook, Youtube etc.
Proprietarisation of standards and code that build the Internet
One of the main ways of appropriating the commons of the Internet is through the increasing use of proprietary and closed standards and code in building the Internet system. Such appropriation allows the extortion of illegitimate rent out of the many new forms of commons-based activities that are being made possible through the Internet.
Embedding control points in the Internet
A growing confluence of corporatist and statist interests has led to the embedding of more and more means of control into the Internet in a manner that greatly compromises citizens’ rights and freedoms. Whether it is the pressure on Internet
Service Providers to examine Internet traffic for ‘intellectual property’ violations; or imposition of cultural and political controls on the Internet by states within their boundaries; or ITU’s work on IP trace-back mechanisms; or the tightening of US
control over the global Internet infrastructure in the name of securing the root zone file and the domain name system, these new forms of controlling the Internet are being negotiated among dominant interests away from public scrutiny and wider public interest-based engagements.
Democratic deficit in global Internet governance
The current global Internet governance regime – a new-age privatized governance system professing allegiance mostly to a single country, the US – has proven to be an active instrument of perpetuation of dominant commercial and geo-political interests. Lately, OECD countries have begun some work on developing public policy principles that, due to the inherently global nature of the Internet, can be expected to become globally applicable. It is quite unacceptable that OECD countries shirk from discussing the same public policy issues at global public policy forums like the IGF that they discuss among themselves at OECD meetings. Apparently, developing countries are expected to focus on finding ways to reach connectivity to their people, and not burden themselves with higher-level Internet governance issues!
People’s and communities’ right to self-determination and participation in governance of issues that impact their lives should underpin global Internet governance.
---------------------------------------------
You can download the letter here (.pdf format).
Letter to ICANN on NCSG
Dear Sir or Madam,
Greetings from the Centre for Internet and Society - Bangalore. We are a Bangalore based research and advocacy organisation promoting consumer and citizen rights on the Internet. We currently focus on IPR reform, IPR alternatives and electronic accessibility by the disabled. Please see our website <http://cis-india.org> for more information about us and our activities.
It has come to our attention that ICANN is imposing the ICANN staff-drafted charter for a Noncommercial Stakeholder Group (NCSG) and ignoring the version drafted by civil society. As you know, the civil society version was drafted using a consensus process and more than 80 international noncommercial organizations, including mine, support it.
This is an unacceptable situation since the governance structures contained within the NCSG charter determine how effectively noncommercial users can influence policy decisions at ICANN in years to come. On behalf of Internet users in India - I would strongly urge you to reject the staff drafted version of the charter and adopt the version drafted and endorsed by civil society.
Best wishes,
Sunil Abraham
Executive Director
Centre for Internet and Society
Comments on the Draft Rules under the Information Technology Act
Comments on the Draft Rules under the Information Technology Act as Amended by the Information Technology (Amendment) Act, 2008
Submitted by the Centre for Internet and Society, Bangalore
Prepared by Ananth Padmanabhan, Advocate in the Madras High Court
Interception, Monitoring and Decryption
Section 69
The section says:
- Where the Central Government or a State Government or any of its officer specially authorised by the Central Government or the State Government, as the case may be, in this behalf may, if satisfied that it is necessary or expedient so to do in the interest of the sovereignty or integrity of India, defence of India, security of the State, friendly relations with foreign States or public order or for preventing incitement to the commission of any cognizable offence relating to above or for investigation of any offence, it may subject to the provisions of sub-section (2), for reasons to be recorded in writing, by order, direct any agency of the appropriate Government to intercept, monitor or decrypt or cause to be intercepted or monitored or decrypted any information generated, transmitted, received or stored in any computer resource.
- The procedure and safeguards subject to which such interception or monitoring or decryption may be carried out, shall be such as may be prescribed.
- The subscriber or intermediary or any person in-charge of the computer resource shall, when called upon by any agency referred to in sub-section (1), extend all facilities and technical assistance to-
(a) provide access to or secure access to the computer resource generating transmitting, receiving or storing such information; or
(b) intercept, monitor, or decrypt the information, as the case may be; or
(c) provide information stored in computer resource.- The subscriber or intermediary or any person who fails to assist the agency referred to in sub-section (3) shall be punished with imprisonment for a term which may extend to seven years and shall also be liable to fine.
Recommendation #1
Section 69(3) should be amended and the following proviso be inserted:
Provided that only those intermediaries with respect to any information or computer resource that is sought to be monitored, intercepted or decrypted, shall be subject to the obligations contained in this sub-section, who are, in the opinion of the appropriate authority, prima facie in control of such transmission of the information or computer resource. The nexus between the intermediary and the information or the computer resource that is sought to be intercepted, monitored or decrypted should be clearly indicated in the direction referred to in sub-section (1) of this section.
Reasons for the Recommendation
In the case of any information or computer resource, there may be more than one intermediary who is associated with such information. This is because “intermediary” is defined in section 2(w) of the amended Act as,
“with respect to any electronic record means any person who on behalf of another person receives, stores or transmits that record or provides any service with respect to that record, including telecom service providers, network service providers, internet service providers, webhosting service providers, search engines, online payment sites, online-auction sites, online-market places and cyber cafes”.
The State or Central Government should not be given wide-ranging powers to enforce cooperation on the part of any such intermediary without there being a clear nexus between the information that is sought to be decrypted or monitored by the competent authority, and the control that any particular intermediary may have over such information.
To give an illustration, merely because some information may have been posted on an online portal, the computer resources in the office of the portal should not be monitored unless the portal has some concrete control over the nature of information posted in it. This has to be stipulated in the order of the Central or State Government which authorizes interception of the intermediary.
Recommendation #2
Section 69(4) should be repealed.
Reasons for the Recommendation
The closest parallels to Section 69 of the Act are the provisions in the Telegraph Rules which were brought in after the decision in PUCL v. Union of India, (1997) 1 SCC 301, famously known as the telephone tapping case.
Section 69(4) fixes tremendous liability on the intermediary for non-cooperation. This is violative of Article 14. Similar provisions in the Indian Penal Code and Code of Criminal Procedure, which demand cooperation from members of the public as regards production of documents, letters etc., and impose punishment for non-cooperation on their part, impose a maximum punishment of one month. It is bewildering why the punishment is 7 years imprisonment for an intermediary, when the only point of distinction between an intermediary under the IT Act and a member of the public under the IPC and CrPC is the difference in the media which contains the information.
Section 69(3) is akin to the duty cast upon members of the public to extend cooperation under Section 39 of the Code of Criminal Procedure by way of providing information as to commission of any offence, or the duty, when a summons is issued by the Court or the police, to produce documents under Sections 91 and 92 of the Code of Criminal Procedure. The maximum punishment for non-cooperation prescribed by the Indian Penal Code for omission to cooperate or wilful breach of summons is only a month under Sections 175 and 176 of the Indian Penal Code. Even the maximum punishment for furnishing false information to the police is only six months under Section 177 of the IPC. When this is the case with production of documents required for the purpose of trial or inquiry, it is wholly arbitrary to impose a punishment of six years in the case of intermediaries who do not extend cooperation for providing access to a computer resource which is merely apprehended as being a threat to national security etc. A mere apprehension, however reasonable it may be, should not be used to pin down a liability of such extreme nature on the intermediary.
This would also amount to a violation of Articles 19(1)(a) as well as 19(1)(g) of the Constitution, not to mention Article 20(3). To give an example, much of the information received from confidential sources by members of the press would be stored in computer resources. By coercing them, through the 7 year imprisonment threat, to allow access to this computer resource and thereby part with this information, the State is directly infringing on their right under Article 19(1)(a). Furthermore, if the “subscriber” is the accused, then section 69(4) goes against Article 20(3) by forcing the accused to bear witness against himself.
Draft Rules under Section 69
Rule 3
Directions for interception or monitoring or decryption of any information generated, transmitted, received or stored in any computer resource under sub- section (2) of section 69 of the Information Technology (Amendment) Act, 2008 (hereinafter referred to as the said Act) shall not be issued except by an order made by the concerned competent authority who is Union Home Secretary in case of Government of India; the Secretary in-charge of Home Department in a State Government or Union Territory as the case may be. In unavoidable circumstances, such order may be made by an officer, not below the rank of a Joint Secretary to the Government of India, who has been duly authorised by the Union Home Secretary or by an officer equivalent to rank of Joint Secretary to Government of India duly authorised by the Secretary in-charge of Home Department in the State Government or Union Territory, as the case may be:
Provided that in emergency cases –
(i) in remote areas, where obtaining of prior directions for interception or monitoring or decryption of information is not feasible; or
(ii) for operational reasons, where obtaining of prior directions for interception or monitoring or decryption of any information generated, transmitted, received or stored in any computer resource is not feasible;
the required interception or monitoring or decryption of any information generated, transmitted, received or stored in any computer resource shall be carried out with the prior approval of the Head or the second senior most officer of the Security and Law Enforcement Agencies (hereinafter referred to as the said Security Agencies) at the Central Level and the officers authorised in this behalf, not below the rank of Inspector General of Police or an officer of equivalent rank, at the State and Union Territory level. The concerned competent authority, however, shall be informed of such interceptions or monitoring or decryption by the approving authority within three working days and that such interceptions or monitoring or decryption shall be got confirmed by the concerned competent authority within a period of seven working days. If the confirmation from the concerned competent authority is not received within the stipulated seven working days, such interception or monitoring or decryption shall cease and the same information shall not be intercepted or monitored or decrypted thereafter without the prior approval of the concerned competent authority, as the case may be.
Recommendation #3
In Rule 3, the following proviso may be inserted:
“Provided that in the event of cooperation by any intermediary being required for the purpose of interception, monitoring or decryption of such information as is referred to in this Rule, prior permission from a Supervisory Committee headed by a retired Judge of the Supreme Court or the High Courts shall be obtained before seeking to enforce the Order mentioned in this Rule against such intermediary.”
Reasons for the Recommendation
Section 69 and the draft rules suffer from absence of essential procedural safeguards. This has come in due to the blanket emulation of the Telegraph Rules. Additional safeguards should have been prescribed to ensure that the intermediary is put to minimum hardship when carrying on the monitoring or being granted access to a computer resource. Those are akin to a raid, in the sense that it can stop an online e-commerce portal from carrying out operations for a day or even more, thus affecting their revenue. It is therefore recommended that in any situation where cooperation from the intermediary is sought, prior judicial approval has to be taken. The Central or State Government cannot be the sole authority in such cases.
Furthermore, since access to the computer resource is required, an executive order should not suffice, and a search warrant or an equivalent which results from a judicial application of the mind (by the Supervisory Committee, for instance) should be required.
Recommendation #4
The following should be inserted after the last line in Rule 22:
The Review Committee shall also have the power to award compensation to the intermediary in cases where the intermediary has suffered loss or damage due to the actions of the competent authority while implementing the order issued under Rule 3.
Reasons for the Recommendation
The Review Committee should be given the power to award compensation to the loss suffered by the intermediary in cases where the police use equipment or software for monitoring/decryption that causes damage to the intermediary’s computer resources / networks. The Review Committee should also be given the power to award compensation in the case of monitoring directions which are later found to be frivolous or even worse, borne out of mala fide considerations. These provisions will act as a disincentive against the abuse of power contained in Section 69.
Blocking of Access to Information
Section 69A
The section provides for blocking of websites if the government is satisfied that it is in the interests of the purposes enlisted in the section. It also provides for penalty of up to seven years for intermediaries who fail to comply with the directions under this section.
The rules under this section describe the procedure which have to be followed barring which the review committee may, after due examination of the procedural defects, order an unblocking of the website.
Section 69A(3)
The intermediary who fails to comply with the direction issued under sub-section (1) shall be punished with an imprisonment for a term which may extend to seven years and also be liable to fine.
Recommendation #5
The penalty for intermediaries must be lessened.
Reasons for Recommendations
The penal provision in this section which prescribes up to seven years imprisonment and a fine on an intermediary who fails to comply with the directions so issued is also excessively harsh. Considering the fact that various mechanisms are available to escape the blocking of websites, the intermediaries must be given enough time and space to administer the block effectively and strict application of the penal provisions must be avoided in bona fide cases.
The criticism about Section 69 and the draft rules in so far as intermediary liability is concerned, will also apply mutatis mutandis to these rules as well as Section 69A.
Draft Rules under Section 69A
Rule 22: Review Committee
The Review Committee shall meet at least once in two months and record its findings whether the directions issued under Rule (16) are in accordance with the provisions of sub-section (2) of section 69A of the Act. When the Review Committee is of the opinion that the directions are not in accordance with the provisions referred to above, it may set aside the directions and order for unblocking of said information generated, transmitted, received, stored or hosted in a computer resource for public access.
Recommendation #6
A permanent Review Committee should be specially for the purposes of examining procedural lapses.
Reasons for Recommendation
Rule 22 provides for a review committee which shall meet a minimum of once in every two months and order for the unblocking of a site of due procedures have not been followed. This would mean that if a site is blocked, there could take up to two months for a procedural lapse to be corrected and it to be unblocked. Even a writ filed against the policing agencies for unfair blocking would probably take around the same time. Also, it could well be the case that the review committee will be overborne by cases and may fall short of time to inquire into each. Therefore, it is recommended that a permanent Review Committee be set up which will monitor procedural lapses and ensure that there is no blocking in the first place before all the due procedural requirements are met.
Monitoring and Collection of Traffic Data
Draft Rules under Section 69B
The section provides for monitoring of computer networks or resources if the Central Government is satisfied that conditions so mentioned are satisfied.
The rules provide for the manner in which the monitoring will be done, the process by which the directions for the same will be issued and the liabilities of the intermediaries and monitoring officers with respect to confidentiality of the information so monitored.
Grounds for Monitoring
Rule 4
The competent authority may issue directions for monitoring and collection of traffic data or information generated, transmitted, received or stored in any computer resource for any or all of the following purposes related to cyber security:
(a) forecasting of imminent cyber incidents;
(b) monitoring network application with traffic data or information on computer resource;
(c) identification and determination of viruses/computer contaminant;
(d) tracking cyber security breaches or cyber security incidents;
(e) tracking computer resource breaching cyber security or spreading virus/computer contaminants;
(f) identifying or tracking of any person who has contravened, or is suspected of having contravened or being likely to contravene cyber security;
(g) undertaking forensic of the concerned computer resource as a part of investigation or internal audit of information security practices in the computer resource;
(h) accessing a stored information for enforcement of any provisions of the laws relating to cyber security for the time being in force;
(i) any other matter relating to cyber security.
Rule 6
No direction for monitoring and collection of traffic data or information generated, transmitted, received or stored in any computer resource shall be given for purposes other than those specified in Rule (4).
Recommendation #7
Clauses (a), (b), (c), and (i) of Rule 4 must be repealed.
Reasons for Recommendations
The term “cyber incident” has not been defined, and “cyber security” has been provided a circular definition. Rule 6 clearly states that no direction for monitoring and collection of traffic data or information generated, transmitted, received or stored in any computer resource shall be given for purposes other than those specified in Rule 4. Therefore, it may prima facie appear that the government is trying to lay down clear and strict safeguards when it comes to monitoring at the expense of a citizens' privacy. However, Rule 4(i) allows the government to monitor if it is satisfied that it is “any matter related to cyber security”. This may well play as a ‘catch all’ clause to legalise any kind of monitoring and collection and therefore defeats the purported intention of Rule 6 of safeguarding citizen’s interests against arbitrary and groundless intrusion of privacy. Also, the question of degree of liability of the intermediaries or persons in charge of the computer resources for leak of secret and confidential information remains unanswered.
Rule 24: Disclosure of monitored data
Any monitoring or collection of traffic data or information in computer resource by the employee of an intermediary or person in-charge of computer resource or a person duly authorised by the intermediary, undertaken in course of his duty relating to the services provided by that intermediary, shall not be unlawful, if such activities are reasonably necessary for the discharge his duties as per the prevailing industry practices, in connection with :
(vi) Accessing or analysing information from a computer resource for the purpose of tracing a computer resource or any person who has contravened, or is suspected of having contravened or being likely to contravene, any provision of the Act that is likely to have an adverse impact on the services provided by the intermediary.
Recommendation #8
Safeguards must be introduced with respect to exercise of powers conferred by Rule 24(vi).
Reasons for Recommendations
Rule 24(vi) provides for access, collection and monitoring of information from a computer resource for the purposes of tracing another computer resource which has or is likely to contravened provisions of the Act and this is likely to have an adverse impact on the services provided by the intermediary. Analysis of a computer resource may reveal extremely confidential and important data, the compromise of which may cause losses worth millions. Therefore, the burden of proof for such an intrusion of privacy of the computer resource, which is first used to track another computer resource which is likely to contravene the Act, should be heavy. Also, this violation of privacy should be weighed against the benefits accruing to the intermediary. The framing of sub rules under this clearly specifying the same is recommended.
The disclosure of sensitive information by a monitoring agency for purposes of ‘general trends’ and ‘general analysis of cyber information’ is uncalled for as it dissipates information among lesser bodies that are not governed by sufficient safeguards and this could result in outright violation of citizen’s privacy.
Manner of Functioning of CERT-In
Draft Rules under Section 70B(5)
Section 70B provides for an Indian Computer Emergency Response Team (CERT-In) which shall serve as a national agency for performing duties as prescribed by clause 4 of this section in accordance to the rules as prescribed.
The rules provide for CERT-In’s authority, composition of advisory committee, constituency, functions and responsibilities, services, stakeholders, policies and procedures, modus operandi, disclosure of information and measures to deal with non compliance of orders so issued. However, there are a few issues which need to be addressed as under:
Definitions
In these Rules, unless the context otherwise requires, “Cyber security incident” means any real or suspected adverse event in relation to cyber security that violates an explicit or implied security policy resulting in unauthorized access, denial of service/ disruption, unauthorized use of a computer resource for processing or storage of information or changes to data, information without authorization.
Recommendation #9
The words ‘or implied’’ must be excluded from rule 2(g) which defines ‘cyber security incident’, and the term ‘security policy’ must be qualified to state what security policy is being referred to.
Reasons for Recommendation
“Cyber security incident” means any real or suspected adverse event in relation to cyber security that violates an explicit or implied security policy resulting in unauthorized access, denial of service/disruption, unauthorized use of a computer resource for processing or storage of information or changes to data, information without authorization.
Thus, the section defines any circumstance where an explicit or implied security policy is contravened as a ‘cyber security incident’. Without clearly stating what the security policy is, an inquiry into its contravention is against an individual’s civil rights. If an individual’s actions are to be restricted for reasons of security, then the restrictions must be expressly defined and such restrictions cannot be said to be implied.
Rule 13(4): Disclosure of Information
Save as provided in sub-rules (1), (2), (3) of rule 13, it may be necessary or expedient to so to do, for CERT-In to disclose all relevant information to the stakeholders, in the interest of sovereignty or integrity of India, defence of India, security of the State, friendly relations with foreign States or public order or for preventing incitement to the commission of an offence relating to cognizable offence or enhancing cyber security in the country.
Recommendation #10
Burden of necessity for disclosure of information should be made heavier.
Reasons for the Recommendation
Rule 13(4) allows the disclosure of information by CERT-In in the interests of ‘enhancing cyber security’. This enhancement however needs to be weighed against the detriment caused to the individual and the burden of proof must be on the CERT-In to show that this was the only way of achieving the required.
Rule 19: Protection for actions taken in Good Faith
All actions of CERT-In and its staff acting on behalf of CERT-In are taken in good faith in fulfillment of its mandated roles and functions, in pursuance of the provisions of the Act or any rule, regulations or orders made thereunder. CERT-In and its staff acting on behalf of CERT-In shall not be held responsible for any unintended fallout of their actions.
Recommendation #11
CERT-In should be made liable for their negligent action and no presumption of good faith should be as such provided for.
Reasons for the Recommendation
Rule 19 provides for the protection of CERT-In members for the actions taken in ‘good faith’. It defines such actions as ‘unintended fallouts’. Clearly, if information has been called for and the same is highly confidential, then this rule bars the remedy for any leak of the same due to the negligence of the CERT-In members. This is clearly not permissible as an agency that calls for delicate information should also be held responsible for mishandling the same, intentionally or negligently. Good faith can be established if the need arises, and no presumption as to good faith needs to be provided.
Draft Rules under Section 52
These rules, entitled the “Cyber Appellate Tribunal (Salary, Allowances and Other Terms and Conditions of Service of Chairperson and Members) Rules, 2009” are meant to prescribe the framework for the independent and smooth functioning of the Cyber Appellate Tribunal. This is so because of the specific functions entrusted to this Appellate Tribunal. Under the IT Act, 2000 as amended by the IT (Amendment) Act, 2008, this Tribunal has the power to entertain appeals against orders passed by the adjudicating officer under Section 47.
Recommendation #12
Amend qualifications Information Technology (Qualification and Experience of Adjudicating Officers and Manner of Holding Enquiry) Rules, 2003, to require judicial training and experience.
Reasons for the Recommendation
It is submitted that an examination of these rules governing the Appellate Tribunal cannot be made independent of the powers and qualifications of Adjudicating Officers who are the original authority to decide on contravention of provisions in the IT Act dealing with damage to computer system and failure to furnish information. Even as per the Information Technology (Qualification and Experience of Adjudicating Officers and Manner of Holding Enquiry) Rules, 2003, persons who did not possess judicial experience and training, such as those holding the post of Director in the Central Government, were qualified to perform functions under Section 46 and decide whether there has been unauthorized access to a computer system. This involves appreciation of evidence and is not a merely administrative function that could be carried on by any person who has basic knowledge of information technology.
Viewed from this angle, the qualifications of the Cyber Appellate Tribunal members should have been made much tighter as per the new draft rules. The above rules when read with Section 50 of the IT Act, as amended in 2008, do not say anything about the qualification of the technical members apart from the fact that such person shall not be appointed as a Member, unless he is, or has been, in the service of the Central Government or a State Government, and has held the post of Additional Secretary or Joint Secretary or any equivalent post. Though special knowledge of, and professional experience in, information technology, telecommunication, industry, management or consumer affairs, has been prescribed in the Act as a requirement for any technical member.
Draft Rules under Section 54
These Rules do not suffer any defect and provide for a fair and reasonable enquiry in so far as allegations made against the Chairperson or the members of the Cyber Appellate Tribunal are concerned.
Penal Provisions
Section 66A
Any person who sends, by means of a computer resource or a communication device,
(a) any information that is grossly offensive or has menacing character; or
(b) any information which he knows to be false, but for the purpose of causing annoyance, inconvenience, danger, obstruction, insult, injury, criminal intimidation, enmity, hatred or ill will, persistently by making use of such computer resource or a communication device,
(c) any electronic mail or electronic mail message for the purpose of causing annoyance or inconvenience or to deceive or to mislead the addressee or recipient about the origin of such messages,
shall be punishable with imprisonment for a term which may extend to three years and with fine.
Sec. 32 of the 2008 Act inserts Sec. 66A which provides for penal measures for mala fide use of electronic resources to send information detrimental to the receiver. For the section to be attracted the ‘information’ needs to be grossly offensive, menacing, etc. and the sender needs to have known it to be false.
While the intention of the section – to prevent activities such as spam-sending – might be sound and even desirable, there is still a strong argument to be made that words is submitted that the use of words such as ‘annoyance’ and ‘inconvenience’ (in s.66A(c)) are highly problematic. Further, something can be grossly offensive without touching upon any of the conditions laid down in Article 19(2). Without satisfying the conditions of Article 19(2), this provision would be ultra vires the Constitution.
Recommendation #13
The section should be amended and words which lead to ambiguity must be excluded.
Reasons for the Recommendation
A clearer phrasing as to what exactly could convey ‘ill will’ or cause annoyance in the electronic forms needs to be clarified. It is possible in some electronic forms for the receiver to know the content of the information. In such circumstances, if such a possibility is ignored and annoyance does occur, is the sender still liable? Keeping in mind the complexity of use of electronic modes of transmitting information, it can be said that several such conditions arise which the section has vaguely covered. Therefore, a stricter and more clinical approach is necessary.
Recommendation #14
A proviso should be inserted to this section providing for specific exceptions to the offence contained in this section for reasons such as fair comment, truth, criticism of actions of public officials etc.
Reasons for the Recommendation
The major problem with Section 66A lies in clause (c) as per which any electronic mail or electronic mail message sent with the purpose of causing annoyance or inconvenience is covered within the ambit of offensive messages. This does not pay heed to the fact that even a valid and true criticism of the actions of an individual, when brought to his notice, can amount to annoyance. Indeed, it may be brought to his attention with the sole purpose of causing annoyance to him. When interpreting the Information Technology Act, it is to be kept in mind that the offences created under this Act should not go beyond those prescribed in the Indian Penal Code except where there is a wholly new activity or conduct, such as hacking for instance, which is sought to be criminalized.
Offensive messages have been criminalized in the Indian Penal Code subject to the conditions specified in Chapter XXII being present. It is not an offence to verbally insult or annoy someone without anything more being done such as a threat to commit an offence, etc. When this is the case with verbal communications, there is no reason to make an exception for those made through the electronic medium and bring any electronic mail or message sent with the purpose of causing annoyance or inconvenience within the purview of an offensive message.
Section 66F
The definition of cyber-terrorism under this provision is too wide and can cover several activities which are not actually of a “terrorist” character.
Section 66F(1)(B) is particularly harsh and goes much beyond acts of “terrorism” to include various other activities within its purview. As per this provision,
“[w]hoever knowingly or intentionally penetrates or accesses a computer resource without authorisation or exceeding authorised access, and by means of such conduct obtains access to information, data or computer database that is restricted for reasons for the security of the State or foreign relations, or any restricted information, data or computer database, with reasons to believe that such information, data or computer database so obtained may be used to cause or is likely to cause injury to the interests of the sovereignty and integrity of India, the security of the State, friendly relations with foreign States, public order, decency or morality, or in relation to contempt of court, defamation or incitement to an offence, or to the advantage of any foreign nation, group of individuals or otherwise, commits the offence of cyber terrorism.”
This provision suffers from several defects and hence ought to be repealed.
Recommendation #15
Section 66F(1)(B) has to be repealed or suitably amended to water down the excessively harsh operation of this provision. The restrictive nature of the information that is unauthorisedly accessed must be confined to those that are restricted on grounds of security of the State or foreign relations. The use to which such information may be put should again be confined to injury to the interests of the sovereignty and integrity of India, the security of the State, friendly relations with foreign States, or public order. A mere advantage to a foreign nation cannot render the act of unauthorized access one of cyber-terrorism as long as such advantage is not injurious or harmful in any manner to the interests of the sovereignty and integrity of India, the security of the State, friendly relations with foreign States, or public order. A mens rea requirement should also be introduced whereby mere knowledge that the information which is unauthorisedly accessed can be put to such uses as given in this provision should not suffice for the unauthorised access to amount to cyber-terrorism. The unauthorised access should be with the intention to put such information to this use. The amended provision would read as follows:
“[w]hoever knowingly or intentionally penetrates or accesses a computer resource without authorisation or exceeding authorised access, and by means of such conduct obtains access to information, data or computer database that is restricted for reasons for the security of the State or foreign relations, with the intention that such information, data or computer database so obtained may be used to cause injury to the interests of the sovereignty and integrity of India, the security of the State, friendly relations with foreign States, or public order, commits the offence of cyber terrorism.”
Reasons for the Recommendation
The ambit of this provision goes much beyond information, data or computer database which is restricted only on grounds of security of the State or foreign relations and extends to “any restricted information, data or computer database”. This expression covers any government file which is marked as confidential or saved in a computer used exclusively by the government. It also covers any file saved in a computer exclusively used by a private corporation or enterprise. Even the use to which such information can be put need not be confined to those that cause or are likely to cause injury to the interests of the sovereignty and integrity of India, the security of the State, or friendly relations with foreign States. Information or data which is defamatory, amounting to contempt of court, or against decency / morality, are all covered within the scope of this provision. This goes way beyond the idea of a terrorist activity and poses serious questions. While there is no one globally accepted definition of cyberterrorism, it is tough to conceive of slander as a terrorist activity.
To give an illustration, if a journalist managed to unauthorisedly break into a restricted database, even one owned by a private corporation, and stumbled upon information that is defamatory in character, he would have committed an act of “cyber-terrorism.” Various kinds of information pertaining to corruption in the judiciary may be precluded from being unauthorisedly accessed on the ground that such information may be put to use for committing contempt of court. Any person who gains such access would again qualify as a cyber-terrorist. The factual situations are numerous where this provision can be put to gross misuse with the ulterior motive of muzzling dissent or freezing access to information that may be restricted in nature but nonetheless have a bearing on probity in public life etc. It is therefore imperative that this provision may be toned down as recommended above.
IT Act and Commerce
This post analyses the amendments brought about to the Information Technology Act, 2000 (“IT Act 2000”) through the recent 2008 amendments (“IT Act 2008”).
Definitions
The IT Act 2008 has introduced a few additional definitions to the list of definitions originally included in the IT Act 2000. These definitions have either amplified the existing provisions or been introduced in order to address new issues required to be defined in the context of the newly introduced provisions in the statute. Some of the significant definitions have been discussed below:
Computer Network
The definition of “computer network” has been amended to specifically include the wireless interconnection of computers. While wireless technology did fall within the scope of the IT Act under the rather generic head of “other communication media”, the Amendment Act clarifies the scope of the IT Act by expressly including the term “wireless”.
Communication Devices
The IT Amendment Bill, 2006, had provided an explanation for “communication devices” under Section 66A. This definition has been moved into the definition section and now applies across all sections of the IT Act 2008. “Communication devices” is defined to mean “a cell phone, personal digital assistance (PDA) device or combination of both or any device used to communicate, send or transmit any text, video, audio or image”.
There has been case law even under the IT Act that has held mobile phones to fall within the ambit of the IT Act, as a result of which all the provisions of the Act that apply to computers are equally applicable to mobile phones. This amendment only makes that position more explicit.
Electronic Signatures
One of the major criticisms of the IT Act 2000 was the fact that it was not a technology neutral legislation. This was specifically so in relation to the provisions in the IT Act 2000 relating to the use of digital signatures for the purpose of authentication of electronic records. The statute made specific reference to the use of asymmetric cryptosystem technologies in the context of digital signatures, and, in effect, any authentication method that did not use this technology was not recognised under the IT Act 2000.
The IT Act 2008 has attempted to make this more technology neutral. In doing so, the attempt has been to bring the law in line with the United Nations Commission on International Trade Law Model Law on Electronic Signatures (“Model Law”).
Replacement of Digital Signatures
The first significant change in the IT Act 2008 is the replacement of the term “digital signatures” with “electronic signatures” in almost all the provisions in the IT Act 2000. In some provisions, reference continues to be made to digital signatures, but the net effect of the amendments is to treat digital signatures as a subset (or an example of one type) of electronic signatures.
Electronic signatures have been defined as the authentication of an electronic record using the authentication techniques specified in the 2nd Schedule to the Act, provided they are reliable.
The reliability criterion has been introduced, very much along the lines of the Model Law. However, the contents of the 2nd Schedule are yet to be stipulated, which means that despite the existence of a reliability standard, the only authentication method available at this point in time is the digital signature regime.
Dual Requirement
One significant implication of this amendment is the introduction of a dual requirement – to meet the reliability standard as well as to be included in the 2nd Schedule. However, structuring the authentication procedures in this manner offsets the objective tests of neutrality borrowed from the Model Law, since an authentication method may meet the reliability test but will not be deemed to be legally enforceable unless it is notified in the 2nd Schedule.
Additionally, there will be grounds for challenging electronic signatures that are notified to the 2nd Schedule, if it can be shown that the signature so notified is not reliable under the terms of the reliability criteria. This can act as an impediment to the recognition of electronic signatures by notification.
Emphasis on Digital Signatures
Another concern is the treatment of digital signatures in the post amendment statute. The IT Act 2008 continues to retain all the provisions relating to digital signatures within the main body of the statute. The term “digital signature” has not been uniformly substituted with “electronic signature” throughout the statute. In certain provisions this leads to a certain amount of absurdity, such as in those relating to representations made as to the issuance, suspension or revocation of digital signature certificates; due to the lack of uniformity, these principles now apply only to digital signatures and not to all types of electronic signatures.
It would have been preferable if the provisions relating to digital signatures had been moved in their entirety to the 2nd Schedule. Then, digital signatures would have become just another class of electronic signatures listed in the Schedule. By omitting to do this, the authors ensure that digital signature-specific provisions remaining in the main body of the statute challenge the technology neutrality of the statute.
Certifying Authorities
The IT Act 2008 has made the certifying authority the repository of all electronic signatures issued under the statute. Given that there are, at present, multiple certifying authorities, this provision is impractical. Instead, the statute should have either referred to the Controller of Certifying Authorities or should have been worded to state that each certifying authority would be the repository for all electronic signature certificates issued by it.
Impact on Other Statutes
Since the enactment of the IT Act 2000, amendments have been carried out in other statutes, relying on the concept of digital signatures. For instance, the Negotiable Instruments Act, 1881, makes the use of a digital signature essential for an electronic cheque.1 While the IT Act 2008 has expanded the scope of the available authentication measures, by introducing the technologically neutral concept of electronic signatures, corresponding amendments in other statutes like the Negotiable Instruments Act, 1881, will need to be carried out, so that they are not limited in their application to digital signatures.
Data Protection
Prior to the passing of the IT Act 2008, the concept of 'data protection' was not recognised in India. The amendments have now introduced some amount of legal protection for data stored in the electronic medium. This chapter analyses the changes sought to be introduced and their impact on data protection law in India.
Data under the IT Act 2000
The only provision under the IT Act 2000, which dealt with unauthorised access and damage to data, was Section 43. Under that section, penalties were prescribed in respect of any person who downloads copies or extracts data from a computer system, introduces computer contaminants or computer viruses into a computer system or damages any data residing in a computer system.
Data under the IT Act 2008
Under the IT Act 2008, far-reaching changes have been made in relation to data. Two sections have been inserted specifically for that purpose – Sections 43-A and 72-A, one dealing with the civil and the other with the criminal remedies in relation to the breach of data related obligations.
The Civil Remedies for Data Protection
The newly introduced Section 43-A reads as follows:
Compensation for failure to protect data - Where a body corporate, possessing, dealing or handling any sensitive personal data or information in a computer resource which it owns, controls or operates, is negligent in implementing and maintaining reasonable security practices and procedures and thereby causes wrongful loss or wrongful gain to any person, such body corporate shall be liable to pay damages by way of compensation, to the person so affected.
Explanation - For the purposes of this section:
(i) “Body Corporate” means any company and includes a firm, sole proprietorship or other association of individuals engaged in commercial or professional activities;
(ii) “Reasonable Security Practices and Procedures” means security practices and procedures designed to protect such information from unauthorised access, damage, use, modification, disclosure or impairment, as may be specified in an agreement between the parties or as may be specified in any law for the time being in force and in the absence of such agreement or any law, such reasonable security practices and procedures, as may be prescribed by the Central Government in consultation with such professional bodies or associations as it may deem fit; and
(iii) “Sensitive Personal Data or Information” means such personal information as may be prescribed by the Central Government in consultation with such professional bodies or associations as it may deem fit.
While at first this provision appears to address several long standing concerns relating to data protection in India, there are several insidious flaws that could affect the development of a data protection jurisprudence in the country.
Non-Electronic Data
In the first instance, there is no mention, under this provision, of non-electronic data. Most international data protection statutes recognise and protect data stored in any electronic medium or a relevant filing system (including, for instance, a salesperson's diary). The newly introduced provisions of the IT Act 2008 do not provide any protection for data stored in a non-electronic medium.
It could be argued that given the legislative focus of this statute (it has been called the Information Technology Act with a reason), it would be inappropriate to include within this statute protection for forms of data that do not relate to the digital or electronic medium. While that argument is valid to many who look to the new provisions introduced in the IT Act 2008 as the answer to the data protection concerns that the country has been facing all these years, their enthusiasm must be tempered as these new provisions merely provide solutions for electronic data.
Classification of Data
Most international data protection statutes distinguish between different levels of personal data – specifying difference levels of protection for personal information and sensitive personal information. Depending on whether the data can be classified as one or the other, they have different levels of protection, as loss, unauthorised access or disclosure of sensitive personal information is considered to have a deeper impact on the data subject.
The new provisions of the IT Act 2008 make no such distinction. Section 43-A applies to all “sensitive personal data or information” but does not specify how personal data not deemed to be sensitive is to be treated. In essence, personal information and sensitive personal information do not appear to be differentially treated in the context of data protection.
Consequences
Under most international data protection statutes, the person in “control” of the data is liable for the consequences of disclosure, loss or unauthorised access to such information. This ensures that liability is restricted to those who actually have the ability to control the manner in which the data is treated.
However, under the new provisions of the IT Act 2008, the mere possession of information and its subsequent misuse would render any person who possesses this data liable to damages. While there is likely to be a debate on what constitutes possession and how this differs from control, there can be little doubt that by referring to “possession” in addition to “operation” and “control”, the IT Act 2008 appears to have widened the net considerably.
Negligence in Implementing Security Practices
Section 43-A specifically places liability on a body corporate only if such body corporate has been negligent in implementing its security practices and procedures in relation to the data possessed, controlled or handled by it. The choice of language here is significant. The statute specifically refers to the term “negligence” in relation to the security practices and procedures as opposed to stipulating a clear, pass-fail type obligation to conform.
There is a significant difference between the terms “negligence to implement” and “failure to implement”. The former can only result in a breach if the body corporate that was required to follow reasonable security practices with regard to the data in its possession or control does not perform the required action and it can be proved that a reasonable man in the same circumstances would have performed the required action. If a body corporate is to be made liable under the provisions of this Section, it is not enough to demonstrate that security procedures were not followed; it has to be proved in addition that the body corporate was negligent.
Wrongful Loss and Gain
The Section appears to have been constructed on the basis that a breach has occurred in the event that any “wrongful gain” or “wrongful loss” was suffered. These terms have not been defined either under statutes or through any judicial precedents in the civil context. However, these terms do have a definition under criminal law in India. The Indian Penal Code, 1860 (“IPC”), defines “Wrongful Gain” to mean gain, by unlawful means, of property to which the person gaining is not legally entitled; and “Wrongful Loss” to mean the loss by unlawful means of property to which the person losing it is legally entitled.
There does not appear to be any greater significance in the use of these terms even though they are typically found in criminal statutes. Therefore, apart from the slight ambiguity as to purpose, their use in the IT Act does not appear to have any great significance.
Limitation on Liability
The provisions of Section 43 originally had the total liability for a breach capped at Rs. 5,00,00,000 (five crore rupees). The original text of Section 43-A had the same limitation of liability in respect of its data protection provisions. Before the bill was passed into law, this limitation was removed and now a breach of Section 43-A is not subject to any limitation of liabilities.
Reasonable Security Practices and Procedures
Section 43-A makes a reference to “reasonable security practices and procedures” and stipulates that a breach has been caused only if such practices and procedures have not been followed. There are three methods by which reasonable security practices and procedures can be established:
- By agreement;
- By law; and
- By prescription by the Central Government.
As there is no law in India which sets out an appropriate definition for the term and since it will be some time before which the Central Government comes out with necessary regulations, it would appear that the only option available is for the parties to arrive at an agreement as to how the sensitive personal data and information exchanged under their contract is to be handled.
As a corollary, till such time as the government establishes the necessary rules in relation to these security practices and procedures, if a body corporate does not enter into an agreement with the person providing the information as to the reasonable security practices and procedures that would apply, the body corporate cannot be brought within the purview of this section for any loss or damage to data.
The Criminal Remedies for Unlawful Disclosure of Information
In addition to the civil remedies spelled out in such detail in Section 43-A, the newly introduced provisions of Section 72-A of the IT Act 2008 could be used to impose criminal sanctions against any person who discloses information in breach of a contract for services. While not exactly a data protection provision in the same way that Section 43-A is, there are enough similarities in purpose to achieve the same result.
Section 72-A reads:
Punishment for Disclosure of information in breach of lawful contract - Save as otherwise provided in this Act or any other law for the time being in force, any person including an intermediary who, while providing services under the terms of lawful contract, has secured access to any material containing personal information about another person, with the intent to cause or knowing that he is likely to cause wrongful loss or wrongful gain discloses, without the consent of the person concerned, or in breach of a lawful contract, such material to any other person shall be punished with imprisonment for a term which may extend to three years, or with a fine which may extend to Rupees five lakh, or with both.
In substance, this provision appears to be focused on providing criminal remedies in the context of breach of confidentiality obligations under service contracts; given that the section specifically refers to the disclosure of personal information obtained under that service contract, it is fair to classify this as a provision that addresses data protection issues.
Personal Information
The IT Act 2008 does not define “personal information”. Equally, there are no judicial precedents that provide any clarity on the term. The Right to Information Act, 2005 does provide a definition for “personal information”, but that definition is inappropriate in the context of the IT Act 2008. In the absence of a useable definition for the term “personal information”, it becomes difficult to assess the scope and ambit of the provision and in particular to understand the extent to which it is enforceable.
"Willful"
The section would only apply to persons who willfully disclose personal information and cause wrongful loss or gain. Hence, in order to make a person liable it has to be proved that the person disclosing the personal information did so with an intention to cause wrongful loss or gain. It would be a valid defense to claim that any loss caused was unintentional.
Service Contracts
The section appears to be particular about the fact that it only applies in the context of personal information obtained under a contract for services. This appears to rule out confidential information (that is not of a personal nature) that has been received under any other form of agreement (including, for example, a technology license agreement). The section is clearly intended to protect against the misuse of personal information and cannot be adapted to provide a wider level of protection against all breaches of confidential information. That said, employers now have a much stronger weapon against employees who leave with the personal records of other fellow employees.
Consent
This section also clearly applies only to those disclosures of personal information with the intent to cause wrongful loss or gain which have taken place without the consent of the person whose personal information is being disclosed. What remains to be seen is how the law will deal with situations where a general consent for disclosures has been obtained at the time of recruitment.
Such clauses are made effective around the world by including opt in and opt out clauses, to allow the employee to either expressly agree to the disclosure of his personal information or to specifically exclude himself from the ambit of any such disclosures.
Media of Material
This section, unlike several other provisions of the IT Act 2008, deals with all manner of materials without requiring them to be digital. However, while disclosure of information stored in the non-electronic medium has been recognised, in the absence of a clear definition of personal information, it is difficult to ascertain the application and enforcement of this section.
What’s Missing
In order to be a truly effective data protection statute, the IT Act 2008 must include provisions relating to the collection, circumstances of collection, control, utilisation and proper disposal of data. At present the statute is silent about these aspects. In many ways, the statute addresses the particular concerns of companies or corporate entities looking for protection in relation to data outsourced to any other corporate entity for processing. Within these specific parameters the statute works well. However it does little to protect the average citizen of the country from the theft of personal data. Until we have statutory recognition of these issues, we will not be able to say that we have an effective data protection law in India.
Primer on the New IT Act
The latest amendments to the Information Technology Act 2000, passed in December 2008 by the Lok Sabha, and the draft rules framed under it contain several provisions that can be abused and misused to infringe seriously on citizens' fundamental rights and basic civil liberties. We have already written about some of the problems with this Act earlier. With this information bulletin, drafted by Chennai-based advocate Ananth Padmanabhan, we wish to extend that analysis into the form of a citizens' dialogue highlighting ways in which the Act and the rules under it fail. Thus, we invite your comments, suggestions, and queries, as this is very much a work in progress. We will eventually consolidate this dialogue and follow up with the government on the concerns of its citizens.
Intermediaries beware
Internet service providers, webhosting service providers, search engines, online payment sites, online auction sites, online market places, and cyber cafes are all examples of “intermediaries” under this Act. The Government can force any of these intermediaries to cooperate with any interception, monitoring or decryption of data by stating broad and ambiguous reasons such as the “interest of the sovereignty or integrity of India”, “defence of India”, “security of the State”, “friendly relations with foreign States”, “public order” or for “preventing incitement to” or “investigating” the commission of offences related to those. This power can be abused to infringe on the privacy of intermediaries as well as to hamper their constitutional right to conduct their business without interference.
If a Google search on “Osama Bin Laden” throws up an article that claims to have discovered his place of hiding, the Government of India can issue a direction authorizing the police to monitor Google’s servers to find the source of this information. While Google can, of course, establish that this information cannot be attributed directly to the organization, making the search unwarranted, that would not help it much. While section 69 grants the government these wide-ranging powers, it does not provide for adequate safeguards in the form of having to show due cause or having an in-built right of appeal against a decision by the government. If Google refused to cooperate under such circumstances, its directors would be liable to imprisonment of up to seven years.
Pre-censorship
The State has been given unbridled power to block access to websites as long as such blocking is deemed to be in the interest of sovereignty and integrity of India, defence of India, security of the State, friendly relations with foreign States, and other such matters.
Thus, if a web portal or blog carries or expresses views critical of the Indo-US nuclear deal, the government can block access to the website and thus muzzle criticism of its policies. While some may find that suggestion outlandish, it is very much possible under the Act. Since there is no right to be heard before your website is taken down nor is there an in-built mechanism for the website owner to appeal, the decisions made by the government cannot be questioned unless you are prepared to undertake a costly legal battle.
Again, if an intermediary (like Blogspot or an ISP like Airtel) refuses to cooperate, its directors may be personally liable to imprisonment for up to a period of seven years. Thus, being personally liable, the intermediaries are rid of any incentive to stand up for the freedom of speech and expression.
We need to monitor your computer: you have a virus
The government has been vested with the power to authorize the monitoring and collection of traffic data and information generated, transmitted, received or stored in any computer resource. This provision is much too widely-worded.
For instance, if the government feels that there is a virus on your computer that can spread to another computer, it can demand access to monitor your e-mails on the ground that such monitoring enhances “cyber security” and prevents “the spread of computer contaminants”.
Think before you click "Send"
If out of anger you send an e-mail for the purpose of causing “annoyance” or “inconvenience”, you may be liable for imprisonment up to three years along with a fine. While that provision (section 66A(c)) was meant to combat spam and phishing attacks, it criminalizes much more than it should.
A new brand of "cyber terrorists"
The new offence of “cyber terrorism” has been introduced, which is so badly worded that it borders on the ludicrous. If a journalist gains unauthorized access to a computer where information regarding corruption by certain members of the judiciary is stored, she becomes a “cyber terrorist” as the information may be used to cause contempt of court. There is no precedent for any such definition of cyberterrorism. It is unclear what definition of terrorism the government is going by when even unauthorized access to defamatory material is considered cyberterrorism.
Uploads
- Open letter to UN IGF — by Sanchia de Souza — last modified Nov 30, 2008 07:59 AM
The Digital is Political
The links between digital technologies and politics, especially in the light of the recent West Asian-North African uprisings, have been well-established. But there is a pervasive belief that the technologies of computing, in themselves, are apolitical. There are two warring groups when it comes to debates around political participation and social change that the digital and Internet technologies have fostered.
On the one hand are people who celebrate the negotiation- and intervention-making power of these technologies and attribute to them great power that can change the world. On the other are those who look at these developments with suspicion, trying to make a case for the power of the human will rather than the scope of technology design.
Both sides remain convinced that there is a cause-and-effect link between technology and politics, but nobody talks about the politics of technology. The functional focus on digital technologies—economic prosperity, time-space shrinkage, transparent interaction and governance—has been overwhelming. This fosters a pervasive belief that technologies of computation and communication are agnostic to politics: there is a disconnect between everyday practices of technology and spectrum of politics within which we operate.
Let me give an example to explain this. Take a blank sheet of paper. To all appearances, it is completely agnostic to the uses it can be put to. It can become a letter of love, it can become a note of dismissal, shattering the dreams of somebody who is fired, it can be a promissory note facilitating legal and economic transactions, or it can become the rag to mop a spill on your desk. It is generally presumed that the piece of paper does not have any design or agency. And yet, it is obvious from history that this sheet of paper did indeed revolutionise the world.
The advent of the printing press, the ability to mass-produce paper, the possibility of sending disembodied messages, the power of the paper to store information which can then be retrieved, has been transforming the world the last 500 years. It is a technologised platform that, by its very design possibilities and limitations, is able to shape, not only how we have communicated with each other, but also how we think. Let us remember the first proof of our identity is not in images or in sounds, but in a document, printed on a piece of paper, that declares us human and alive and legally present—the birth certificate.
We have grown so used to the world of writing and of printing that we have appropriated paper as an integral part of the human socio-cultural fabric. However, technology interfaces and products have not only a political agenda in their design, but also the power to shape the ways in which human history and memory function. The blank sheet of paper, in its inability to capture oral traditions, eradicates them. The tyranny of a piece of paper brings a fixity to articulations which are fluid. To think of the paper as bereft of political design, ambition and destiny, would be to neglect the lessons learned in history.
The digital interface needs to be understood through similar prisms. It is presumed that the digital interface in itself is not political in nature. Or politics is reduced to the level of content. In the process certain significant questions remain unanswered: who owns the digital technologies? Who supports them? Who benefits from them? Who controls them? Who remains excluded? Who is being made to bear the burdens?
Questions about exclusion and discrimination, built into the very structure of technology, are often overlooked. How do technologies determine who gets a voice? How do the digital webs exclude those who shall always remain outcasts? What happens to our understanding of the relationship between the state and the citizen? What are our digital rights? How does the technology design mitigate social evils? How does technology emerge as the de-facto arbitrator of law?
Politics plays a part in the very presence and design of these technologies. It is perhaps time to proclaim that like the personal, the “The Technological is the Political.”
Privacy
- When Data Means Privacy, What Traces Are You Leaving Behind? — by Noopur Raval — last modified Nov 24, 2011 09:24 AM
- How do you know yourself to be different from others? What defines the daily life that you live and the knowledge you produce in the span of this life? Is all that information yours or are you a mere stakeholder on behalf of the State whose subject you are? What does privacy really mean? In a society that is increasingly relying on information to identify people, collecting and archiving ‘personal’ details of your lives, your name, age, passport details, ration card number, call records etc, how private is your tweet, status update, text message or simply, your restaurant bill?
- Privacy & Media Law — by Sonal Makhija — last modified Dec 14, 2012 10:26 AM
- In her research, Sonal Makhija, a Bangalore-based lawyer, tries to delineate the emerging privacy concerns in India and the existing media norms and guidelines on the right to privacy. The research examines the existing media norms (governed by Press Council of India, the Cable Television Networks (Regulation) Act, 1995 and the Code of Ethics drafted by the News Broadcasting Standard Authority), the constitutional protection guaranteed to an individual’s right to privacy upheld by the courts, and the reasons the State employs to justify the invasion of privacy. The paper further records, both domestic and international, inclusions and exceptions with respect to the infringement of privacy.
- Right to Privacy Bill 2010 — A Few Comments — by Elonnai Hickok — last modified Mar 22, 2012 06:26 AM
- Earlier this year, in February 2011, Rajeev Chandrasekhar introduced the Right to Privacy Bill, 2010 in the Rajya Sabha. The Bill is meant to “provide protection to the privacy of persons including those who are in public life”. Though the Bill states that its objective is to protect individuals’ fundamental right to privacy, the focus of the Bill is on the protection against the use of electronic/digital recording devices in public spaces without consent and for the purpose of blackmail or commercial use.
- Conference Report: 'Privacy Matters' Bangalore — by Prasad Krishna — last modified Feb 08, 2011 05:13 AM
- On February 5th the 'Privacy Matters" conference was held at the TERI Regional Center in Bangalore. The event was a full day and centered around issues of privacy including: privacy rights of minorities, privacy and open government data, and privacy and identity.
- Open Letter to the Finance Committee: Operational Design — by Prasad Krishna — last modified Feb 17, 2011 10:02 AM
- The objective of the UID project is to provide identity infrastructure that is not susceptible to fraud or error. This note highlights parts of the operational design of the project, which are flawed. We plead that each point be taken into consideration and that the design be suitably revised.
- Open Letter to the Finance Committee: UID Budget — by Prasad Krishna — last modified Feb 17, 2011 11:18 AM
- This note presents the aspects of the UID project, which have not been considered or incorporated into the UID’s budget. The costs include re-enrollment, loss in human time, and the cost of the audit function.
- Open Letter to the Finance Committe: Biometrics — by Prasad Krishna — last modified Feb 17, 2011 01:12 PM
- This note points out the weaknesses inherent in biometrics and the pitfalls in using them. It recommends procedural safeguards that should be adopted by the UID in order to make the use of biometrics more secure and inclusive.
- Open Letter to the Finance Committee: Finance and Security — by Prasad Krishna — last modified Feb 17, 2011 11:57 AM
- This note explores the three connections between finance and security and demonstrates the cost implications of operating a centrally designed identity management system as proposed by the UID. In doing so, it shows how the monitoring, storing, and securing of transactional data in a centralized database fall short of meeting the project's objectives of authentication, and thus is an additional cost. Further, it is argued that the blanket monitoring of the transaction database is not an effective method of detecting fraud, and is an expensive component of the project.
- Open Letter to the Finance Committee: UID and Transactions — by Prasad Krishna — last modified Feb 24, 2011 01:35 PM
- Since official documentation from the UIDAI is very limited, we assume that data pertaining to transactions would comprise of the Aadhaar number, identifier of the authenticating device, date-time stamp, and approval/rejection/error code. Recording and maintaining of data pertaining to transactions is very important because it increases transparency and accountability through an audit trail. However, storage of such sensitive data creates many privacy risks, because more often than not metadata gives you as much intelligence as raw data.
- Privacy and Governmental Databases — by Elonnai Hickok — last modified Mar 22, 2012 05:41 AM
- In our research we have found that most government databases are incrementally designed in response to developments and improvements that need to be incorporated from time to time. This method of architecting a system leads to a poorly designed database with many privacy risks such as: inaccurate data, incomplete data, inappropriate disclosure of data, inappropriate access to data, and inappropriate security over data. To address these privacy concerns it is important to analyze the problem that is being addressed from the perspective of potential and planned interoperability with other government databases. Below is a list of problems and recommendations concerning privacy, concerning government databases.
- A Stolen Perspective — by Elonnai Hickok — last modified Mar 21, 2012 09:43 AM
- The note below is a perspective piece on biometrics. On March 11th I traveled down to the Philippines, and had a chance to experience the possible convenience of biometric based identification.
- News Broadcasting Standards Authority censures TV9 over privacy violations! — by Prashant Iyengar — last modified Mar 22, 2012 05:14 AM
- We at PrivacyIndia/CIS are delighted by the recent order issued by the News Broadcasting Standards Authority(NBSA) which slapped a 1 lakh rupee fine on the news channel TV9 for airing an extremely incendiary and invasive programme titled "Gay Culture rampant in Hyderabad".
- 'Privacy Matters', Ahmedabad: Conference Report — by Prasad Krishna — last modified Apr 04, 2011 04:45 AM
- On 26 March 2011, civil society, lawyers, judges, students and NGO’s, gathered together at the Ahmedabad Management Association to take part in 'Privacy Matters' – a public conference organised by Privacy India in partnership with IDRC and Research Foundation for Governance in India (RFGI) — to discuss the challenges of privacy in India, with an emphasis on national security and privacy. The conference was opened by Prashant Iyengar, head researcher at Privacy India and Kanan Drhu, director of RFGI. Mr. Iyengar explained Privacy India’s mandate to raise awareness of privacy, spark civil action, and promote democratic dialogue around privacy challenges and violations in India. RFGI is a think tank established in 2009 which aims to research, promote, and implement various reforms to improve the legal and political process in Gujarat and across India. ‘Privacy Matters – Ahmedabad’ is the third conference out of the eight that Privacy India will be hosting across India. The next conference will take place in Hyderabad on 9 April 2011. It will focus on human rights and privacy.
- Encryption Standards and Practices — by Elonnai Hickok — last modified Mar 22, 2012 05:39 AM
- The below note looks at different types of encryption, varying practices of encryption in India, and the relationship between encryption, data security, and national security.
- Surveillance Technologies — by Elonnai Hickok — last modified Mar 22, 2012 05:40 AM
- The following post briefly looks at different surveillance technologies, and the growing use of the them in India.
- Is Data Protection Enough? — by Elonnai Hickok — last modified Mar 22, 2012 05:28 AM
- The following note looks briefly at different sides of the privacy debate, and asks the question whether a Data Protection law is enough privacy protection for India.
- Privacy and the Information Technology Act — Do we have the Safeguards for Electronic Privacy? — by Prashant Iyengar — last modified Dec 14, 2012 10:29 AM
- How do the provisions of the Information Technology Act measure up to the challenges of privacy infringement? Does it provide an adequate and useful safeguard for our electronic privacy? Prashant Iyengar gives a comprehensive analysis on whether and how the Act fulfils the challenges and needs through a series of FAQs while drawing upon real life examples.
- Consumer Privacy in e-Commerce — by Sahana Sarkar — last modified Mar 28, 2012 04:53 AM
- Looking at the larger picture of national security versus consumer privacy, Sahana Sarkar says that though consumer privacy is important in the world of digital technology, individuals must put aside some of their civil liberties when it comes to the question of national security, as it is necessary to prevent societal damage.
- Copyright Enforcement and Privacy in India — by Prashant Iyengar — last modified Dec 14, 2012 10:27 AM
- Copyright can function contradictorily, as both the vehicle for the preservation of privacy as well as its abuse, writes Prashant Iyengar. The research examines the various ways in which privacy has been implicated in the shifting terrain of copyright enforcement in India and concludes by examining the notion of the private that emerges from a tapestry view of the relevant sections of Copyright Act.
- Privacy Blog — by kaeru — last modified Aug 08, 2011 07:41 AM
- An analysis of privacy in the context of India
- Re-thinking Key Escrow — by Natasha Vaz — last modified Aug 22, 2011 11:44 AM
- Would you make duplicates of your house keys and hand them over to the local police authority? And if so, would you feel safe? Naturally, one would protest this invasion of privacy. Similarly, would it be justified for the government to have a copy of the private key to intercept and decrypt communications? This is the idea behind key escrow; it enables government ‘wiretapping’.
- CCTV in Universities — by Merlin Oommen — last modified Sep 01, 2011 09:50 AM
- Basic Closed Circuit Television (CCTV) Infrastructure is used to observe movements from a central room, and consists of one or more video cameras that transmit video and audio images to a set of monitors or video recorders.
Whole Body Imaging and Privacy Concerns that Follow
Introduction
Whole Body Imaging has been introduced in many countries in light of growing security concerns, two examples in particular being the attack on the twin towers in USA, and what is commonly known as the Christmas Bomb (A man by the name of Umar Farouk Abdulmutallab tried to detonate a bomb on a flight from Amsterdam as it was about to land in Detroit.) Despite the security concerns that have motivated the implementation of Whole Body Imaging, there are also many concerns that have prevented the full fledged application of this technology. Opponents to the technology have stated that the full body scanner would expose travelers to harmful radiation and is thus a health hazard. Others have stated that these digital strip searches (as they are popularly known) will violate child pornography laws. Some, who are trying to encourage the use of full body scanners, are of the opinion that it is better to opt for a whole body scan as the “pat down” searches are more invasive in nature. There are also the concerns that persons may be singled out on the basis of their color and ethnicity. The scope of research for this particular paper is limited to the extent of the privacy concerns that have arisen in light of the use of the technology in order to achieve better security. The question that forms the crux of the debate is: should ones personal privacy be compromised in order to ensure security for one and all? The primary reason why whole body scanners are said to breach privacy is because of the invasive nature of the images produced, which can be detailed enough to show genitalia of the person being scanned.
Learning from the experience of other nations that have already implemented the use of Whole Body Imaging” we can decide what policies India should have in place and most importantly whether or not India realistically has a use for this technology.
Adequate privacy, it is said, is obtained when the restriction on access to persons and personal information allows a person not to be subjected to intrusion and public exposure [1]. Full body scanners can be called intrusive because in effect they allow the government to carry out strip searches by using technology to remove clothes instead of physically doing the same. Apart from this there are other concerns. For instance there have been instances when these images have been saved and have been uploaded on the internet [2]. In Lagos these images have been used as pornographic material. There is also a cause of concern amongst transgender who do not feel comfortable in revealing their gender which is different from the gender that they portray[3] and they are of the opinion that this information could lead to harassment. Since the scanners can detect medical equipment people who use colostomy bags and catheters which are otherwise hidden may find these scans embarrassing [4].
USA
In the U.S, Whole Body Imaging was introduced in light of the growing concerns with regard to security at airports and terrorist attacks. The Transportation Security Administration is responsible for monitoring security at the airport. The TSA has thus introduced Full Body Scanners at airports. In order to address the privacy concerns that have been raised the TSA has taken the following steps:
- Ensuring that the Security officer who is privy to the scan is not the same as the officer interacting with the person who is being scanned.
- The TSA has also stated that personally identifiable information will not be stored and distributed.[5]
- Another step towards safeguarding the privacy of the passengers has been to blur the faces of the person being scanned.[6]
Though the TSA has taken various steps to ensure the privacy of individuals, one can argue that these measures are not without loopholes. The fact that the Security Officer looking at the scan and the Security officer handling the passenger are different does not do away with this invasion of privacy. There is also the added concern that these images may be uploaded on the internet, which in fact has already been done. The release and collection of these images is in contravention of the Privacy Act of 1974 that governs the collection, maintenance, use and dissemination of personal identifiable information about individuals which in the possession of the federal agencies. The TSA assures that the images will not be retained, but the fact is that the machines have been programmed such as to enable retention of images, if the same has been disable, it can be tampered with. Lastly, on the point of blurring of faces, it is a software fix and can be undone as easily as the application of the software. The TSA in its Privacy impact Assessment report had listed down that full body scanning would initially be a secondary screening measure. What this means is that everyone goes through one level of security screening and if one is randomly selected or the security has reason to suspect a passenger, the passenger can be called for a second level of screening. At which point the passengers will undergo full body scanning.
A federal judge in California, in 1976 said that the laws of privacy “encompass the individual's regard for his own dignity; his resistance to humiliation and embarrassment; his privilege against unwanted exposure of his nude body and bodily functions." As already stated, these body scanners lead to situations that can be embarrassing, do lead to unwanted exposure of body, and can lead to situation where the person scanned could be humiliated (as in the case of transgender and other persons with catheters and colostomy bags). The Electronic Privacy Information Center is a non-profit group that was established to focus attention on civil liberties issue. EPIC challenged the constitutional validity of full body scanning, claiming that the same violated the fourth amendment [9]. The amendment guards against unlawful searches and seizures. In the case of whole body imaging, travelers are subjected to “invasive searches” without any suspicion that they did anything wrong, and without being informed of the reason he/she is being subjected to a search of such a nature. [10] The latest is the use of this technology in courthouses in Florida and at train stations.
UK
In the UK if a passenger is selected for full body scanning, the passenger must comply [11]. The passenger is forbidden from flying if he or she refuses to the scanning process and cannot ask for an alternate screening process [12] Unlike the US in the UK the option of a pat-down search is not available. The steps taken to protect the privacy of the passengers are the same as practiced in the US.
- The images of the passengers are not retained
- The images are produce in such a manner that the Security officer cannot recognize the person.
A major concern in UK is the violation of child pornography laws that do not allow the creation of indecent images of a child. However, a rule that would have exempted persons under the age of 18 from full body scans was overturned by the government in the UK [13]. Gordon Brown the Prime Minister of UK in 2010 gave permission for the use of full body scanners at the airports. BAA Ltd, which operates six airports in UK (including the Heathrow Airport) has undertaken the installation of these scanners at its airports. In general, the security at the airports comes under the ambit of the Homeland Security and the department will be supervising the installation of the machines. Lord Adonis, the Transport Secretary, confirmed the new policy in a written parliamentary statement, saying that the scanners would help security staff to detect explosives or other dangerous items [14].
One of the major opponents of Whole Body Imaging has been the Equality and Human Right Commission (EHRC), which is of the opinion that the use of this technology would breach the privacy rules under the Human Rights Act [15]. The move to use this technology has raised concerns about the excessive collection of personal data. Big Brother Watch, a campaign that fights intrusion on privacy and protects liberties of people, started an online movement that opposes and raises concerns with full body scanning. It has also listed down all the airports around the world that are using (or are going to be using) this technology [16]. The only group that has openly welcomed this move of the government has been the Liberal Democrats [17]. The British Department of Transport has published an Interim Code of Practice covering the privacy, health and safety, data protection and equality issues associated with the use of body scanners. The Code calls for the implementation of detailed security standards and for an effective privacy policy to be put in place by airport operators.
The privacy policy should include as a minimum:
- rules regarding the location of the equipment;
- A process for identifying who will read the screen (i.e., a person of the same sex as the person selected for scanning);
- A process for selecting passengers (passengers must not be selected on the basis of personal characteristics such as, gender, age, race or ethnic origin);
- Prohibition on copying or transferring the images in any way;
- Instructions for the images of the passenger to be destroyed and rendered irretrievable once the image has been analyzed; and
- A process to call on an appropriate Security Officer if an image suggests there is a viable threat to passenger or staff security.
The BodyScanner Task Force was established by the European Commission to publish an impact assessment report and to advise the commission, but the task force has yet to publish its report with specific legislative proposals [18].
Concerns in the UK also arose in light of a response of a judge to a complaint by the Electronic Privacy Information Centre (based in Washington). The judge stated that the Department of Homeland Security (USA) would be allowed to keep images of individuals screened at the airport [19]. This raises concerns amongst activists as to which images can and which images cannot be saved by the airport authorities.
Australia
Post the attempted attack on Christmas Day, pressure on countries such as Australia increased to make use of whole body imaging technology. However, the Association of Asia Pacific Airliners, an association of the international carriers servicing in Australia, criticised the use of full body scanners [20]. Apart from the privacy concerns, that people all over the world share, another aspect that is cause for concern in Australia is the increase in traveling cost. The machines used for whole body imaging is extremely expensive, and thus the question posed time and again in Australia is if it will be economically viable to make use of this technology?[21] The Queensland Council for civil liberties has opposed the use of this Advance Imaging Technology (AIT) and has stated that passengers should be allowed to refuse being scanned and should be allowed to opt for a pat down. Kevin Rudd (the Prime Minister of Australia at the time of implementation of this technology) had taken note of the privacy concerns and assured that such measure would be undertaken that would mitigate these concerns. Currently, Body scanners are installed at the international airports in Australia. The transport minister has said that the images produced would be stick figures and not naked images [22]. This move has been taken in light of the back clash that body scanners faced in the USA. Changes regarding whole body imaging have been referred to the Privacy Commissioner in order to ensure that privacy is not intruded. Namely, Full Body screening will not be applied to all the passengers - instead passengers will either be randomly selected or will be selected on the basis of their profiles [23].
India
Currently in India whole body scanners can be found at the Delhi International Airport [24]. Thus, debate and discussion about the use of these scanners has not gained much momentum in India. It would be advisable that when framing legislation or guidelines to govern full body scanners, India incorporates the experiences of other nations who have already started the use of this technology.
Generally speaking it seems as though the use of a full body scanner would not be recommendable for the Indian scenario. It has already been seen that these scans are not very effective in detecting plastic and fluids [25]. Additionally the scanner only shows objects that are on the body and not in the body. Thus, the effectiveness of these scanners is questionable (especially considering it cannot detect plastics and light fluids) [26]. Additionally, in India the demographic using these scanners would be very different from the people using these scanners in other countries. For instance, it has been pointed out that the interest of Muslim women has not been taken into account when introducing this method of screening. Apart from personal privacy issues there are religious issues that arise, and though the instances of the same maybe far apart in other nations, in India the same will act as a hindrance on a daily basis. If not dealt with delicately this can be a major cause of concern that will have far reaching ramifications. Furthermore, one cannot stress enough the cost that will be involved with the implementation of these scanners. These scanners are extremely expensive and require trained Security Officers to operate them. Additionally, what the scanners seek to accomplish can be achieved by insuring that the pat-downs are carried out properly. But there is a caveat that must be mentioned here. In US, one is allowed to choose between a pat-down and a body scanner. There have been instances when these pat-downs have been more intrusive than the body scanners. Thus, there should be guidelines in place as to how these pat-downs should be carried out. The guidelines should specify actions that the Security Officials would not be allowed to carry out.
Lastly, even if India decided to adopt the full body scanners, considering it helps save time and takes only 15 seconds to complete, it should not be used as a primary screening method. Hypothetically, if body scanners are used as a secondary screening process, alternate screening processes should be available if the passenger does not wish to subject himself/ herself to the scan. But then the question is why should the government invest so much in an expensive technology which the passengers can easily avoid?
Bibliography:
[2].http://gizmodo.com/5690749/these-are-the-first-100-leaked-body-scans.
[3]. Available at http://www.airlinereporter.com/2010/08/we-do-not-have-all-the-same-body-parts-and-body-scanners-violates-your-privacy/.
[4].http://www.aclu.org/technology-and-liberty/aclu-backgrounder-body-scanners-and-virtual-strip-searchers.
[5].Privacy impact assessment report. Available at - http://www.dhs.gov/xlibrary/assets/privacy/privacy_pia_tsa_wbi.pdf.
[6].http://www.aclu.org/technology-and-liberty/aclu-backgrounder-body-scanners-and-virtual-strip-searches.
[7].http://travel.usatoday.com/flights/2010-07-13-1Abodyscans13_ST_N.htm .
[8].http://www.stopdigitalstripsearches.org/.
[9]. http://epic.org/privac/airtravel/backscatter/.
[10].http://www.dailymail.co.uk/news/article-2012249/TSA-scanners-catch-implant-bomber-admit-officials.html?ito=feeds-newsxml.
[11].http://news.bbc.co.uk/2/hi/uk_news/8490860.stm.
[12].http://www.bigbrotherwatch.org.uk/home/2010/03/body-scanner-refuseniks.html.
[13].http://news.bbc.co.uk/2/hi/uk_news/8490860.stm.
[14].http://www.timesonline.co.uk/tol/news/uk/article7011224.ece.
[15].http://www.timesonline.co.uk/tol/news/politics/article6990990.ece.
[16].http://www.bigbrotherwatch.org.uk/home/2010/06/airports-with-body-scanners.html.
[17].http://news.bbc.co.uk/2/hi/8438355.stm.
[18].http://www.huntonprivacyblog.com/2010/02/articles/european-union-1/uk-airports-implement-compulsory-use-of-full-body-scanners/.
[19].http://www.bigbrotherwatch.org.uk/home/2011/01/judge-blocks-investigations-into-body-scanners.html.
[20].http://www.theaustralian.com.au/travel/backlash-to-airport-body-scans/story-e6frg8rf-1225817485755.
[21].http://www.sbs.com.au/news/article/1190826/full-body-scanners-to-be-introduced-at-airports.
[22].http://www.theage.com.au/travel/travel-news/fullbody-airport-scans-part-of-security-revamp-20100209-npqo.html.
[23].http://www.theage.com.au/travel/travel-news/fullbody-airport-scans-part-of-security-revamp-20100209-npqo.html.
[24].List of Airports with full body scanners. Available at http://www.bigbrotherwatch.org.uk/home/2010/06/airports-with-body-scanners.html.
[25].http://www.independent.co.uk/news/uk/home-news/are-planned-airport-scanners-just-a-scam-1856175.html.
[26].http://www.bigbrotherwatch.org.uk/home/2010/01/invasion-of-the-body-scanners.html.
UID: Questions without Answers – A Talk by Usha Ramanathan
Ms. Ramanathan began her presentation by describing the progress and evolution of the UID project. She stated three adjectives that reflect the target goal of the Unique Identification Authority of India (UIDAI): unique, ubiquitous and universal. She demonstrated how their initial objectives and claims have been drastically altered in three major ways.
First and foremost, the UIDAI claimed that enrolment is voluntary, not mandatory, and hence, inclusive. Yet, Nandan Nilekani has consistently maintained that other agencies may make it compulsory. UID is becoming ubiquitous and is a prerequisite for access to a wide variety of welfare schemes and services such as PDS, MGNREGS, banks, public health, etc. It is thus clear that this could actually exclude those who do not have a number or whose biometrics doesn't work. Therefore, this undermines the inclusive nature of the project.
Second, the UIDAI claimed that the UID would enable inclusive growth. Ms. Ramanathan expressed a serious concern surrounding the risk of exclusion. Instead of facilitating inclusion, around two to five per cent of the Indian population would be excluded from the current process of authentication and potentially from having a UID number, as they do not have viable biometric data.[1] Physical or visual impairments such as corneal blindness, corneal scars, and malnourishment induced cataracts or ‘low-quality’ fingerprints from a lifetime of hard labour inhibit those from providing valid fingerprints or iris scans.[2]
Third, Ms. Ramanathan reiterated that the National Identification Authority India Bill prohibited sharing data, except by the consent of the resident, by a court order or for national security. However, UID information is being directly fed into the National Intelligence Grid (NATGRID) who will then provide information about people that is in 21 databases, to eleven security agencies, including the RAW and IB over which there is no superintendence or oversight.[3] She discussed the high likelihood of a breach of privacy as there are insufficient standards protecting an individual from unlawful invasion. Additionally, the UIDAI does not have mechanisms in place for an individual to be notified if there is a data breach.
Who owns this project?
A very important question asked is, “Who owns this project?” Ms. Ramanathan stated that the convergence of information especially during the ‘de-duplication process clearly reflects the corporatization of the project. She also questioned the background of some of the technological companies involved. For instance, L-1 Identity Solutions is well known for its links with the CIA. Additionally, Accenture is on a Smart Borders project with US Homeland Security. She explained that ownership also plays into the feasibility and financial cost of the project. Furthermore, the UIDAI has not conducted a feasibility study on the technology or the financial cost of the project.
International Experience
Lastly, Ms. Ramanathan discussed the international experience of a universal identity system. In the United Kingdom, their universal system of identification was labelled as ‘intrusive bullying’ as well as ‘an assault on personal liberties’. The United States and the United Kingdom both abandoned a universal identity system, as it was impractical, unjustified and dangerous.
Ms. Ramanathan raised many questions that evoked thought and discussion from the audience. She provided numerous examples of ambiguity, misconceptions and confusion surrounding the UID project. She urged the audience to exercise their civil liberties or risk losing them. Lastly, she believed that an informed debate involving the UIDAI and the public is long overdue.
“The UIDAI must clarify misconception and provide detailed answers to crucial questions, as there is a lack of understanding within the general population about the UID. Therefore, the UIDAI and the Government of India must increase and ensure transparency of the UID project”, she added.
Ms. Usha Ramanathan was speaking at an event organised by Concern, an IISc Student group. She was speaking in her personal capacity and the opinions reflected above are necessarily not those of CIS.
Design!Public II in Bangalore ― Event Report
The day consisted of discussions on several related topics, as well as engaging the participants in interactive challenge sessions.
Aditya Dev Sood, from the Centre for Knowledge Societies, kick-started the event with some words about the value of innovative thinking. Reflecting upon lessons learned from the previous Design Public conclave, Dr. Sood explained that while the previous event focused on governance innovation, the second Design Public conclave will reflect on the importance of citizen participation in innovation. After brief introductions of the conclave participants and speakers, the first session on Innovation and the Indian Corporation began.
Mr. Krishnan demonstrated the ingenuity of innovation through the history of the Indian mousetrap, in which he described three generations of mousetraps, which increase in the scale of functionality and effectiveness with each new proceeding product. One of the recurring views that emerged during the conversation was that while the Indian society is highly innovative, large Indian corporations do not generally take part in innovation. Harish Bijoor explained why there is a lack of motivation on the part of Indian corporations to innovate by stating, "what happens to large companies is that they get too preoccupied with success." The comfort that comes with the achievement of success makes Indian corporations unmotivated to pursue innovative ideas. Mr. Krishnan also added that "the Indian corporate is too regimented, which kills innovation. Most innovators are outside of corporations."
A distinction between innovation in India and the West was made, stating that in most Western societies, innovation occurs at the top most resource-rich layer of society. In India it is the opposite. Entrepreneurship happens on a grassroots local level. Arun Pande offered a thought on improving the current trends, stating that large companies can play a role in innovation by collaborating with small entrepreneurs working on social issues. It was agreed among the speakers that Indian corporations need to focus on innovative ideas to tackling some of India’s grand challenges and improving the quality of life for the citizens.
On that thought, the second panel began on the question: Is Innovation in the Public and Social Sectors Possible? Sunil Abraham, the panel moderator, introduced the session by giving an example of modern innovation, speaking about Spice M9000 and the extremely efficient and economic way in which it is manufactured. The device comes with features such as a dual SIM card, radio receiver, a receiver for terrestrial television, two large boom-box speakers, and a projector. Five thousand of these devices can be manufactured in Shenzen, China for Rs 2 crores within approximately 45 days.
The panel was asked whether academic knowledge and innovation can be incorporated into practical government policies. Ashwin Mahesh answered this question by stating, "the structure of absorbing information from academia is not present in the public sector." The speakers agreed that the government needs to encourage innovation and support its citizens to pursue innovative solution-based initiatives. Rohini Nilekani was of the opinion that "you need solution-based thinking on two levels, the state and local." Mr. Mahesh added that "the government needs to empower small communities to solve their problems and drive things locally, from the bottom-up." The necessity for private-public partnerships was a clear theme throughout the conversation, Pratham Books being given as a successful example of such endeavour. Mrs. Nilekani explained that "we need to break down the distinction between what is public and what is private. We need to work towards a common goal. We need to innovate and design checks and balances to wheel public interest."
The third panel was on The Challenge of Start Up innovation. Aditya Mishra from the Headstart Foundation defined a startup as something that makes a meaningful impact on society. According to Mr. Mishra, the startup ecosystem is problematic in India because large corporations generally do not engage in partnerships with startups. Naresh Narasimhan pointed out that "there is a notion that startup entrepreneurs do not have enough knowledge, so they get dismissed." It was further explained that aspiring entrepreneurs in India do not have enough spaces where networking and business negotiations could take place. Zackery Denfeld was of the opinion that there is a lot of innovation happening in the middle level, but more innovation needs to be done at the lower level. There is a need to focus on smaller start-ups. Design should be done at a higher paste. People should be able to fail fast, learn from mistakes, and start-up again.
The Theory and Practice of Innovation was the next panel. Upon being asked to give a single sentence definition of design, the speakers provided several enlightening answers. M. P. Ranjan stated that it is human intentions and actions that generate value. Reto Wettach added that design encompasses "methods which help define solutions, and goals which help solve these problems." One of the emerging thoughts from the discussion was that design has a value that is measurable beyond monetary gain. Furthermore, when you take public issues into consideration, the non-designers are just as important as designers. "Everybody has privileged information which they can bring into the synthesis of a solution," stated Eswaran Subrahmanian.
Having learned from each other and the inspiring ideas that were circulating the panel discussions, the participants were given three scenarios for which they were asked to brainstorm innovative approaches and solutions. The scenarios were Online Higher Education, Quality Maternal and Child Healthcare, and Toilet-training for All. During these sessions, the participants were confronted with problems faced by communities in India, which included the lack of higher education opportunities in rural areas, the need for proper and timely administered antenatal care, as well as the need to ensure village sanitation infrastructure. The solutions given to these problems highlighted the importance of a participatory approach to problem solving. Empowering community members and encouraging local leadership in innovative projects ensures their sustainability.
Concluding remarks on lessons learned and a way forward brought the afternoon to an end. Some of the final thoughts were that consensus is integral in the public space. End users and community members need to be involved in the process of design and innovation. While one must look beyond the government for instituting solutions to public problems and concerns, the role of the government, especially the local government, is also important. All sectors of society need to be engaged in design and innovation. "Persistence and methodology can make us an irresistible force," pointed out Ashwin Mahesh.
On that note, the conclave came to an end, but without a doubt, the lessons and inspiration gained by the participants will continue on.
Seventh Open Letter to the Finance Committee: A Note on the Deduplication of Unique Identifiers

With more than one signature, we have Y = 1 only when those of the applicant match the signatures in some other suite of such item by item; and Y = 0 then if at least one of his or her signatures fails to match any already recorded one.
Though the circumstance should be unlikely, a person who has already been registered may apply again to be registered: with fraudulent intent maybe: or simply because he or she has lost the document – some identity card, perhaps – which bears the identifier assigned to him or her by the UIDAI. And the possibilities here may be regarded as the values of a binary variable:
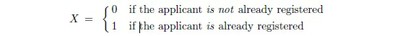
Though we are regarding X and Y as variables equally, and taking them for jointly distributed ones, there is an evident asymmetry between them. The exercise of trying to match a given suite of signatures to some set of other suites can be performed so long as the signatures remain available; but for a given applicant the values of X refer to events already past. Faced with an applicant of whom they may suppose no more than what he or she may disclose, the personnel of the UIDAI cannot directly estimate either of the two quantities:

We have p[X = 0] + p[X = 1] = 1 here, needless to say, so there is only one quantity that needs estimating. But it is worth emphasizing that even when an applicant declares himself to have been registered already— and has come, say, to have a lost card newly issued — the personnel of the UIDAI are obliged to remain agnostic about p[X = 1] : no matter how ready they are to believe him.[1]
That no individual should be assigned more than one identifier is an entirely evident desideratum: so the process of comparing the signatures of a fresh applicant to those already recorded must be a strict one. But the process of comparison should also make it very likely that, when a match of signatures does occur, the applicant is someone who has in fact been registered already. The chance that a genuinely new applicant’s signatures will match some already recorded suite should be very small: the proportion of such mistaken matches, among all matches, should be as low as possible. This proportion is usually denoted by p[X = 0 | Y = 1] : the conditional probability that X = 0 given that Y = 1 : the chance that, despite a match of signatures, the applicant has not in fact been registered already. The defining formula:
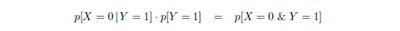
relates this conditional probability to the ‘absolute’ or ‘raw’ probabilities of the events [Y = 1] and [X = 0 and Y = 1] ; the second of which is sometimes said to be contained in the first.
Suppose that there have been N applicants thus far. It is usual to say N trials of X and Y have occurred; but only the outcomes for Y are known. Suppose that matches have been found some m times out of these N ; then N − m applicants will have been registered. With regard to these trials, set
Note that these numbers are not individually known; but as the specified events exhaust the possibilities, we have c 00 +c 01 +c 10 +c 11 = N ; and we do know that
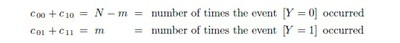
The ratio m/N would be a reasonable estimate of p[Y = 1] ; and (N − m)/N a reasonable estimate of p[Y = 0] = 1 − p[Y = 1] likewise. The quantity we are seeking is p[X = 0 | Y = 1] however: of which the ratio c 01/m would be a natural estimate. But unless we have some sense of the relative magnitudes of c 01 and c 11 the quantity
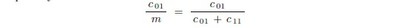
could be anything between 0 and 1 now. To estimate the relative magnitudes of c 01 and c 11 in any direct way would be difficult, because one has no purchase on how likely the events [X = 0 & Y = 1] or [X = 1 & Y = 1] are. So p[X = 0 | Y = 1] must be estimated directly, it would seem; and we shall come back to the question.
The reply we have received from the UIDAI indicates that 2.59 × 107 registrations — or successful ‘enrolments’, as they have put it — had been effected by 17.08.2011;while the ‘enrolments rejected’ came to 2.005 × 103 they say. Enrolments were rejected when ‘residents were duplicates’: if we take this to mean that an applicant was refused registry on account of his signatures matching some suite of signatures already recorded, then we may suppose that
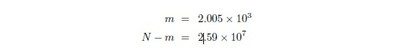
The False Positive Identification Rate, or FPIR, is defined in that reply as the ratio of the number of the number of false positive identification decisions to the total number of enrolment transactions by unenrolled individuals : if by “unenrolled individual” we understand an applicant of whom [X = 0] actually obtains, then in our notation we have
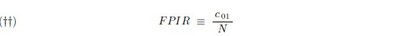
rather: which would be a natural estimate of p[X = 0 & Y = 1] now, and since
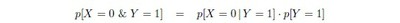
the ‘false postive identification rate’ thus construed could be bound, at least, if p[X = 0 | Y = 1] itself could be. At any rate, this latter proportion seems to be the most pertinent one here: p[X = 0 | Y = 1] is the conditional probability, of mistaken matches, that the UIDAI must strive to keep as low as possible.
The reply from the UIDAI defines a false negative identification as an incorrect decision of a biometric system that an applicant for a UID, making no attempt to avoid recognition, has not been previously enrolled in the system, when in fact they have. One is at a loss to understand how the personnel of the UIDAI are to determine when an applicant is making no attempt to avoid recognition. Putting that aside, the False Negative Identification Rate or FNIR would now appear to be p[X = 1 | Y = 0] : the probability that, despite his or her signatures not matching any already recorded suite, an applicant has in fact already been registered: and with our notation
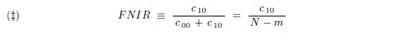
now. But c 10 cannot be reliably estimated, again, because one has no purchase on how likely [X = 1 & Y = 0] is; and the conditional probability p[X = 1 | Y = 0] will have to be estimated or bound in some direct way as well.
The preceding paragraphs have asserted that, in order to estimate or effectively bound the identification rates being sought by the UIDAI, the conditional probabilities p[X = 0 | Y = 1] and p[X = 1 | Y = 0] will have to be addressed in some direct way: without any attempt to estimate the likelihoods of [X = 0 & Y = 1] and [X = 1 & Y = 0] by themselves, that is to say. There might be ways of reliably estimating these conditional probabilities; and the manufacturers of the devices that produce the signatures may have provided tight bounds on what they would be — when the devices are working properly, at least. But let us now consider how the UIDAI has elaborated on these rates.
Their reply to our second question states that the biometric service providers have to meet the following accuracy SLA’s for FPIR and FNIR:
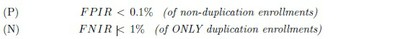
The condition of ‘non-duplication’ in the requirement (P) implies that the FPIR is being understood now as the formula in (†) above computes it: as an estimate of the conditional probability p[Y = 1 |X = 0]: since one already knows that [X = 0] for each enrolment here. Such an estimate could be made if one had obtained a sample of suites of signatures from distinct individuals — where no two suites in the sample could have come from the same individual — and compared each suite to every other: the proportion of matches found would be an estimate of p[Y = 1 |X = 0] now.[2]
The ‘biometric service providers’ the UIDAI has contracted with are presumably able to perform such experiments accurately. But an estimate of p[Y = 1 |X = 0] will not, as we shall momentarily see, by itself readily yield a usable bound on p[X = 0 | Y = 1] : on the crucial likelihood that, despite his or her suite of signatures matching a suite already recorded, an applicant has not in fact been registered.
The condition “ONLY duplicate enrolments” in the requirement (N) implies that the FNIR is being understood as an estimate of the conditional probability p[Y = 0 |X = 1] now: as one already knows that [X = 1] for each enrolment here. The biometric service providers should be able to estimate this probability as well. The FNIR as (‡) construes it is an estimate of p[X = 1 | Y = 0] rather; but a usable bound for this likelihood is readily got from p[Y = 0 |X = 1] now, for we may surely expect p[X = 1] < p[Y = 0].
Let us see if the requirement (P) will yield any usable upper bound on the crucial likelihood p[X = 0 | Y = 1]: which, to note it again, is what the UIDAI must seek to minimise. Consider the consequences when the FPIR is understood as (P) envisages. Taken together with formula (1) above we have
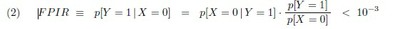
If we are not willing to wager on any upper limit appreciably less than 1 for p[X = 0] , we obtain
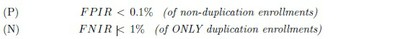
now.[3] Unless one can reasonably suppose that the event [Y = 1] never occurs, one must grant that p[Y = 1] > 0 . We have
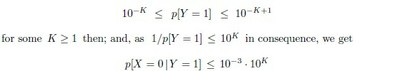
But this inequality yields a usable upper bound only when K < 3: only when K is 1 or 2 that is. In either case, only by supposing that p[Y = 1] > 10−2 will the accuracy mandated for the FPIR by the UIDAI yield a usable upper bound on p[X = 0 | Y = 1] . Since the UIDAI expects that p[Y = 1] < 10−2 surely, we must conclude now that the requirements it has imposed on its ‘biometric service providers’ will not help its personnel estimate an upper limit for the crucial likelihood that, despite his or her suite signatures matching some already recorded suite, an applicant for a UID has not in fact been registered already: which likelihood, to insist again, is what the UIDAI must seek to minimise.
The argument just made will seem perverse: but the calculation is perfectly general. Suppose an FPIR limit of 10−J is mandated; then, unless one is willing to wager an upper limit on p[X = 0] , one cannot get a usable upper bound on p[X = 0 | Y = 1] from this limit on the FPIR, used all by itself, unless one supposes that p[Y = 1] > 10−J+1.
To save writing, denote by L01 the crucial likelihood p[X = 0 | Y = 1] ; and suppose that is some desired upper bound on L01 now. Assume that the FPIR achieved by a service provider is an accurate estimate of p[Y = 1 |X = 0] ; then from (1) we get

Now [X = 0] should not be a rare event at all, and, conversely, [Y = 1] should be a rare event.[4] So one should be able to set some reasonable upper limit to the ratio p[Y = 1]/ p[X = 0] : but without attempting any precise estimate, at all, of either individual probability. One may reasonably expect, for instance, that no more than one in a thousand applicants for a uid will already have been registered; and when p[X = 1] < 10−3 we will have
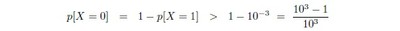
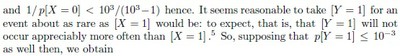
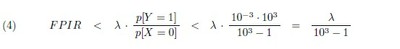
from (3) above. This calculation can be repeated with any number m in place of 3 here, of course, provided p[X = 1] < 10−m and p[Y = 1] < 10−m are both likely; and it seems entirely reasonable, now, for the UIDAI to insist that its biometric service providers meet the requirement.
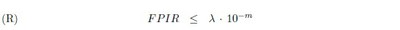
for some appropriate upper bound X on L01 . The considerations leading to (4) make it reasonable to insist on m _ 3 now; and recalling what L01 is — the crucial likelihood that, despite his or her signatures matching some already recorded suite of signatures, an applicant has not in fact been registered — the UIDAI will have to insist on some quite small bound X: for it would not want, too often, to refuse anyone a UID on account of a mistaken match of biometric signatures.[6]
It would be foolish to speculate on what the authorities regard as acceptable error here; but if the UIDAI is of a mind that such mistakes should happen less than one in a thousand times say, then, taking the minimal value of 3 for m in the suggested requirement (R), it should demand an FPIR less than 10−6 : a ‘false positive identification rate’ a thousand-fold less than the limit currently imposed.
[4]The event [Y = 1] must be just as rare, one supposes, as [X = 0] is frequent.
See the RTI application of 30/06/2011 [PDF, 15 kb].
Download the Seventh Open Letter here
SCOSTA and UID Comparison not Valid, says Finance Committee
On January 6, 2011, CIS had sent an open letter to the Parliamentary Finance Committee demonstrating how the Aadhaar biometric standard is weaker than the SCOSTA standard. The text of the reply is reproduced below.
Sir,
This is in response to one of the views/suggestions offered by CIS on the National Identification Authority of India Bill, 2010.
CIS View /Suggestion:
"Though the Aadhaar biometrics are useful for the de-duplication and identification of individuals, the Smart Card Operating System for Transport Application [(SCOSTA), developed by the National Informatics Centre in India)] standard is a more secure, structurally sound, and cost-effective approach to authentication of identity for India. Therefore, the Aadhaar biometric based authentication process should be replaced with a SCOSTA standard based authentication process."
In this regard, do you agree with the following view? If not, please justify.
"Comparison between SCOSTA and the UID project are not valid since SCOSTA is fundamentally a standard for smart card based authentication and does not work for the objectives of the unique id project.
The UID project follows a different approach and has multiple objectives — providing identity to residents of India, ensuring inclusion of poor and marginalized residents in order to enable access to benefits and services, eliminating the fakes, duplicates and ghost identities prevalent in other databases and provide a platform for authentication in a cost effective and accessible manner.
UIDAI is not issuing cards or smart cards. Cards can be issued by agencies that are providing services. UID authentication does not exclude smart cards — service providers can still choose to issue smart cards to their beneficiaries or customers if they want to."
You are requested to email your view by 14 October, 2011 positively.
Standing Committee on Finance Branch
Lok Sabha Secretariat
Sixth Annual Meeting of the Internet Governance Forum, Nairobi: A Summary
Privacy, Security, and Access to Rights: A Technical and Policy Analyses
Workshop No. 219
The workshop was moderated by Kim Pham, Expression Technologies, Civil Society (United States). The panel members included Carlos Affonso Pereira de Souza, Centro de Technologica e Socieda (Brazil), Christopher Soghoian, Indiana University (United States), Karen Reilly, Tor Project, Technical/Civil Society (United States) and Sunil Abraham, Centre for Internet and Society (India).
See the workshop details here
Use of Digital Technologies for Civic Engagement and Political Change: Lessons Learned and Way Forward
Workshop No. 184
The workshop was moderated by Katim S Touray Council Vice Chair, Free Software and Open Source Foundation for Africa and Member, ICANN Board of Directors. Fouad Bajwa of Gerry Morgan Foundation (Pakistan) was the remote moderator. Nnenna Nwakanma of Nnenna.org, Simeon Oriko of @TheKuyuProject &@StorySpaces, Wael Khalil, Activist and Sunil Abraham of the Centre for Internet & Society were the panel members. Nishant Shah from the Centre for Internet & Society participated remotely from Bangalore.
See the workshop details here
See the entire transcription here
The Impact of Regulation: FOSS and Enterprise
Workshop No. 211
The workshop was moderated by Dorothy Gordon, Director General, AITI-KACE, Judy Okite was the remote moderator. The panel members were Satish Babu, ICFOSS, India, Yves Miezan Ezo, Smile Training, Manager, (France), Sunil Abraham, Executive Director, Centre for Internet & Society, Bangalore, Evans Ikua, FOSS Certification Manager, ict@innovation program.
See the workshop details here
See the entire transcription here
Proprietary Influences in Free and Open Source Software: Lessons to Open and Universal Internet Standards
Workshop No. 201
The workshop was moderated by Alejandro Pisanty, Director General for Academic Computing Services of the National University of Mexico (UNAM), Mexico. Tracy Hackshaw, Computer Society of Trinadad and Tobago, Trinadad and Tobago, Venkatesh Hariharan, Head of Public Policy and Government Affairs at Google, India and Scott O Bradner, University Technology Security Officer, Harvard University, USA were the panel members.
See the workshop details here
See the entire transcription here
Access and Diversity of Broadband Internet Access
Workshop No. 113
The workshop was moderated by N Ravi Shanker, Addl Secy, Department of Information Technology, Ministry of Information Technology, Government of India (Chair). Abhishek Singh, Director, Department of Information Technology, Ministry of Information Technology, Government of India, Venkatesh Hariharan, Head of Public Policy and Government Relations, Google India and Sunil Abraham, Executive Director, The Centre for Internet and Society, India were the panel members.
See the workshop details here
See the entire transcription here
Putting users First: How can Privacy be Protected in Today’s Complex Mobile Ecosystem?
Workshop No. 75
This workshop was moderated by Ambassador David Gross, Partner, Wiley Rein LLP, Yiannis Theodorou, Regulatory Policy Manager, GSMA was the remote moderator. The panel members included Pat Walshe, Director of Privacy-GSMA), Jeff Brueggeman (Vice President-Publiy Policy AT&T), Patrick Ryan, Policy Counsel, Open Internet for Google Inc, Ms Juliana Rotich, Executive Director of Ushahidi Inc, Sunil Abraham, Executive Director, The Centre for Internet and Society (India) and Ian Brown, co-director of Oxford University's Information Security and Privacy Programme.
See the workshop details here
See the entire transcription here
Analysis of DIT's Response to Second RTI on Website Blocking
What the DIT's Response Tells Us, and What It Doesn't
We at the Centre for Internet and Society had sent in a right to information request to the Department of Information Technology (DIT) asking for more information about website blocking in India. The response we got from the DIT was illuminating in many ways. The following are the noteworthy points, in brief:
- Six government officials, and one politician have so far made requests for 'disabling access' to certain online content under s.69A of the Information Technology (IT) Act.
- 68 individual items have been requested to be blocked, those being 64 websites (domain-level blocking), 1 sub-domain, and 3 specific web pages. Seemingly, none of these requests have been accepted.
- The data provided by the government seemingly conflicts with the data released by the likes of Google (via its Transparency Report).
- India's law enforcement agencies are circumventing the IT Act, the Indian Penal Code (IPC), and ultimately the Constitution, by not following proper procedure for removal of online content.
- Either the DIT is not providing us all the relevant information on blocking, or is not following the law.
Conflicting Data on Censorship Requests
The latest Google Transparency Report, released on October 25, 2011, shows that there were 68 written requests (imaginably taking the form of forceful requests/orders) from Indian law enforcement agencies for removal of 358 items from Google's various. If you take the figures since January 2010, it adds up to over 765.
However, the official government statistics show only eight separate requests having been made to the DIT (which, under the IT Act, is the only authority that can order the blocking of online content), adding up to a total of 64 websites (domain-level), 1 sub-domain, and 3 specific web pages. Of these only 3 are for Google's services (2 for Blogger, and 1 for YouTube).
If classified according to presumable reason for seeking of the block, that would be 61 domains hosting adult content; 1 domain (tamil.net.in), 1 sub-domain (ulaginazhagiyamuthalpenn.blogspot.com), and 2 specific pages (video of a speech by Bal Thackeray on YouTube and Wikipedia page for Sukhbir Singh Badal) for political content; 1 for religious content (a blog post titled "Insults against Islam" in Malay); and 1 domain hosting online gambling (betfair.com). It is unclear for why one of the requests was made (topix.net).1
Content Removal vs. Content Blocking
Section 69A of the IT Act provides the Central Government the power to "direct any agency of the Government or intermediary to block for access by the public or cause to be blocked for access by the public any information generated, transmitted, received, stored or hosted in any computer resource". The only person through whom this power can be exercised is the 'Designated Officer' (currently Dr. Gulshan Rai of the DIT), who in turn has to follow the procedure laid down in the rules drafted under s.69A ("Information Technology (Procedure and Safeguard for Blocking for Access of Information by Public) Rules, 2009", the 'Blocking Rules').
Because of this, we see everyone from the Secretary of the Public Law and Order Department of Tamil Nadu to the Joint Commissioner of Police of Mumbai and the State President of the Bharatiya Janata Minority Morcha approaching the Designated Officer for blocking of websites.
However, as the data from Google shows, there are many times more requests being sent to remove content. The only explanation for this is that an order to 'block for access... or cause to be blocked for access by the public' is taken to be different from an order for removal of content. Nothing in the IT Act, nor in the Blocking Rules actually address this issue.2
Thus, there is a possibility that the forcible removal of content is treated separately from blocking of content. That would mean that while blocking is regulated by the IT Act, forcible removal of content is not. Thus, it would seem that forcible removal of online content is happening without clear regulation or limits.3
Role of the Indian Penal Code and Code of Criminal Procedure
There are existing provisions in the Indian Penal Code that provide the government the power to censor book, pamphlets, and other material on varied grounds, including obscenity, causing of enmity between communities, etc. The police is provided powers to enforce such governmental orders. Section 95 of the Code of Criminal Procedure allows the State Government to declare (through an official notification) certain publications which seem to violate the Indian Penal Code as 'forfeited to the Government' and to issue search warrants for the same. After this the police can enforce that notification.
It is clear that this is not the case for any of the content removal requests that were sent to Google.
Police Are Defeating the Constitution and the IT Act
Therefore, it would seem that law enforcement agencies are operating outside the bounds set up under the Indian Penal Code, the Code of Criminal Procedure, as also the Information Technology Act, when they send requests for removal of content to companies like Google. While a company might comply with it because it appears to them to violate their own terms of service (which generally include a wide clause about content being in accordance with all local laws), community guidelines, etc., it would appear that it is not required under the law to do so if the order itself is not legal.
However, anecdotal evidence has it that most companies comply with such 'requests' even when they are not under any legal obligation to do so.
This way the intention of Parliament in enacting s.69A of the IT Act—to regulate government censorship of the Internet and bring it within the bounds laid down in the Constitution—is defeated.
DIT Either Evasive or Not Following Rules
The DIT did not provide answers on:
- Whether any block ordered by the DIT has ever been revoked
- On what basis DIT decides which intermediary (web host, ISP, etc.) to send the order of blocking to
It also provided the minutes for only one meeting4 of the committee that decides whether to carry out a block, when we had requested for minutes of all the meetings it has ever held. That committee (the Committee for Examination of Requests, constituted under Rule 8(4) of the Blocking Rules) has to consider every single item in every single request forwarded to the Designated Officer, and 68 items were sent to the Designated Officer in 6 requests. Quite clearly something doesn't add up. Either the Committee is not following the Blocking Rules or the DIT is not providing a full reply under the RTI Act.
-
A request was made to block http://www.topix.net, by the 'Commmissioner, Maharashtra State, Colaba, Mumbai—400001', presumably the Commissioner of State Intelligence Department of Maharashtra, whose office is located in Colaba. ↩
-
However, the Blocking Rules require the person or the hosting intermediary being contacted for a response. This provides the person/intermediary the opportunity to remove the content voluntarily or to oppose the request for blocking.
"Rule 8. Examination of request: (1) On receipt of request under rule 6, the Designated Officer shall make all reasonable efforts to identify the person or intermediary who has hosted the information or part thereof as well as the computer resource on which such information or part thereof is being hosted and where he is able to identify such person or intermediary and the computer resource hosting the information or part thereof which have been requested to be blocked for public access, he shall issue a notice by way of letters or fax or e-mail signed with electronic signatures to such person or intermediary in control of such computer resource to appear and submit their reply and clarifications if any, before the committee referred to in rule 7, at a specified date and time, which shall not be less than forty-eight hours from the time of receipt of such notice by such person or intermediary." ↩
-
While it is possible to imagine that the Indian Penal Code and the Code of Criminal Procedure lay down limits, it is clear from the Google Transparency Report that the requests from removal are not coming based only on court orders, but from the executive and the police. The police have no powers under the IPC or the CrPC to request removal of content without either a public notification issued by the State Government or a court order. ↩
-
The minutes of the meeting held on August 24, 2010, on the request for blocking of www.betfair.com were sent as 'Annexure III' of the DIT response. This request was not granted. ↩
India's Statement Proposing UN Committee for Internet-Related Policy
66th Session of the UN General Assembly
New York. October 26, 2011.
Agenda Item 16: Information and Communications
Technologies for Development (ICT): Global Internet Governance
Statement by India
Mr. Chairman,
We thank the Secretary-General for his report on enhanced cooperation on public policy issues pertaining to the Internet, contained in document A/66/77, which provides a useful introduction to the discussions under this agenda item.
As a multi-ethnic, multi-cultural and democratic society with an open economy and an abiding culture of pluralism, India emphasizes the importance that we attach to the strengthening of the Internet as a vehicle for openness, democracy, freedom of expression, human rights, diversity, inclusiveness, creativity, free and unhindered access to information and knowledge, global connectivity, innovation and socio-economic growth.
We believe that the governance of such an unprecedented global medium that embodies the values of democracy, pluralism, inclusion, openness and transparency should also be similarly inclusive, democratic, participatory, multilateral and transparent in nature.
Indeed, this was already recognized and mandated by the Tunis Agenda in 2005, as reflected in paragraphs 34, 35, 56, 58, 59, 60, 61 and 69 of the Agenda. Regrettably, in the six long years that have gone by, no substantial initiative has been taken by the global community to give effect to this mandate.
Meanwhile, the internet has grown exponentially in its reach and scope, throwing up several new and rapidly emerging challenges in the area of global internet governance that continue to remain inadequately addressed. It is becoming increasingly evident that the Internet as a rapidly-evolving and inherently global medium, needs quick-footed and timely global solutions and policies, not divergent and fragmented national policies.
The range and criticality of these pressing global digital issues that continue to remain unaddressed, are growing rapidly with each passing day. It is, therefore, urgent and imperative that a multilateral, democratic participative and transparent global policy-making mechanism be urgently instituted, as mandated by the Tunis Agenda under the process of ‘Enhanced Co-operation’, to enable coherent and integrated global policy-making on all aspects of global Internet governance.
Operationalizing the Tunis mandate in this regard should not be viewed as an attempt by governments to “take over” or “regulate and circumscribe” the internet. Indeed, any such misguided attempt would be antithetical not only to the internet, but also to human welfare. As a democratic and open society that has historically welcomed outside influences and believes in openness to all views and ideas and is wedded to free dialogue, pluralism and diversity, India attaches great importance to the preservation of the Internet as an unrestricted, open and free global medium that flourishes through private innovation and individual creativity and serves as a vehicle for open communication, access to culture, knowledge, democratization and development.
India recognizes the role played by various actors and stakeholders in the development and continued enrichment of the internet, and is firmly committed to multi-stakeholderism in internet governance, both at the national and global level. India believes that global internet governance can only be functional, effective and credible if all relevant stake-holders contribute to, and are consulted in, the process.
Bearing in mind the need for a transparent, democratic, and multilateral mechanism that enables all stakeholders to participate in their respective roles, to address the many cross-cutting international public policy issues that require attention and are not adequately addressed by current mechanisms and the need for enhanced cooperation to enable governments, on an equal footing, to carry out their roles and responsibilities in international public policy issues pertaining to the Internet, India proposes the establishment of a new institutional mechanism in the United Nations for global internet-related policies, to be called the United Nations Committee for Internet-Related Policies (CIRP). The intent behind proposing a multilateral and multi-stakeholder mechanism is not to “control the internet’’ or allow Governments to have the last word in regulating the internet, but to make sure that the Internet is governed not unilaterally, but in an open, democratic, inclusive and participatory manner, with the participation of all stakeholders, so as to evolve universally acceptable, and globally harmonized policies in important areas and pave the way for a credible, constantly evolving, stable and well-functioning Internet that plays its due role in improving the quality of peoples’ lives everywhere.
The CIRP shall be mandated to undertake the following tasks:
- Develop and establish international public policies with a view to ensuring coordination and coherence in cross-cutting Internet-related global issues;
- Coordinate and oversee the bodies responsible for technical and operational functioning of the Internet, including global standards setting;
- Facilitate negotiation of treaties, conventions and agreements on Internet-related public policies;
- Address developmental issues related to the internet;
- Promote the promotion and protection of all human rights, namely, civil, political, social, economic and cultural rights, including the Right to Development;
- Undertake arbitration and dispute resolution, where necessary; and,
- Crisis management in relation to the Internet.
The main features of CIRP are provided in the annex to this statement. In brief, the CIRP will comprise 50 Member States chosen on the basis of equitable geographical representation, and will meet annually for two working weeks in Geneva. It will ensure the participation of all relevant stakeholders by establishing four Advisory Groups, one each for civil society, the private sector, inter-governmental and international organizations, and the technical and academic community. The Advisory Groups will provide their inputs and recommendations to the CIRP. The meetings of CIRP and the advisory groups will be serviced by the UNCTAD Secretariat that also services the meetings of the Commission on Science and Technology for Development. The Internet Governance Forum will provide inputs to CIRP in the spirit of complementarity between the two. CIRP will report directly to the General Assembly and present recommendations for consideration, adoption and dissemination among all relevant inter-governmental bodies and international organizations. CIRP will be supported by the regular budget of the United Nations; a separate Fund would be set up by drawing from the domain registration fees collected by various bodies, in order to mainly finance the Research Wing to be established by CIRP to support its activities.
Those familiar with the discourse on global internet governance since the beginning of the WSIS process at the turn of the millennium, will recognize that neither the mandated tasks of the CIRP, nor its proposed modalities, are new. The Working Group on Internet Governance (WGIG) set up by the UN Secretary- General had explicitly recognized the institutional gaps in global internet governance and had proposed four institutional models in its report to the UN General Assembly in 2005. The contours of the CIRP, as proposed above, reflect the common elements in the four WGIG institutional models. While the excellent report of the WGIG was much discussed and deliberated in 2005, unfortunately, no concrete follow-up action was taken to give effect to its recommendations on the institutional front. We hope that this anomaly will be redressed at least six years later, with the timely establishment of the CIRP.
In order to operationalize this proposal, India calls for the establishment of an open-ended working group under the Commission on Science and Technology for Development for drawing up the detailed terms of reference for CIRP, with a view to actualizing it within the next 18 months. We are open to the views and suggestions of all Member States, and stand ready to work with other delegations to carry forward this proposal, and thus seek to fill the serious gap in the implementation of the Tunis Agenda, by providing substance and content to the concept of Enhanced Co-operation enshrined in the Tunis Agenda.
Thank you, Mr. Chairman.
***
Annex
The United Nations Committee for Internet-Related Policies (CIRP)
The United Nations Committee for Internet-Related Policies (CIRP) will have the following features:
Membership: The CIRP will consist of 50 Member States of the United Nations, chosen/elected on the basis of equitable geographical representation. It will provide for equitable representation of all UN Member States, in accordance with established UN principles and practices. It will have a Bureau consisting of one Chair, three Vice-Chairs and a Rapporteur.
Meetings: The CIRP will meet annually for two working weeks in Geneva, preferably in May/June, and convene additional meetings, as and when required. The UNCTAD Secretariat will provide substantive and logistical support to the CIRP by servicing these meetings.
Multi-stakeholder participation: Recognizing the need to involve all stakeholders in Global Internet Governance in their respective roles, the CIRP shall ensure the participation of all stakeholders recognized in the Tunis Agenda. Four Advisory Groups – one each for Civil Society, the Private Sector, Inter-Governmental and International Organisations, and the Technical and Academic Community - will be established, to assist and advise the CIRP. These Groups would be self-organized, as per agreed principles, to ensure transparency, representativity and inclusiveness. The Advisory Groups will meet annually in Geneva and in conjunction with any additional meetings of the CIRP. Their meetings will be held back-to- back with the meetings of the CIRP, so that they are able to provide their inputs and recommendations in a timely manner, to the CIRP.
Reporting: The CIRP will report directly to the UN General Assembly annually, on its meetings and present recommendations in the areas of policy and implementation for consideration, adoption and dissemination to all relevant inter-governmental bodies and international organizations. .
Research Wing: The Internet is a rapidly-evolving and dynamic medium that throws up urgent and rapidly-evolving challenges that need timely solutions. In order to deal effectively and prudently with these emerging issues in a timely manner, it would be vital to have a well-resourced Research Wing attached to the CIRP to provide ready and comprehensive background material, analysis and inputs to the CIRP, as required.
Links with the IGF: Recognizing the value of the Internet Governance Forum as an open, unique forum for multi-stakeholder policy dialogue on Internet issues, the deliberations in the IGF along with any inputs, background information and analysis it may provide, will be taken as inputs for consideration of the CIRP. An improved and strengthened IGF that can serve as a purposeful body for policy consultations and provide meaningful policy inputs to the CIRP, will ensure a stronger and more effective complementarity between the CIRP and the IGF.
Budget: Like other UN bodies, the CIRP should be supported by the regular budget of the United Nations. In addition, keeping in view its unique multi-stakeholder format for inclusive participation, and the need for a well-resourced Research Wing and regular meetings, a separate Fund should also be set up drawing from the domain registration fees collected by various bodies involved in the technical functioning of the Internet, especially in terms of names and addresses.
***
Excerpts from the Tunis Agenda
Paragraph 34 of the Tunis Agenda defines Internet Governance as “the development and application by governments, the private sector and civil society, in their respective roles, of shared principles, norms, rules, decision-making procedures, and programmes that shape the evolution and use of the Internet”.
Paragraph 35 reaffirms the respective roles of stakeholders as follows: “(a) Policy authority for Internet-related public policy issues is the sovereign right of States. They have rights and responsibilities for international Internet-related public policy issues”. (b) The private sector has had, and should continue to have, an important role in the development of the Internet, both in the technical an economic fields. (c) Civil society has also played an important role on Internet matters, especially at community level, and should continue to play such a role. (d) Intergovernmental organizations have had, and should continue to have, a facilitating role in the coordination of Internet-related public policy issues. (e) International organizations have also had and should continue to have an important role in the development of Internet-related technical standards and relevant policies.”
While delineating the respective roles of stakeholders, Paragraph 56 recognizes the need for an inclusive, multi-stakeholder approach by affirming that “The Internet remains a highly dynamic medium and therefore any framework and mechanisms designed to deal with Internet governance should be inclusive and responsive to the exponential growth and fast evolution of the Internet as a common platform for the development of multiple applications”.
Paragraph 58 recognizes “that Internet governance includes more than Internet naming and addressing. It also includes other significant public policy issues such as, inter alia, critical Internet resources, the security and safety of the Internet, and developmental aspects and issues pertaining to the use of the Internet”.
Paragraph 59 further recognizes that “Internet governance includes social, economic and technical issues including affordability, reliability and quality of service”. Paragraph 60 further recognizes that “there are many cross-cutting international public policy issues that require attention and are not adequately addressed by the current mechanisms”.
Paragraph 61 of the Tunis Agenda therefore concludes that “We are convinced that there is a need to initiate, and reinforce, as appropriate, a transparent, democratic, and multilateral process, with the participation of governments, private sector, civil society and international organisations, in their respective roles. This process could envisage creation of a suitable framework or mechanisms, where justified, thus spurring the ongoing and active evolution of the current arrangements in order to synergize the efforts in this regard”.
Paragraph 69 further recognizes “the need for enhanced cooperation in the future, to enable governments, on an equal footing, to carry out their roles and responsibilities, in international public policy issues pertaining to the Internet, but not in the day-to-day technical and operational matters, that do not impact on international public policy issues”.
***
Press Coverage of Online Censorship Row
Monday, December 5, 2011
India Asks Google, Facebook to Screen Content | Heather Timmons (New York Times, India Ink)
Tuesday, December 6, 2011
Sibal warns social websites over objectionable content | Sandeep Joshi (The Hindu)
Hate speech must be blocked, says Sibal | Praveen Swami & Sujay Mehdudia (The Hindu)
Won't remove material just because it's controversial: Google | (Press Trust of India)
Any Normal Human Being Would Be Offended | Heather Timmons (New York Times, India Ink)
After Sibal, Omar too feels some online content inflammatory | (Press Trust of India)
Online uproar as India seeks social media screening | Devidutta Tripathy and Anurag Kotoky (Reuters)
Kapil Sibal for content screening: Facebook, Twitter full of posts against censorship | (IANS)
India May Overstep Its Own Laws in Demanding Content Filtering | John Ribeiro (IDG)
Kapil Sibal warns websites: Mixed response from MPs | (Press Trust of India)
Websites must clean up content, says Sibal | (NewsX)
Kapil Sibal warns websites; Google says won't remove material just because it's controversial | Press Trust of India
Censorship By Any Other Name... | Yamini Lohia (Mint)
Kapil Sibal: We have to take care of sensibility of our people | Associated Press
Kapil Sibal gets backing of Digvijaya Singh over social media screening | Press Trust of India
Sibal Gets What He Set Out To Censor | (Hindustan Times, Agencies)
Objectionable Matter Will Be Removed, Censorship Not in Picture Yet: Kapil Sibal | Amar Kapadia (News Tonight)
Wednesday, December 7, 2011
Kapil Sibal Doesn't Understand the Internet | Shivam Vij (India Today)
'Chilling' Impact of India's April Internet Rules | Heather Timmons (New York Times, India Ink)
Screening, not censorship, says Sibal | (Business Standard)
Chandni Chowk to China | Salil Tripathi (Mint)
Kapil Sibal vs the internet | Sandipan Deb (Mint)
No Need for Censorship of the Internet: Cyber Law Experts | (Times News Network)
Protest with flowers for Sibal | (The Hindu)
Kapil Sibal cannot screen this report | Team DNA, Blessy Chettiar & Renuka Rao (Daily News and Analysis)
Kapil Sibal warns websites, but experts say prescreening of user content not practical | (Reuters)
Sibal's Remarks Brought Disgust | Hitesh Mehta (News Tonight)
BJP backs mechanism to curb objectionable content on websites | (The Hindu)
Move to regulate networking sites should be discussed in Parliament: BJP | (Press Trust of India)
Sibal under attack in cyberspace | (Press Trust of India)
Kapil Sibal's web censorship: Indian govt wanted 358 items removed, says Google | (Press Trust of India)
Kapil Sibal gets BJP support but with rider | (Indo-Asian News Service)
Sibal's way of regulating web not okay, says BJP | (Indo-Asian News Service)
Censorship in Blasphemy's Clothings | Gautam Chikermane (Hindustan Times, Just Faith)
India wants Google, Facebook to screen content | Sharon Gaudin (Computer World)
Should we be taming social media? | Swati Prasad (ZDNet, Inside India)
Kapil Sibal gets lampooned for views on Web control | (Daily News and Analysis)
'We don't need no limitation' | Asha Prakash (Times of India)
Five reasons why India can't censor the internet | Prasanto K. Roy (Indo-Asian News Service)
We Are the Web | (Indian Express)
Thursday, December 8, 2011
Kapil Sibal under attack in cyberspace, (Press Trust of India)
Speak Up for Freedom | Pranesh Prakash (Indian Express)
Newswallah: Censorship | Neha Thirani (New York Times, India Ink)
No Question of Censoring the Internet, Says Sachin Pilot | (NDTV)
Mind Your Netiquette, or We'll Mind it for You | A.A.K. (The Economist)
Take Parliament's view to regulate social networking sites, BJP tells govt | (Times News Network)
India wanted 358 items removed | Priscilla Jebaraj (The Hindu)
Indian Government v Social Networking sites: Expert Views | (Bar & Bench News Network)
Can Government Muzzle Websites? | Priyanka Joshi & Piyali Mandal (Business Standard)
US concerned over internet curbs, sidesteps India move | (Indo-Asian News Service)
Why Internet Companies Are Upset with Kapil Sibal | (Rediff)
Why Censor Facebook When You Don't Censor Sunny Leone? | (Indo-Asian News Service)
Online content issue: Talks with India on, says U.S. | (Press Trust of India)
US calls for Internet freedom amid India plan | Agence France-Presse
How India Makes E-books Easier to Ban than Books (And How We Can Change That)
E-Books Are Easier To Ban Than Books, And Safer
Contrary to what Mr. Sibal's recent hand-wringing at objectionable online material might suggest, under Indian laws currently in force it is far easier to remove material from the Web, by many degrees of magnitude, than it is to ever get them removed from a bookstore or an art gallery. To get something from a bookstore or an art gallery one needs to collect a mob, organize collective outrage and threats of violence, and finally convince either the government or a magistrate that the material is illegal, thereby allowing the police to seize the books or stop the painting from being displayed. The fact of removal of the material will be noted in various records, whether in government records, court records, police records or in newspapers of record. By contrast, to remove something from the Web, one needs to send an e-mail complaining about it to any of the string of 'intermediaries' that handle the content: the site itself, the web host for the site, the telecom companies that deliver the site to your computer/mobile, the web address (domain name) provider, the service used to share the link, etc. Under the 'Intermediary Guidelines Rules' that have been in operation since 11th April 2011, all such companies are required to 'disable access' to the complained-about content within thirty-six hours of the complaint. It is really that simple.
"That's ridiculous," you think, "surely he must be exaggerating." Think again. A researcher working with us at the Centre for Internet and Society tried it out, several times, with many different intermediaries and always with frivolous and flawed complaints, and was successful six out of seven times . Thus it is easier to prevent Flipkart or Amazon from selling Rushdie's Midnight's Children than it is to prevent a physical bookstore from doing so: today Indira Gandhi wouldn't need to win a lawsuit in London against the publishers to remove a single line as she did then; she would merely have to send a complaint to online booksellers and get the book removed. It is easier to block Vinay Rai's Akbari.in (just as CartoonsAgainstCorruption.com was recently blocked) than it is to prevent its print publication. Best of all for complainants: there is no penalty for frivolous complaints such as those sent by us, nor are any records kept of who's removed what. Such great powers of censorship without any penalties for their abuse are a sure-fire way of ensuring a race towards greater intolerance, with the Internet — that republic of opinions and expressions — being a casualty.
E-Book Bans Cannot Be Challenged
In response to some of the objections raised, the Cyberlaw Division of the Department of Information Technology, ever the dutiful guardian of free speech, noted that if you have a problem with access to your content being 'disabled', you could always approach a court and get that ban reversed. Unfortunately, the Cyberlaw Division of the Department of Information Technology forgot to take into account that you can't contest a ban/block/removal if you don't know about it. While they require all intermediaries to disable access to the content within thirty-six hours, they forgot to mandate the intermediary to tell you that the content is being removed. Whoops. They forgot to require the intermediary to give public notice that content has been removed following a complaint from person ABC or corporation XYZ on such-and-such grounds. Whoops, again.
So while records are kept, along with reasons, of book bans, there are no such records required to be kept of e-book bans.
E-Book Censors Are Faceless
Vinay Rai is a brave man. He is being attacked by fellow journalists who believe he's disgracing the professional upholders of free-speech, and being courted by television channels who believe that he should be encouraged to discuss matters that are sub judice. He is viewed by some as a man who's playing politics in courts on behalf of unnamed politicians and bureaucrats, while others view him as being bereft of common-sense for believing that companies should be legally liable for not having been clairvoyant and removing material he found objectionable, though he has never complained to them about it, and has only provided that material to the court in a sealed envelope. I choose, instead, to view him as a scrupulous and brave man. He has a face, and a name, and is willing to openly fight for what he believes in. However, there are possibly thousands of unscrupulous Vinay Rais out there, who know the law better than he does, and who make use not of the court system but of the Intermediary Guidelines Rules, firmly assured by those Rules that their censorship activities will never be known, will never be challenged by Facebook and Google lawyers, and will never be traced back to them.
Challenging Invisible Censorship
Dear reader, you may have noticed that this is a bit like a trial involving Free Speech in which Free Speech is presumed guilty upon complaint, is not even told what the charges against it are, has not been given a chance to prove its innocence, and has no right to meet its accusers nor to question them. Yet, the Cyberlaw Division of the Department of Information Technology continues to issue press releases defending these Rules as fair and just, instead of being simultaneously Orwellian and Kafkaesque. These Rules are delegated legislation passed by the Department of Information Technology under s.79 of the Information Technology Act. The Rules were laid before Parliament during the 2011 Monsoon session. We at CIS believe that these Rules are *ultra vires* the IT Act as well as the Constitution of India, not only with respect to what is now (newly) proscribed online (which in itself is enough to make it unconstitutional), but how that which is purportedly unlawful is to be removed. We have prepared an alternative that we believe is far more just and in accordance with our constitutional principles, taking on best practices from Canada, the EU, Chile, and Brazil, while still allowing for expeditious removal of unlawful material. We hope that the DIT will consider adopting some of the ideas embodied in our draft proposal.
As Parliament passed the IT Act in the midst of din, without any debate, it is easy to be skeptical and wonder whether Rules made under the IT Act will be debated. However, I remain hopeful that Parliament will not only exercise its power wisely, but will perform its solemn duty — borne out of each MP's oath to uphold our Constitution — by rejecting these Rules.
Photo credit: Lynn Gardner, under CC-BY-NC-SA 2.0 licence*
This was reproduced in Outlook Magazine on 27 January 2012
Statutory Motion Against Intermediary Guidelines Rules
Motion to Annul Intermediary Guidelines Rules
A motion to annul the Intermediary Guidelines Rules was moved on March 23, 2012, by Shri P. Rajeeve, CPI(M) MP in the Rajya Sabha from Thrissur, Kerala.
The motion reads:
"That this House resolves that the Information Technology (Intermediaries Guidelines) Rules, 2011 issued under clause (zg) of sub-section (2) of Section 87 read with sub-section (2) of Section 79 of the Information Technology Act, 2000 published in the Gazette of India dated the 13th April, 2011 vide Notification No. G.S.R 314(E) and laid on the Table of the House on the 12th August, 2011, be annuled; and
That this House recommends to Lok Sabha that Lok Sabha do concur on this Motion."
This isn't the first time that Mr. Rajeeve is raising his voice against the Intermediary Guidelines Rules. Indeed, even when the Rules were just in draft stage, he along with the MPs Kumar Deepak Das, Rajeev Chandrashekar, and Mahendra Mohan drew Parliamentarians' attention to the rules. Yet, the government did not heed the MPs' concern, nor the concern of all the civil society organizations that wrote in to them concerned about human rights implications of the new laws. On September 6, 2011, Lok Sabha MP Jayant Choudhary gave notice (under Rule 377 of the Lok Sabha Rules) that the Intermediary Guidelines Rules as well as the Reasonable Security Practices Rules need to be reviewed. Yet, the government has not even addressed those concerns, and indeed has cracked down even harder on online freedom of speech since then.
Fundamental Problems with Intermediary Guidelines Rules
The fundamental problems with the Rules, which deal with objectionable material online:
Shifting blame.
It makes the 'intermediary', including ISPs like BSNL and Airtel responsible for objectionable content that their users have put up.
No chance to defend.
There is no need to inform users before this content is removed. So, even material put up by a political party can be removed based on anyone's complaint, without telling that party. This was done against a site called *CartoonsAgainstCorruption.com". This goes against Article 19(1)(a).
Lack of transparency
No information is required to be provided that content has been removed. It's a black-box system, with no one, not even the government, knowing that content has been removed following a request. So even the government does not know how many sites have been removed after these Rules have come into effect.
No differentiation between intermediaries.
A one-size-fits-all system is followed where an e-mail provider is equated with an online newspaper, which is equated with a video upload site, which is equated with a search engine. This is like equating the post-office and a book publisher as being equivalent for, say, defamatory speech. This is violative of Article 14 of the Constitution, which requires that unequals be treated unequally by the law.
No proportionality.
A DNS provider (i.e., the person who gives you your web address) is an intermediary who can be asked to 'disable access' to a website on the basis of a single page, even though the rest of the site has nothing objectionable.
Vague and unconstitutional requirements.
Disparaging speech, as long as it isn't defamatory, is not criminalised in India, and can't be because the Constitution does not allow for it. Content about gambling in print is not unlawful, but now all Internet intermediaries are required to remove any content that promotes gambling.
Allows private censorship.
The Rules do not draw a distinction between arbitrary actions of an intermediary and take-downs subsequent to a request.
Presumption of illegality.
The Rules are based on the presumption that all complaints (and resultant mandatory taking down of the content) are correct, and that the incorrectness of the take-downs can be disputed in court (if they ever discover that it has been removed). This is contrary to the presumption of validity of speech used by Indian courts, and is akin to prior restraint on speech. Courts have held that for content such as defamation, prior restraints cannot be put on speech, and that civil and criminal action can only be taken post-speech.
Government censorship, not 'self-regulation'.
The government says these are industry best-practices in existing terms of service agreements. But the Rules require all intermediaries to include the government-prescribed terms in an agreement, no matter what services they provide. It is one thing for a company to choose the terms of its terms of service agreement, and completely another for the government to dictate those terms of service.
Problems Noted Early
We have noted in the past the problems with the Rules, including when the Rules were still in draft form:
-
CIS Para-wise Comments on Intermediary Due Diligence Rules, 2011
-
Invisible Censorship: How the Government Censors Without Being Seen
Other organizations like the Software Freedom Law Centre also sent in scathing comments on the law, noting that they are unconstitutional.
We are very glad that Shri Rajeeve has moved this motion, and we hope that it gets adopted in the Lok Sabha as well, and that the Rules get defeated.
India's Broken Internet Laws Need a Shot of Multi-stakeholderism
(An edited version of this article was published in the Indian Express as "Practise what you preach" on Thursday, April 26, 2012.)
The laws in India relating to the Internet are greatly flawed, and the only way to fix them would be to fix the way they are made. The Cyber-Laws & E-Security Group in the Department of Electronics and Information Technology (DEIT, who refer to themselves as 'DeitY' on their website!) has proven itself incapable of making fair, balanced, just, and informed laws and policies. The Information Technology (IT) Act is filled with provisions that neither lawyers nor technologists understand (not to mention judges). (The definition of "computer source code" in s.65 of the IT Act is a great example of that.)
The Rules drafted under s.43A of the IT Act (on 'reasonable security practices' to be followed by corporations) were so badly formulated that the government was forced to issue a clarification through a press release, even though the clarification was in reality an amendment and amendments cannot be carried out through press releases. Despite the clarification, it is unclear to IT lawyers whether the Rules are mandatory or not, since s.43A (i.e., the parent provision) seems to suggest that it is sufficient if the parties enter into an agreement specifying reasonable security practices and procedures. Similarly, the "Intermediary Guidelines" Rules (better referred to as the Internet Censorship Rules) drafted under s.79 of the Act have been called "arbitrary and unconstitutional" by many, including MP P. Rajeev, who has introduced a motion in the Rajya Sabha to repeal the Rules ("Caught in a net", Indian Express, April 24, 2012). These Rules give the power of censorship to every citizen and allow them to remove any kind of material off the Internet within 36 hours without anybody finding out. Last year, we at the Centre for Internet and Society used this law to get thousands of innocuous links removed from four major search engines without any public notice. In none of the cases (including one where an online news website removed more material than the perfectly legal material we had complained about) were the content-owners notified about our complaint, much less given a chance to defend themselves.
Laws framed by the Cyber-Law Group are so poorly drafted that they are misused more often than used. There are too many criminal provisions in the IT Act, and their penalties are greatly more than that of comparable crimes in the IPC. Section 66A of the IT Act, which criminalizes "causing annoyance or inconvenience" electronically, has a penalty of 3 years (greater than that for causing death by negligence), and does not require a warrant for arrest. This section has been used in the Mamata Banerjee cartoon case, for arresting M. Karthik, a Hyderabad-based student who made atheistic statements on Facebook, and against former Karnataka Lokayukta Santosh Hegde. Section 66A, I believe, imperils freedom of speech more than is allowable under Art. 19(2) of the Constitution, and is hence unconstitutional.
While s.5 of the Telegraph Act only allows interception of telephone conversations on the occurrence of a public emergency, or in the interest of the public safety, the IT Act does not have any such threshold conditions, and greatly broadens the State's interception abilities. Section 69 allows the government to force a person to decrypt information, and might clash with Art.20(3) of the Constitution, which provides a right against self-incrimination. One can't find any publicly-available governmental which suggests that the constitutionality of provisions such as s.66A or s.69 was examined.
Omissions by the Cyber-Law Group are also numerous. The Indian Computer Emergency Response Team (CERT-In) has been granted very broad functions under the IT Act, but without any clarity on the extent of its powers. Some have been concerned, for instance, that the broad power granted to CERT-In to "give directions" relating to "emergency measures for handling cyber security incidents" includes the powers of an "Internet kill switch" of the kind that Egypt exercised in January 2011. Yet, they have failed to frame Rules for the functioning of CERT-In. The licences that the Department of Telecom enters into with Internet Service Providers requires them to restrict usage of encryption by individuals, groups or organisations to a key length of only 40 bits in symmetric key algorithms (i.e., weak encryption). The RBI mandates a minimum of 128-bit SSL encryption for all bank transactions. Rules framed by the DEIT under s.84A of the IT Act were to resolve this conflict, but those Rules haven't yet been framed.
All of this paints a very sorry picture. Section 88 of the IT Act requires the government, "soon after the commencement of the Act", to form a "Cyber Regulations Advisory Committee" consisting of "the interests principally affected or having special knowledge of the subject-matter" to advise the government on the framing of Rules, or for any other purpose connected with the IT Act. This body still has not been formed, despite the lag of more than two and a half years since the IT Act came into force. Justice Markandey Katju’s recent letter to Ambika Soni about social media and defamation should ideally have been addressed to this body.
The only way out of this quagmire is to practise at home that which we preach abroad on matters of Internet governance: multi-stakeholderism. Multi-stakeholderism refers to the need to recognize that when it comes to Internet governance there are multiple stakeholders: government, industry, academia, and civil society, and not just the governments of the world. This idea has gained prominence since it was placed at the core of the "Declaration of Principles" from the first World Summit on Information Society in Geneva in 2003, and has also been at the heart of India's pronouncements at forums like the Internet Governance Forum. Brazil has an "Internet Steering Committee" which is an excellent model that practices multi-stakeholderism as a means of framing and working national Internet-related policies. DEIT's Internet Governance Division, which formulates India's international stance on Internet governance, has long recognized that governance of the Internet must be done in an open and collaborative manner. It is time the DEIT's Cyber-Law and E-Security Group, which formulates our national stance on Internet governance, realizes the same.
Privacy Matters — Medical Privacy
The conversation brought together a cross section of citizens, lawyers, activists, researchers, academia and students.
 |
Prashant Iyengar, Assistant Professor, Jindal Law University, opened the conference with an explanation of Privacy India’s mandate to raise awareness, spark civil action and promote democratic dialogue around privacy challenges and violations in India. He summarized the series of ten consultations previously organized across India:
|
|---|

| Elonnai Hickok, a member of Privacy India, introduced the draft book Privacy in India: A Policy Guide that Privacy India has been compiling. Focusing on the draft chapter, Medical Privacy, she provided examples of legislation and policy containing safeguards to privacy such as Medical Council of India's Code of Ethics Regulations 2002, and pointed out legislation with missing safeguards such as in the Mental Health Act of 1987. Additionally, she gave many examples of projects being implemented in India that impact health privacy including Save the Baby Girl Project, the Mother and Child Tracking System, the UID, and a cloud based system known as Health Hiway. |
 |
|---|
Medical Privacy in India
 |
Dr. Dharmesh Lal, MBBS, DHA, MD, DNB, DVLDP, Officiating Dean, IIHMR, Delhi, discussed the correlation between medical privacy and confidentiality. Medical Privacy involves the confidentiality of patient-provider encounters, along with the secrecy and security of information memorialized in physical, electronic and graphic records created as a consequence of patient-provider encounters. Confidentiality involves restricting information to persons belonging to a set of specifically authorized recipients. |
|---|
He went on to explain that limited financial resources in public hospitals often preclude the separate examination of one patient at a time. “In Government hospitals, large numbers of patients congregate in the doctors office,” he says. Privacy is also related to a patient's financial status and decreases as one goes down the socio-economic ladder.
Additionally, he described the privacy concerns that arise due to infrastructural constraints. India's healthcare infrastructure has not kept up with the development of government health initiatives. For examples, the Janani Suraksha Yojana (JSY) initiative was launched in 2005, under the National Rural Health Mission (NRHM). JSY was implemented with the objective of reducing maternal and neo-natal mortality by promoting institutional delivery among the Poor Pregnant Woman. Financial incentives were provided to mothers. There was a phenomenal increase of institutional delivery. However, there was no proportional increase in infrastructure.
He called for a change in medical education, administration and management, stating, “Privacy protection has to be established as a core value that connects organizational culture. Alarmingly, medical curriculum in India does not have formal component on medical privacy, significant curriculum reforms in undergraduate medical teaching is necessary.
Medical Privacy- Legal Aspects
|
Mr. Pandit, Advocate, Pandit law Office, discussed the Hippocratic oath, which includes the duty of the caregiver to ‘keep secret’ and ‘never reveal’ ‘all that may come to my knowledge’. In other words, right to medical privacy has to be balanced with right to healthy life of another whose right will be affected unless such information is disclosed to her/him. He described the code of conduct prescribed by Indian Medical Council to its members, as a guideline to be followed is intended to preserve protect and uphold dignity of profession. Physicians should merit the confidence of patients entrusted to their care, rendering to each a full measure of service & devotion. |
 |
|---|
Referring to the Dr.Tokugha Yepthomi Vs Appollo Hospital Enterprises Ltd & Anr. III case, he described the Supreme Court’s verdict on the ‘Right to Life’.
The “Right to life” would positively include the right to be told that a person, with whom she was proposed to be married, was a victim of deadly disease, which was sexually communicable, since right of life includes right to lead a healthy life. Moreover where there is a clash of two fundamental rights, The RIGHT which would advance the public morality or public interest, would alone be enforced through the process of Court.
He concluded by asserting that there is considerable force in the argument that there is a need for a comprehensive legislation to protect the interest of poor patients and ordinary citizens who cannot afford to initiate a protracted legal battle to protect their medical privacy.
Supreme Court views on Medical Negligence
 |
Professor K. Elumalai, Director, School of law, IGNOU, provided numerous Supreme Court verdicts on medical negligence cases. He summarized the cases and discussed their salient features. He discussed the manner in which a Medical professional can be prosecuted for medical negligence under criminal law. It must be shown that the accused did something or failed to do something which in the given facts and circumstances, no medical professional in his ordinary senses and prudence would have done or failed to do. |
|---|
Confidentiality and privacy in medical Settigs vis-a-vis PLHIV
Ms. Nitu Sanadhya, Senior Legal Officer, Lawyers Collective, HIV/ AIDS Unit, stressed the importance of a rights-based approach and integrationist legal response to the HIV epidemic. When legislations or policies discriminate or isolate persons living with HIV, for example, through mandatory testing and breach of confidentiality, it drives the epidemic underground.
|
In India, there is no comprehensive law on HIV. In 2007, the National Aids Control Organization (NACO) released the Operational Guidelines for Integrated Counseling and Testing Centres. She described the salient features of the guideline especially focusing on the privacy provisions. She described the various situations that permit a health practitioner to disclose the HIV status of a patient to a partner and/ or third party. Discriminatory practices that arise out of a breach or confidentiality or privacy violation include stigmatization, denial of access to treatment, loss of employment, etc. |
 |
|---|
Under the RTI Act, A person’s HIV status is confidential and is protected in law and can only be disclosed to a third person in limited circumstances. The RTI Act specifically exempts the disclosure of personal information which is not of public interest; information which would cause an unwarranted invasion of privacy; and information which has been received in a fiduciary capacity. Therefore, The RTI Act 2005 cannot be used to obtain a person’s HIV report.
Privacy in Practice
|
|
Dr. Anand Philip, Personal Physician at NationWide Primary Healthcare Service Pvt. Ltd., drew from his personal experiences. During his presentation he emphasized how privacy is important, but it is clear that privacy does not happen the way it is theorized by. In fact there are many dichotomies in what we believe privacy is and how it is used. He pointed out that we often take for granted why privacy matters and where it comes from. He discussed how without patient autonomy and patient dignity, privacy cannot |
|---|
be upheld. Yet, one sees a constant breach of people’s dignities in the medical system. Some people rationalize this violation of dignity by explaining that in India, doctors are used to people who have nothing and thus, dignity is not important. Yet, he argued, dignity is something that is inherent. The lack of dignity practiced in India's medical system shows a problem with how we are trained. Giving an example of how dignity is breached in India, Dr. Philip referred to two people being treated on the same table. He pointed out that the physical aspects of privacy are non-existent. For example, the WHO recommends five feet between beds, but typically two or three feet exist between hospital beds. Furthermore, there are often no curtains in hospitals. He then moved from physical privacy to information physical. In a hospital information flows in all directions, it is not a controlled environment and the patient does not choose who sees his/her information – the hospital decided. Dr. Philip then talked about training. The health care system encompasses a larger team of people from doctors to sweepers. Training is only given to clinical staff. Thus other aspects such as the Indian culture, infrastructure, and training all impact how privacy is carried out in the medical field. In conclusion Dr. Philip re-stated that privacy is a byproduct of autonomy and dignity. He noted that offering a patient dignity was a critical step that must be taken by service providers. Closing his presentation, he challenged the audience with the following questions: Considering how autonomy is not important, how do we reach people with the idea? Since physical privacy is key to other forms of privacy, how do we take it more seriously? What can we do about the medical team's approach to privacy?
Best Practices of Medical Privacy in Various Health Settings
|
|
Sriram Lakshmanan, Head Information Security, UnitedHealth Group Information Systems, spoke about the US health-care market touching on medicare, medicaid, employer-sponsored insurance, and individual insurance plans. He also commented on the EU regime pointing out that most of the laws in the EU have a long list of identifiers indicating when your information counts as being compromised. Canada PIPEDA, is very strict and protects health privacy. In his opinion, the IT Act caters to many aspects of privacy. He also touched upon the eight OECD Privacy Principles and |
|---|
how they can be adopted for the Indian scenario. A few of the principles included collection limitation principle, data quality principle, purpose specification principle, use limitation principle. For example, if health information for treating malaria is collected, than that information should only be used for that purpose. Closing his presentation, he noted that most of the technologies that we use today for health run on IT, and thus can be used to compromise individual or hospital wide information.
Epidemics and Privacy
| Dr. Rajib Dasgupta, Assistant Professor, Center of Social Medicine and Community Heath at Jawaharlal Nehru University, examined conflicts of issues of privacy, confidentiality and the role of the state in the context of epidemics and the provisions within the Epidemic Diseases Act. Epidemics are population-level events in contrast to illnesses that only involve individuals; therein lies the uniqueness of the intersection between medical privacy and public health ethics. The state has unique responsibilities to detect, diagnose, manage and control epidemics. This has local/regional and international ramifications. Also linked to these are limits to the powers, rights of individuals and the extent to which such rights may need to be suspended. |
 |
|---|
The exercise of actions within the Act is not necessarily bereft of infringement of privacy and overt discrimination. Certain diseases, as indeed limitations imposed by the state, have elements of stigma that further confound the fuzziness of this debate.
When an epidemic occurs, the need for privacy in the mind of the individual goes down, as they are concerned solely with receiving treatment. He also pointed out that there are contradictory elements during epidemics. For instance an area might not want to be named as having an outbreak of a disease, but at the same time individuals will line up outside hospitals for treatment, exposing the fact that they have the disease. He also spoke about how steps taken to address epidemics can invade privacy. For example, during the SARS outbreak, it was the practice to put the patient in an infectious disease hospital. This was invasive to personal privacy as it created stigma and discrimination. Closing his presentation he explained how the conventional notions of privacy do not necessary hold in the case of epidemics because it is an emergency outbreak. Thus, protocol is established on a case-to-case basis. Despite this he believes that it is possible and valuable to protect privacy in cases of epidemics.
HIV/ AIDS and Privacy
 |
KK Abraham, President of Indian Network for People Living with HIV/AIDS, described how privacy could be understood as a luxury, in some cases it can be understood as a right, and in other cases it is understood of responsibility. Regarding HIV patients, Mr. Abraham emphasized the need for privacy to be understood as a right. Mr. Abraham also pointed out that as trends are changing in India, and more services are becoming available, that this is the right time to talk about privacy. Closing his presentation Mr. Abraham called for a greater understanding of patients' privacy needs and the negative effect of stigma. |
|---|
HIPPA with reference to Applicability to Patient Privacy and Clinical Data Confidentiality in India
| Dr. Lavanian Dorairaj, MD, CEO at HCIT Consultants, described how IT is a powerful tool for health care, despite the fact that health care has been hesitant to use IT. He explained that IT can help reduce errors in health care; it can help increase accessibility of patient data, improve diagnosis, treatment, and prognosis. Healthcare IT has great advantages but needs to be handled with great responsibility. He also pointed out that IT can lead to privacy violations if inappropriate access to patient records takes place. He argued that though India has recognized the need for privacy, it still needs to find a way to implement privacy protections and police the implementation of the guidelines. Drawing on examples from HIPPA, he argued that India would benefit from establishing privacy standards and security standards for health information. He explained further that HIPPA is a flexible rule, which obligates relevant entities to comply. The Rule is designed to be flexible. Entities regulated by the rules are obligated to comply. |
 |
|---|
 |  |
|---|

 |  |
|---|


Presentations
Click to download the presentation files. [Zip files, 2184 Kb]
Analysing Latest List of Blocked Sites (Communalism & Rioting Edition)
Note: This post will be updated as more analysis is done. Last update: 23:59 on August 22, 2012. This is being shared under a Creative Commons Attribution-NonCommercial licence.
How many items have been blocked?
There are a total of 309 specific items (those being URLs, Twitter accounts, img tags, blog posts, blogs, and a handful of websites) that have been blocked. This number is meaningless at one level, given that it doesn't differentiate between the blocking of an entire website (with dozens or hundreds of web pages) from the blocking of a single webpage. However, given that very few websites have been blocked at the domain-level, that number is still reasonably useful.
Please also note, we currently only have information related to what telecom companies and Internet Service Providers (ISPs) were asked to block till August 21, 2012. We do not have information on what individual web services have been asked to remove. That might take the total count much higher.
Why have these been blocked?
As far as I could determine, all of the blocked items have content (mostly videos and images have been targeted, but also some writings) that are related to communal issues and rioting. (Please note: I am not calling the content itself "communal" or "incitement to rioting", just that the content relates to communal issues and rioting.) This has been done in the context of the recent riots in Assam, Mumbai, UP, and the mass movement of people from Bangalore.
There were reports of parody Twitter accounts having been blocked. Preliminary analysis on the basis of available data show that parody Twitter accounts and satire sites have not been targetted solely for being satirical. For instance, very popular parody Twitter accounts, such as @DrYumYumSingh are not on any of the four orders circulated by the Department of Telecom. (I have no information on whether such parody accounts are being taken up directly with Twitter or not: just that they aren't being blocked at the ISP-level. Media reports indicate six accounts have been taken up with Twitter for being similar to the Prime Minister's Office's account.)
Are the blocks legitimate?
The goodness of the government's intentions seem, quite clearly in my estimation, to be unquestionable. Yet, even with the best intentions, there might be procedural illegalities and over-censorship.
There are circumstances in which freedom of speech and expression may legitimately be limited. The circumstances that existed in Bangalore could justifiably result in legitimate limitations on freedom of speech. For instance, I believe that temporary curbs — such as temporarily limiting SMSes & MMSes to a maximum of five each fifteen minutes for a period of two days — would have been helpful.
However it is unclear whether the government has exercised its powers responsibly in this circumstance. The blocking of many of the items on that list are legally questionable and morally indefensible, even while a some of the items ought, in my estimation, to be removed.
If the government has blocked these sites under s.69A of the Information Technology Act ("Power to Issue Directions for Blocking for Public Access of Any Information through any Computer Resource"), the persons and intermediaries hosting the content should have been notified provided 48 hours to respond (under Rule 8 of the Information Technology (Procedure and Safeguards for Blocking for Access of Information by Public) Rules 2009). Even if the emergency provision (Rule 9) was used, the block issued on August 18, 2012, should have been introduced before the "Committee for Examination of Request" by August 20, 2012 (i.e., within 48 hours), and that committee should have notified the persons and intermediaries hosting the content.
Importantly, even though many of the items on that list are repugnant and do deserve (in my opinion) to be removed, ordering ISPs to block them is largely ineffectual. The people and companies hosting the material should have been asked to remove it, instead of ordering Internet service providers (ISPs) to block them. All larger sites have clear content removal policies, and encouraging communal tensions and hate speech generally wouldn't be tolerated. That this can be done without resort to the dreadful Intermediary Guidelines Rules (which were passed last year) shows that those Rules are unnecessary. It is our belief that those Rules are also unconstitutional.
Are there any egregious mistakes?
Yes, there are numerous such examples of egregious mistakes.
- Most importantly, some even people and posts debunking rumours have been blocked.
- Some of the Twitter accounts are of prominent people who write for the mainstream media, and who have written similar content offline. If their online content is being complained about, their offline content should be complained about too.
- Quite a number of the links include articles published and reports broadcast in the mainstream media (including a Times Now report, a Telegraph picture gallery, etc.), and in print, making the blocks suspect. Only the online content seems to have been targeted for censorship.
There are numerous mistakes and inconsistencies that make blocking pointless and ineffectual.
- Some of the items are not even web addresses (e.g., a few HTML img tags were included).
- Some of the items they have tried to block do not even exist (e.g., one of the Wikipedia URLs).
- An entire domain was blocked on Sunday, and a single post on that domain was blocked on Monday.
- For some Facebook pages, the secure version (https://facebook.com/...) is listed, for others the non-secure version (http://facebook.com/...) is listed.
- For some YouTube videos, the 'base' URL of YouTube videos is blocked, but for other the URL with various parameters (like the "&related=" parameter) is blocked. That means that even nominally 'blocked' videos will be freely accessible.
All in all, it is clear that the list was not compiled with sufficient care.
Despite a clear warning by the DIT that "above URLs only" should be blocked, and not "the main websites like www.facebook.com, www.youtube.com, www.twitter.com, etc.", it has been seen that some ISPs (like Airtel) have gone overboard in their blocking.
Why haven't you put up the whole list?
Given the sensitivity of the issue, we felt it would be premature to share the whole list. However, we strongly believe that transparency should be an integral part of all censorship. Hence, this analysis is an attempt to provide some much-needed transparency. We intend to make the entire list public soon, though. (Given how porous such information is, it is likely that someone else will procure the list, and release it sooner than us.)
Why can I still access many items that are supposed to be blocked?
One must keep in mind that fresh orders have been issued on a day-by-day basis, that there are numerous mistakes in the list making it difficult to apply (some of these mistakes have been mentioned above), and the fact that that this order has to be implemented by hundreds of ISPs.
Your ISP probably has not have got around to enforcing the blocks yet. At the time of this writing, most ISPs don't seem to be blocking yet. This analysis is based on the orders sent around to ISPs, and not on the basis of actual testing of how many of these have actually been blocked by Airtel, BSNL, Tata, etc.
Additionally, if you are using Twitter through a client (on your desktop, mobile, etc.) instead of the web interface, you will not notice any of the Twitter-related blocks.
So you are fine with censorship?
No. I believe that in some cases, the government has the legal authority to censor. Yet, exercising that legal authority is usually not productive, and in fact there are other, better ways of limiting the harms caused by speech and information than censorship. Limiting speech might even prove harmful in situations like these, if it ends up restricting people's ability to debunk false rumours. In a separate blog post (to be put up soon), I am examining how all of the government's responses have been flawed both legally and from the perspective of achieving the desired end.
So what should the government have done?
Given that the majority of the information it is targeting is on Facebook, Youtube, and Twitter, the government could have chosen to fight alongside those services to get content removed expeditiously, rather than fight against them. (There are some indications that the government might be working with these services, but it certainly isn't doing enough.)
For instance, it could have asked all of them to expedite their complaints mechanism for a few days, by ensuring that the complaints mechanism is run 24x7 and that they respond quickly to any complaint submitted about communal incitement, spreading of panic, etc. This does not need the passing of an order under any law, but requires good public relations skills and a desire not to treat internet services as enemies. The government could have encouraged regular users to flag false rumours and hate speech on these sites. On such occasions, social networking sites should step up and provide all lawful assistance that the government may require. They should also be more communicative in terms of the help they are providing to the government to curtail panic-inducing rumours and hate speech. (Such measures should largely be reactive, not proactive, to ensure legitimate speech doesn't get curtailed.)
The best antidote for the rumours that spread far and wide and caused a mass movement of people from Bangalore to the North-Eastern states would have been clear debunking of those rumours. Mass outreach to people in the North-East (very often the worried parents) and in Bangalore using SMSes and social media, debunking the very specific allegations and rumours that were floating around, would have been welcome. However, almost no government officials actually used social media platforms to reach out to people to debunk false information and reassure them. Even a Canadian interning in our organization got a reassuring SMS from the Canadian government.
It is indeed a pity that the government notified a social media engagement policy today, when the need for it was so very apparent all of the past week.
And what of all this talk of cybersecurity failure and cyber-wars?
Cybersecurity is indeed a cause of concern for India, but only charlatans and the ignorant would make any connection between India's cybersecurity and recent events. The role of Pakistan deserves a few words. Not many Pakistani websites / webpages have been blocked by the Indian government. Two of the Pakistani webpages that have been blocked are actually pages that debunk the fake images that have been doing the rounds in Pakistan for at least the past month. Even Indian websites like Kafila have noted these fake images long ago, and Ayesha Siddiqa wrote about this on August 5, 2012, and Yousuf Saeed wrote about it on August 13, 2012. Even while material that may have been uploaded from Pakistan, it seems highly unlikely they were targeted at an Indian audience, rather than a Pakistani or global one.
| Domain | Total Number of Entries | Tuesday, August 21, 2012 | Monday, August 20, 2012 | Sunday, August 19, 2012 | Saturday, August 18, 2012 |
|---|---|---|---|---|---|
| ABC.net.au | 1 | 1 | |||
| AlJazeera.com | 4 | 4 | |||
| AllVoices.com | 1 | 1 | |||
| WN.com | 1 | 1 | |||
| AtjehCyber.net | 1 | 1 | |||
| BDCBurma.org | 1 | 1 | |||
| Bhaskar.com | 1 | 1 | |||
| Blogspot.com | 4 | 3 | 1 | ||
| Blogspot.in | 7 | 1 | 3 | 3 | |
| Catholic.org | 1 | 1 | |||
| CentreRight.in | 2 | 2 | |||
| ColumnPK.com | 1 | 1 | |||
| Defence.pk | 4 | 2 | 1 | 1 | |
| EthioMuslimsMedia.com | 1 | 1 | |||
| Facebook.com (HTTP) | 75 | 36 | 7 | 18 | 14 |
| Facebook.com (HTTPS) | 27 | 3 | 23 | 1 | |
| Farazahmed.com | 5 | 1 | 4 | ||
| Firstpost.com | 2 | 1 | 1 | ||
| HaindavaKerelam.com | 1 | 1 | |||
| HiddenHarmonies.org | 1 | 1 | |||
| HinduJagruti.org | 2 | 1 | 1 | ||
| Hotklix.com | 1 | 1 | |||
| HumanRights-Iran.ir | 2 | 2 | |||
| Intichat.com | 1 | 1 | |||
| Irrawady.org | 1 | 1 | |||
| IslamabadTimesOnline.com | 1 | 1 | |||
| Issuu.com | 1 | 1 | |||
| JafriaNews.com | 1 | 1 | |||
| JihadWatch.org | 2 | 2 | |||
| KavkazCenter | 1 | 1 | |||
| MwmJawan.com | 1 | 1 | |||
| My.Opera.com | 1 | 1 | |||
| Njuice.com | 1 | 1 | |||
| OnIslam.net | 1 | 1 | |||
| PakAlertPress.com | 1 | 1 | |||
| Plus.Google.com | 4 | 4 | |||
| Reddit.com | 1 | 1 | |||
| Rina.in | 1 | 1 | |||
| SandeepWeb.com | 1 | 1 | |||
| SEAYouthSaySo.com | 1 | 1 | |||
| Sheikyermami.com | 1 | 1 | |||
| StormFront.org | 1 | 1 | |||
| Telegraph.co.uk | 1 | 1 | |||
| TheDailyNewsEgypt.com | 1 | 1 | |||
| TheFaultLines.com | 1 | 1 | |||
| ThePetitionSite.com | 1 | 1 | |||
| TheUnity.org | 1 | 1 | |||
| TimesofIndia.Indiatimes.com |
1 | 1 | |||
| TimesOfUmmah.com | 1 | 1 | |||
| Tribune.com.pk | 1 | 1 | |||
| Twitter.com (HTTP) | 1 | 1 | |||
| Twitter.com (HTTPS) | 11 | 1 | 10 | ||
| Twitter account | 18 | 16 | 2 | ||
| TwoCircles.net | 2 | 2 | |||
| Typepad.com | 1 | 1 | |||
| Vidiov.info | 1 | 1 | |||
| Wikipedia.org | 3 | 3 | |||
| Wordpress.com | 8 | 1 | 3 | 2 | 2 |
| YouTube.com | 85 | 18 | 39 | 14 | 14 |
| YouTu.be | 1 | 1 | |||
| Totals | 309 | 65 | 88 | 80 | 75 |
The analysis has been cross-posted/quoted in the following places:
- LiveMint (September 4, 2012)
- The Hindu (August 26, 2012)
- Wall Street Journal (August 25, 2012)
- tech 2 (August 25, 2012)
- China Post (August 25, 2012)
- The Hindu (August 24, 2012)
- LiveMint (August 24, 2012)
- Global Voices (August 24, 2012)
- Reuters (August 24, 2012)
- Outlook (August 23, 2012)
- FirstPost.India (August 23, 2012)
- IBN Live (August 23, 2012)
- News Click (August 23, 2012)
- Medianama (August 23, 2012)
- KAFILA (August 23, 2012)
- CIOL (August 23, 2012)
A Public Meeting on DNA Profiling Bill in Delhi
The use of DNA samples for forensics purposes has been increasing as law enforcement in India are relying on DNA samples as a source of evidence to solve crimes. India currently does not have a legislation specifically regulating the collection, use, and storage of DNA samples for forensics purposes. To address this gap, in 2007 a draft DNA Profiling Bill was created by the Centre for DNA Fingerprinting and Diagnostics. In February 2012 a new draft of the bill from the department of biotechnology was been leaked. The draft Bill envisions creating state level DNA databases that will feed into a national level DNA database for the purposes of solving crime.
Opening the meeting was a presentation by Dr. Anupama that focused on how DNA analysis has been used in various cases in India. Dr. Anupama emphasized the important role that DNA plays and the usefulness of the technology, but also cautioned that the police are still perfecting the use of DNA samples for forensic purposes. She promoted the passing of the DNA profiling bill with the correct safeguards. Dr. Anupama also provided insight into the current procedure for DNA analysis in India noting that consent is taken from individuals before taking DNA samples, and that ethical clearance is taken before DNA samples are taken and used for research purposes. She also noted that labs are working on improving quality insurance and emphasized the importance of chain of custody in ensuring that DNA samples are not contaminated.
Following Dr. Anupama, Jeremy Gruber spoke about the US experience with DNA databases and explained how DNA testing was initially introduced as a tool for establishing additional evidence for convicting violent felony offenders or freeing innocent individuals on a case to case basis. He explained how the technology of DNA sampling and its use in forensic cases can be both a useful tool when used justly and democratically, or can be harmful when used unjustly and undemocratically. He noted that there has been an increase in the routine use and retention of DNA by law enforcement today for purposes such as using DNA databases for familial searching purposes, and using DNA analysis to create profiles of individuals. Concerns that Jeremy Gruber raised with respect to the draft DNA Profiling Bill included the assumption in the preamble of the bill that DNA is an infallible piece of evidence, pointing out that when DNA is used for forensic purposes it is vulnerable to inaccuracies such as false matches, sample contamination, and analysis error. He also made the point that the definitions found in the bill are overly broad and work to expand the scope by defining a wide range of crimes for which individuals will be added to the DNA database for. These broad definitions essentially turn the database into an all crimes database. Other concerns with the bill included that DNA laboratories are not clearly independent of the police, and that the bill allows for the additional collection of DNA from missing persons and victims.
In her presentation, Dr. Helen Wallace described the UK experience, where the first DNA database was established in 1995. In 2000 a major expansion of the UK DNA database took place, but was controversial for a number of reasons. In 2008 the European Court of Justice ruled that the regime of retaining DNA samples in the UK was unlawful and a breach of privacy. Now the UK law requires that only a barcode with identifying information be stored. Dr. Wallace also emphasized the fact that the number of convictions resulting from DNA detections has not increased as the UK DNA database has expanded, because the number of solved crimes is driven by the number of crime scene samples. Thus, samples on a database are only useful if they relate directly to the crime scene and a possible criminal. Therefore the more profiles that are added to the database that are related to petty crimes, civil cases, victims, volunteers etc. the less efficient and accurate the database becomes. Dr. Wallace recommended that a DNA database contain only careful crime scene evidence in order to ensure samples are matched accurately. Concerns with the DNA profiling Bill emphasized by Dr. Wallace included that consent is not provided for in the bill, and court orders are not required. Furthermore, the bill does contain a removal process, and it is unclear what DNA profiling system will be used.
Responding to the presentations made by the speakers, members of the audience raised concerns over the use of DNA sampling in India for reasons beyond forensic purposes, such as requiring surrogate mothers and the children to undergo DNA tests. Other members of the audience pointed out that the bill does not address the rights of suspects and prisoners. Additionally the question of the evidentiary weight of DNA samples in court was raised, along with the concern that the broad collection of DNA samples from individuals is just another example of the growing trend by the Indian government to collect and store information about its citizens.
Transparency and Privacy
 Transparency and Privacy.pdf
—
PDF document,
541 kB (554467 bytes)
Transparency and Privacy.pdf
—
PDF document,
541 kB (554467 bytes)
The UK DNA Database and the European Court of Human Rights
 UK-DNA-database-lessons.ppt
—
Microsoft PowerPoint presentation,
1706 kB (1746944 bytes)
UK-DNA-database-lessons.ppt
—
Microsoft PowerPoint presentation,
1706 kB (1746944 bytes)
Forensic DNA Databases
 FGPI 2012 India.pptx
—
ZIP archive,
886 kB (907551 bytes)
FGPI 2012 India.pptx
—
ZIP archive,
886 kB (907551 bytes)
Privacy Perspectives on the 2012 -2013 Goa Beach Shack Policy
The lack of clarity and specificity in these requirements, the fact that these technologies are used in public spaces to collect undefined categories and amounts of information, and the fact that the technology can cut through space – and does not distinguish between private and public and primarily captures information where it is directed to, give rise to privacy concerns and raises fundamental questions about the ways in which technologies can be used to effectively increase security while still protecting the rights of individuals and the promotion of business.
An example of a blanket CCTV installation requirement from the government is seen in the 2012-2013 Goa Beach Shack Policy.[1] This blog will examine the shack policy from a privacy perspective, and how identification requirements are evolving. The blog will explore different principles by which surveillance technologies like CCTVs can be employed in order to promote effectiveness and protect the rights of individuals.
To help understand the current status of the Shack Policy and the extent of CCTV use in Goa, I spoke with a number of shack owners, cyber café owners, the Ministry of Tourism, and the Police of Goa. In this blog I do not use any direct quotes and write only from the perspective of my personal observations.
Current Status of the Shack Policy
This year, for the 2012-2013 tourist season, the Department of Tourism of Goa is implementing the Beach Shack Policy for regulating the establishment and running of temporary shacks at beaches in Goa. The policy applies only to the licensing, construction, maintenance, and demolition of temporary shacks on beaches owned by the government. The policy lays out requirements that must be submitted by applicants for obtaining a license and requirements relating to the operation of the shacks including size, security, health and safety, and noise control. Shacks, huts, hotels, etc. built on private land do not come under the scope of the policy. The shacks can only be bars and restaurants that can run from November 1st through May 31st, after which they must be taken down until the next season. The licensing of these shacks is to enable local employment opportunities in Goa. This can be seen by the requirement in the policy that Shacks are to be granted to only one member of the family who is unemployed.[2] Currently, the Ministry of Tourism has almost completed the allotment of shack spaces on all beaches in Goa. The police will assist in the enforcement of the policy, but their exact role is in the process of being clarified. Before the 2012-2013 policy, shacks were regulated by annual beach shack policies, which are not available online, but can be accessed through an RTI request to the Department of Tourism. Resistance to the policy has been seen by some because of concerns that the shacks will take away business from local private owners, will block fishing boats, will cause trash and sewage problems, and create issues for free movement of people on the beach.
Inside the policy:
Application Requirements
To apply for a license for a temporary shack, every application must be turned in by hand and must be accompanied by a residence certificate in original issued by Village Panchayat Municipality, attested copy of ration card, four copies of a recent colored passport photos with name written on the back, attested copy of birth certificate/passport copy/Pan Card and any other information that the applicant desires to furnish, and affidavit. In addition individuals must provide their name, address, telephone number, name of the shack, name of the beach stretch, nationality, experience, and any other information they wishes to provide.[3] These requirements are not excessive and have been kept to what seems minimally necessary for providing a license, though the option for individuals to provide any additional information they wish – could be used to convey meaningful information or extraneous information to the government.
Operational Requirements
The policy has a number of operational requirements for shack owners as well. For example owners must clearly display a self identifying photograph on the shack[4] and they must agree to assist the Tourism Department and Police department in stopping any crime and violation of any law along the Beach.[5]
The policy also requires that any person handling food must take a course conducted by IHMCT, GTDC, or Porvorim,[6] shacks must also be made out of eco friendly material as much as possible and the use of cement is banned,[7] and the proper disposal of trash and waste water will be the responsibility of the shack owner.[8] Furthermore, foreigners working in the shacks must have a work visa,[9] and loud music is not allowed to be played after 10:30 p.m.[10]
As noted in the introduction, each shack must install a CCTV surveillance system that provides real-time footage with an internal looping system in a non-invasive form. [11] But I got to understand that the CCTV requirement will be slowly introduced and will not be implemented this year due to resistance from shack owners. When the requirement is implemented, hopefully different aspects around the use of CCTVs will be clarified including: the retention period for the recordings, access control to the recordings, the responsibilities of the shack owner, where the camera will be set up and where it needs to be directed to, etc.
Currently in Goa there are official requirements for CCTVs to be installed in Cyber Cafes under section 144 of the CrPc. This requirement only came into effect on October 1st 2012.[12]Some private hotels, huts, and restaurants run CCTV cameras for their own security purposes. When asked if CCTVs will also become mandatory for private areas, some said this will happen, while others said it would be difficult to implement.
Enforcement
The policy uses a number of measures to ensure enforcement. For examples, successful applicants must place a security deposit of 10,000 with Director of Tourism. If any term of the policy is violated, the deposited amount will be given to the Government Treasury and the individual is required to pay another Rs. 10,000 to continue operating.[13]The placement of deck beds on the beach without authorization will also be treated as an offense under the Goa Tourist Places (protection and maintenance) Act 2001 and will be punished with a term of imprisonment minimum three months, which may extend to 3 years, and a fine which may extend to Rs. 5,000 or both. All offenses under the Act are cognizable and non-refundable. [14] If the shack is not dismantled at the end of the season, the individual will have their application rejected for the next three years.[15] Shack owners will also be penalized of they are caught discriminating against who can and cannot enter into the shack.[16]
Interestingly, though CCTV cameras can be used to ‘catch’ a number of offenses, the offenses that are penalized under the Act do not seem to require the presence of a CCTV camera. Additionally, the policy is missing penalties for the tampering and misuse of these cameras and unauthorized access to recordings.
Other practices around security and identification in Goa
In 2011 Goa also issued a new ‘C’ form that must be filled out by foreigners entering hotels.[17]
The form requires twenty six categories of information to be filled out including: permanent address, next destination to be proceeded to, contact number in hotel, purpose of visit, whether employed in India, and where the foreigner arrived from. According to hotel owners, three copies of these records are made. Two are submitted to the police and one is kept with the hotel. The records kept with the hotel are often kept for an undefined time period. In 2011 the police also enforced a new practice where every shack, hut, hotel etc. must have an all night security guard to ensure security on the beach. It was noted that registration of migrant workers is now mandatory, and that non-registered or undocumented vendors are removed from working on the beaches.
Will the 2012 – 2013 Beach Shack Policy have new implications?
In its current form, especially taking into consideration that the CCTV requirement will not be implemented immediately, the 2012 – 2013 shack policy does not seem alarming from a privacy perspective. On the general policy, though the penalties, such as the possibility of three months in prison for having too many beach chairs, seems to be over-reaching, there are a number of positive requirements in the policy such as the use of eco-friendly material, noise control, and strict procedures for disposing of trash and sewage.
The privacy perspective could change when CCTVs are implemented. The amount of data that would be generated and the ambiguity around the employment of the cameras could raise a number of privacy concerns. Yet the fact that this part of the policy will only be implemented later down the road seems indicative of both the shack owners discomfort in using the technology, and perhaps the government’s recognition that a certain level of ground work needs to be done before CCTVs are made mandatory for every shack in the state. Hopefully before the requirement is implemented, the ground work will be set up either at a national level – in the form of a national privacy legislation, or at the state level – in the form of appropriate safeguards and procedures built into the policy.
At the macro level, and when examined in the context of the growing use of CCTVs by private owners, the implementation of the UID and NPR requirements in Goa, and the introduction of the new ‘C’ form for foreigners, the CCTV requirement found in the Shack Policy seems to part of a growing trend across the country where the government seems to seek to identify all individuals and their movements/actions for unclear and undefined purposes, and looks towards identification through the collection of personal information and use of technology as a means to solve security issues.
For example, Goa is not the only city to consider mandatory installation of CCTV’s. In Delhi, the Department of Tourism issued a similar requirement in a 2012 amendment to the “existing Guidelines for Classification/Reclassification of Hotels”. According to the amendment hotels applying for approval are required to provide documentation that security features including CCTV systems are in place.[18] Similarly, in 2011 the Delhi State Industrial and Infrastructure Development Corporation began implementing a plan to install CCTVs outside of government and private liquor shops, amounting to 550 shops in total. The goal was to use the CCTV cameras to catch individuals breaking the Excise Act on camera and use the recordings during trials. According to news coverage, the cameras are required to be capable of recording images 50 meters away and all data must be stored for a period of 30 days.[19]
The ambiguity that exists around the legal use of many of these security systems and technologies, including CCTV’s was recently highlighted in Report of the Group of Experts on Privacy headed by Justice A.P Shah.[20] The report noted that the use of CCTV cameras and more broadly the use of electronic recording devices in India is an area that needs regulation and privacy safeguards. The report describes how the nine proposed national privacy principles of notice, choice and consent, collection limitation, purpose limitation, access and correction, disclosure of information, security, and openness, could be applied and will be affected by the use of these technologies.[21]
Conclusion
In India and elsewhere, the police are faced on a daily basis with the challenge of preventing and responding to all types of crime, and from this perspective – any information, clue, or lead is helpful and necessary, and the potential usefulness of CCTVs in identifying criminals and to some extent deterring crime is clear. On the other hand when CCTVs are employed without safeguards and regulations it could result in infractions of privacy and rights or could simply move the crime away from the surveilled area to an unsurveilled area.
Finding a way to ensure that police have access to the information that they need and that crime is prevented, while at the same time ensuring that the rights of individuals are not compromised, and the private sectors ability to easily do business is not limited by unrealistic security requirements, is an important discussion that governments, policy makers, and the public should be having. The answer hopefully is not found in a binary game of all or nothing, surveillance or no surveillance – but instead is found through mechanisms and principles that apply to both security and privacy such as transparency, oversight, proportionality, and necessity. For example, practices around what access the police legally have via surveillance systems, retention practices, cost of implementing surveillance, and amount of surveillance undertaken each year could be made transparent to the public to ensure that the public is informed and aware of the basic information around these systems. Furthermore, clear oversight over surveillance systems including distinction between the responsibilities and liabilities can ensure that unreasonable requirements are not placed. Lastly any surveillance that is undertaken should be necessary and proportional to the crime or threat that it is being used to prevent or detect. These principles along with the defined National Privacy Principles could help measure what amount and what type of surveillance could be the most effective, and ensure that when surveillance is employed it is done in a way that also protects the rights of individuals and the private sector.
Notes
[1].Ministry of Tourism. Goa Government. 2012-2013 Beach Shack Policy. Available at: http://bit.ly/Xk18NH. Last accessed: October 24th 2012.
[2]. Id. Section 2.
[3]. Id. Application Requirements 1-8. Pg 1&2.
[4]. Section 33.
[5].A part of the affidavit
[6].Id. Section 4.
[7]. Id. Section 17.
[8].Id. Section 28.
[9]. Id. Section 35.
[10].Id. Section 37.
[11]. Id. Section 38.
[12]. Order No. 38/10/2006. Under Section 144 of the Code of Criminal Procedure, 1973. Available at: http:// www.goaprintingpress.gov.in/downloads/1213/1213-28-SIII-OG.pdf
[13]. Beach Shack Policy 2012 - 2013, Section 16.
[14]. Id. Section 18.
[15]. Id. Section 22.
[16]. Id. Section 32.
[17]. Arrival Report of Foreigner in Hotel.”Form C” . Available at: http://bit.ly/TbUO4S
[18]. Government of India. Ministry of Tourism. Amendment in the existing Guidelines for Classification / Reclassification of Hotels. June 28th 2012. Available at: http://bit.ly/RXtgBg. Last Accessed: October 24th 2012.
[19]. Bajpaj, Ravi. CCTV shots to check drinking outside city liquor vends. The Indian Express reproduced on the website of dsidc. December 20th 2011. Available at: http://bit.ly/VHwCzd. Last accessed: October 24th 2012.
[20]. GOI. Report of the Group of Experts on Privacy. October 2012. Available at: http://bit.ly/VqzKtr. Last accessed: October 24th 2012.
[21]. Id. pg. 61-62.
Rethinking DNA Profiling in India
Elonnai Hickok's article was published in Economic & Political Weekly, Vol - XLVII No. 43, October 27, 2012
DNA evidence was first accepted by the courts in India in 1985,[1] and in 2005 the Criminal Code of Procedure was amended to allow for medical practitioners, after authorisation from a police officer who is not below the rank of sub-inspector, to examine a person arrested on the charge of committing an offence and with reasonable grounds that an examination of the individual will bring to light evidence regarding the offence. This can include
"the examination of blood, blood stains, semen, swabs in case of sexual offences, sputum and sweat, hair samples, and finger nail clippings, by the use of modern and scientific techniques including DNA profiling and such other tests which the registered medical practitioner thinks necessary in a particular case."[2]
Though this provision establishes that authorisation is needed for collection of DNA samples, defines who can collect samples, creates permitted circumstances for collection, and lists material that can be collected, among other things, it does not address how the collected DNA evidence should be handled, and what will happen to the evidence after it is collected and analysed. These gaps in the provision indicate the need for a more comprehensive legislation regulating the collection, use, analysis and storage of DNA samples, including for crime-related purposes in India.
The initiative to draft a Bill regulating the use of DNA samples for crime-related reasons began in 2003, when the Department of Biotechnology (DoB) established a committee known as the DNA Profiling Advisory Committee to make recommendations for the drafting of the DNA profiling Bill 2006, which eventually became the Human DNA Profiling Bill 2007.[3] The 2007 draft Bill was prepared by the DoB along with the Centre for DNA Fingerprinting and Diagnostics (CDFD).[4]
The CDFD is an autonomous institution supported by the DoB. In addition to the CDFD, there are multiple Central Forensic Science Laboratories in India under the control of the Ministry of Home Affairs and the Central Bureau of Investigation,[5], along with a number of private labs [6] which analyse DNA samples for crime-related purposes.
In 2007, the draft Human DNA Profiling Bill was made public, but was never introduced in Parliament. In February 2012, a new version of the Bill was leaked. If passed, the Bill will establish state-level DNA databases which will feed into a national-level DNA database, and proposes to regulate the use of DNA for the purposes of
"enhancing protection of people in the society and the administration of justice."[7]
The Bill will also establish a DNA Profiling Board responsible for 24 functions, including specifying the list of instances for human DNA profiling and the sources of collection, enumerating guidelines for storage and destruction of biological samples, and laying down standards and procedures for establishment and functioning of DNA laboratories and DNA Data Banks.[8] The lack of harmonisation and clear policy indicates that there is a need in India for standardising the collection and use of DNA samples. Although DNA evidence can be useful for solving crimes, the current 2012 draft Bill is missing critical safeguards and technical standards essential to preventing the misuse of DNA and protecting individual rights.
Concerns that have been raised with regards to the Bill are both intrinsic, including problems with effectiveness of achieving the set objectives, and extrinsic, including concerns with the fundamental principles of the Bill. For example, the use of DNA material as evidence and the subsequent creation of a DNA database can be useful for solving crimes when the database contains DNA profiles from[9] from DNA samples[10] only from crime scenes, and is restricted to DNA profiles from individuals who might be repeat offenders. If a wide range of DNA profiles are added to the database, the effectiveness of the database decreases, and the likelihood of a false match increases as the ability to correctly identify a criminal depends on the number of crime scene DNA profiles on the database, and the number of false matches that occur is proportional to the number of comparisons made (more comparisons = more false matches).[11] This inverse relationship between the effectiveness of the DNA database and the size of the database was found in the UK when it was proven that the expansion of the UK DNA database did not help to solve more crimes, despite millions of profiles being added to the database.[12]
The current scope of the draft 2012 Bill is not limited to crimes for which samples can be taken and placed in the database. Instead the Bill creates indexes within every databank including: crime scene indexes, suspects index, offender’s index, missing persons index, unknown deceased persons’ index, volunteers’ index, and such other DNA indices as may be specified by regulations made by the Board.[13] How independent each of these indices are, is unclear. For example, the Bill does not specify when a profile is searched for in the database – if all indices are searched, or if only the relevant indices are searched, and the Bill requires that when a DNA profile is added to the databank, it must be compared with all the existing profiles.[14] The Bill also lists a range of offences for which DNA profiling will be applicable and DNA samples collected, and used for the identification of the perpetrator including, unnatural offences, individual identification, issues relating to assisted reproductive technologies, adultery, outraging the modesty of women etc.[15] Though the Bill is not incorrect in its list of offences where DNA profiling could be applicable, it is unclear if DNA profiles from all the listed offenses will be stored on the database. If it is the case that the DNA profiles will be stored, it would make the scope of the database too broad.
Unlike other types of identifiers, such as fingerprints, DNA can reveal very personal information about an individual, including medical history, family history and location.[16] Thus, having a DNA database with a broad scope and adding more DNA profiles onto a database, increases the potential for misuse of information stored on the database, because there is more opportunity for profiling, tracking of individuals, and access to private data. In its current form, the Bill protects against such misuse to a certain extent by limiting the information that will be stored with a DNA profile and in the indices,[17] but the Bill does not make it clear if the DNA profiles of individuals convicted for a crime will be stored and searched independently from other profiles. Additionally, though the Bill limits the use of DNA profiles and DNA samples to identification of perpetrators,[18] it allows for DNA profiles/DNA samples and related information related to be shared for creation and maintenance of a population statistics database that is to be used, as prescribed, for the purpose of identification research, protocol development, or quality control provided that it does not contain any personally identifiable information and does not violate ethical norms.”[19]
An indication of the possibility of how a DNA database could be misused in India can be seen in the CDFD’s stated objectives, where it lists "to create DNA marker databases of different caste populations of India."[20] CDFD appears to be collecting this data by requiring caste and origin of state to be filled in on the identification form that is submitted with any DNA sample.[21] Though an argument could be made that this information could be used for research purposes, there appears to be no framework over the use of this information and this objective. Is the information stored along with the DNA sample? Is it used in criminal cases? Is it revealed during court cases or at other points of time?
Similarly, in the Report of the Working Group for the Eleventh Five Year Plan, it lists the following as a possible use of DNA profiling technology:
"Human population analysis with a view to elicit profiling of different caste populations of India to use them in forensic DNA fingerprinting and develop DNA databases."[22]
This objective is based on the assumption that caste is an immutable genetic trait and seems to ignore the fact that individuals change their caste and that caste is not uniformly passed on in marriage. Furthermore, using caste for forensic purposes and to develop DNA databases could far too easily be abused and result in the profiling of individuals, and identification errors. For example, in 2011 the UK police, in an attempt to catch the night stalker Delroy Grant, used DNA to (incorrectly) predict that he originated from the Winward Islands. The police then used mass DNA screenings of black men. The police initially eliminated Delroy Grant as a suspect because another Delroy Grant was on the DNA database, and the real Delroy Grant was eventually caught when the police pursued more traditional forms of investigation.[23]
Other uses for DNA databases and DNA samples in India have been envisioned over the years. For example, in 2010 the state of Tamil Nadu sought to amend the Prisoners Identification Act 1920 to allow for the establishment of a prisoners’ DNA database – which would require that any prisoner’s DNA be collected and stored.[24] In another example, the home page of BioAxis DNA Research Centre (P) Limited, a private DNA laboratory offering forensic services states,
"In a country like India which is densely populated there is huge requirement for these type of databases which may help in stopping different types of fraud like Ration card fraud, Voter ID Card fraud, Driving license fraud etc. The database may help the Indian police to differentiate the criminals and non criminals."[25] Not only is this statement incorrect in stating that a DNA database will differentiate between criminals and non-criminals, but DNA evidence is not useful in stopping ration card fraud etc. as it would require that DNA be extracted and authenticated for every instance of service. In 2012, the Department of Forensic Medicine and Toxicology at AFMC Pune proposed to establish a DNA data bank containing profiles of armed forces personnel.[26] And in Uttar Pradesh, the government ordered mandatory sampling for DNA fingerprinting of dead bodies.[27] These examples raise important questions about the scope of use, collection and storage of DNA profiles in databases that the Bill is silent on.
The assumption in the Bill that DNA evidence is infallible is another point of contention. The preamble of the Bill states that, "DNA analysis of body substances is a powerful technology that makes it possible to determine whether the source of origin of one body substance is identical to that of another, and further to establish the biological relationship, if any, between two individuals, living or dead with any doubt."[28]
This statement ignores the possibility of false matches, cross-contamination, and laboratory error[29] as DNA evidence is only as infallible as the humans collecting, analysing, and marshalling the evidence. These mistakes are not purely speculative, as cases that have relied on DNA as evidence in India demonstrate that the reliability of DNA evidence is questionable due to collection, analysis, and chain of custody errors. For example, in the Aarushi murder case the forensic expert who testified failed to remember which samples were collected at the scene of the crime[30] in the French diplomat rape case, the DNA report came out with both negative and positive results;[31] and in the Abhishek rape case the DNA sample had to be reanalysed after initial analysis did not prove conclusive.[32] Yet the Bill does not mandate a set of best practices that could help in minimising these errors, such as defining what profiling system will be used nationally, and defining specific security measures that must be taken by DNA laboratories – all of which are currently left to be determined by the DNA board.[33]
The assumption in the preamble that DNA can establish if a relationship exists between two individuals without a doubt is also misleading as it implies that the use of DNA samples and the creation of a database will increase the conviction rate, when in actuality the exact number of accurate convictions resulting purely from DNA evidence is unknown, as is the number of innocent people who are falsely accused of a crime based on DNA evidence in India. This misconception is reflected on the website of the Department of Biotechnology’s information page for CDFD where it states:
"…The DNA fingerprinting service, given the fact that it has been shown to bring about dramatic increase in the conviction rate, will continue to be in much demand. With the crime burden on the society increasing, more and more requests for DNA fingerprinting are naturally anticipated. For example, starting from just a few cases of DNA fingerprinting per month, CDFD is now handling similar number of cases every day."[34]
In addition to the claim that the DNA fingerprinting service has shown a dramatic increase in the conviction rate, is not supported by evidence in this article, according to the CDFD 2010-2011 annual report, the centre analysed DNA from 57 cases of deceased persons, 40 maternity/paternity cases, four rape and murder cases, eight sexual assault cases, and three kidney transplantation cases.[35] This is in comparison to the 2006 – 2007 annual report, which quoted 83 paternity/maternity dispute cases, 68 identification of deceased, 11 cases of sexual assault, eight cases of murder, and two cases of wildlife poaching.[36] From the numbers quoted in the CDFD annual report, it appears that paternity/maternity cases and identification of the deceased are the most frequent types of cases using DNA evidence.
Other concerns with the Bill include access controls to the database and rights of the individual. For example, the Bill does not require that a court order be issued for access to a DNA profile, and instead leaves it in the hand of the DNA bank manager to determine if communication of information relating to a match to a court, tribunal, law enforcement agency, or DNA laboratory is appropriate.[37]
Additionally, the Data Bank Manager is empowered to grant access to any information on the database to any person or class of persons that he/she considers appropriate for the purposes of proper operation and maintenance or for training purposes.[38] The low standards for access that are found in the Bill are worrisome as the possibility for tampering of evidence and analysis is increased.
The Bill is also missing important provisions that would be necessary to protect the rights of the individual. For example, individuals are not permitted a private cause of action for the unlawful collection, use, or retention of DNA, and individuals do not have the right to access their own information stored on the database.[39] These are significant gaps in the proposed legislation as it restricts the rights of the individual.
In conclusion, India could benefit from having a legislation regulating, standardising, and harmonising the use, collection, analysis, and retention of DNA samples for crime-related purposes. The current 2012 draft of the Bill is a step in the right direction, and an improvement from the 2007 DNA Profiling Bill. The 2012 draft draws upon best practices from the US and Canada, but could also benefit from drawing upon best practices from countries like Scotland. Safeguards missing from the current draft that would strengthen the Bill include: limiting the scope of the DNA database to include only samples from a crime scene for serious crimes and not minor offenses, requiring the destruction of DNA samples once a DNA profile is created, clearly defining when a court order is needed to collect DNA samples, defining when consent is required and is not required from the individual for a DNA sample to be taken, and ensuring that the individual has a right of appeal.
[1]. Law Commission of India. Review of the Indian Evidence Act 1872. Pg. 43 Available at: http://lawcommissionofindia.nic.in/reports/185thReport-PartII.pdf. Last accessed: October 9th 2012.
[2]. Section 53. The Criminal Code of Procedure, 1973. Available at: http://www.vakilno1.com/bareacts/crpc/s53.htm. Last accessed October 9th 2012.
[3]. Department of Biotechnology. Ministry of Science & Technology GOI. Annual Report 2009 – 2010. pg. 189. Available at: http://dbtindia.nic.in/annualreports/DBT-An-Re-2009-10.pdf. Last Accessed October 9th 2012.
[4]. Chhibber, M. Govt Crawling on DNA Profiling Bill, CBI urges it to hurry, cites China. The Indian Express. July 12 2010. Available at: http://www.indianexpress.com/news/govt-crawling-on-dna-profiling-bill-cbi-urges-it-to-hurry-cites-china/645247/0. Last accessed: October 9th 2012.
[5]. Perspective Plan for Indian Forensics. Final report 2010. Table 64.1 -64.3 pg. 264-267. Available at: http://mha.nic.in/pdfs/IFS%282010%29-FinalRpt.pdf. Last accessed: October 9th 2012. And CBI Manual. Chapter 27. Available at: http://mha.nic.in/pdfs/IFS%282010%29-FinalRpt.pdf. Last accessed: October 9th 2012.
[6]. For example: International Forensic Sciences, DNA Labs India (DLI), Truth Labs and Bio-Axis DNA Research Centre (P) Limited.
[7]. Draft Human DNA Profiling Bill 2012. Introduction.
[8]. Id. section 12(a-z)
[9]. Id. Definition l. “DNA Profile” means results of analysis of a DNA sample with respect to human identification.
[10]. Id. Definition m. “DNA sample” means biological specimen of any nature that is utilized to conduct CAN analysis, collected in such manner as specified in Part II of the Schedule.
[11]. The UK DNA database and the European Court of Human Rights: Lessons India can learn from UK mistakes. PowerPoint Presentation. Dr. Helen Wallace, Genewatch UK. September 2012.
[12]. Hope, C. Crimes solved by DNA evidence fall despite millions being added to database. The Telegraph. November 12th 2008. Available at: http://www.telegraph.co.uk/news/uknews/law-and-order/3418649/Crimes-solved-by-DNA-evidence-fall-despite-millions-being-added-to-database.html. Last accessed: October 9th 2012
[13]. Draft Human DNA Profiling Bill 2012. Section 32 (4(a-g))
[14]. Id. Section 35
[15]. Id. Schedule: List of applicable instances of Human DNA Profiling and Sources of Collection of Samples for DNA Test.
[16]. Gruber J. Forensic DNA Databases. Council for Responsible Genetics. September 2012. Powerpoint presentation.
[17]. Draft Human DNA Profiling Bill 2012. Section 32 (5)-
6)(a)-(b[+]
. Indices will only contain DNA identification records and analysis prepared by the laboratory and approved by the DNA Board, while profiles in the offenders index will contain only the identity of the person, and other profiles will contain only the case reference number.
[18]. Id. Section 39
[19]. Id. Section 40(c)
[20]. CDFD. Annual Report 2010-2011. Pg19. Available at: http://www.cdfd.org.in/images/AR_2010_11.pdf. Last accessed: October 9th 2012.
[21]. Caste and origin of state is a field of information that is required to be completed when an ‘identification form’ is sent to the CDFD along with a DNA sample for analysis. Form available at: http://www.cdfd.org.in/servicespages/dnafingerprinting.html
[22]. Report of the Working Group for the Eleventh Five Year Plan (2007 – 2012). October 2006. Pg. 152. Section: R&D Relating Services. Available at: http://planningcommission.nic.in/aboutus/committee/wrkgrp11/wg11_subdbt.pdf. Last accessed: October 9th 2012
[23]. Evans. M. Night Stalker: police blunders delayed arrest of Delroy Grant. March 24th 2011. The Telegraph. Available at: http://www.telegraph.co.uk/news/uknews/crime/8397585/Night-Stalker-police-blunders-delayed-arrest-of-Delroy-Grant.html. Last accessed: October 10th 2012.
[24]. Narayan, P. A prisoner DNA database: Tamil Nadu shows the way. May 17th 2012. Available at: http://timesofindia.indiatimes.com/india/A-prisoner-DNA-database-Tamil-Nadu-shows-the-way/iplarticleshow/5938522.cms. Last accessed: October 9th 2012.
[25]. BioAxis DNA Research Centre (P) Limited. Website Available at: http://www.dnares.in/dna-databank-database-of-india.php. Last accessed: October 10th 2012.
[26]. Times of India. AFMC to open DNA profiling centre today. February 2012. Available at:http://articles.timesofindia.indiatimes.com/2012-02-08/pune/31037108_1_dna-profile-dna-fingerprinting-data-bank. Last accessed: October 10th 2012.
[27]. Siddiqui, P. UP makes DNA sampling mandatory with postmortem. Times of India. September 4th 2012. Available at:http://articles.timesofindia.indiatimes.com/2012-09-04/lucknow/33581061_1_dead-bodies-postmortem-house-postmortem-report. Last accessed: October 10th 2012.
[28]. Draft DNA Human Profiling Bill 2012. Introduction
[29]. Council for Responsible Genetics. Overview and Concerns Regarding the Indian Draft DNA Profiling Bill. September 2012. Pg. 2. Available at: http://cis-india.org/internet-governance/indian-draft-dna-profiling-act.pdf/view. Last accessed: October 9th 2012.
[30]. DNA. Aarushi case: Expert forgets samples collected from murder spot. August 28th 2012. Available at: http://www.dnaindia.com/india/report_aarushi-case-expert-forgets-samples-collected-from-murder-spot_1733957. Last accessed: October 10th 2012.
[31]. India Today. Daughter rape case: French diplomat’s DNA test is inconclusive. July 7th 2012. Available at: http://indiatoday.intoday.in/story/french-diplomat-father-rapes-daughter-dna-test-bangalore/1/204270.html. Last accessed: October 10th 2012.
[32]. The Times of India. DNA tests indicate Abhishek raped woman. May 30th 2006. Available at: http://articles.timesofindia.indiatimes.com/2006-05-30/india/27826225_1_abhishek-kasliwal-dna-fingerprinting-dna-tests. Last accessed: October 10th 2012.
[33]. Draft Human DNA Profiling Bill 2012. Section 18-27.
[34]. Department of Biotechnology. DNA Fingerprinting & Diagnostics, Hyderabad. Available at: http://dbtindia.nic.in/uniquepage.asp?id_pk=124. Last accessed: October 10 2012.
[35]. CDFD Annual Report 2010 – 2011.Pg.19. Available at: http://www.cdfd.org.in/images/AR_2010_11.pdf. Last accessed: October 10th 2012.
[36]. CDFD Annual Report 2006-2007.Pg. 13. Available at: http://www.cdfd.org.in/images/AR_2006_07.pdf. Last accessed: October 10th 2012.
[37]. Draft Human DNA Profiling Bill 2012. Section 35
[38]. Id. Section 41.
[39].Council for Responsible Genetics. Overview and Concerns Regarding the Indian Draft DNA Profiling Bill. September 2012. Pg. 9 Available at: http://cis-india.org/internet-governance/indian-draft-dna-profiling-act.pdf/view. Last accessed: October 9th 2012.
Q&A to the Report of the Group of Experts on Privacy
Executive Summary
The executive summary explains how the need for a horizontal privacy legislation that recognizes the right to privacy has come about in India in light of projects and practices such as the UID, NATGRID, and the changing nature of business and technology. The executive summary highlights the committee’s recommendations of what should be considered by legislatures while enacting a privacy legislation in India.
Q: What are the salient features of the committee’s recommendations?
A: In its report the committee recommended that any privacy legislation passed should:
- Be technologically neutral and interoperable with international standards to ensure that the regulation can adapt to changing technology, and that business will be promoted.
- Recognize the multiple dimensions of privacy including physical and informational privacy.
- Apply to all data controllers both in the private sector and the public sector to ensure that businesses and governments are held accountable to protecting privacy.
- Establish a set of privacy principles that can be applicable to different practices, policies, projects, departments, and businesses to create a uniform level of privacy protection across all sectors.
- Create an enforcement regime of co-regulation, where industry has the choice of developing privacy principles and ensuring compliance at the sectoral level with regular oversight by the Privacy Commissioners.
Chapter 1: Constitutional Basis for Privacy
This chapter summarizes a number of decisions from the Indian Judiciary that demonstrate how the right to privacy in India has been defined on a case to case basis and has been defined as either a fundamental right or a common law right.
Q: What are the contexts of the cases covered?
A: This chapter covers cases that speak to the:
- Right to privacy in the context of surveillance by the State
- Balancing the ‘right to privacy’ against the ‘right to free speech’
- The ‘right to privacy’ of HIV patients
- Prior judicial sanctions for tapping telephones
- The ‘search and seizure’ powers of revenue authorities
Chapter 2: International Privacy Principles
This chapter summarizes recent developments in privacy laws, international privacy principles, and privacy principles developed by specific countries. This review aided the Committee in forming its recommendations for the report.
Q: Privacy principles from which countries were reviewed by the Committee?
A: The Committee reviewed privacy principles from the following countries and international organizations.
- EU Regulations of January 2012
- US Consumer Privacy Bill of Rights
- OECD Privacy Principles
- APEC Privacy Framework
- Australia
- Canada
Chapter 3: National Privacy Principles, Rationales, and Emerging Issues
This chapter lays out the nine national privacy principles and describes the rationale for each principle along with emerging issues around each principle.
Q: What could the principles apply to?
A: The principles apply to the collection, processing, storage, retention, access, disclosure, destruction, sharing, transfer, and anonymization of sensitive personal information, personal identifiable information, and identifiable information by data controllers. The national privacy principles can also be applied to legislation, projects, practices, and policies to ensure that provisions and requirements are in compliance with the national privacy principles.
Q: Who could be brought under the scope of the principles?
A: The principles are applicable to every data controller in the private sector and the public sector. For example organizations and government departments that determine the purposes and means of processing personal information will be brought under the scope of the principles and will be responsible for carrying out the processing of data in accordance with sectoral privacy standards or the national privacy principles.
Q: How could the National Privacy Principles impact individuals?
A: The principles provide individuals with the right to 1. Receive notice before giving consent stating what personal information is being collected, the purposes for which personal information is being collected, the uses of collected personal information, whether or not personal information will be disclosed to third persons, security safeguards established by the data controller, processes available to data subjects to access and correct personal information, and contact details of privacy officers. 2. Opt in and out of providing personal information 3. Withdraw given consent at any point of time. 4. Access and correct any personal information held by data controllers 5. Allow individuals to issue a complaint with the respective ombudsman, privacy commissioner, or court.
Q: Would the National Privacy Principles be binding for every data controller?
A: Yes, but Self Regulating Organizations at the industry level have the option of developing principles for that specific sector. These principles must be approved by the privacy commissioner and be in compliance with the National Privacy Principles.
Chapter 4: Analysis of Relevant Legislation, Bills, and Interests from a Privacy Perspective
This chapter examines relevant legislation, bills, and interests from a privacy perspective. In doing so the chapter clarifies how the right to privacy should intersect with the right to information and the freedom of expression, and anaylzes current and upcoming legislation to demonstrate what existing provisions in the legislation uphold the privacy principles, what existing provisions are in conflict with the principles, and what provisions are missing to ensure that the legislation is compliant to the extent possible with the principles.
Q: How does the report understand the relationship between the Right to Information and the Right to Privacy?
A: When applied the Privacy Act should not circumscribe the Right to Information Act. Furthermore, RTI recipients should not be considered data controllers and thus should not be brought under the ambit of the privacy principles.
Q: How does the report understand the relationship between the freedom of expression and privacy?
A: Questions about how to balance the right to privacy with the freedom of expression can arise in many circumstances including: the right to be forgotten and data portability, journalistic expression, state secrecy and whistle blowers, and national security. Most often, public interest is the test used to determine if the right to privacy should supersede the freedom of expression or vice versa.
Chapter 5: The Regulatory Framework
This chapter outlines the committee’s recommendations for a regulatory framework for the Privacy Act.
Q: Who are the main actors in the regulatory framework?
A: The report recommends that a regulatory framework be comprised of one privacy commissioner at the central level and four commissioners at the regional level, self regulating organizations (SRO’s) at the industry level, data controllers and privacy officers at the organization level, and courts.
Q: What are the salient features of the regulatory framework?
A: The salient features of the regulatory framework include 1. A framework of co-regulation 2. Complaints 3. Exceptions to the Privacy Act 4. Offenses under the Act
Q: What are exceptions to the right to privacy? Are these blanket exceptions?
A: National security; public order; disclosure of information in public interest; prevention, detection, investigation and prosecution of criminal offences; and protection of the individual or of the rights and freedoms of others are suggested exceptions to the right to privacy. The committee has qualified these exceptions with the statement that before an exception can be made for the following circumstances, the proportionality, legality, and necessity in a democratic state should be used to measure if the exception applies and the extent of the exception. Thus, they are not blanket exceptions to the right to privacy
Historical and scientific research and journalistic purposes were also recommended as additional exceptions to the right to privacy that may be considered. These exceptions will not be subjected to the principles of proportionality, legality, and necessary in a democratic state.
Q: What are the powers and responsibilities of the privacy commissioners?
A: The powers and responsibilities of the Privacy Commissioners are the following:
Responsibilities:
- Enforcement of the Act
- Broadly oversee interception/access, audio & video recordings, the use of personal identifiers, and the use of bodily or genetic material.
- Evaluate and approve privacy principles developed by SRO’s
- Collaborate with stakeholders to endure effective regulation, promote awareness of the Act, and sensitize citizens to privacy considerations
Powers:
- Order privacy impact assessments on organisations
- Investigate complaints suomotu or based off of complaints from data subjects (summon documents, call and examine witnesses, and take a case to court if necessary )
- Fine non-compliant data controllers
Q: How does Co-regulation work?
A: The purpose of establishing a regulatory framework of co-regulation is to ensure that appropriate policies and principles are articulated and enforced for all sectors. If a sector wishes to develop its own privacy standards, the industry level self regulating organization will submit to the privacy commissioner a sub set of self regulatory norms. If these norms are approved by the privacy commissioner the SRO will be responsible for enforcing those norms, but the privacy commissioner will have the power to sanction member data controllers for violating the norms. If a sector does not have an SRO or does not wish to develop its own set of standards, the National Privacy Principles will be binding.
Q: What are data controllers? What are privacy officers? What are ombudsmen?
A: A data controller is any entity that handles or process data. Privacy officers receive and handle complaints at the organizational level and may be appointed as part of a SRO’s privacy requirements for a sector. Ombudsmen are appointed at the SRO level and are also responsible for receiving and handling complaints. The objective of having ombudsman and privacy officers is to reduce the burden of handling complaints on the commissioner and the courts.
Q: When can an individual issue a complaint? Which body should individuals issue complaints to?
A: An individual can issue a complaint at any point of time when they feel that their personal information has not been handled by a data controller according to the principles, or that a data controller is not in compliance with the Act. When applicable complaints are encouraged to be issued first to the organization. If the complaint is not resolved, the individual can take the complaint to the SRO or privacy commissioner. The individual also has the option of taking a complaint straight to the courts. When a complaint is received by the commissioner, the commissioner may fine the data controller if it is found to be non-compliant. Data controllers cannot appeal fines issued by the commissioner, but they can appeal the initial decision of non-compliance.
Q: Can an individual receive compensation for a violation of privacy:
A: Yes. Individuals who suffer damages caused by non-compliance with the principles or any obligation under the Act can receive compensation, but the compensation must be issued by the courts and cannot be issued by a privacy commissioner. Actors that can be held liable by individuals include data controllers, organization directors, agency directors, and heads of Governmental departments.
Q: What offences does the report reccomend?
A: The following constitutes as an offence under the Act:
- Non-compliance with the privacy principles
- Unlawful collection, processing, sharing/disclosure, access, and use of personal data
- Obstruction of commissioner
- Failure to comply with notification issued by commissioner
- Processing data after receiving a notification
- Failure to appear before commissioner
- Failure to produce documents requested by commissioner
- Sending report to commissioner with false or misleading information
Chapter 6: The Multiple Dimensions of Privacy
This chapter gives examples of practices that impact privacy in India which the national privacy principles could be applied to. These include interception/access, the use of electronic recording devices, the use of personal identifiers, and the use of bodily and genetic material. The current state of each practice in India is described, and the inconsistencies and gaps in the regimes are highlighted. Each section also provides recommendations of which privacy principles need to be addressed and strengthened in each practice, and how the privacy principles would be affected by each practice.
Q: Does the report give specific recommendations as to how each practice should be amended to incorporate the National Privacy Principles?
A: No. Each section explains the current state of the practice in India, gaps and inconsistencies with the current practice, and recommends broadly what principles need to be addressed and strengthened in the regime, and how the National Privacy Principles may be affected by the practice.
Summary of Recommendations
This chapter consolidates and clarifies all of the Committee’s recommendations for a Privacy Act in India.
Q: Are the recommendations in this chapter different from chapters above?
A: No. The recommendations in this chapter reflect the recommendations made earlier. This chapter does clarify the recommended scope and objectives of the Privacy Act including:
- The Act should define and harmonize with existing laws in force.
- The Act should extend the right of privacy to all individuals in India and all data processed by any company or equipment locating in India, and all data that originated in India.
- The Act should clarify that the publication of personal data for artistic and journalistic purposes in public interest, the use of personal information for household purposes, and the disclosure of information as required by the Right to Information Act should not constitute an infringement of privacy.
- The Act should not require a ‘reasonable expectation’ of privacy to be present for the right to be evoked.
- If any other legislation provides more extensive protections than those set out by the Privacy Act, than the more extensive protections should apply.
Report of the Group of Experts on Privacy [PDF, 1270 Kb]
Report of the Group of Experts on Privacy
 Report of the Group of Experts on Privacy.pdf
—
PDF document,
1269 kB (1299685 bytes)
Report of the Group of Experts on Privacy.pdf
—
PDF document,
1269 kB (1299685 bytes)
Arbitrary Arrests for Comment on Bal Thackeray's Death
Facts of the case
This morning, there was a short report in the Mumbai Mirror about two girls having been arrested for comments one of them made, and the other 'liked', on Facebook about Bal Thackeray:
Police on Sunday arrested a 21-year-old girl for questioning the total shutdown in the city for Bal Thackeray’s funeral on her Facebook account. Another girl who ‘liked’ the comment was also arrested.
The duo were booked under Section 295 (a) of the IPC (for hurting religious sentiments) and Section 64 (a) of the Information Technology Act, 2000. Though the girl withdrew her comment and apologised, a mob of some 2,000 Shiv Sena workers attacked and ransacked her uncle’s orthopaedic clinic at Palghar.
“Her comment said people like Thackeray are born and die daily and one should not observe a bandh for that,” said PI Uttam Sonawane.
What provisions of law were used?
There's a small mistake in Mumbai Mirror's reportage as there is no section "64(a)"1 in the Information Technology (IT) Act, nor a section "295(a)" in the Indian Penal Code (IPC). They must have meant section 295A of the IPC ("outraging religious feelings of any class") and section 66A of the IT Act ("sending offensive messages through communication service, etc."). (Update: The Wall Street Journal's Shreya Shah has confirmed that the second provision was section 66A of the IT Act.)
Section 295A of the IPC is cognizable and non-bailable, and hence the police have the powers to arrest a person accused of this without a warrant.2 Section 66A of the IT Act is cognizable and bailable.
Update: Some news sources claim that section 505(2) of the IPC ("Statements creating or promoting enmity, hatred or ill-will between classes") has also been invoked.
Was the law misapplied?
This is clearly a case of misapplication of s.295A of the IPC.3 This provision has been frivolously used numerous times in Maharashtra. Even the banning of James Laine's book Shivaji: Hindu King in Islamic India happened under s.295A, and the ban was subsequently held to have been unlawful by both the Bombay High Court as well as the Supreme Court. Indeed, s.295A has not been applied in cases where it is more apparent, making this seem like a parody news report.
Interestingly, the question arises of the law under which the friend who 'liked' the Facebook status update was arrested. It would take a highly clever lawyer and a highly credulous judge to make 'liking' of a Facebook status update an act capable of being charged with electronically "sending ... any information that is grossly offensive or has menacing character" or "causing annoyance or inconvenience", or under any other provision of the IT Act (or, for that matter, the IPC).4 That 'liking' is protected speech under Article 19(1)(a) is not under question in India (unlike in the USA where that issue had to be adjudicated by a court), since unlike the wording present in the American Constitution, the Indian Constitution clearly protects the 'freedom of speech and expression', so even non-verbal expression is protection.
Role of bad law and the police
In this case the blame has to be shared between bad law (s.66A of the IT Act) and an abuse of powers by police. The police were derelict in their duty, as they failed to provide protection to the Dhada Orthopaedic Hospital, run by the uncle of the girl who made the Facebook posting. Then they added insult to injury by arresting Shaheen Dhada and the friend who 'liked' her post. This should not be written off as a harmless case of the police goofing up. Justice Katju is absolutely correct in demanding that such police officers should be punished.
Rule of law
Rule of law demands that laws are not applied in an arbitrary manner. When tens of thousands were making similar comments in print (Justice Katju's article in the Hindu, for instance), over the Internet (countless comments on Facebook, Rediff, Orkut, Twitter, etc.), and in person, how did the police single out Shaheen Dhada and her friend for arrest?5
Social Media Regulation vs. Suppression of Freedom of Speech and Expression
This should not be seen merely as "social media regulation", but as a restriction on freedom of speech and expression by both the law and the police. Section 66A makes certain kinds of speech-activities ("causing annoyance") illegal if communicated online, but legal if that same speech-activity is published in a newspaper. Finally, this is similar to the Aseem Trivedi case where the police wrongly decided to press charges and to arrest.
This distinction is important as it being a Facebook status update should not grant Shaheen Dhada any special immunity; the fact of that particular update not being punishable under s.295 or s.66A (or any other law) should.
-
Section 64 of the IT Act is about "recovery of penalty" and the ability to suspend one's digital signature if one doesn't pay up a penalty that's been imposed.↩
-
The police generally cannot, without a warrant, arrest a person accused of a bailable offence unless it is a cognizable offence. A non-bailable offence is one for which a judicial magistrate needs to grant bail, and it isn't an automatic right to be enjoyed by paying a bond-surety amount set by the police.↩
-
Section 295A of the IPC has been held not to be unconstitutional. The first case to challenge the constitutionality of section 66A of the IT Act was filed recently in front of the Madurai bench the Madras High Court.)↩
-
One can imagine an exceptional case where such an act could potentially be defamatory, but that is clearly exceptional.↩
-
This is entirely apart from the question of how the Shiv Sena singled in on Shaheen Dhada's Facebook comment.↩
This blog entry has been re-posted in the following places
DoT Blocks Domain Sites — But Reasons and Authority Unclear
These websites offer users various tools to buy and sell domain names and simplify the purchasing process. Users on India Broad Band forum and websites like Medianama reported that these domain sites were not accessible and the following message was displayed instead — "This website/URL has been blocked until further notice either pursuant to Court orders or on the Directions issued by the Department of Telecommunications".
.In Registry’s Anti-Abuse Policy
If the issue at hand is one of abusive registrations, it would fall under the .IN Domain Anti-abuse Policy adopted by the National Internet Exchange of India (NIXI) and the .in registry. This policy states that NIXI will have the right to "deny, cancel, or transfer any registration or transaction, or place any domain name(s) on registry lock, hold, or similar status" if necessary. This raises a question as to why the Department of Telecommunications (DoT) would issue directions to block these domain marketplaces instead of cancelling their registration or placing it on hold under the policies adopted by NIXI.
A second, more important question would be whether the DoT has the power to block websites or take action under NIXI’s anti-abuse policy. NIXI and the .in registry both work under the aegis of the Department of Electronics and Information Technology. In addition, the Information Technology Act, 2000 ("the IT Act") is the only legislation that provides the authority to block a website and this authority is bestowed upon the Secretary, Department of Information Technology.
Information Technology Act
Section 69-A of the IT Act authorizes the central government to issue directions/orders to block public access to any information generated, transmitted, received, stored or hosted in any computer resource i.e., block websites. Such orders can be issued if the authorized officer finds that it is necessary to do so in the India’s sovereign and national interests or in the interest of public order. These interests include defence, security of the state, friendly relations with foreign neighbours and preventing incitement to the commission of an offence.
The procedures and safeguards that are to be followed before issuing an order to block a website are detailed in the Information Technology (Procedure and Safeguards for blocking for access of information by public) Rules, 2009 ("the rules"). The rules provide that upon receiving a complaint, the concerned organization for the blocking of access to information shall examine the complaint to ensure that there is a need to take action under the reasons mentioned above. If such action is found necessary, a request if forwarded and a committee established as per the rules reviews any requests made to block access to any information. During this review, there is also provision for a notice and reply procedure. This allows for the person controlling the online publication of such information to appear before the committee and respond to the request or make any clarifications regarding the information.
The recommendations of the committee are then sent to the Secretary of the Department of Information Technology who further directs an agency of the government or the intermediary to block the relevant content/website. The rules also provide procedures for blocking access in case of an emergency and in cases where court orders directing the blocking of information have been issued.
Whereas the ideas of sovereign interest and public order are admittedly very broad, there is no clear explanation as to what actions of domain sites/marketplaces such as BuyDomain and sedo.co.uk would be considered to impinge upon either. Neither is there any information available regarding why the DoT considers this to be the case.
Breaking Down Section 66A of the IT Act
Back in February 2009 (after the IT Amendment Act, 2008 was hurriedly passed on December 22, 2008 by the Lok Sabha, and a day after by the Rajya Sabha[1] but before it was notified on October 27, 2009) I had written that s.66A is "patently in violation of Art. 19(1)(a) of the Constitution of India":
Section 66A which punishes persons for sending offensive messages is overly broad, and is patently in violation of Art. 19(1)(a) of our Constitution. The fact that some information is "grossly offensive" (s.66A(a)) or that it causes "annoyance" or "inconvenience" while being known to be false (s.66A(c)) cannot be a reason for curbing the freedom of speech unless it is directly related to decency or morality, public order, or defamation (or any of the four other grounds listed in Art. 19(2)). It must be stated here that many argue that John Stuart Mill's harm principle provides a better framework for freedom of expression than Joel Feinberg's offence principle. The latter part of s.66A(c), which talks of deception, is sufficient to combat spam and phishing, and hence the first half, talking of annoyance or inconvenience is not required. Additionally, it would be beneficial if an explanation could be added to s.66A(c) to make clear what "origin" means in that section. Because depending on the construction of that word s.66A(c) can, for instance, unintentionally prevent organisations from using proxy servers, and may prevent a person from using a sender envelope different from the "from" address in an e-mail (a feature that many e-mail providers like Gmail implement to allow people to send mails from their work account while being logged in to their personal account). Furthermore, it may also prevent remailers, tunnelling, and other forms of ensuring anonymity online. This doesn't seem to be what is intended by the legislature, but the section might end up having that effect. This should hence be clarified.
I stand by that analysis. But given that it is quite sparse, in this post I will examine s.66A in detail.
Here's what s. 66A of the IT (Amendment) Act, 2008 states:
66A. Punishment for sending offensive messages through communication service, etc.,
Any person who sends, by means of a computer resource or a communication device,—
(a) any information that is grossly offensive or has menacing character;
(b) any information which he knows to be false, but for the purpose of causing annoyance, inconvenience, danger, obstruction, insult, injury, criminal intimidation, enmity, hatred, or ill will, persistently by making use of such computer resource or a communication device,
(c) any electronic mail or electronic mail message for the purpose of causing annoyance or inconvenience or to deceive or to mislead the addressee or recipient about the origin of such messages
shall be punishable with imprisonment for a term which may extend to three years and with fine.
Explanation: For the purposes of this section, terms "electronic mail" and "electronic mail message" means a message or information created or transmitted or received on a computer, computer system, computer resource or communication device including attachments in text, images, audio, video and any other electronic record, which may be transmitted with the message.[2]
A large part of s.66A can be traced back to s.10(2) of the UK's Post Office (Amendment) Act, 1935:
If any person —
(a) sends any message by telephone which is grossly offensive or of an indecent, obscene, or menacing character; or
(b) sends any message by telephone, or any telegram, which he knows to be false, for the purpose of causing annoyance, inconvenience, or needless anxiety to any other person; or
(c) persistently makes telephone calls without reasonable cause and for any such purposes as aforesaid;
he shall be liable upon summary conviction to a fine not exceeding ten pounds, or to imprisonment for a term not exceeding one month, or to both such fine and imprisonment.
Section 66A bears a striking resemblance to the three parts of this law from 1935, with clauses (b) and (c) being merged in the Indian law into a single clause (b) of s.66A, with a whole bunch of new "purposes" added. Interestingly, the Indian Post Office Act, 1898, was never amended to add this provision.
The differences between the two are worth exploring.
Term of Punishment
The first major difference is that the maximum term of imprisonment in the 1935 Act is only one month, compared to three years in s.66A of the IT Act. It seems the Indian government decided to subject the prison term to hyper-inflation to cover for the time. If this had happened for the punishment for, say, criminal defamation, then that would have a jail term of up to 72 years! The current equivalent laws in the UK are the Communications Act, 2003 (s. 127) and the Malicious Communications Act 1988 (s.1) for both of which the penalty is up to 6 months' imprisonment or to a maximum fine of £5000 or both. What's surprising is that in the Information Technology (Amendment) Bill of 2006, the penalty for section 66A was up to 2 years, and it was changed on December 16, 2008 through an amendment moved by Mr. A. Raja (the erstwhile Minister of Communications and IT) to 3 years. Given that parts of s.66A(c) resemble nuisance, it is instructive to note the term of punishment in the Indian Penal Code (IPC) for criminal nuisance: a fine of Rs. 200 with no prison term.
"Sending" vs. "Publishing"
J. Sai Deepak, a lawyer, has made an interesting point that the IT Act uses "send" as part of its wording, and not "publish". Given that, only messages specifically directed at another would be included. While this is an interesting proposition, it cannot be accepted because: (1) even blog posts are "sent", albeit to the blog servers — s.66A doesn't say who it has to be sent to; (2) in the UK the Communications Act 2003 uses similar language and that, unlike the Malicious Communication Act 1988 which says "sends to another person", has been applied to public posts to Twitter, etc.; (3) The explanation to s.66A(c) explicitly uses the word "transmitted", which is far broader than "send", and it would be difficult to reconcile them unless "send" can encompass sending to the publishing intermediary like Twitter.
Part of the narrowing down of s.66A should definitely focus on making it applicable only to directed communication (as is the case with telephones, and with the UK's Malicious Communication Act), and not be applicable to publishing.
Section 66A(c)
Section 66A(c) was also inserted through an amendment moved by Mr. Raja on December 16, 2008, which was passed by the Lok Sabha on December 22, 2008, and a day after by the Rajya Sabha. (The version introduced in Parliament in 2006 had only 66A(a) and (b).) This was done in response to the observation by the Standing Committee on Information Technology that there was no provision for spam. Hence it is clear that this is meant as an anti-spam provision. However, the careless phrasing makes it anything but an anti-spam provision. If instead of "for the purpose of causing annoyance or inconvenience or to deceive or to mislead the addressee or recipient about the origin of such messages" it was "for the purpose of causing annoyance and inconvenience and to deceive and to mislead the addressee or recipient about the origin of such messages", it would have been slightly closer to an anti-spam provision, but even then doesn't have the two core characteristics of spam: that it be unsolicited and that it be sent in bulk. (Whether only commercial messages should be regarded as spam is an open question.) That it arise from a duplicitous origin is not a requirement of spam (and in the UK, for instance, that is only an aggravating factor for what is already a fine-able activity).
Curiously, the definitional problems do not stop there, but extend to the definitions of "electronic mail" and "electronic mail message" in the 'explanation' as well. Those are so vast that more or less anything communicated electronically is counted as an e-mail, including forms of communication that aren't aimed at particular recipients the way e-mail is.
Hence, the anti-spam provision does not cover spam, but covers everything else. This provision is certainly unconstitutional.
Section 66A(b)
Section 66A(b) has three main elements: (1) that the communication be known to be false; (2) that it be for the purpose of causing annoyance, inconvenience, danger, obstruction, insult, injury, criminal intimidation, enmity, hatred or ill will; (3) that it be communicated persistently. The main problem here is, of course, (2). "Annoyance" and "inconvenience", "insult", "ill will" and "hatred" are very different from "injury", "danger", and "criminal intimidation". That a lawmaker could feel that punishment for purposes this disparate belonged together in a single clause is quite astounding and without parallel (except in the rest of the IT Act). That's akin to having a single provision providing equal punishment for calling someone a moron ("insult") and threatening to kill someone ("criminal intimidation"). While persistent false communications for the purpose of annoying, insulting, inconveniencing, or causing ill will should not be criminalised (if need be, having it as a civil offence would more than suffice), doing so for the purpose of causing danger or criminal intimidation should. However, the question arises whether you need a separate provision in the IT Act for that. Criminal intimidation is already covered by ss. 503 and 506 of the IPC. Similarly, different kinds of causing danger are taken care of in ss.188, 268, 283, 285, 289, and other provisions. Similarly with the other "purposes" listed there, if, for instance, a provision is needed to penalise hoax bomb threats, then the provision clearly should not be mentioning words like "annoyance", and should not be made "persistent". (At any rate, s. 505(1) of the IPC suffices for hoax bomb threats, so you don't need a separate provision in the IT Act).
I would argue that in its current form this provision is unconstitutional, since there is no countervailing interest in criminalising false and persistent "insults", etc., that will allow those parts of this provision to survive the test of 'reasonableness' under Art.19(2). Furthermore, even bits that survive are largely redundant. While this unconstitutionality could be cured by better, narrower wording, even then one would need to ensure that there is no redundancy due to other provisions in other laws.
Section 66A(a)
In s.66A(a), the question immediately arises whether the information that is "grossly offensive" or "menacing" need to be addressed at someone specific and be seen as "grossly offensive" or "menacing" by that person, or be seen by a 'reasonable man' test.
Additionally, the term "grossly offensive" will have to be read in such a heightened manner as to not include merely causing offence. The one other place where this phrase is used in Indian law is in s.20(b) of the Indian Post Office Act (prohibiting the sending by post of materials of an indecent, obscene, seditious, scurrilous, threatening, or grossly offensive character). The big difference between s.20(b) of the IPO Act and s.66A of the IT Act is that the former is clearly restricted to one-to-one communication (the way the UK's Malicious Communication Act 1988 is). Reducing the scope of s.66A to direct communications would make it less prone to challenge.
Additionally, in order to ensure constitutionality, courts will have to ensure that "grossly offensive" does not simply end up meaning "offensive", and that the maximum punishment is not disproportionately high as it currently is. Even laws specifically aimed at online bullying, such as the UK's Protection from Harassment Act 1997, can have unintended effects. As George Monbiot notes, the "first three people to be prosecuted under [the Protection from Harassment Act] were all peaceful protesters".
Constitutional Arguments in Importing Laws from the UK
The plain fact is that the Indian Constitution is stronger on free speech grounds than the (unwritten) UK Constitution, and the judiciary has wide powers of judicial review of statutes (i.e., the ability of a court to strike down a law passed by Parliament as 'unconstitutional'). Judicial review of statutes does not exist in the UK (with review under its EU obligations being the exception) as they believe that Parliament is supreme, unlike India. Putting those two aspects together, a law that is valid in the UK might well be unconstitutional in India for failing to fall within the eight octagonal walls of the reasonable restrictions allowed under Art.19(2). That raises the question of how they deal with such broad wording in the UK.
Genealogy of UK Law on Sending 'Indecent', 'Menacing', 'Grossly Offensive' Messages
Quoting from the case of DPP v. Collins [2006] UKHL 40 [6]:
The genealogy of [s. 127(1) of the Communication Act] may be traced back to s.10(2)(a) of the Post Office (Amendment) Act, 1935, which made it an offence to send any message by telephone which is grossly offensive or of an indecent, obscene or menacing character. That subsection was reproduced with no change save of punctuation in s.66(a) of the Post Office Act 1953. It was again reproduced in s.78 of the Post Office Act 1969, save that "by means of a public telecommunication service" was substituted for "by telephone" and "any message" was changed to "a message or other matter". Section 78 was elaborated but substantially repeated in s.49(1)(a) of the British Telecommunications Act 1981 and was re-enacted (save for the substitution of "system" for "service") in s.43(1)(a) of the Telecommunications Act 1984. Section 43(1)(a) was in the same terms as s.127(1)(a) of the 2003 Act, save that it referred to "a public telecommunication system" and not (as in s.127(1)(a)) to a "public electronic communications network". Sections 11(1)(b) of the Post Office Act 1953 and 85(3) of the Postal Services Act 2000 made it an offence to send certain proscribed articles by post.
While the above quotation talks about s.127(1) it is equally true about s.127(2) as well. In addition to that, in 1988, the Malicious Communications Act (s.1) was passed to prohibit one-to-one harassment along similar lines.
The UK's Post Office Act was eclipsed by the Telecommunications Act in 1984, which in turn was replaced in 2003 by the Communications Act. (By contrast, we still stick on to the colonial Indian Post Office Act, 1898.) Provisions from the 1935 Post Office Act were carried forward into the Telecommunications Act (s.43 on the "improper use of public telecommunication system"), and subsequently into s.127 of the Communications Act ("improper use of public electronic communications network"). Section 127 of the Communications Act states:
127. Improper use of public electronic communications network
(1) A person is guilty of an offence if he —
(a) sends by means of a public electronic communications network a message or other matter that is grossly offensive or of an indecent, obscene or menacing character; or
(b) causes any such message or matter to be so sent.
(2) A person is guilty of an offence if, for the purpose of causing annoyance, inconvenience or needless anxiety to another, he —
(a) sends by means of a public electronic communications network, a message that he knows to be false,
(b) causes such a message to be sent; or
(c) persistently makes use of a public electronic communications network.
(3) A person guilty of an offence under this section shall be liable, on summary conviction, to imprisonment for a term not exceeding six months or to a fine not exceeding level 5 on the standard scale, or to both.
(4) Subsections (1) and (2) do not apply to anything done in the course of providing a programme service (within the meaning of the Broadcasting Act 1990 (c. 42)).
Currently in the UK there are calls for repeal of s.127. In a separate blog post I will look at how the UK courts have 'read down' the provisions of s.127 and other similar laws in order to be compliant with the European Convention on Human Rights.
Comparison between S. 66A and Other Statutes
Section 144, IPC, 1860
Power to issue order in urgent cases of nuisance or apprehended danger
- ...obstruction, annoyance or injury to any person lawfully employed, or danger to human life, health or safety, or a disturbance of the public tranquillity
Babulal Parate v. State of Maharastra and Ors. [1961 AIR SC 884] (Magistrates order under s. 144 of the Cr. PC, 1973 was in violation of Art.19(1)(a) of the Constitution).
A special thanks is due to Snehashish Ghosh for compiling the below table.
| Section | Term(s)/phrase(s) used in 66A | Term(s)/ phrase(s) used in similar sections |
|---|---|---|
| Section 66A (heading) | Punishment for sending offensive messages through communication service, etc | Section 127, CA, 2003, "Improper use of public electronic communications network" |
| Section 66A(a) | Any person who sends, by means of a computer resource or a communication device | Section 1(1), MCA 1988, "Any person who sends to another person..." |
| Section 66A(a) | Grossly offensive | Section 1(1)(a)(i), MCA 1988; Section 127(1)(a),CA, 2003; Section 10(2)(a), Post Office (Amendment) Act, 1935*; Section 43(1)(a), Telecommunications Act 1984*; Section 20, India Post Act 1898 |
| Section 66A(a) | Menacing character | Section127(1)(a),CA, 2003 |
| Section 66A(b) | Any information which he knows to be false | Section 1(1)(a)(iii), MCA 1988 "information which is false and known or believed to be false by the sender"; Section 127(2)(a), CA, 2003, "a message that he knows to be false" |
| Section 66A(b) “purpose of...” |
Causing annoyance | Section127(2), CA, 2003 |
|
Inconvenience |
Section 127 (2), CA, 2003 | |
| Danger | ||
| Insult | Section 504, IPC, 1860 | |
| Injury | Section 44 IPC, 1860, "The word 'injury' denotes any harm whatever illegally caused to any person, in body, mind, reputation or property." |
|
| Criminal intimidation | Sections 503 and 505 (2), IPC, 1860 | |
| Enmity, hatred or ill-will | Section 153A(1)(a), IPC, 1860 | |
| Persistently by making use of such computer resource or a communication device | Section 127(2)(c), CA, 2003, "persistently makes use of a public electronic communications network." | |
| Section 66A(c) |
Deceive or to mislead |
- |
Notes
MCA 1988: Malicious Communications Act (s.1)
CA: Communications Act 2003 (s.127)
*Replaced by Communications Act 2003
[1]. The Information Technology (Amendment) Bill, 2008, was one amongst the eight bills that were passed in fifteen minutes on December 16, 2008.
[2]. Inserted vide Information Technology Amendment Act, 2008.
This was re-posted in Outlook (November 28, 2012)
Fixing India’s anarchic IT Act
A file photo of Shaheen Dhada (left) and Renu Srinivas, the two girls who were arrested for their Facebook posts in Mumbai. Photo: AP
Pranesh Prakash's article was published in LiveMint on November 28, 2012.
How could the ministry of communications and information technology draft such a loosely-worded provision that’s clearly unconstitutional? How could the ministry of law allow such shoddy drafting with such disproportionate penalties to pass through? Were any senior governmental legal officers—such as the attorney general—consulted? If so, what advice did they tender, and did they consider this restriction “reasonable”? These are some of the questions that arise, and they raise issues both of substance and of process.
When the intermediary guidelines rules were passed last year, the government did not hold consultations in anything but name. Industry and non-governmental organizations (NGOs) sent in submissions warning against the rules, as can be seen from the submissions we retrieved under the Right to Information Act and posted on our website. However, almost none of our concerns, including the legality of the rules, were paid heed to.
Earlier this year, parliamentarians employed a little-used power to challenge the law passed by the government, leading communications minister Kapil Sibal to state that he would call a meeting with “all stakeholders”, and will revise the rules based on inputs. A meeting was called in August, where only select industry bodies and members of Parliament were present, and from which a promise emerged of larger public consultations. That promise hasn’t been fulfilled.
Substantively, there is much that is rotten in the IT Act and the various rules passed under it, and a few illustrations—a longer analysis of which is available on the Centre for Internet and Society (CIS) website—should suffice to indicate the extent of the malaise.
Some of the secondary legislation (rules) cannot be passed under the section of the IT Act they claim as their authority. The intermediary guidelines violate all semblance of due process by not even requiring that a person whose content is removed is told about it and given a chance to defend herself. (Any content that is complained about under those rules is required to be removed within 36 hours, with no penalties for wilful abuse of the process. We even tested this by sending frivolous complaints, which resulted in removal.)
The definition of “cyber terrorism” in section 66F(1)(B) of the IT Act includes wrongfully accessing restricted information that one believes can be used for defamation, and this is punishable by imprisonment for life. Phone-tapping requires the existence of a “public emergency” or threat to “public safety”, but thanks to the IT Act, online surveillance doesn’t. The telecom licence prohibits “bulk encryption” over 40 bits without key escrow, but these are violated by all, including the Reserve Bank of India, which requires that 128-bit encryption be used by banks. These are but a few of the myriad examples of careless drafting present in the IT Act, which lead directly to wrongful impingement of our civil and political liberties. While we agree with the minister for communications, that the mere fact of a law being misused cannot be reason for throwing it out, we believe that many provisions of the IT Act are prone to misuse because they are badly drafted, not to mention the fact that some of them display constitutional infirmities. That should be the reason they are amended, not merely misuse.
What can be done? First, the IT Act and its rules need to be fixed. Either a court-appointed amicus curiae (who would be a respected senior lawyer) or a committee with adequate representation from senior lawyers, Internet policy organizations, government and industry must be constituted to review and suggest revisions to the IT Act. The IT Act (in section 88) has a provision for such a multi-stakeholder advisory committee, but it was filled with mainly government officials and became defunct soon after it was created, more than a decade ago. This ought to be reconstituted. Importantly, businesses cannot claim to represent ordinary users, since except when it comes to regulation of things such as e-commerce and copyright, industry has little to lose when its users’ rights to privacy and freedom of expression are curbed.
Second, there must be informal processes and platforms created for continual discussions and constructive dialogue among civil society, industry and government (states and central) about Internet regulation (even apart from the IT Act). The current antagonism does not benefit anyone, and in this regard it is very heartening to see Sibal pushing for greater openness and consultation with stakeholders. As he noted on the sidelines of the Internet Governance Forum in Baku, different stakeholders must work together to craft better policies and laws for everything from cyber security to accountability of international corporations to Indian laws. In his plenary note at the forum, he stated: “Issues of public policy related to the Internet have to be dealt with by adopting a multi-stakeholder, democratic and transparent approach” which is “collaborative, consultative, inclusive and consensual”. I could not have put it better myself. Now is the time to convert those most excellent intentions into action by engaging in an open reform of our laws.
Pranesh Prakash is policy director at the Centre for Internet and Society.
Draft nonsense
Pranesh Prakash's op-ed was published in the Times of India on November 24, 2012.
Section 66A of the Information Technology Act once again finds itself in the middle of a brewing storm. It has been used in cases ranging from the Mamata Banerjee cartoon case, the Aseem Trivedi case, the Karti Chidambaram case, the Chinmayi case, to the current Bal Thackeray-Facebook comments case. In all except the Karti Chidambaram case (which is actually a case of defamation where 's. 66A' is inapplicable), it was used in conjunction with another penal provision, showing that existing laws are more than adequate for regulation of online speech. That everything from online threats wishing sexual assault (the Chinmayi case) to harmless cartoons are sought to be covered under this should give one cause for concern. Importantly, this provision is cognisable (though bailable), meaning an arrest warrant isn't required. This makes it a favourite for those wishing to harass others into not speaking.
Section 66A prohibits the sending "by means of a computer resource or a communication device" certain kinds of messages. These messages are divided into three sub-parts : (a) anything that is "grossly offensive or has menacing character";(b) information known to be false for the purposes of "causing annoyance, inconvenience, danger, obstruction, insult, injury, criminal intimidation, enmity, hatred or ill will" and is sent persistently;or (c) "for the purpose of causing annoyance or inconvenience or to deceive or to mislead the addressee or recipient about the origin of such messages". This carries with it a punishment of up to three years in jail and a fine without an upper limit. As even non-lawyers can see, these are very broadly worded, with use of 'or' everywhere instead of 'and', and the punishment is excessive. The lawyers amongst the readers will note that while some of the words used are familiar from other laws (such as the Indian Penal Code), they are never used this loosely. And all should hopefully be able to conclude that large parts of section 66A are plainly unconstitutional.
If that is so obvious, how did we end up getting this law? We copied (and badly at that) from the UK. The sad part is that the modifications that were introduced while copying are the bits that cause the most trouble. The most noteworthy of these changes are the increase in term of punishment to 3 years (in the UK it's 6 months); the late introduction (on December 16, 2008 by A Raja) of sub-section (c), meant as an anti-spam provision, but covering everything in the world except spam;and the mangling up of sub-section (b) to become a witches brew of all the evil intentions in this world.
Further, we must recognise that our Constitution is much stronger when it comes to issues like free speech than the UK's unwritten constitution, and our high courts and Supreme Court have the power to strike down laws for being unconstitutional, unlike in the UK where Parliament reigns supreme. The most the courts can do there is accommodate the European Convention on Human Rights by 'reading down' laws rather than striking them down.
Lastly, even if we do decide to engage in policy-laundering, we need to do so intelligently. The way the government messed up section 66A should serve as a fine lesson on how not to do so. While one should fault the ministry of communications and IT for messing up the IT Act so badly, it is apparent that the law ministry deserves equal blame as well for being the sleeping partner in this deplorable joint venture. For instance, wrongfully accessing a computer to remove material which one believes can be used for defamation can be considered 'cyber-terrorism'. Where have all our fine legal drafters gone? In a meeting, former SEBI chairman M Damodaran noted how bad drafters make our policies seem far dumber than they are. We wouldn't be in this soup if we had good drafters who clearly understand the fundamental rights guaranteed by our constitution.
There are a great many things flawed in this unconstitutional provision, from the disproportionality of the punishment to the non-existence of the crime. The 2008 amendment to the IT Act was one of eight laws passed in 15 minutes without any debate in the 2008 winter session of Parliament. For far too long the Indian government has spoken about "multi-stakeholder" governance of the internet at international fora (meaning that civil society and industry must be seen as equal to governments when it comes to policymaking for the governance of the internet). It is about time we implemented multi-stakeholder internet governance domestically. The way to go forward in changing this would be to set up a multi-stakeholder body (including civil society and industry) which can remedy this and other ridiculously unconstitutional provisions of our IT Act.
Transcripts from WCIT-12
This is an unedited rough transcript of the discussions/sessions at the WCIT,2012 which is live-streamed and made available by the ITU. We are hosting the live-streamed text for archival purposes:
Section 66-A, Information Technology Act, 2000: Cases
There has been numerous instances application of the Section 66-A, Information Technology Act, 2000 (“ITA”) in the lower courts. Currently, there are six High Court decisions, in which the section has been mentioned or discussed. In this blog post, I will be summarizing facts of a few cases insofar as they can be gathered from the orders of the Court and are pertinent to the application of 66-A, ITA.
Sajeesh Krishnan v. State of Kerala (Kerala High Court, Decided on June 5, 2012)
Petition before High Court for release of passport seized by investigating agency during arrest
In the case of Sajeesh Krishnan v. State of Kerala (Decided on June 5, 2012), a petition was filed before the Kerala High Court for release of passport seized at the time of arrest from the custody of the investigating agency. The Court accordingly passed an order for release of the passport of the petitioner.
The Court, while deciding the case, briefly mentioned the facts of the case which were relevant to the petition. It stated that the “gist of the accusation is that the accused pursuant to a criminal conspiracy hatched by them made attempts to extort money by black mailing a Minister of the State and for that purpose they have forged some CD as if it contained statements purported to have been made by the Minister.” The Court also noted the provisions under which the accused was charged. They are Sections 66-A(b) and 66D of the Information Technology Act, 2000 along with a host of sections under the Indian Penal Code, 1860 (120B – Criminal Conspiracy, 419 – Cheating by personation, 511- Punishment for attempting to commit offences punishable with imprisonment for life or other imprisonment, 420 – Cheating and dishonestly inducing delivery of property, 468 – Forgery for purpose of cheating, 469 – Forgery for purpose of harming and 201 – Causing disappearance of evidence of offence, or giving false information to screen offender read with 34 of Indian Penal Code, 1860)
Nikhil Chacko Sam v. State of Kerala (Kerala High Court, Decided on July 9, 2012)Order of the Kerala High Court on issuing of the summons to the petitioner
In another case, the Kerala High Court while passing an order with respect to summons issued to the accused, also mentioned the charge sheet laid by the police against the accused in its order. The accused was charged under section 66-A, ITA. The brief facts which can be extracted from the order of the Court read: “that the complainant and the accused (petitioner) were together at Chennai. It is stated that on 04.09.2009, the petitioner has transmitted photos of the de facto complainant and another person depicting them in bad light through internet and thus the petitioner has committed the offence as mentioned above.”
J.R. Gangwani and Another v. State of Haryana and Others (Punjab and Haryana High Court, Decided on October 15, 2012)
Petition for quashing of criminal proceedings under section 482 of the Criminal Procedure Code, 1973
In the Punjab and Haryana High Court, an application for quashing of criminal proceeding draws attention to a complaint which was filed under Section 66-A(c). This complaint was filed under Section 66-A(c) on the ground of sending e-mails under assumed e-mail addresses to customers of the Company which contained material which maligned the name of the Company which was to be sold as per the orders of the Company Law Board. The Complainant in the case received the e-mails which were redirected from the customers. According to the accused and the petitioner in the current hearing, the e-mail was not directed to the complainant or the company as is required under Section 66-A (c).
The High Court held that, “the petitioners are sending these messages to the purchasers of cranes from the company and those purchasers cannot be considered to be the possible buyers of the company. Sending of such e-mails, therefore, is not promoting the sale of the company which is the purpose of the advertisement given in the Economic Times. Such advertisements are, therefore, for the purpose of causing annoyance or inconvenience to the company or to deceive or mislead the addressee about the origin of such messages. These facts, therefore, clearly bring the acts of the petitioners within the purview of section 66A(c) of the Act.”
Mohammad Amjad v. Sharad Sagar Singh and Ors. (Criminal Revision no. 72/2011 filed before the Court of Sh. Vinay Kumar Khana Additional Sessions Judge – 04 South East: Saket Courts Delhi)Revision petition against the order of the metropolitan magistrate
In a revision petition came up before the Additional Sessions Judge on the grounds that the metropolitan magistrate has dismissed a criminal complaint under Section 156(3) of the Criminal Procedure Code without discussing the ingredients of section 295-A, IPC and 66-A, IT Act.
In this case, the judge observed that, “...section 66A of Information Technology Act (IT Act) does not refer at all to any 'group' or 'class' of people. The only requirement of Section 66A IT Act is that the message which is communicated is grossly offensive in nature or has menacing character.” He also observed that the previous order “not at all considered the allegations from this angle and the applicability of Section 66A Information Technology Act, 2000 to the factual matrix of the instant case.”
Comments on the Proposed Rule 138A of the Central Motor Vehicle Rules, 1989 Concerning Radio Frequency Identification Tags
I Preliminary
1.1 These initial comments are made with regard to Notification GSR 738(E), published in the Gazette of India, Extraordinary, Part II, Section 3, Sub-section (i), on 3 October 2012
(“Impugned Notification”).
1.2 The Impugned Notification proposes to insert a new rule 138A in the Central Motor Vehicle Rules, 1989 (“CMV Rules”) to make mandatory the installation of radio frequency identification (“RFID”) tags on all light and heavy motor vehicles to enable their instant identification and monitoring by electronic toll collection booths, the police and any other authority or person that is able to query and read RFID tags.
II Validity of the Impugned Notification
(a) The Scope and Limits of the Executive Power of the Union
2.1 The competence of the Central Government to govern by executive action (such as the Impugned Notification) is restricted to the extent of the executive power of the Union.[1] Following the Ram Jawaya Kapur case,[2] it is settled that the extent of the Union’s executive power is coterminous with the legislative power of Parliament even in the absence of controlling legislation in that field.[3] This is in addition to the Union’s subordinate executive power to give effect to legislation through statutory delegation[4] and its directory executive power to give directions to the States.[5] Thus, there are three kinds of executive power exercisable by the Union:
(a) the regular power, exercisable in the absence of controlling legislation, if the subject of executive action is a matter upon which Parliament is competent to legislate;
(b) the subordinate power, exercisable under the terms of a controlling statute, if that statute specifically delegates such a power to the Union; and
(c) the directory power, exercisable within judicial limits, to secure the compliance of the States with the laws of the Union.
2.2 The regular executive power of the Union cannot be exercised over a matter that is controlled by parliamentary legislation.[6] This principle is akin to, but does not correspond exactly with, the doctrine of occupied field which is primarily concerned with the legislative entries contained in Schedule VII of the Constitution of India. Nevertheless, it is settled that since the power of the executive to act is subject to the control of the legislature, a statutory regime, where it exists, cannot be circumvented by the free exercise of executive power.[7] In the case of the Impugned Notification, the Motor Vehicles Act, 1988 constitutes a statutory regime that occupies the field to preclude regular executive action by the Central Government with regard to RFID tags in motor vehicles. The Impugned Notification should next be examined only in light of the scope and limits of the Union’s subordinate executive power since, as the Impugned Notification is not a direction to the States, the Union’s directory executive power is not in issue.
(b) Extent of the Central Government’s Rule-Making Power
2.3 The subordinate executive power of the Union emanates from section 110 of the Motor Vehicles Act, 1988 (“MV Act”) that confers the Central Government with the power to make rules to implement the statute. At this point it is important to note that the legislative competence of the MV Act is traceable to Entry 35 of List III, Schedule VII of the Constitution of India. Entry 35 concerns:
Mechanically propelled vehicles including the principles on which taxes on such vehicles are to be levied.
Entry 35 being a concurrent subject, it is open to both the Union and the States to act to regulate motor vehicles.[8] Accordingly, the MV Act also vests the States with subordinate executive power through sections 28, 38, 65, 95, 96, 107, 111, 138 and 176 which confer State Governments with the power to make rules to implement the statute in, and amend its application to, their particular states. As for the Union, so for the States is the regular executive power precluded by the existence of a statutory regime.[9]
2.4 Section 110 of the MV Act states:
110. Power of the Central Government to make rules. – (1) The Central Government may make rules regulating the construction, equipment and maintenance of motor vehicles and trailers with respect to all or any of the following matters, namely:-
(a) the width, height, length and overhand of vehicles and of the loads carried;
(b) the size, nature, maximum retail price and condition of tyres, including embossing thereon of date and year of manufacture, and the maximum load carrying capacity;
(c) brakes and steering gear;
(d) the use of safety glasses including prohibition of the use of tinted safety glasses;
(e) signalling appliances, lamps and reflectors;
(f) speed governors;
(g) the emission of smoke, visible vapour, sparks, ashes, grit or oil;
(h) the reduction of noise emitted by or caused by vehicles;
(i) the embossment of chassis number and engine number and the date of manufacture;
(j) safety belts, handle bars of motor cycles, auto-dippers and other equipments essential for safety of drivers, passengers and other road-user;
(k) standards of the components used in the vehicle as inbuilt safety devices;
(l) provision for transportation of goods of dangerous or hazardous nature to human life;
(m) standards for emission of air pollutants;
(n) installation of catalytic convertors in the class of vehicles to be prescribed;
(o) the placement of audio-visual or radio or tape recorder type of devices in public vehicles;
(p) warranty after sale of vehicle and norms therefor:
Provided that any rules relating to the matters dealing with the protection of environment, so far as may be, shall be made after consultation with the Ministry of the Government of India dealing with environment.
(2) Rules may be made under sub-section (1) governing the matters mentioned therein, including the manner of ensuring the compliance with such matters and the maintenance of motor vehicles in respect of such matters, either generally in respect of motor vehicles or trailers or in respect of motor vehicles or trailers of a particular class or in particular circumstances.
(3) Notwithstanding anything contained in this section,-
(a) the Central Government may exempt any class of motor vehicles from the provisions of this Chapter;
(b) a State Government may exempt any motor vehicle or any class or description of motor vehicles from the rules made under sub-section (1) subject to such conditions as may be prescribed by the Central Government.
2.5 The subordinate executive power of the Union, i.e. the rule-making power, is restricted to the exact extent of the delegation.[10] This is a well settled and undisputed principle of administrative law. Therefore, the Central Government cannot, in exercise of the rule-making power granted under section 110 of the MV Act, frame rules for matters for which it has not been specifically empowered under that section. Section 110 of the MV Act does not grant the Central Government the power to make rules for mandating RFID tags on vehicles. Clauses (a) to (p) of section 110(1) descriptively list the matters relating to the construction, equipment and maintenance of motor vehicles that the Central Government is competent to regulate by exercising its executive power. This list is exactingly drafted; the absence of general words or a miscellaneous empowerment obviates the need for examining any particular word or words in clauses (a) to (p) in light of the principle of ejusdem generis.
2.6 In the absence of a specific empowerment, or even a general empowerment that may be positively construed ejusdem generis, only two clauses of section 110(1) require further examination. These are:
(e) signalling appliances, lamps and reflectors; and,
(o) the placement of audio-visual or radio or tape recorder type of devices in public vehicles;
Clause (e), which deals with signalling appliances, cannot be read to include RFID tags since, in accordance with the principle of noscitur a sociis, the meaning of the words “signalling appliances” is derived from its association with the words “lamps and reflectors.”[11] Therefore, RFID tags, which are totally unrelated to lamps, reflectors and related signalling appliances, are not the subject of clause (e). On the other hand, while clause (o) contains an executive empowerment in respect of radio devices, the empowerment only concerns “public vehicles”; and, hence, the installation of RFID tags in non-public vehicles including light vehicles, such as cars, and heavy vehicles, such trucks and lorries, cannot be carried out under this clause. In any event, the word “radio” must be interpreted noscitur a sociis in light of its association with the words “audio-visual” and “tape recorder” to yield an executive empowerment in respect of in-vehicle entertainment devices only.
2.7 Therefore, in the absence of an empowerment under section 110 of the MV Act in respect of RFID tags, the Impugned Notification of the Central Government is ultra vires the MV Act. Rules that are ultra vires the parent statute for exceeding the limits of subordinate executive power are void.[12] The Impugned Notification is both ultra vires its parent statute and void. In this regard, it is instructive to note that it is settled that void rules neither acquire validity by a subsequent conferment of statutory power nor by their publication in the Official Gazette.[13]
III Constitutional Implications regarding Privacy
3.1 Across the world, RFID technology has been challenged on the basis of its intrusion into personal privacy. RFID tags operate on a pre-determined radio frequency; and, unless the tags are programmed to rapidly, constantly and randomly switch frequencies or are able to jam unauthorised queries – an extremely expensive proposition, RFID signals can be easily intercepted. The interception a vehicle’s RFID signals, whether by public authorities or by private persons, can yield detailed locational information of the driver of the vehicle. This is an unwarranted intrusion into the locational privacy of individuals.
3.2 Locational privacy is an intrinsic part of the right to privacy. An intrusion into this right, such as in the form of mandatory RFID tags on vehicles, will reveal information as to inter alia a person’s whereabouts and daily routine as well as addresses of friends’ houses, visits to the hospital, visits to a place of worship, restaurant preferences, addresses of children’s schools and so on. This will affect ordinary citizens, politicians and civil servants equally. All this information will be at the hands of the police. To place the power of tracking and monitoring ordinary individuals with the police, when such technology is not even available with intelligence agencies, would be an act of recklessness. This is compounded by the total lack of safeguards accompanying the attempted imposition of RFID technology.
3.3 Following the Kharak Singh[14] and Gobind[15] cases, the locational privacy of individuals, specifically in relation to their privacy from the police, is constitutionally protected.[16] It is now accepted that privacy is an essential ingredient of personal liberty forming a part of the right recognised under Article 21 of the Constitution. It is further settled that the personal liberty of an individual cannot be taken away except by a law that establishes a procedure that is fair, just and reasonable that withstands the tests of Article 14 and Article 19 of the Constitution.[17]The Impugned Notification, while constituting a “law” under Article 13 of the Constitution, does not create a fair, just and reasonable procedure to deprive individuals of their personal liberty and therefore fails the tests imposed by Maneka Gandhi. Therefore, the Impugned Notification, even if it were not void for want of competence, would be ultra vires the Constitution for violating Article 21.[18]
IV Summary
4.1 In sum:
(a) Section 110 of the MV Act does not bestow on the Central Government a specific empowerment to make rules in respect of RFID tags;
(b) The Impugned Notification exceeds the delegated limits of the Central Government’s subordinate executive power;
(c) The Impugned Notification is ultra vires the MV Act, its parent statute;
(d) Rules that are ultra vires the parent statute for exceeding the limits of subordinate executive power are void;
(e) The Impugned Notification is void;
(f) The imposition of mandatory RFID tags on vehicles will yield locational information to seriously invade the right to privacy;
(g) The right to privacy is an essential ingredient of personal liberty and is constitutionally protected;
(h) The Impugned Notification violates the right to privacy without creating a fair, just and reasonable procedure to deprive persons of their personal liberty;
(i) The Impugned Notification is ultra vires the Constitution for violating Article 21;
(j) Any rule that mandates RFID tags on vehicles to violate the right to privacy is void ab initio.
[1]. Article 73 of the Constitution of India.
[2]. Ram Jawaya Kapur AIR 1955 SC 549.
[3]. Ibid at prs. 12-14.
[4]. See generally, In re Delhi Laws Act AIR 1951 SC 332, Harishankar Bagla AIR 1954 SC 465, Rajnarain Singh AIR 1954 SC 569 and Edward Mills AIR 1955 SC 25.
[5]. See Articles 256 and 257 of the Constitution and State of Rajasthan (1977) 3 SCC 592.
[6]. Bishamber Dayal (1982) 1 SCC 39 at pr. 20.
[7]. Bharat Coking Coal (1990) 4 SCC 557 at prs. 15-17.
[8].Article 253 of the Constitution.
[9]. Article 162 of the Constitution.
[10]. See In re Delhi Laws Act AIR 1951 SC 332, State of Bihar (2000) 4 SCC 640, Shri Sitaram Sugar (1990) 3 SCC 223 [all Constitution Benches], Ramakrishnan Kulwant Rai 1989 Supp (1) SCC 541, K. M. Charia Abdullah (1965) 1 SCR 601, Charanjit Gill (2000) 5 SCC 742, ADM (Rev.) Delhi Administration (2000) 5 SCC 451 and State of Karnataka (1983) 2 SCC 402.
[11]. For foundational Indian case law on the principle of noscitur a sociis, see generally, M. K. Ranganathan AIR 1955 SC 604, Hospital Mazdoor Sabha AIR 1960 SC 110 and Corporation of the City of Nagpur AIR 1960 SC 675.
[12]. See Supreme Court Welfare Association (1989) 4 SCC 187 and State of Karnataka (1983) 2 SCC 402.
[35]. General Officer Commanding-in-Chief (1988) 2 SCC 351 at prs. 12-14.
[14]. Kharak Singh AIR 1963 SC 1295. The majority, speaking through Ayyangar, J., found that ‘domiciliary visits’ conducted by the police in exercise of powers granted under police regulations violated Article 21 of the Constitution; and, the minority speaking through Subba Rao, J., found that both secret police picketing (as to the location of individuals) and domiciliary visits violated both Article 21 and Article 19(1)(d) of the Constitution.
[15]. Gobind (1975) 2 SCC 148.
[16]. For a jurisprudential development of the right to privacy in India, see generally Kharak Singh AIR 1963 SC 1295, R. M. Malkani (1973) 1 SCC 471, Gobind (1975) 2 SCC 148, R. Rajagopal (1994) 6 SCC 632, People’s Union for Civil Liberties (1997) 1 SCC 301, Mr ‘X’ (1998) 8 SCC 296, Canara Bank (2005) 1 SCC 496, Bharat Shah (2008) 13 SCC 5, Naz Foundation (2009) 160 DLT 277, Selvi (2010) 7 SCC 263 and Ram Jethmalani (2011) 8 SCC 1.
[17]. Maneka Gandhi (1978) 1 SCC 248 at prs. 4-14 (per Bhagwati, Untwalia and Fazal Ali, JJ.), 48-49 (per Chandrachud, J.), 62-78 and 79-91 (per Krishna Iyer, J.) and 192-199, 201, 203 and 211-215 (per Beg, CJI.)
[18]. In this regard, see also Supreme Court Welfare Association (1989) 4 SCC 187 and N. Bakshi 1962 Supp (1) SCR 505 for the proposition that rules violating the Constitution are void ab initio.
Online Censorship: How Government should Approach Regulation of Speech
Sunil Abraham's article was published in the Economic Times on December 2, 2012.
Of course, we must get the basics right — bad law has to be amended, read down by courts or repealed, and bad implementation of law should be addressed via reform and capacity building for the police. But most importantly those in power must understand how to approach the regulation of speech.
To begin with, speech is regulated across the world. Even in the US — contrary to popular impression in India — speech is regulated both online and offline.
However, law is not the basis of most of this regulation. Speech is largely regulated by social norms. Different corners of our online and offline society have quite complex forms of self-regulation.
The harm caused by speech is often proportionate to the power of the person speaking — it maybe unacceptable for a politician or a filmstar to make an inflammatory remark but that very same utterance from an ordinary citizen may be totally fine.
To complicate matters, the very same speech by the very same person could be harmful or harmless based on context. A newspaper editor may share obscene jokes with friends in a bar, but may not take similar liberties in an editorial.
The legal scholar Alan Dershowitz tells us, "The best answer to bad speech is good speech." More recently the quote has been amended, with "more speech" replacing "good speech".
Censorship by the state has to be reserved for the rarest of rare circumstances. This is because censorship usually results in unintended consequences.
The "Streisand Effect", named after the singer-actor Barbra Streisand, is one of these consequences wherein attempts to hide or censor information only result in wider circulation and greater publicity.
The Maharashtra police's attempt to censor the voices of two women has resulted in their speech being broadcast across the nation on social and mainstream media. If the state had instead focused on producing good speech and more speech, nobody would have even heard of these women.
Circumventing Censorship
Peer-to-peer technologies on the internet mimic the topology of human networks and can also precipitate unintended consequences when subject to regulation. John Gilmore, a respected free software developer, puts it succinctly: "The Net interprets censorship as damage and routes around it."
Most of the internet censorship in the US is due to IPR-enforcement activities. This is why Christopher Soghoian, a leading privacy activist, attributes the massive adoption of privacy-enhancing technologies such as proxies and VPNs (virtual private networks) by American consumers to the crackdown on online piracy.
In India, and even when the government has had legitimate reasons to regulate speech, there have been unintended consequences.
During the exodus of people from the North-east, the five SMS per day restriction imposed by the government resulted in another exodus from SMS to alternative messaging platforms such as BlackBerry Messenger (BBM), WhatsApp and Twitter.
In both cases the circumvention of censorship by the users has resulted in a worsening situation for law-enforcement organisations — VPNs and applications like WhatsApp are much more difficult to monitor and regulate.
Mixed Memes
Regulation of speech also cannot be confused with cyber war or security. Speech can occasionally have security implications but that cannot be the basis for enlightened regulation.
A cyber war expert may be tempted to think of censored content as weapons, but unlike weapons that usually remain lethal, content that can cause harm today may become completely harmless tomorrow. This is unlike a computer virus or malware. For example, during the exodus, the online edition of ET featured the complete list of 309 URLs that were in the four block orders issued by the government to ISPs.
However, this did not result in fresh harm, demonstrating the fallacy of cyber war analogies. A cyber security expert, on the other hand, may be tempted to implement a 360° blanket surveillance to regulate speech, but as Gilmore again puts it, "If you're watching everybody, you're watching nobody."
In short, if your answer to bad speech is more censorship, more surveillance and more regulation, then as the internet meme goes, "You're Doing It Wrong".
Submission by Indian Civil Society Organisations on Proposals for the Future ITRs and Related Processes
We, the undersigned civil society organisations from India, respectfully acknowledge the important role that the ITU has played in the spread of telecommunications around the world. However, we are concerned about the lack of transparency and openness of the processes related to the WCIT: the WCIT/ITU excludes civil society, academia and other stakeholders from participation in and access to most dialogues and documents. The documents that are publicly available show that some of the proposals might deal with Internet governance. According to established principles as laid down in the Tunis Agenda - which process the ITU helped to lead - Internet governance processes are required to be multistakeholder in nature. The WCIT and ITU processes require urgent improvement with regard to openness, inclusiveness and transparency. While we appreciate the current opportunity to share our comments, we would like to encourage the ITU and its Member States to adopt a genuine multistakeholder approach at the earliest.
As mentioned, we do welcome the current opportunity to share our thoughts. Though this list is not exhaustive, some of our major concerns are as follows:
We believe that, given the historical development of present methods of internet regulation, aspects of Internet governance that have been and are presently addressed by bodies other than ITU should not be brought under the mandate of the ITU through the ITRs.
We therefore strongly recommend that the ITRs continue to be restricted to aspects of the physical layer that have traditionally been the areas of its focus. The ITRs scope should not be expanded to other layers, nor to content - any measure that impinges on these layers should be kept out of ITRs and taken up at other appropriate (multi-stakeholder) fora. In addition, it is crucial that “ICTs” and the term “processing” be excluded from the definition of telecommunication as this clearly opens up the possibility for Member States to regulate/attempt to regulate the “content/“application” layer on the internet at the ITU.
We also recommend that provisions regarding international naming, numbering, addressing and identification resources will be restricted to telephony, as should provisions regarding transit rate, originating identification and end-to-end QoS. Provisions regarding the routing of Internet traffic should not find a place in the ITRs at all.
We recognise that concerns regarding cyber security, spam, fraud, etc. are real and that some of these concerns require to be addressed at the global level. However, as these are being discussed in many other fora, we believe that the ITRs are not the best place to address these. Their inclusion here could inhibit the further evolution and expansion of the Internet. We also believe that any fora discussing cyber security should be multistakeholder, open and transparent.
We note that the proposal ARB/7/24 defines an “operating agency” as “any individual, company, corporation or governmental agency which operates a telecommunication installation intended for an international telecommunication service or capable of causing harmful interference with such a service” and believe that this definition is too broad in scope and ambit. Inclusion of such a term would broaden the mandate of the ITU to regulate numerous actors in the Internet sphere who do not fall under the infrastructure layer of the Internet. The term “operating agency” should be defined in a narrower or more restrictive manner and, irrespective of its exact definition, only be used in exceptional cases. Normally, the obligations of member states should be with respect to “recognised operating agencies” and not omnibus all “operating agencies”.
Signed:
- Centre for Internet and Society
- Delhi Science Forum
- Free Software Movement India
- Internet Democracy Project
- Knowledge Commons (India)
Statement of Civil Society Members and Groups Participating in the "Best Bits" pre-IGF meeting at Baku in 2012
We thank the Secretariat of the ITU for making the opportunity to submit our views.
Nevertheless, the process of the revision of the International Telecommunication Regulations (ITRs) has not been sufficiently inclusive and transparent, despite some recent efforts to facilitate public participation. Fundamental to the framing of public policy must be the pursuit of the public interest and fundamental human rights, and we urge Member States to uphold and protect these values.
We as civil society organizations wish to engage with the World Conference on International Telecommunication (WCIT) process in this spirit. Member States, in most cases, have not held open, broad-based, public consultations in the lead up to the WCIT, nor have they indicated such a process for the WCIT itself.
In order to address this deficiency, and at a minimum, we would urge:
- All Member States and regional groups to make their proposals available to the public in sufficient time to allow for meaningfulpublic participation;
- All delegates to support proposals to open sessions of the WCIT meeting to the public;
- The ITU Secretariat to increase transparency of the WCIT including live webcast with the video, audio, and text transcripts, as far as possible, to enable participation by all, including persons with disabilities;
- The ITU Secretariat, Member States, and regional groups to make as much documentation publicly available as possible on the ITU's website, so that civil society can provide substantive input on proposals as they are made available;
- Member States to encourage and facilitate civil society participation in their national delegations;
- The ITU to create spaces during the WCIT for civil society to express their views, as was done during the WSIS process.
Given the uncertainty about the nature of final proposals that will be presented, we urge delegates that the following criteria be applied to any proposed revisions of the ITRs.
- That any proposed revisions are confined to the traditional scope of the ITRs, where international regulation is required around technical issues is limited to telecommunications networks and interoperability standards.
- There should be no revisions to the ITRs that involve regulation of the Internet Protocol and the layers above.
- There should be no revisions that could have a negative impact on affordable access to the Internet or the public's rights to privacy and freedom of expression.
More generally we call upon the ITU to promote principles of net neutrality, open standards, affordable access and universal service, and effective competition.
Signatories:
- Access (Global)
- Association for Progressive Communications (Global)
- Bangladesh NGOs Network for Radio and Communication (Bangladesh)
- Bytes for All (Pakistan)
- Center for Democracy and Technology (United States of America)
- Centre for Community Informatics Research (Canada)
- Centre for Internet and Society (India)
- Collaboration on International ICT Policy for East and Southern Africa (Eastern and Southern Africa)
- Consumer Council of Fiji (Fiji)
- Consumers International (Global)
- Dynamic Coalition on Internet Rights and Principles (IRP) (Global)
- Electronic Frontier Finland (Finland)
- Imagining the Internet Center (United States of America)
- Instituto Nupef (Brazil)
- Internet Democracy Project (India)
- Internet Research Project (Pakistan)
- Global Partners and Associates (United Kingdom)
- GobernanzadeInternet.co (Colombia)
- ICT Watch Indonesia (Indonesia)
- Instituto Brasileiro de Defesa do Consumidor / Brazilian Institute for
- Consumer Defense (Brazil)
- InternetNZ (New Zealand)
- IT for Change (India)
- Media Education Center (Armenia)
- ONG Derechos Digitales (Chile)
- OpenMedia (Canada)
- Public Knowledge (United States of America)
- Thai Netizen Network (Thailand)
- Ginger Paque (Venezuala)
- Nnenna Nwakanma (Côte d'Ivoire)
- Sonigitu Ekpe (Nigeria)
- Wolfgang Kleinwächter (Denmark)
Submission on India's Draft Comments on Proposed Changes to the ITU's ITRs
Our detailed comments on India's draft proposals can be found here. Also read the final version of Indian Government's submission to ITU on November 3, 2012.
Background
We believe that, aspects of Internet governance that have been and are presently addressed by bodies other than ITU should not be brought under the mandate of the ITU through the ITRs.
Some of the proposed changes to the ITR's could have a significant negative impact on the openness of the Internet.
In addition, the processes related to the WCIT lack openness and transparency: the WCIT / ITU excludes civil society, academia and other stakeholders from participation in and access to most dialogues and documents, contrary to established principles of Internet governance as laid down in the Tunis Agenda and as supported by the Indian government at several national and international fora. The WCIT process needs to be improved both at the domestic and global level. We urge the Indian government to support a more open process in the future, with respect to deliberations that will have a significant impact on the people.
We recognise that concerns regarding cyber-security, spam, fraud, etc. are real and that some of these concerns require to be addressed at the global level. However, we believe that as a number of parallel processes are working on these specific issues, these need not be brought under the ITRs.
We therefore strongly recommend that the ITRs continue to be restricted to the infrastructure layer that has traditionally been the area of its focus and not the content or the application layer of the Internet. Any measure that impinges on these layers should be kept out of ITRs and taken up at other appropriate (multi-stakeholder) fora.
We note that the proposal ARB/7/24 defines an "operating agency" as "any individual, company, corporation or governmental agency which operates a telecommunication installation intended for an international telecommunication service or capable of causing harmful interference with such a service" and believe that this definition is too broad in scope and ambit. Inclusion of such a term would broaden the mandate of the ITU to regulate numerous actors in the Internet sphere who do not fall under the infrastructure layer of the Internet. We call on the Indian government to ensure that the term "operating agency" is defined in a narrower or more restrictive manner and only used in exceptional cases. Normally, the obligations of member states should be with respect to "recognised operating agencies" and not omnibus all "operating agencies".
Follow-up
We would like to note that we have never officially received this document directly from the Indian government. In view of the support the Indian government continually espouses for multi-stakeholder Internet governance, this is a matter of deep regret.
We are aware that the official closing date for proposals is early November. However, we also know that several governments intend to submit proposals right upto the beginning of the WCIT meeting. In addition, several governments have included civil society representatives on their official delegation.
We therefore call upon the Department of Telecommunications to organise an open consultation with civil society representatives, to discuss both India's proposals and the comments of various civil society representatives on them, in greater depth, as part of DoT’s preparation for the WCIT meeting and in line with India's espoused commitment to multi-stakeholderism. We look forward to discussing our inputs with the Government to make the decision making process on governance more participatory and inclusive.
Reaction to Draft Proposal from India based on final draft ITR document of ITU
 RECOS ON INDIAS PROPOSAL FOR ITR AMENDMENTS Nov2.pdf
—
PDF document,
127 kB (130152 bytes)
RECOS ON INDIAS PROPOSAL FOR ITR AMENDMENTS Nov2.pdf
—
PDF document,
127 kB (130152 bytes)
Will The International Telecommunication Regulations (ITRs) Impact Internet Governance? A Multistakeholder Perspective
Principles
I'll outline some broad principles that should be kept in mind while deciding on proposals for the International Telecommunications Regulations (ITR).
Any proposal should be considered for the ITR if an only if it satisfies all the below criteria:
- Only if international regulation is needed
- If only national regulation is sufficient, then ITR is not the right place for it.
- International roaming price transparency, for instance, is an issue where international cooperation is required.
- Only if it is a technical issue limited to telecommunications networks and interoperability
- On the issues of 'security', if it is strictly about network security, then it is fine.
- ITU already does some standard setting work around this.
- If it about security of root server operations, or DNS, etc., that's not around telecommunications, despite being a technical issue.
- If it is about criminal activities on telecommunications networks, that is not a technical issue.
- Only if it is something that can be decided at the level of states.
- Multistakeholder issues should not end up at the ITU, since the ITU is not a multistakeholder body.
- This principle has been accepted by the ITU itself in the Geneva Declaration as well as the Tunis Agenda.
- Only if it proposes to address a proven harm
- The ETNO proposal, for instance, does not make it very clear why they think current interconnection system is a problem.
- Though the ETNO proposal says that it is required to enable "fair compensation", "sustainable development of telecom", it does so without showing why the current payment mechanisms are unsustainable, or how telecom industry has changed lately, or even how moving from voice to data (even for voice) is going to affect "sustainable development of telecom".
- Geoff Huston provides the wonderful example of how ten years ago, content providers were asking for fair compensation from telecom providers ("content is being provided free, while ISPs charge customers; ISPs are worthless without content, hence ISPs need to share revenue with content providers"). Now the opposite argument is being made by telecom operators.
- Airtel in India has publicly asked Google and Facebook for revenue sharing.
- Rohan Samarajiva of LIRNEasia
- He believes ETNO proposal is bad for developing countries.
- Adverse unintended effect of ETNO proposal ("sending-party network pays") is that less traffic will be directed towards poorer regions without the ability (whether through ad sales, or otherwise) to justify that expenditure by the sender.
- ISOC paper is one of the most in-depth analysis so far.
- They strongly believe it is going to be bad for Internet
- Truth is that there has been no clear economic study so far of the potential impact. Hence counting benefits without proper analysis is risky.
- Only if there's no better place than ITU
- If another existing organization like ICANN or IETF can look at it, then ITU should not take over.
If all the above principles are satisfied, then the question becomes:
- Does the proposal further substantive principles, such as:
- Development
- Competition and prevention of monopolies
- Etc.
If the proposal does advance such substantive principles, then we should ask what kind of regulation is needed: Whether mandatory or not whether it is the minimal amount required to achieve the policy objectives.
Conclusion
Indian government's positions on the specific proposals to the ITR haven't yet been made public.
But the India government has taken a public position on the larger issue before: the IBSA statement on Enhanced Cooperation from December 2010. the IBSA reaffirms its commitment to the stability and security of the Internet as a global facility based on the full participation of all stakeholders, from both developed and developing countries, within their respective roles and responsibilities in line with paragraph 35 of the Tunis Agenda.
"The management of the Internet encompasses both technical and public policy issues and should involve all stakeholders and relevant intergovernmental and international organizations."
Demonization of the ITU is not good, though some in civil society have engaged in it, and is not the issue here. * After all, ITU was a core part of the WSIS process that led to the multistakeholder system. * ITU does have its own role to play in Internet governance.
Importantly, transparency and public participation is required. * We have signed an international civil society letter asking ITU to be more transparent. This has had a little impact; more documents are now out in the public. And there's now WCITLeaks.org * The Indian government must hold inclusive meetings with all relevant experts and stakeholders, including civil society organizations and academics.
Indian Government's Submission to ITU
Read the detailed comments on India's draft proposal on the Proposed Amendments to the ITU’s ITR’s – November 3, 2012
|
World Conference on International Telecommunications (WCIT-12) Dubai, 3-14 December 2012 | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
PLENARY MEETING |
Document 21-E 3 November 2012 Original: English |
India (Republic of)
PROPOSALS FOR THE WORK OF THE CONFERENCE
Introduction
We recognise and appreciate the efforts of International Telecommunication Union in preparing the Draft on proposed ITRs for WCIT 2012.
The attached proposal is developed through a consultation process involving various stakeholder groups, both, in Indian Public and Private sectors. Due consideration has been given to the existing legislations and government policies in the preparation of this proposal. We acknowledge that since 1988, there have been significant changes and challenges in Telecommunications / ICTs in terms of Technological breakthroughs, New Services and Market Structure. Acknowledging this fact, India’s proposal is offered in the form of addition (ADD) or modification (MOD) only on some of the relevant proposals, by giving reference to the appropriate CWG/4/XXX number mentioned in the Annex 2 of the ITU Document 4(Add.2)-E. Considering the magnitude of issues in International Telecommunications, India may take appropriate stand on other provisions of the draft ITR document during the WCIT discussions.
Further, the proposals from different regions to the conference as well as its preparatory process were carefully studied. In order to help the conference achieve a consensus on the various issues being discussed, the content of this proposal has been largely drawn from the output of the Council Working Group on WCIT (WCIT/4 Add.2 ” Draft of the future ITRs”).
A new proposal on 5A: Confidence and Security of Telecommunications/ICTs is also included as India believes that an international framework on Security is of importance in today’s connected world.
INTERNATIONAL TELECOMMUNICATION
REGULATIONS
PREAMBLE
|
MOD |
IND/21/1 |
|---|
1 While the sovereign right of each Member State to regulate its telecommunications is fully recognized, the provisions of the present International Telecommunication Regulations (hereinafter “Regulations”) complement the Constitution and Convention of the International Telecommunication Union, with a view to attaining the purposes of the International Telecommunication Union in promoting the development of telecommunication services and their most efficient operation while harmonizing the development of facilities for world-wide telecommunications.
Reasons: This Proposal is based on CWG/4A2/3.
Article 1
Purpose and Scope of the Regulations
ADD IND/21/2
3A c) These Regulations recognize that Member States should endeavour to take the necessary measures to prevent interruptions of services and ensure that no harm is caused by their operating agencies to the operating agencies of other Member States which are operating in accordance with the provisions of these Regulations.
Reasons: This Proposal is based on CWG/4A2/12.
ADD IND/21/3
3B d) These Regulations recognize the absolute priority for safety of life telecommunications, including distress telecommunications, emergency telecommunications services and telecommunications for disaster relief as provided in Article.
Reasons: This Proposal is based on CWG/4A2/14.
Article 2
Definitions
ADD IND/21/4
14A 2.1A Telecommunication/ICT: Any transmission, emission or reception, including processing, of signs, signals, writing, images and sounds or intelligence of any nature by wire, radio, optical or other electromagnetic systems, having a bearing on Telecommunication Technologies and Services.
Reasons: This Proposal is based on CWG/4A2/48.
ADD IND/21/5
27A 2.11 Transit rate: a rate set by the point of transit in a third country (indirect relation).
Reasons: This Proposal is based on CWG/4A2/74.
ADD IND/21/6
27C 2.13 Spam: information transmitted over telecommunication networks as text, sound, image, tangible data used in a man-machine interface bearing advertizing nature or having no meaningful message, simultaneously or during a short period of time, to a large number of particular addressees without prior consent of the addressee (recipient) to receive this information or information of this nature.
Reasons: This Proposal is based on CWG/4A2/78.
ADD IND/21/7
27D 2.14 Hub: a transit center (or network operator) that offers to other operators a telecommunication traffic termination service to nominated destinations contained in the offer.
Reasons: This Proposal is based on CWG/4A2/80.
ADD IND/21/8
27E 2.15 Hubbing: the routing of telecommunication traffic in hubbing mode consists in the use of hub facilities to terminate telecommunication traffic to other destinations.
Reasons: This Proposal is based on CWG/4A2/82.
ADD IND/21/9
27F 2.16 Network fraud: (fraud on international telecommunication networks): The causing of harm to operating agencies or to the public, the wrongful obtaining of gain in the provision of international telecommunication services through abuse of trust or deception, including through inappropriate use of numbering resources.
Reasons: This Proposal is based on CWG/4A2/87.
ADD IND/21/10
27G 2.17 Global telecommunication service (GTS): A service which enables communication to be established through a global number between subscribers whose physical location and national jurisdiction have no bearing on the tariff to be set for the service’s use; which satisfies and complies with recognized and accepted international standards; and which is provided over the public telecommunication network by operating agencies having obtained the relevant numbering resources from ITU-T.
Reasons: This Proposal is based on CWG/4A2/89.
ADD IND/21/11
27H 2.21 Originating Identification: The Originating Identification is the service by which the terminating party shall receive the identity information in order to identify the origin of the communication.
Reasons: This Proposal is based on CWG/4A2/81.
ADD IND/21/12
27L 2.25 Stability of the international telecommunication network: The capability of the international telecommunication network to carry international traffic in the event of failure of telecommunication nodes or links and also in the face of internal and external destructive actions and to return to its original state.
Reasons: This Proposal is based on CWG/4A2/99.
ADD IND/21/13
27M 2.26 Security of the international telecommunication network: The capability of the international telecommunication network to withstand internal and external destabilizing actions liable to compromise its functioning.
Reasons: This Proposal is based on CWG/4A2/101.
ADD IND/21/14
27N 2.27 International Roaming: Provision to the subscriber of the opportunity to use telecommunication services offered by other operating agencies of other member states, with which the subscriber has not concluded an agreement.
Reasons: This Proposal is based on CWG/4A2/103.
ADD IND/21/15
27O 2.28 IP interconnection: IP interconnection refers to means and rules employed to ensure the delivery of IP traffic through different networks.
Reasons: This Proposal is based on CWG/4A2/105.
ADD IND/21/16
27P 2.29 End to end quality of service delivery and best effort delivery: End to End quality of service delivery refers to the delivery of PDU (Packet Data Unit) with predefined end-to-end performance objectives; Best-effort delivery refers delivery to of a PDU without predefined performance targets.
Reasons: This Proposal is based on CWG/4A2/107.
Article 3
International Network
ADD IND/21/17
31A 3.5 Member States shall ensure that international naming, numbering, addressing and identification resources are used only by the assignees and only for the purposes for which they were assigned; and that unassigned resources are not used. The provisions of the relevant ITU-T Recommendations shall be applied.
Reasons: This Proposal is based on CWG/4A2/134.
ADD IND/21/18
31B 3.6 International calling party number delivery shall be provided in accordance with relevant ITU-T Recommendations.
Reasons: This Proposal is based on CWG/4A2/142.
Article 4
International Telecommunication Services
MOD IND/21/19
34 4.3 Subject to national law, Member States shall endeavour to ensure that operating agencies provide and maintain, to the greatest extent practicable, a satisfactory quality of service corresponding to the relevant ITU-T Recommendations with respect to:
Reasons: This Proposal is based on CWG/4A2/168.
MOD IND/21/20
35 a) access to the international network by users using terminals which are permitted to be connected to the network and which do not cause harm or diminish the level of safety and security of technical facilities and personnel;
Reasons: This Proposal is based on CWG/4A2/174.
MOD IND/21/21
36 b) international telecommunication facilities and services available to customers for their use;
Reasons: This Proposal is based on CWG/4A2/176.
MOD IND/21/22
37 c) at least a form of telecommunication service which is reasonably accessible to the public, including those who may not be subscribers to a specific telecommunication service; and
Reasons: This Proposal is based on CWG/4A2/179.
MOD IND/21/23
38 d) a capability for interworking between different services, as appropriate, to facilitate international telecommunication services.
Reasons: This Proposal is based on CWG/4A2/181.
ADD IND/21/24
38A 4.4 Member States shall ensure that operating agencies providing international telecommunication services, including roaming, make available to subscribers information on tariffs and taxes. Each subscriber should be able to have access to such information and receive it in a timely manner and free of charge when roaming (entering into roaming), except where the subscriber has previously declined to receive such information.
Reasons: This Proposal is based on CWG/4A2/188.
ADD IND/21/25
38B 4.5 Given the particular characteristics of GTS, which allows subscribers to have a worldwide number, implement GTSs in accordance with the National regulations.
Reasons: This Proposal is based on CWG/4A2/195.
ADD IND/21/26
38E 4.8 Member States, subject to national security requirements, may foster the establishment of mutual agreements on mobile services accessed within a predetermined border zone in order to prevent or mitigate inadvertent roaming charges.
Reasons: This Proposal is based on CWG/4A2/201.
Article 5
Safety of Life and Priority of Telecommunications
MOD IND/21/27
39 5.1 Safety of life telecommunications, including distress telecommunications, emergency telecommunication services and telecommunications for disaster relief, shall be entitled to transmission as of right and shall, where technically practicable, have absolute priority over all other telecommunications, in accordance with the relevant Articles of the Constitution, Convention and relevant ITU-T Resolutions and Recommendations.
Reasons: This Proposal is based on CWG/4A2/204.
ADD IND/21/28
41B 5.5 Member States should cooperate to introduce in addition to their existing national emergency numbers, a global number for calls to the emergency services globally.
Reasons: This Proposal is based on CWG/4A2/217.
ADD IND/21/29
41C 5.6 Member States shall ensure that operating agencies inform every roaming subscriber of the number to be used for calls to the emergency services, while entering into roaming, free of charge.
Reasons: This Proposal is based on CWG/4A2/219.
ADD IND/21/30
Article 5A
Confidence and security of telecommunications/ICTs
Reasons: This Proposal is based on CWG/4A2/221.
ADD IND/21/31
41D 5A1. Member‐States shall have the right to take appropriate measures to protect and Secure the ICT Network infrastructure and data contained in or flowing through the Network and also to prevent the misuse of ICT network and services within their state.
5A2. The Member States should endeavour to take appropriate measures, individually or in cooperation with other Member states, to ensure Security of the ICT Network and information, including user information, contained in or flowing through the ICT network within their jurisdiction.
5A3. Member‐States should endeavour to oversee that Operating Agencies in their territory do not engage in activities which impinge on the security and integrity of ICT network such as denial of service attack, unsolicited electronic communication (spam), unsolicited access to network elements and devices etc., to enable effective functioning of ICTs in secure and trustworthy conditions.
5A4. Member States should endeavour to cooperate to harmonize national laws, jurisdictions, and practices in the relevant areas.
Reasons: Combined proposal on clauses proposed from CWG/4A2/222 to 232 in 5A and 5B.
Article 6
Charging and Accounting
ADD IND/21/32
43A 6.1.1A Cost of International Roaming Services
a) Member States shall encourage competition in the international roaming market;
b) Member States are encouraged to cooperate to develop policies for reducing charges on international roaming services.
Reasons: This Proposal is based on CWG/4A2/243.
MOD IND/21/33
45 6.1.3 Member States are free to levy fiscal taxes on international telecommunication services in accordance with their national laws; however, the Member States should endeavour to avoid international double taxation on such services.
Reasons: This Proposal is based on CWG/4A2/249.
ADD IND/21/34
54E 6.10 Subject to national law, Member States shall ensure that Operating Agencies collaborate in preventing and controlling fraud in international telecommunications by:
– Identifying and transmitting to the transit and destination Operating Agencies the pertinent information required for the purposes of payment for the routing of international traffic, in particular the originating Country Code, National Destination Code and the Calling Party Number.
– Following up requests of other Member States or their Operating Agencies to investigate calls that cannot be billed, and helping to resolve outstanding accounts.
– Following up requests of other Member States or their Operating Agencies to identify the source of calls originated from their territories exerting potential fraudulent activity.
Reasons: This Proposal is based on CWG/4A2/287.
ADD IND/21/35
54F 6.11 The ITU Standardization Sector shall be responsible for disseminating the regulatory frameworks in place in administrations having an impact on matters related to fraud.
Reasons: This Proposal is based on CWG/4A2/289.
ADD IND/21/36
54H 6.12A Member States shall foster the establishment of international roaming mobile services prices based on principles of reasonability, competitiveness and non-discrimination relative to prices applied to local users of the visited country.
Reasons: This Proposal is based on CWG/4A2/293.
ADD IND/21/37
54K 6.14 Member States should foster continued investment in high-bandwidth infrastructures.
Reasons: This Proposal is based on CWG/4A2/299.
ADD IND/21/38
54L 6.15 Member States shall promote cost-oriented pricing. Regulatory measures may be imposed to the extent that this cannot be achieved through market mechanisms and to the extent that such measures do not hinder competition.
Reasons: This Proposal is based on CWG/4A2/301.
ADD IND/21/39
54N 6.17 Member States shall promote transparency of end-user prices, in particular to avoid surprising bills for international services (e.g mobile roaming and data roaming).
Reasons: This Proposal is based on CWG/4A2/305.
ADD IND/21/40
54S 6.D Member States should endeavour to take measures to ensure that an adequate return is provided on investments in network infrastructures in identified areas. If this cannot be achieved through market mechanisms, then other mechanisms may be used.
Reasons: This Proposal is based on CWG/4A2/315.
ADD IND/21/41
54O 6.18 Member States should consider measures to favour special interconnection rates for landlocked countries.
Reasons: This Proposal is based on CWG/4A2/307.
ADD IND/21/42
54P 6.18A Member States should endeavour that Recognized Operating Agencies establish charging units and parameters that bill telecommunication service consumers according to what is effectively consumed.
Reasons: This Proposal is based on CWG/4A2/309.
ADD IND/21/43
54R 6.20 Rendering and Settlement of Accounts
6.20.1 The settlement of international accounts shall be regarded as current transactions and shall be effected in accordance with the current international obligations of the Member States and Sector Members concerned in those cases where their governments have concluded arrangements on this subject. Where no such arrangements have been concluded, and in the absence of special agreements made under Article 42 of the Constitution, these settlements shall be effected in accordance with the Administrative Regulations.
6.20.2 Administrations of Member States and Sector Members which operate international telecommunication services shall come to an agreement with regard to the amount of their debits and credits.
6.20.3 The statement of accounts with respect to debits and credits referred to in No. 498 above shall be drawn up in accordance with the provisions of the Administrative Regulations, unless special arrangements have been concluded between the parties concerned.
Reasons: The text is taken from CV 497, 498 and 499. This proposal is based on CWG/4A2/313.
ADD IND/21/44
57B Member States shall encourage the provision of global services based on international standards that ensure accessible telecommunications and ICT services to persons with disabilities.
So Much to Lose
Nishant Shah's column was published in the Indian Express on December 2, 2012.
Unless you have been hiding under a rock, you have been a witness to the maelstrom of events that accompanied the death of the political leader Bal Thackeray. For me, the brouhaha was elbowed out by the case of the police arresting two women for critiquing the events on Facebook. The person who wondered about the nature of the enforced mourning and the state of our public life, and her friend who “liked” the comment on Facebook, were booked and arrested under charges that can only be considered preposterous.
I will not repeat these arguments because it is needless to say that I am on the side of the women and think of this as yet another manifestation of the stringent measures which are being evolved as an older broadcast way of thinking meets the decentralised realities of digital technologies.
In the midst of this the idea of internet freedom needs to be revisited. The global Press Freedom Index 2011-12 report compiled by Reporters Without Borders, ranks India at 131, or as a “partly free” country, marking us as a country where the notion of internet freedom is not to be taken for granted, and possibly also one where the concept is not properly understood.
Citing various instances from the central government’s plans to censor the social web to the authoritarian crackdown on activists and cultural producers involved in online civic protests, from the traditional media industry’s stronghold over intellectual property regimes to the arrest of individuals for voicing their independent critiques online, the report shows that we not only have an infrastructure deficit (with only 10 per cent of the people in the country connected), but also a huge social and political deficit, which is being exposed by our actions and reactions to the Web.
Take the case of professor Ambikesh Mahapatra dean of the chemistry department of Jadavpur University, who was picked up by the police and lodged in the lock up for almost 40 hours for forwarding an e-mail that contained a cartoon of Trinamool Congress leaders Mamata Banerjee, Mukul Roy and Dinesh Trivedi. He and his housing society co-resident Subrata Sengupta were charged with defamation and outraging the modesty of a woman. While the proceedings are underway with the next date of hearing slated in February, 2013, the Jadavpur university professor says, “Section, 66A of the IT Act is being used for suppression of the freedom of speech. In my opinion, it is being misused by the state government, repeatedly. The section does not empower anyone to arrest those who voice their opinion and never meant to harm anybody’s image. Prompt action is needed to check the misuse of law.”
Likewise, Ravi Srinivasan, a 46-year-old a businessman from Pondicherry, was arrested for tweeting against Karti Chidambaram, son of Union Finance Minister P Chidambaram. His arrest and consequent release has not blunted his spirit. He says, “At the time (of the arrest) I had not heard of Section 66(A). I still cannot fathom why and how a tweet sent out to just 12 people — half of them family and friends — caught the eye of the police. By evening, when I had come home from the police station, my Twitter following had gone up to 1,700. About 15,000 people re-tweeted the statement that got me arrested.”
Given the series of incidents that have marked the last year and the whimsical nature of regulatory injunctions on internet freedom in the country, it might be a good idea for us to reflect on democracy and freedom.
We need to examine the fundamental nature of freedom, and how these attempts at regulating the internet are only a symptom of the systemic failures of enshrining freedom of speech, information, identity and dignity in India. However, internet freedom is often a difficult concept to engage with, because it is one of those phrases that seem to be self-explanatory but without a straightforward explanation. There are three axes which might be useful to unpack the baggage that comes with internet freedom, both for our everyday practices, and our imagined future:
Freedom of: The freedom of the internet is something that is new and needs more attention. We have to stop thinking of the internet as merely a medium or a conduit of information. As the Web becomes inextricably linked with our everyday lives, the internet is no longer just an appendage or an externality. It becomes a reference point through which our social, political and economic practices are shaped. It becomes a defining point through which we draw our meanings of what it is to be a part of the society, to have rights, to be politically aware, to be culturally engaged — to be a human. The freedom of the Net is important because the crackdowns on the Net are an attack on our rights and freedoms. The silencing of a voice on Facebook, might soon gag the voices of people on the streets, creating conditions of silence in the face of violence perpetuated by the powerful.
Freedom to: Freedom to the internet is often confused with access to the internet. While, of course, access is important in our imagination of a just society where everybody is equally connected, freedom is also about creating open and fair societies. If the power of the internet is in creating alternative spaces of expression, deliberation and opinion-making, then the freedom to the internet is about being safe and responsible in these spaces. A society that controls these spaces of public discussion, under the guise of security and public safety, is a society that has given up its faith in freedom.
Freedom for: It is often not clear that when popular technologies of information and communication are regulated and censored, it is not merely the technology that is being controlled. What is being shaped and contained is the way people use them. The freedom for the internet is about the freedom for people. The possibility that Internet Service Providers are being coerced into revealing personal information of users to police states, that intermediaries are being equipped to remove content that they find offensive from the web, and that views expressed on the social media can lead to legal battles by those who have the power but not the acumen to exercise it, all have alarming consequences. There is a need to fight for freedom, not only for the defence of technology but also for the defence of the rights that we cherish that risk being eroded.
The case of these Facebook arrests is not new. It has happened before and it will continue happening as immature governments are unable to cope with the real voices of representational democracy. These cases sometimes get naturalised because they get repeated, and even without our knowledge, can start creating a life of fear, where we internalise the regulatory system, not voicing our opinions and ideas for fear of persecution. And so, whether you agree with their politics or not, whether you endorse the viewpoints of the people who are under arrest, whether you feel implicated or not in this case, we have to realise that even if we might not agree with somebody’s viewpoint, we must defend their right to have that particular viewpoint. Anything else, and tomorrow, when you want to say something against powers of oppression, you might find yourself alone, as your voice gets heard only by those who will find creative ways of silencing you.
— With inputs from Gopu Mohan, Madhuparna Das and V Shoba
The Worldwide Web of Concerns
Pranesh Prakash's column was published in the Asian Age on December 10, 2012.
The International Telecommunication Union’s World Conference on International Telecommunications (WCIT-12) is currently under way in Dubai, after a gap of 25 years. At this conference, the International Telecommunication Regulations — a binding treaty containing high-level principles — are to be revised.
Much has changed since the 1988 Melbourne conference. Since 1988, mobile telephony has grown by leaps and bounds, the Internet has expanded and the World Wide Web has come into existence. Telecommunications is now, by and large, driven by the private sector and not by state monopolies.
While there are welcome proposals (consumer protection relating to billing of international roaming), there have also been contentious issues that Internet activists have raised: a) process-related problems with the ITU; b) scope of the ITRs, and of ITU’s authority; c) content-related proposals and “evil governments” clamping down on free speech; d) IP traffic routing and distribution of revenues.
Process-related problems: The ITU is a closed-door body with only governments having a voice, and only they and exorbitant fees-paying sector members have access to documents and proposals. Further, governments generally haven’t held public consultations before forming their positions. This lack of transparency and public participation is anathema to any form of global governance and is clearly one of the strongest points of Internet activists who’ve raised alarm bells over WCIT.
Scope of ITRs: Most telecom regulators around the world distinguish between information services and telecom services, with regulators often not having authority over the former. A few countries even believe that the wide definition of telecommunications in the ITU constitution and the existing ITRs already covers certain aspects of the Internet, and contend that the revisions are in line with the ITU constitution. This view should be roundly rejected, while noting that there are some legitimate concerns about the shift of traditional telephony to IP-based networks and the ability of existing telecom regulations (such as those for mandatory emergency services) to cope with this shift.
ITU’s relationship with Internet governance has been complicated. In 1997, it was happy to take a hands-off approach, cooperating with Internet Society and others, only to seek a larger role in Internet governance soon after. In part this has been because the United States cocked a snook at the ITU and the world community in 1998 through the way it established Internet Corporation for Assigned Names and Numbers (ICANN) as a body to look after the Internet’s domain name system. While the fact that the US has oversight over ICANN needs to change (with de-nationalisation being the best option), Russia wants to supersede ICANN and that too through current revisions of the ITRs. Russia’s proposal is a dreadful idea, and must not just be discarded lightly but thrown away with great force. The ITU should remain but one among multiple equal stakeholders concerned with Internet governance.
One important, but relatively unnoticed, proposed change to ITU’s authority is that of making the standards that ITU’s technical wing churns out mandatory. This is a terrible idea (especially in view of the ITU’s track record at such standards) that only a stuffy bureaucrat without any real-world insight into standards adoption could have dreamt up.
Content-related proposals: Internet activists, especially US-based ones, have been most vocal about the spectre of undemocratic governments trying to control online speech through the ITRs. Their concerns are overblown, especially given that worse provisions already exist in the ITU’s constitution. A more real threat is that of increasing national regulation of the Internet and its subsequent balkanisation, and this is increasingly becoming reality even without revisions to the ITRs. Having said that, we must ensure that issues like harmonisation of cyber-security and spam laws, which India has been pushing, should not come under ITU’s authority. A further worry is the increasing militarisation of cyberspace, and an appropriate space must be found by nation-states to address this pressing issue, without bringing it under the same umbrella as online protests by groups like Anonymous.
Division of revenue: Another set of proposals is being pushed by a group of European telecom companies hoping to revive their hard-hit industry. They want the ITU to regulate how payments are made for the flow of Internet traffic, and to prevent so-called “net neutrality” laws that aim to protect consumers and prevent monopolistic market abuse. They are concerned that the Googles and Facebooks of the world are free-riding on their investments. That all these companies pay to use networks just as all home users do, is conveniently forgotten. Thankfully, most countries don’t seem to be considering these proposals seriously.
Can general criteria be framed for judging these proposals? In submissions to the Indian government, the Centre for Internet and Society suggested that any proposed revision of the ITRs be considered favourably only if it passes all the following tests: if international regulation is required, rather than just national-level regulation (i.e., the principle of subsidiarity); if it is a technical issue limited to telecommunications networks and services, and their interoperability; if it is an issue that has to be decided exclusively at the level of nation-states; if the precautionary principle is satisfied; and if there is no better place than the ITRs to address that issue. If all of the above are satisfied, then it must be seen if it furthers substantive principles, such as equity and development, competition and prevention of monopolies, etc. If it does, then we should ask what kind of regulation is needed: whether it should be mandatory, whether it is the correct sort of intervention required to achieve the policy objectives.
The threat of a “UN takeover” of the Internet through the WCIT is non-existent. Since the ITU’s secretary-general is insisting on consensus (as is tradition) rather than voting, the possibility of bad proposals (of which there are many) going through is slim. However, that doesn’t mean that activists have been crying themselves hoarse in vain. That people around the world are a bit more aware about the linkage between the technical features of the Internet and its potential as a vehicle for free speech, commerce and development, is worth having to hear some shriller voices out there.
The writer is policy director at the Centre for Internet and Society, Bengaluru
The Trouble with Hurried Solutions
Chinmayi Arun's Op-ed was published in the Hindu on December 15, 2012.
The World Conference on International Telecommunication (WCIT) that concluded on December 14 saw much heated debate. Some countries wanted to use the International Telecommunication Union (ITU) to gain intergovernmental control of the World Wide Web. Some saw it as an opportunity to democratise the Internet, by replacing U.S. and corporate domination of Internet policy, with a more intergovernmental process. Others insisted that the Internet must be left alone.
The result is that after many days’ deliberations, there was no consensus. The amended International Telecommunication Regulations (ITRs) document has not yet been signed by over 50 countries, of which some like the United States have refused to sign altogether, while others have said that they will need to consult with their national governments before signing.
This article discusses the broader issue under question, which is, whether ITU is the best forum to solve the cross-border problems that arise in relation to the Internet.
WCIT, ITU and ITRs
The ITU has been creating international policy from the days in which the telegraph was prevalent. Although it is now a United Nations agency, its existence predates the U.N. As technology evolved, forcing the telegraph to give way to the telephone, the ITU created new standards for telephony. It even rechristened itself from ‘International Telegraph Union’ to ‘International Telecommunications Union’.
The ITU performs an essential role in ensuring that multiple states with their varying technology, standards and legal systems, are able to interconnect and co-ordinate. Its harmonising rules and standards make co-ordination easier and cheaper than having each state come to an agreement with every other state. The ITRs within the ITU framework facilitate co-ordination by creating binding rules for member states.
Some countries’ proposals for the amendment of the ITRs would have affected content on the Internet substantially. However, after prolonged negotiation, the final draft that was under consideration contained an explicit statement excluding such content from the ITRs’ purview. This draft also came with a resolution that made reference to states’ elaborating their Internet related public policy positions in ITU fora, which was a source of controversy.
Some of the initial suggestions like Russia’s controversial proposal would have given the ITU greater sway over the Internet, permitting it to lay down global standards. These standards may have encouraged countries to inspect data transmitted across the Internet to check whether it is undesirable content raising serious privacy and freedom of speech concerns, especially in countries that do not protect these rights.
The global standards created by the ITU would have permeated to the companies that create the web-based applications that we use, and the resulting law and technological choices would have affected individual users.
Internet governance
The ITU makes its decisions using a traditional model that only seeks consensus between governments, and this is far removed from the way in which the Internet has been governed thus far. Therefore, although expanding the ITU’s mandate to the Internet may seem natural to those who have followed its evolution mirroring the evolution of information technology, the ITU’s manner of functioning is viewed by many as being at odds with the more multi-stakeholder and ad hoc system used to build Internet policy.
In the 1990s, John Perry Barlow proclaimed that cyberspace was outside national borders, and questioned the authority and legitimacy of a national government’s attempts to govern it. Over the years, it has become clear that national governments can exert jurisdiction in cyberspace: filtering content, launching surveillance of users, and creating law that impacts citizens’ behaviour online directly and indirectly.
However, governments’ exertion of will on Internet users is tempered greatly by the other forces that have a strong influence on the Internet. User-behaviour and content often depend on the policies of major service providers like Google, Yahoo, Twitter and Facebook.
Key standards and functions like the allocation of domain names and developing of Internet standards are managed by organisations like ICANN and IETF, which are not governmental organisations. Features like user anonymity are based on technological choices on the World Wide Web. Therefore, governments face significant obstacles and counterbalancing power when they attempt to impose their will on citizens online.
The ITU can weigh this power balance in favour of governments. Many fear that more government power will lead to more censorship, surveillance and stifling of the innovation that is integral to the evolution of Internet. But others support ITU intervention, in the belief that an international inter-governmental regulatory body would be more accountable, and would prevent corporate abuse of power.
Several of the aforementioned corporations, as well as regulatory bodies under question, are headquartered in the United States. There are those who see this as excessive U.S. influence on the Internet, eroding the sovereignty of other states, which have relatively limited influence over what their citizens can transmit and access online. These people see the ITU as a forum that can democratise Internet Governance, giving states shared influence over the web. However, this shared influence is resisted by those who find that the U.S. influence offers them more leverage and protection for their freedom of speech, than increased influence of countries that threaten this internationally accepted human right.
Powerful arguments in favour of increased ITU involvement include highlighting the dangers of abandoning the Internet to the free market. It is true that markets need some regulation to guard against malfunction and abuse of power by stronger players. However, the significant question is not whether these markets should be regulated, but how they should be regulated. Unfortunately, many of the arguments that supported expansion of the ITU’s mandate failed to establish why the ITU is the best solution to the problems plaguing the Internet, rather than being the most readily available reaction.
Any regulatory intervention must have very clear objectives, and some estimate of its likely impact. The intervention must not be considered in isolation but in contrast with other ways to achieve the same goals. Although some of the serious transnational issues plaguing the Internet need international solutions, the ITU, at least in its current avatar, is not necessarily the best remedy. It also remains unclear exactly what effect ITU intervention would have on the Internet — whether it would really offer solutions as intended, or whether it would prove more detrimental than useful, condoning of human rights violations and slowing the blistering innovation that is characteristic of the Internet.
Lack of consensus
Therefore, some of the initial concerns expressed by the countries that refused to sign the ITRs were legitimate. However, the final ITRs document addressed many of these concerns. The dissent emerged over the insertion of text in the preamble that recognised member states’ rights to access international telecommunication networks. These rights, being expressed only in the preamble, are not enforceable, even if they express intentions that are unacceptable to some.
The debates at the WCIT made it clear that the world is not yet ready to come to a unified position on this subject. Perhaps the ITU’s continuation in its path towards increasing, and making effective, multi-stakeholder participation will be the unifying factor some day, if it evolves into a forum which everyone sees as sufficiently democratic, transparent and accountable for Internet policy.
(The writer is Assistant Professor of Law at National Law University, Delhi, and a Fellow of the Centre for Internet and Society, Bangalore. She attended the WCIT from December 3-14)
Presentation on MLATS
 Presentation on MLATS-1.pdf
—
PDF document,
313 kB (321475 bytes)
Presentation on MLATS-1.pdf
—
PDF document,
313 kB (321475 bytes)
Internet-driven Developments — Structural Changes and Tipping Points
The symposium served as an inaugural event for the Global Network of Interdisciplinary Centers, which currently includes as its members:
- The Berkman Center for Internet and Society at Harvard University
- The Alexander von Humboldt Institute for Internet & Society
- The Centre for Internet and Society, Bangalore
- The Center for Technology & Society at the Fundacao Getulio Vargas Law School, Keio University
- The MIT Media Lab and its Center for Civic Media
- The NEXA Center for Internet & Society at Politicnico di Torino.
Individuals and researchers from the Centers focused on understanding the effects of internet and society. The participants were brought together to explore the past, present, and future tipping points of the internet, to identify knowledge gaps, and to find areas of collaboration and future action between institutes and individuals. Specifically, the symposium set out to examine fundamental questions about the internet, identify structural changes that are occurring because of the internet, and the forces that are catalyzing these changes. Questions asked and discussed included:
- What forces are changing production and service models?
- What forces are influencing entrepreneurship and innovation? and
- What forces are changing political participation?
Production and Service Models
Discussion
When participants discussed the changes that are happening to production and service models, concepts such as big data, algorithms, peer based models of production, and intermediaries were identified as actors and tools that are driving change in production and service models in the context of the internet. For example, big data and algorithms are being used to alter the nature, scope, and reach of business by allowing for the personalization and customization of services. To this end, many organizations have incorporated customer participation into business models, and provide platforms for feedback and input. The personalization of services has placed greater emphasis on the voice of the customer, allowing customers to guide and influence business by voicing preferences, satisfaction levels, etc. In this way, consumers can determine what type of service they want, and can also make political statements through their choices and feedback. In the process, however, such platforms generate and depend on large amounts of data and thus raise concerns about privacy.
Knowledge gaps that were identified during the conversation included how to predict what would make a participatory platform and peer based model successful, and how these platforms can be effectively researched. When looking at big data, a knowledge gap that was identified included how to ensure that data are collected ethically and accurately, as well as the related question: once large data sets are collected, how can the data be analyzed and used in a meaningful way?
There was also discussion about the increasingly critical and powerful role that intermediaries serve within the scope of the internet as they act as the platform provider and regulator for internet content. Intermediaries both allow for content to be posted on the internet, and determine what information is accessed through the filtering of web searches. Increasingly, governments are seeking to regulate intermediaries and create strict rules of compliance with governmental mandates. At the same time governments are placing the responsibility and liability of regulating what content is posted on internet on intermediaries, essentially placing them in the role of an adjudicator. This is one example of how the relationship between the private sector, the government, and the individual is changing, because it is only recently that private intermediaries have been held responsible first to governments, and only secondarily to customers.
Knowledge gaps identified in the discussion on intermediaries included understanding and researching how intermediaries decide to filter content found through searches. On what basis is each filter done? Are there actors influencing this process? And what are the economics behind the process?
Personal Thoughts
When reflecting on how the internet is changing and influencing the production of goods and services, I personally would add to the points discussed in the meeting the fact that the internet has also impacted the job economy. Reports show that jobs in the extraction and manufacturing sector are decreasing, as the internet has created a mandatory new tech oriented skill set that often outweighs the need for other skill sets. This change is far reaching as the job economy influences what skills students choose to learn, why and for what purposes individuals migrate across borders for employment, and in what industries governments invest money towards domestic development. In addition to changing the nature of skills in demand, the nature of the services themselves is changing. Though services are becoming more personalized and tailored to the individual, this personalization is automated, and replacing the ‘human touch’ that was once prized in business. Whether customers care if the service they are given is generated by an algorithm or delivered by an individual may depend on a person’s preference, but the European Union has seen this shift as being significant enough to address automated decision making in Article 15 of the EU directive, which provides individuals the right to not be subject to a decision which legally impacts him/her which is based only on automated processing of data. This directive encompasses decisions such as evaluation of a person’s performance at work, creditworthiness, reliability, conduct, etc.
The internet has also increased the cost of small mistakes made by businesses, as any mistake will now potentially impact millions of customers. The impact of any mistake makes risk management much more important and difficult, as businesses must seek to anticipate and mitigate any and all mistakes. The internet has also created a new level of dependency on the network, as businesses shift all of their services and functions over to the internet. Thus, if the network goes down, businesses will lose revenue and customers. This level of dependency on the network that exists today is different from past reliance’s on technology — in the sense that in the past there was not one single type of technology that would be essential for many businesses to run. The closest analogue was transportation: if trucks, trains, or ships were unavailable, multiple industries would be impacted. The difference is that those who relied on rail could shift temporarily to ships or trucks. Those relying on the network have no alternatives. Furthermore, past technologies were constantly evolving in the resources they depended on — from coal to gas, etc, but for the internet, it seems that the resource is not evolving, so much as expanding as increased bandwidth and connectivity are the solution to allowing technological evolution and innovation through the internet.
As discussed above, intermediaries are becoming key and powerful players, but they also seem to be increasingly placed between a rock and a hard place, as governments around the world are asking national and multinational intermediaries to filter content that violates national laws in one context, but not another context. Furthermore, intermediaries are increasingly being asked to comply with law enforcement requests for access to data that is often not within the jurisdiction of the requesting country. The difficult position intermediaries are placed in demonstrates how the architecture of the internet is borderless but the regulation and use of the internet is still tied to borders and jurisdiction.
Entrepreneurship and Innovation
Discussion
When discussing entrepreneurship and innovation it was pointed out by participants that grey markets and market failures are important indicators for possibilities of new business models and forms of innovation. Because of that, it is important to study what has failed and why when identifying new possibilities and trends. The importance of policies and laws that allow for innovation and entrepreneurship was also highlighted.
Personal Thoughts
When thinking about entrepreneurship and innovation on the internet and forces driving them, it seems clear that tethering, conglomerating, and organizing information from multiple sources is one direction that innovation is headed. Services are coming out that have the ability to search the internet based on individual preferences and provide more accurate data quickly. This removes the need for individuals to search the internet at length to find the information or products they want. Along the same lines, it seems that there is a greater trend towards personalization. Services are finding new and innovative ways to bring individuals customized products. Another trend is the digitization of all services — from moving libraries online, to bookstores online, to grocery stores online. Lastly, there is a constant demand for new applications to be developed. These can range from applications enabling communication through social networking, to applications that act as personal financial consultants, to applications that act as personal trainers. The ability for concepts, trends, etc to go viral on the internet has also added another dimension to entrepreneurship and innovation as any individual can potentially become successful by something going viral. The ability for something to go viral on the internet does not just impact entrepreneurship and innovation, but also impacts political participation and production and service models.
Political Participation
Discussions also centered on how political participation is changing as the internet is being used as a new platform for participation. For example, it is now possible for individuals to leverage their voice and message to local and global communities. Furthermore, this message can be communicated on a seemingly personal scale. Individuals from one community are able to connect to communities from another location — both local and abroad, and to work together to catalyze change. Messages and communications can be spread easily to millions of people and can go viral. This ability has changed and created new public spheres, where anyone can contribute to a dialogue from anywhere. Empowerment is shifting as well, because the internet allows for new power structures to be created by any actor who knows how to leverage the network. These factors allow for more voices to be heard and for greater citizen participation. The role of the youth in political movements was also emphasized in the discussions. On the other hand governments have responded by more heavily regulating speech and content on the internet when dissenting voices and campaigns are seen as a threat. It was also brought out that though emerging forms of online political participation have been heralded by many for achievements such as facilitating democracy, transparency, and bringing a voice to the silenced — many have warned that analysis of these political forms of participation overlook individual contributions and time. Other critiques that were discussed included the fact that digital revolutions also exclude individuals who do not have access to the internet or to platforms/applications and overlook actions and movements that take place offline.
Knowledge gaps that were identified included understanding the basics of the change that is happening in political participation through the internet. For example, it is unclear who the actors are that determine the conditions and scope for these changes, and like participatory forms of business, what enables and mobilizes change. Furthermore, it is unclear who specifically benefits from these changes and how, and who participates in the changes — and in what capacity. Additionally, much of the change has been quantified in the dialogue of the ‘global’ — global voices, global movements — but that dialogue ignores the local.
Personal Thoughts
In addition to the discussions on political participation, I believe the internet has created the possibility for ‘social governance’. To address situations in which there is no particular law against an action, but individuals come together and speak out against actions that they see on the internet that they believe should be stopped or changed. Depending on the extent individuals choose to enforce these decisions, this can be potentially dangerous as individuals are essentially rewriting laws and social norms without subjecting them to the crucible of consensus decision-making or review. In addition, forms of political participation are not changing just in terms of how the individual engages politically with states and governments, but also in the ways that politicians are engaging with citizens. For example, politicians are using Facebook and Twitter as means to communicate and gather feedback from supporters. Politicians are also using technology to reach more individuals with their messages — from experimenting with 3D holograms, to web casting, to using technology like CCTV cameras to prove transparency. The impact of this could be interesting, as technology is becoming a mediating tool that works in both directions between citizens and governments. Is this changing the traditional understandings of the State and the relationship between the State and the citizen?
Conclusion and ways forward
The discussions also pulled out dichotomies that apply to the internet and illustrate tensions arising from different forces. These dichotomies can be shaped by individuals and actors attempting to regulate the internet, as for example with new models of regulation vs. old models of regulation, private vs. public, local vs. global, owned vs. unowned, and zoned vs. unzoned. These dichotomies can be shaped by how the internet is used. For example, fair vs. unfair, just vs. unjust, represented vs. silenced, and uniform vs. diverse.
Common questions being asked and areas for potential research that came out of these discussions included information communication and media, how to address different and at times contradictory policies and levels of development in different countries, and what is the impact of big data on different sectors and industries like e-health and journalism? What is the importance of ICT in creating economic progress? How is the Internet changing the nature of democracy?
When discussing ways forward and areas for future collaboration it was brought out that exploring ways to leverage open data, ways to effectively use and build off of perspectives and experiences from other contexts and cultures, and ways to share resources across borders including funding, human presence, and expertise were important questions to answer. Common challenges that were identified by participants ranged from cyber security and the rise of state and non-state actors in cyber warfare, finding adequate funding to support research, sustaining international collaborations, ensuring that research is meaningful and can translate into useful resources for policy and law makers, and ensuring that projects are designed with a long-term objective and vision in mind.
The discussions, presentations, and contributions by participants during the two day symposium were interesting and important as they demonstrated just how multi-faced the internet is, and how it is never one dimensional. How the internet is researched, how it is used, and how it is regulated will be constantly changing. Whether this change is a step forward, or a re-invention of what has already been done, is up to all who use the internet including the individual, the corporation, the researcher, the policy maker, and the government.
The Worldwide Web of Concerns
Pranesh Prakash's column was published in the Deccan Chronicle on December 10, 2012.
Much has changed since the 1988 Melbourne conference. Since 1988, mobile telephony has grown by leaps and bounds, the Internet has expanded and the World Wide Web has come into existence.
Telecommunications is now, by and large, driven by the private sector and not by state monopolies.
While there are welcome proposals (consumer protection relating to billing of international roaming), there have also been contentious issues that Internet activists have raised: a) process-related problems with the ITU; b) scope of the ITRs, and of ITU’s authority; c) content-related proposals and “evil governments” clamping down on free speech; d) IP traffic routing and distribution of revenues.
Process-related problems: The ITU is a closed-door body with only governments having a voice, and only they and exorbitant fees-paying sector members have access to documents and proposals. Further, governments generally haven’t held public consultations before forming their positions. This lack of transparency and public participation is anathema to any form of global governance and is clearly one of the strongest points of Internet activists who’ve raised alarm bells over WCIT.
w Scope of ITRs: Most telecom regulators around the world distinguish between information services and telecom services, with regulators often not having authority over the former. A few countries even believe that the wide definition of telecommunications in the ITU constitution and the existing ITRs already covers certain aspects of the Internet, and contend that the revisions are in line with the ITU constitution. This view should be roundly rejected, while noting that there are some legitimate concerns about the shift of traditional telephony to IP-based networks and the ability of existing telecom regulations (such as those for mandatory emergency services) to cope with this shift.
ITU’s relationship with Internet governance has been complicated. In 1997, it was happy to take a hands-off approach, cooperating with Internet Society and others, only to seek a larger role in Internet governance soon after. In part this has been because the United States cocked a snook at the ITU and the world community in 1998 through the way it established Internet Corporation for Assigned Names and Numbers (ICANN) as a body to look after the Internet’s domain name system. While the fact that the US has oversight over ICANN needs to change (with de-nationalisation being the best option), Russia wants to supersede ICANN and that too through current revisions of the ITRs. Russia’s proposal is a dreadful idea, and must not just be discarded lightly but thrown away with great force. The ITU should remain but one among multiple equal stakeholders concerned with Internet governance.
One important, but relatively unnoticed, proposed change to ITU’s authority is that of making the standards that ITU’s technical wing churns out mandatory. This is a terrible idea (especially in view of the ITU’s track record at such standards) that only a stuffy bureaucrat without any real-world insight into standards adoption could have dreamt up.
Content-related proposals: Internet activists, especially US-based ones, have been most vocal about the spectre of undemocratic governments trying to control online speech through the ITRs. Their concerns are overblown, especially given that worse provisions already exist in the ITU’s constitution. A more real threat is that of increasing national regulation of the Internet and its subsequent balkanisation, and this is increasingly becoming reality even without revisions to the ITRs.
Having said that, we must ensure that issues like harmonisation of cyber-security and spam laws, which India has been pushing, should not come under ITU’s authority. A further worry is the increasing militarisation of cyberspace, and an appropriate space must be found by nation-states to address this pressing issue, without bringing it under the same umbrella as online protests by groups like Anonymous.
Division of revenue: Another set of proposals is being pushed by a group of European telecom companies hoping to revive their hard-hit industry. They want the ITU to regulate how payments are made for the flow of Internet traffic, and to prevent socalled “net neutrality” laws that aim to protect consumers and prevent monopolistic market abuse. They are concerned that the Googles and Facebooks of the world are free-riding on their investments. That all these companies pay to use networks just as all home users do, is conveniently forgotten. Thankfully, most countries don’t seem to be considering these proposals seriously.
Can general criteria be framed for judging these proposals? In submissions to the Indian government, the Centre for Internet and Society suggested that any proposed revision of the ITRs be considered favourably only if it passes all the following tests: if international regulation is required, rather than just national-level regulation (i.e., the principle of subsidiarity); if it is a technical issue limited to telecommunications networks and services, and their interoperability; if it is an issue that has to be decided exclusively at the level of nation-states; if the precautionary principle is satisfied; and if there is no better place than the ITRs to address that issue. If all of the above are satisfied, then it must be seen if it furthers substantive principles, such as equity and development, competition and prevention of monopolies, etc. If it does, then we should ask what kind of regulation is needed: whether it should be mandatory, whether it is the correct sort of intervention required to achieve the policy objectives.
The threat of a “UN takeover” of the Internet through the WCIT is non-existent. Since the ITU’s secretary-general is insisting on consensus (as is tradition) rather than voting, the possibility of bad proposals (of which there are many) going through is slim. However, that doesn’t mean that activists have been crying themselves hoarse in vain. That people around the world are a bit more aware about the linkage between the technical features of the Internet and its potential as a vehicle for free speech, commerce and development, is worth having to hear some shriller voices out there.
The writer is policy director at the Centre for Internet and Society, Bengaluru
Tomorrow, Today
Nishant Shah's end of the year column was published in the Indian Express on December 29, 2012.
And I find myself in a similar frame of mind, celebrating with joy the promises that were kept, reflecting sombrely on the opportunities we missed, and speculating about what the new year is going to bring in for the future of digital and internet technologies, and how they are going to change the ways in which we understand what it means to be human, to be social, and to be the political architects of our lives.
We all know that dramatic change is rare. Nothing transforms overnight, and a lot of what we can look forward to in the next year, is going to be contingent on how we have lived in this one. And yet, the rapid pace at which digital technologies change and morph, and the ways in which they produce new networked conditions of living, make it worthwhile to speculate on what are the top five things to look out for in 2013, when it comes to the internet and how it is going to affect our techno-social lives.
Head in the Cloud
If the last year was the year of the mobile, as more and more smartphones started penetrating societies, providing new conditions of portable and easy computing, making ‘app’ the word of the year, then the next year definitely promises to be the year of the cloud. As internet broadband and mobile data access become affordable, increasingly we are going to see services that no longer require personal computing power. All you will need is a screen and a Wi-Fi connection and everything else will happen in the cloud. No more hard drives, no more storage, no more disconnectivity, and data in the cloud.
More Talk
One of the biggest problems with the internet has been that it has been extremely text heavy. We often forget that the text is still a matter of privilege as questions of illiteracy and translation still hound a large section of the global population. However, with the new protocols of access, availability of 4G spectrum and the release of IPV6 as the new standard, we can expect faster voice and video-based communication at almost zero costs. It might be soon time to say goodbye to the SMS.
Big Data
You think you are suffering from information overload now? Wait for the next year as mobile and internet penetration are estimated to rise by 30 per cent around the world! This is going to be the year of Big Data — data so big that it can no longer be fathomed or understood by human beings. We will be dependent on machines to read it, process it, and show us patterns and trends because we are now at a point in our information societies where we are producing data faster than we can process it. Our governments, markets and societies are going to have to produce new ways of governing these data landscapes, leading to dramatic changes in notions of privacy, property and safety.
No Next Big Thing
If you haven’t noticed it, the pace of dramatic innovation has slowed down in the last few years and it will slow down even more. We have been riding the wave of the next big thing, in the last few years, constantly in search of new gadgets, platforms and ways of networking. However, the coming year is going to make innovation granular. It will be a year where things become better, and innovation happens behind the scene. So if you thought this was the year that Facebook will finally become obsolete and something else will take over, you might want to reconsider deleting your account, and start looking at the changes that shall happen behind the scenes, for better or for worse.
The Return of the Human
The rise of the social network has distracted us from looking at the human conditions. We have been so engaged in understanding friendship in the time of Facebook, analysing relationships, networked existences and our own performance as actors of information, that we haven’t given much thought to what it means to be human in our rapidly digitising worlds. And yet, the revolutions and the uprisings we have witnessed have been about people using these social networks to reinforce the ideas of equity, justice, inclusion, peace and rights across the world. As these processes strengthen and find new public spaces of collaboration, we will hopefully see social and political movements which reinforce, that at the end of the day, what really counts, is being human.
The future, specially in our superconnected times, is always unpredictable. But the rise of digital technologies has helped us revisit some of the problems that have been central to a lot of emerging societies — problems of inequity, injustice, violence and violation of rights. And here is hoping that the tech trends in the coming year, will be trends that help create a better version of today, tomorrow.
State Surveillance and Human Rights Camp: Summary
This research was undertaken as part of the 'SAFEGUARDS' project that CIS is undertaking with Privacy International and IDRC.
The camp also examined different types of data, understanding tools that governments can use to access data, and looked at examples of surveillance measures in different contexts. The camp was divided into plenary sessions and individual participatory workshops, and brought together activists, researchers, and experts from all over the world. Experiences from multiple countries were shared, with an emphasis on the experience of surveillance in Latin America. Among other things, this blog summarizes my understanding of the discussions that took place.
The camp also served as a platform for collaboration on the Draft International Principles on Communications Surveillance and Human Rights. These principles seek to set an international standard for safeguards to the surveillance of communications that recognizes and upholds human rights, and provide guidance for legislative changes related to communications and communications meta data to ensure that the use of modern communications technology does not violate individual privacy. The principles were first drafted in October 2012 in Brussels, and are still in draft form. A global consultation is taking place to bring in feedback and perspective on the principles.
The draft principles were institutionalized for a number of reasons including:
- Currently there are no principles or international best standards specifically prescribing necessary and important safeguards to surveillance of communication data.
- Practices around surveillance of communications by governments and the technology used by governments is rapidly changing, while legislation and safeguards protecting individual communications from illegal or disproportionate surveillance are staying the same, and thus rapidly becoming outdated.
- New legislation that allows surveillance through access to communication data that is being proposed often attempts to give sweeping powers to law enforcement for access to data across multiple jurisdictions, and mandates extensive cooperation and assistance from the private sector including extensive data retention policies, back doors, and built in monitoring capabilities.
- Surveillance of communications is often carried out with few safeguards in place including limited transparency to the public, and limited forms of appeal or redress for the individual.
This has placed the individual in a vulnerable position as opaque surveillance of communications is carried out by governments across the world — the abuse of which is unclear. The principles try to address these challenges by establishing standards and safeguards which should be upheld and incorporated into legislation and practices allowing the surveillance of communications.
A summary of the draft principles is below. As the principles are still a working draft, the most up to date version of the principles can be accessed here.
Summary of the Draft International Principles on Communications Surveillance and Human Rights
Legality: Any surveillance of communications undertaken by the government must be codified by statute.
Legitimate Purpose: Laws should only allow surveillance of communications for legitimate purposes.
Necessity: Laws allowing surveillance of communications should limit such measures to what is demonstrably necessary.
Adequacy: Surveillance of communications should only be undertaken to the extent that is adequate for fulfilling legitimate and necessary purposes.
Competent Authority: Any authorization for surveillance of communications must be made by a competent and independent authority.
Proportionality: All measures of surveillance of communications must be specific and proportionate to what is necessary to achieve a specific purpose.
Due process: Governments undertaking surveillance of communications must respect and guarantee an individual’s human rights. Any interference with an individual's human rights must be authorized by a law in force.
User notification: Governments undertaking surveillance of communications must allow service providers to notify individuals of any legal access that takes place related to their personal information.
Transparency about use of government surveillance: The governments ability to survey communications and the process for surveillance should be transparent to the public.
Oversight: Governments must establish an independent oversight mechanism to ensure transparency and accountability of lawful surveillance measures carried out on communications.
Integrity of communications and systems: In order to enable service providers to secure communications securely, governments cannot require service providers to build in surveillance or monitoring capabilities.
Safeguards for international cooperation: When governments work with other governments across borders to fight crime, the higher/highest standard should apply.
Safeguards against illegitimate access: Governments should provide sufficient penalties to dissuade against unwarranted surveillance of communications.
Cost of surveillance: The financial cost of the surveillance on communications should be borne by the government undertaking the surveillance.
Types of Data
The conversations during the camp reviewed a number of practices related to surveillance of communications, and emphasized the importance of establishing the draft principles. Setting the background to various surveillance measures that can be carried out by the government, the different categories of communication data that can be easily accessed by governments and law enforcement were discussed. For example, law enforcement frequently accesses information such as IP address, account name and number, telephone number, transactional records, and location data. This data can be understood as 'non-content' data or communication data, and in many jurisdictions can easily be accessed by law enforcement/governments, as the requirements for accessing communication data are lower than the requirements for accessing the actual content of communications. For example, in the United States a court order is not needed to access communication data whereas a judicial order is needed to access the content of communications.[1]
Similarly, in the UK law enforcement can access communication data with authorization from a senior police officer.[2]
It was discussed how it is concerning that communication data can be accessed easily, as it provides a plethora of facts about an individual. Given the sensitivity of communication data and the ability for personal information to be derived from the data, the ease that law enforcement is accessing the data, and the unawareness of the individual about the access- places the privacy of users at risk.
Ways of Accessing Data
Ways in which governments and law enforcement access information and associated challenges was discussed, both in terms of the legislation that allows for access and the technology that is used for access.
Access and Technology
In this discussion it was pointed out that in traditional forms of accessing data governments are no longer effective for a number of reasons. For example, in many cases communications and transactions, etc., that take place on the internet are encrypted. The ubiquitous use of encryption means more protection for the individual in everyday use of the internet, but serves as an obstacle to law enforcement and governments, as the content of a message is even more difficult to access. Thus, law enforcement and governments are using technologies like commercial surveillance software, targeted hacking, and malware to survey individuals. The software is sold off the shelf at trade shows by commercial software companies to law enforcement and governments. Though the software has been developed to be a useful tool for governments, it was found that in some cases it has been abused by authoritarian regimes. For example in 2012, it was found that FinSpy, a computer espionage software made by the British company Gamma Group was being used to target political dissidents by the Government of Bahrain. FinSpy has the ability to capture computer screen shots, record Skype chats, turn on computer cameras and microphones, and log keystrokes.[3]
In order to intercept communications or block access to sites, governments and ISPs also rely on the use of deep packet inspection (DPI).[4] Deep packet inspection is a tool traditionally used by internet service providers for effective management of the network. DPI allows for ISP's to monitor and filter data flowing through the network by inspecting the header of a packet of data and the content of the packet.[5] With this information it is possible to read the actual content of packets, and identify the program or service being used.[6]
DPI can be used for the detection of viruses, spam, unfair use of bandwidth, and copyright enforcement. At the same time, DPI can allow for the possibility of unauthorized data mining and real time interception to take place, and can be used to block internet traffic whether it is encrypted or not.[7]
Governmental requirements for deep packet inspection can in some cases be found in legislation and policy. In other cases it is not clear if it is mandatory for ISP's to provide DPI capabilities, thus the use of DPI by governments is often an opaque area. Recently, the ITU has sought to define an international standard for deep packet inspection known as the "Y.2770" standard. The standard proposes a technical interoperable protocol for deep packet inspection systems, which would be applicable to "application identification, flow identification, and inspected traffic types".[8]
Access and Legislation
The discussions also examined similarities across legislation and policy which allows governments legal access to data. It was pointed out that legislation providing access to different types of data is increasingly becoming outdated, and is unable to distinguish between communications data and personal data. Thus, relevant legislation is often based on inaccurate and outdated assumptions about what information would be useful and what types of safeguards are necessary. For example, it was discussed how US surveillance law has traditionally established safeguards based on assumptions like: surveillance of data on a personal computer is more invasive than access to data stored in the cloud, real-time surveillance is more invasive than access to stored data, surveillance of newer communications is more invasive than surveillance of older communications, etc. These assumptions are no longer valid as information stored in the cloud, surveillance of older communications, and surveillance of stored data can be more invasive than access to newer communications, etc. It was also discussed that increasingly relevant legislation also contains provisions that have generic access standards, unclear authorization processes, and provide broad circumstances in which communication data and content can be accessed. The discussion also examined how governments are beginning to put in place mandatory and extensive data retention plans as tools of surveillance. These data retention mandates highlight the changing role of internet intermediaries including the fact that they are no longer independent from political pressure, and no longer have the ability to easily protect clients from unauthorized surveillance.
1]. EFF. Mandatory Data Retention: United States. Available at: https://www.eff.org/issues/mandatory-data-retention/us
[2].Espiner, T. Communications Data Bill: Need to Know. ZDNet. June 18th 2012. http://www.zdnet.com/communications-data-bill-need-to-know-3040155406/
[3]. Perlroth, M. Software Meant to Fight Crime is Used to Spy on Dissidents. The New York Times. August 30th 2012. Available at: http://www.nytimes.com/2012/08/31/technology/finspy-software-is-tracking-political-dissidents.html?_r=0
[4]. Wawro, A. What is Deep Packet Inspection?. PCWorld. February 1st 2012. Available at: http://www.pcworld.com/article/249137/what_is_deep_packet_inspection_.html
[5]. Geere, D. How deep packet inspection works. Wired. April 27th 2012. Available at: http://www.wired.co.uk/news/archive/2012-04/27/how-deep-packet-inspection-works
[6]. Kassner. M. Deep Packet Inspection: What You Need to Know. Tech Republic. July 27th 2008. Available at: http://www.techrepublic.com/blog/networking/deep-packet-inspection-what-you-need-to-know/609
[7]. Anonyproz. How to Bypass Deep Packet Inspection Devices or ISPs Blocking Open VPN Traffic. Available at: http://www.anonyproz.com/supportsuite/index.php?_m=knowledgebase&_a=viewarticle&kbarticleid=138
[8].Chirgwin. R. Revealed: ITU's deep packet snooping standard leaks online: Boring tech doc or Internet eating monster. The Register. December 6th 2012. Available at: http://www.theregister.co.uk/2012/12/06/dpi_standard_leaked/
Mining the Web Collective
While the context of this workshop focussed on deciphering and mapping opinions related to academic controversies surrounding climate change, the very same techniques of deploying digital tools to crawl through associated content on the websphere, maybe used to map any other controversy that has been actively influencing public and political opinion.
As one of the participants in the workshop, in an attempt to make my interpretation as accessible as possible to a wider inter-disciplinary audience, below is my own assimilation and extrapolation of the musings and discussions that entailed. Further I have drawn out limitations and future directions towards more viable paradigms that augment the mapping and democratization of public opinion.
The session drew an outset around how new digital tools could aid researchers by enabling them to quickly see an individual entity’s data as well as it’s associated aggregates, and register all of this within a single view in real-time. Contrasting the traditional methods of data collection through individual surveys, new digital methods can almost instantaneously bridge the gap between the individual and the collective and help us answer the question that Latour poses in his most recent paper that revisits social theory around the Tardean concept of reciprocally connected ‘monads’ -- ''.... is there an alternative to the common sense version that distinguishes atoms, interactions and wholes as successive sequences (whatever the order and the timing)? An alternative that should not oblige the inquirer to change gears from the micro to the macro levels ..... but remains fully continuous ...'' [Latour et al , 2012].
Encompassing the Collective
The geometric basis of the universe as expressed by Edgar Allan Poe, asserts that the ‘universe.. is a sphere of which the centre is everywhere and circumference nowhere’ (Eureka, p 20) This is essentially a post-Euclidean conception of space, in line with the view of early 20th century physicist Alexander Friedmann who posits that the ‘universe is not finite in space, but neither does space have any boundary’ and so the centre of the universe is relative to every single atom — hence every single observer.
In many ways, the process of data collection and visualization that was carried out at the workshop tried at best to mimic this geometric basis of space. By starting with a single entity (say, mammals) the empiricist begins with nothing more than a named 'label'. One then extends the specification of this entity, by populating a list with an increasing number of elements. This process of 'learning' about an entity is essentially an infinite process, as many abstract associations maybe permitted to enter the list. However, the observer stops this iterative process at a point when he feels that he has enough knowledge to describe the entity within the (seemingly finite) 'scope' of study. What we then have is a highly individualized point of view with respect to one entity that has a view of all it's associated attributes.
It is worth noting here that the attributes themselves can be looked at as individualized entities, and vice versa, from their own view point, depending on the way in which one navigates, thereby making the map invertible. For instance while 'egg-laying' maybe one of the attributes of a 'mammal', if we navigated to define 'egg-laying' to be our starting entity, it's view point can contain attributes like 'mammals' and 'birds'. This process is entirely different from the bottom up approach of constructing a general view by combining individual counterparts. In fact, there is no one general view here, as the picture is an exploded graph emanating from a single entity's view point, each to it's own 'umwelt'.[Kaveli et al, 2010].
(Re)formation of Opinion
The formation of a fundamental percept in the human brain, for instance, during the cognitive activity of reading a text, is in itself a bottom-up serial process where individual words progressively make up semantic associations to form a meaningful structure (just as this sentence), along with contextual association with previously acquired knowledge. This capacity limit for information processing [Rene and Ivanoff, 2005] which is a prerequisite for our highly focussed mechanism of attention is the reason why we cannot capture the entire star map within a single glance at the night sky.
Somewhere down this iterative line of observing an entity, and not having access to all of its attributes in entirety, leads to over-specification and an entanglement with isolated systems, thereby falling into a local maxima as opposed to a global solution. This is the basis of opinion formation and by envisaging it as a 'closed' object it is transformed into a percept, open to interpretation and often conflicting with another, thereby resulting in a controversy.
One of the objectives of the controversy mapping workshop was to transform the 'immutable' percept surrounding a controversy into a visual map that all at once registers weblinked attributes surrounding it, to give us a possibly emergent and unbiased picture.
The Method to the Madness
The process of framing of a ‘controversial topic’ and the collation of massive data and links on the internet that surround the topic could indeed be a cumbersome task. An informed approach is thus required in order to achieve a meaningful result.
Firstly, one needs to consider reliable sources and means of knowledge production that provide enough fuel to kindle the analysis of the controversy. One needs to move on from casual matters of opinion or statements (such as “the cumulative effects of CFC result in ozone layer depletion”) to identifying a hypothesis or theory that is being actively contested by academicians and experts through research and publication. This serves to outline an important preliminary sketch of the controversy that exists within the community.
Secondly, it is essential to remember that specialized researchers do not exist in self-centered isolation but often operate in tandem with multiple stakeholders, investors, donors, sponsors and a diverse audience that they cater to through articles, books, research projects and published journals. For instance, several theorists who are into the business of developing a so-called ‘language of critique’ often ensure through working group meetings that a selected group of researchers are on the ‘same page’ while using common words to canvass a spearhead towards prospective calls from popular journals. At other times, one may perceive a very direct link between mainstream press and cutting-edge research. This group comprising allies and endorsers are an important constituent of the mapping process as they provide key points of entry into the controversy.
Further, as more and more data relating to a controversy is accrued, one must decipher not only how the position of the controversy is being dynamically shaped over time along with its stakeholders but also be able to extrapolate how and why its current position of uncertainty might evolve. This would involve identifying potential points of contention that could respark a debate over an issue that has reached near closure.
Mapping the Controversy around ‘Anthropocene’
 |
|---|
The topic chosen by my group (which consisted of scholars Neesha Dutt, Muthatha Ramanathan and Prasanna Kolte) was ‘Anthropocene’, a geo-chronological term that was informally introduced by a Nobel laureate in the field of atmospheric chemistry, Paul Crutzen, at a dinner party. ‘Anthropocene’ apparently marks the post industrial period as a time window that represents the impact that human activities have had on earth’s ecological systems, thereby affecting climate change. The widespread acceptance and popularity of the the word has even seen a move to officially recognize ‘Anthropocene’ as geological unit of time, complemented by a number of dubious research projects that assume the ‘anthropocenic’ view of climate change. The tools used were Navicrawler to populate a massive list of webpages that featured the keyword and other landing websites that each of the webpages point to. The context of the websites based on their content were labelled manually and no native text parsing and analysis was used. An interconnected visual graph structure was then obtained using Gephi, a software that uses Force Layout -2 , a graph layout algorithm for network visualization. [M. Bastian et al, 2009].
Future Directions
Including a layer of geographical representation to the formation and spread of an opinion is a key direction towards which opinion mining and controversy mapping is headed. A limiting factor while crawling articles over the web using currently available digital tools is the inaccurate representation of geographical source. An article posted in a popular science blog in India, may actually have its server hosted in California and this fact may often be abstracted to our crawler.
Furthermore, apart from the geographical source of a web article, an interesting direction would be to employ geo-located public opinion interfaces to collect a sample set of public opinion related to an issue, across diverse geographical locations in realtime. This would serve as valuable layer to overlay onto the controversy web map.
Another constraint of the digital methods referred to here within, is the medium specific approach that does not look beyond the sample space of the internet. Listening to and analyzing internet social media dynamics and combing large data sets to churn out a report is not much of a challenge. Cross media influences in public and political opinion have become increasingly clear with television broadcasts and newspaper reports directly contributing to discussions that happen on internet forums and websites. Take for instance Blue Fin Labs that started off within the Cognitive Machines group of MIT Media Lab. Initially known as the Human Speechome project which used deep machine learning algorithms to map out relationships between spoken word and context, Blue Fin Labs now applies the same technique to map internet comments and posts to corresponding audio-visual stimuli in television broadcasts that caused those comments to be made on the web.
Video
Data visualization of connecting the social graph to the TV content graph
References
- Cappi, Alberto (1994). "Edgar Allan Poe's Physical Cosmology". The Quarterly Journal of the Royal Astronomical Society 35: 177–192
- Castells, M. (2000). Materials for an exploratory theory of the network society. British Journal of Sociology Vol. No. 51 Issue No. 1 (January/March 2000).
- Edgar Allen Poe (1848) ‘Eureka : A Prose Poem'.
- Kull, Kaveli 2010. Umwelt. In: Cobley, Paul (ed.), The Routledge Companion to Semiotics. London: Routledge, 348–349.
- Latour, B. et al 2012 “The Whole is Always Smaller Than It’s Parts A Digital Test of Gabriel Tarde’s Monads” British Journal of Sociology (forthcoming)http://www.bruno-latour.fr/sites/default/files/123-WHOLE-PART-FINAL.pdf
- M. Bastian, S. Heymann, and M. Jacomy, “Gephi: an open source software for exploring and manipulating networks,” in International AAAI Conference on Weblogs and Social Media. Association for the Advancement of Artificial Intelligence, 2009.
- M. E. J. Newman, “Analysis of weighted networks,” 2004, arxiv:cond-mat/0407503.
- Reynolds, C. W. (1987) Flocks, Herds, and Schools: A Distributed Behavioral Model, in Computer Graphics, 21(4) (SIGGRAPH '87 Conference Proceedings) pp. 25-34.
- Rene Marois and Jason Ivanoff, Capacity limits of information processing in the brain, TRENDS in Cognitive Sciences Vol.9 No.6 June 2005
- T. M. J. Fruchterman and E. M. Reingold, “Graph drawing by force-directed placement,” Softw: Pract. Exper., vol. 21 no. 11, pp. 1129–1164, Nov. 1991.
No Civil Society Members in the Cyber Regulations Advisory Committee
In multiple op-eds (Indian Express and Mint), I have pointed out the need for the government to reconstitute the "Cyber Regulations Advisory Committee" (CRAC) under section 88 of the Information Technology Act. That it be reconstituted along the model of the Brazilian Internet Steering Committee was also part of the suggestions that CIS sent to the government after a meeting FICCI had convened along with the government on September 4, 2012.
Section 88 requires that people "representing the interests principally affected" by Internet policy or "having special knowledge of the subject matter" be present in this advisory body. The main function of the CRAC is to advise the the Central Government "either generally as regards any rules or for any other purpose connected with this Act".
Despite this important function, the CRAC had — till November 2012 — only ever met twice, both times in 2001. The response to an RTI informed us that the body had never provided any advice to the government.
Government Not Serious
The increasing pressure on the government for botching up Internet regulations has led it to reconstitute the CRAC. However, the list of members of the committee shows that the government is not serious about this committee representing "the interests primarily affected" by Internet policy.
Importantly, this goes against the express wish of the Shri Kapil Sibal, the Union Minister for Communications and IT, who has repeatedly stated that he believes that Internet-related policymaking should be an inclusive process. Most recently, at the 2012 Internet Governance Forum he stated that we need systems that are:
"collaborative, consultative, inclusive and consensual, for dealing with all public policies involving the Internet"
Interestingly, despite the Hon'ble Minster verbally inviting civil society organizations (on November 23, 2012) for a meeting of the CRAC that happened on November 25, 2012, the Department of Electronics and Information Technology refused to send us invitations for the meeting. This hints at a disconnect between the political and bureaucratic wings of the government, at least at some levels.
Interestingly, this isn't the first time this has been pointed out. Na. Vijayashankar was levelling similar criticisms against the CRAC way back in August 2000 when the original CRAC was constituted.
Breakdown by Stakeholder Groupings
While there is no one universal division of stakeholders in Internet governance, but four goups are widely recognized: governments (national and intergovernmental), industry, technical community, and civil society. Using that division, we get:
- Government - 15 out of 22 members
- Industry bodies - 6 out of 22 members
- Technical community / Academia - 1 out of 22 members
- Civil society - 0 out of 22 members.
List of Members of Cyber Regulatory Advisory Committee
The official notification (G.S.R. 827(E)) is available on the DEIT website and came into force on November 16, 2012.
(Note: Names with strikethroughs have been removed from the CRAC since 2000, and those with emphasis have been added.)
- Minister, Ministry of Communication and Information Technology - Chairman
- Minister of State, Ministry of Communications and Information Technology - Member
- Secretary, Ministry of Communication and Information Technology, Department of Electronics and Information Technology - Member
- Secretary, Department of Telecommunications - Member
Finance Secretary - Member - Secretary, Legislative Department - Member
- Secretary, Department of Legal Affairs - Member
Shri T.K. Vishwanathan, Presently Member Secretary, Law Commission - Member - Secretary, Ministry of Commerce - Member
- Secretary, Ministry of Home Affairs - Member
- Secretary, Ministry of Defence - Member
- Deputy Governor, Reserve Bank of India - Member
- Information Technology Secretary from the states by rotation - Member
- Director, IIT by rotation from the IITs - Member
- Director General of Police from the States by rotation - Member
- President, NASSCOM - Member
- President, Internet Service Provider Association - Member
- Director, Central Bureau of Investigation - Member
- Controller of Certifying Authority - Member
- Representative of CII - Member
- Representative of FICCI - Member
- Representative of ASSOCHAM - Member
- President, Computer Society of India - Member
- Group Coordinator, Department of Electronic and Information Technology - Member Secretary
7th India Digital Summit 2013
 Agenda-2.pdf
—
PDF document,
963 kB (986588 bytes)
Agenda-2.pdf
—
PDF document,
963 kB (986588 bytes)
Draft International Principles on Communications Surveillance and Human Rights
The principles are still in draft form. The most recent version can be accessed here. This research was undertaken as part of the 'SAFEGUARDS' project that CIS is undertaking with Privacy International and IDRC.
Our goal is that these principles will provide civil society groups, industry, and governments with a framework against which we can evaluate whether current or proposed surveillance laws and practices are consistent with human rights. We are concerned that governments are failing to develop legal frameworks to adhere to international human rights and adequately protect communications privacy, particularly in light of innovations in surveillance laws and techniques.
These principles are the outcome of a consultation with experts from civil society groups and industry across the world. It began with a meeting in Brussels in October 2012 to address shared concerns relating to the global expansion of government access to communications. Since the Brussels meeting we have conducted further consultations with international experts in communications surveillance law, policy and technology.[1]
We are now launching a global consultation on these principles. Please send us comments and suggestions by January 3rd 2013, by emailing rights (at) eff (dot) org.
Preamble
Privacy is a fundamental human right, and is central to the maintenance of democratic societies. It is essential to human dignity and it reinforces other rights, such as freedom of expression and association, and is recognised under international human rights law.[2] Activities that infringe on the right to privacy, including the surveillance of personal communications by public authorities, can only be justified where they are necessary for a legitimate aim, strictly proportionate, and prescribed by law.[3]
Before public adoption of the Internet, well-established legal principles and logistical burdens inherent in monitoring communications generally limited access to personal communications by public authorities. In recent decades, those logistical barriers to mass surveillance have decreased significantly. The explosion of digital communications content and information about communications, or “communications metadata”, the falling cost of storing and mining large sets of data, and the commitment of personal content to third party service providers make surveillance possible at an unprecedented scale.[4]
While it is universally accepted that access to communications content must only occur in exceptional situations, the frequency with which public authorities are seeking access to information about an individual’s communications or use of electronic devices is rising dramatically—without adequate scrutiny. [5] When accessed and analysed, communications metadata may create a profile of an individual's private life, including medical conditions, political and religious viewpoints, interactions and interests, disclosing even greater detail than would be discernible from the content of a communication alone. [6] Despite this, legislative and policy instruments often afford communications metadata a lower level of protection and do not place sufficient restrictions on how they can be subsequently used by agencies, including how they are data-mined, shared, and retained.
It is therefore necessary that governments, international organisations, civil society and private service providers articulate principles establishing the minimum necessary level of protection for digital communications and communications metadata (collectively "information") to match the goals articulated in international instruments on human rights— including a democratic society governed by the rule of law. The purpose of these principles is to:
- Provide guidance for legislative changes and advancements related to communications and communications metadata to ensure that pervasive use of modern communications technology does not result in an erosion of privacy.
- Establish appropriate safeguards to regulate access by public authorities (government agencies, departments, intelligence services or law enforcement agencies) to communications and communications metadata about an individual’s use of an electronic service or communication media.
We call on governments to establish stronger protections as required by their constitutions and human rights obligations, or as they recognize that technological changes or other factors require increased protection.
These principles focus primarily on rights to be asserted against state surveillance activities. We note that governments are required not only to respect human rights in their own conduct, but to protect and promote the human rights of individuals in general.[7] Companies are required to follow data protection rules and yet are also compelled to respond to lawful requests. Like other initiatives,[8] we hope to provide some clarity by providing the below principles on how state surveillance laws must protect human rights.
The Principles
Legality: Any limitation to the right to privacy must be prescribed by law. Neither the Executive nor the Judiciary may adopt or implement a measure that interferes with the right to privacy without a previous act by the Legislature that results from a comprehensive and participatory process. Given the rate of technological change, laws enabling limitations on the right to privacy should be subject to periodic review by means of a participatory legislative or regulatory process
Legitimate Purpose: Laws should only allow access to communications or communications metadata by authorised public authorities for investigative purposes and in pursuit of a legitimate purpose, consistent with a free and democratic society.
Necessity: Laws allowing access to communications or communications metadata by authorised public authorities should limit such access to that which is strictly and demonstrably necessary, in the sense that an overwhelmingly positive justification exists, and justifiable in a democratic society in order for the authority to pursue its legitimate purposes, and which the authority would otherwise be unable to pursue. The onus of establishing this justification, in judicial as well as in legislative processes, is on the government.
Adequacy: Public authorities should restrain themselves from adopting or implementing any measure of intrusion allowing access to communications or communications metadata that is not appropriate for fulfillment of the legitimate purpose that justified establishing that measure.
Competent Authority: Authorities capable of making determinations relating to communications or communications metadata must be competent and must act with independence and have adequate resources in exercising the functions assigned to them.
Proportionality: Public authorities should only order the preservation and access to specifically identified, targeted communications or communications metadata on a case-by-case basis, under a specified legal basis. Competent authorities must ensure that all formal requirements are fulfilled and must determine the validity of each specific attempt to access or receive communications or communications metadata, and that each attempt is proportionate in relation to the specific purposes of the case at hand. Communications and communications metadata are inherently sensitive and their acquisition should be regarded as highly intrusive. As such, requests should at a minimum establish a) that there is a very high degree of probability that a serious crime has been or will be committed; b) and that evidence of such a crime would be found by accessing the communications or communications metadata sought; c) other less invasive investigative techniques have been exhausted; and d) that a plan to ensure that the information collected will be only that information reasonably related to the crime and that any excess information collected will be promptly destroyed or returned. Neither the scope of information types, the number or type of persons whose information is sought, the amount of data sought, the retention of that data held by the authorities, nor the level of secrecy afforded to the request should go beyond what is demonstrably necessary to achieve a specific investigation.
Due process: Due process requires that governments must respect and guarantee an individual’s human rights, that any interference with such rights must be authorised in law, and that the lawful procedure that governs how the government can interfere with those rights is properly enumerated and available to the general public.[9]While criminal investigations and other considerations of public security and safety may warrant limited access to information by public authorities, the granting of such access must be subject to guarantees of procedural fairness. Every request for access should be subject to prior authorisation by a competent authority, except when there is imminent risk of danger to human life. [10]
User notification: Notwithstanding the notification and transparency requirements that governments should bear, service providers should notify a user that a public authority has requested his or her communications or communications metadata with enough time and information about the request so that a user may challenge the request. In specific cases where the public authority wishes to delay the notification of the affected user or in an emergency situation where sufficient time may not be reasonable, the authority should be obliged to demonstrate that such notification would jeopardize the course of investigation to the competent judicial authority reviewing the request. In such cases, it is the responsibility of the public authority to notify the individual affected and the service provider as soon as the risk is lifted or after the conclusion of the investigation, whichever is sooner.
Transparency about use of government surveillance: The access capabilities of public authorities and the process for access should be prescribed by law and should be transparent to the public. The government and service providers should provide the maximum possible transparency about the access by public authorities without imperiling ongoing investigations, and with enough information so that individuals have sufficient knowledge to fully comprehend the scope and nature of the law, and when relevant, challenge it. Service providers must also publish the procedure they apply to deal with data requests from public authorities.
Oversight: An independent oversight mechanism should be established to ensure transparency of lawful access requests. This mechanism should have the authority to access information about public authorities' actions, including, where appropriate, access to secret or classified information, to assess whether public authorities are making legitimate use of their lawful capabilities, and to publish regular reports and data relevant to lawful access. This is in addition to any oversight already provided through another branch of government such as parliament or a judicial authority. This mechanism must provide – at a minimum – aggregate information on the number of requests, the number of requests that were rejected, and a specification of the number of requests per service provider and per type of crime. [11]
Integrity of communications and systems: It is the responsibility of service providers to transmit and store communications and communications metadata securely and to a degree that is minimally necessary for operation. It is essential that new communications technologies incorporate security and privacy in the design phases. In order, in part, to ensure the integrity of the service providers’ systems, and in recognition of the fact that compromising security for government purposes almost always compromises security more generally, governments shall not compel service providers to build surveillance or monitoring capability into their systems. Nor shall governments require that these systems be designed to collect or retain particular information purely for law enforcement or surveillance purposes. Moreover, a priori data retention or collection should never be required of service providers and orders for communications and communications metadata preservation must be decided on a case-by-case basis. Finally, present capabilities should be subject to audit by an independent public oversight body.
Safeguards for international cooperation: In response to changes in the flows of information and the technologies and services that are now used to communicate, governments may have to work across borders to fight crime. Mutual legal assistance treaties (MLATs) should ensure that, where the laws of more than one state could apply to communications and communications metadata, the higher/highest of the available standards should be applied to the data. Mutual legal assistance processes and how they are used should also be clearly documented and open to the public. The processes should distinguish between when law enforcement agencies can collaborate for purposes of intelligence as opposed to sharing actual evidence. Moreover, governments cannot use international cooperation as a means to surveil people in ways that would be unlawful under their own laws. States must verify that the data collected or supplied, and the mode of analysis under MLAT, is in fact limited to what is permitted. In the absence of an MLAT, service providers should not respond to requests of the government of a particular country requesting information of users if the requests do not include the same safeguards as providers would require from domestic authorities, and the safeguards do not match these principles.
Safeguards against illegitimate access: To protect individuals against unwarranted attempts to access communications and communications metadata, governments should ensure that those authorities and organisations who initiate, or are complicit in, unnecessary, disproportionate or extra-legal interception or access are subject to sufficient and significant dissuasive penalties, including protection and rewards for whistleblowers, and that individuals affected by such activities are able to access avenues for redress. Any information obtained in a manner that is inconsistent with these principles is inadmissible as evidence in any proceeding, as is any evidence derivative of such information.
Cost of surveillance: The financial cost of providing access to user data should be borne by the public authority undertaking the investigation. Financial constraints place an institutional check on the overuse of orders, but the payments should not exceed the service provider’s actual costs for reviewing and responding to orders, as such would provide a perverse financial incentive in opposition to user’s rights.
Signatories
Organisations
- Article 19 (International)
- Bits of Freedom (Netherlands)
- Center for Internet & Society India (CIS India)
- Derechos Digitales (Chile)
- Electronic Frontier Foundation (International)
- Privacy International (International)
- Samuelson-Glushko Canadian Internet Policy and Public Interest Clinic (Canada)
- Statewatch (UK)
Individuals
- Renata Avila, human rights lawyer (Guatemala)
Footnotes
[1]For more information about the background to these principles and the process undertaken, see https://www.privacyinternational.org/blog/towards-international-principles-on-communications-surveillance
[2]Universal Declaration of Human Rights Article 12, United Nations Convention on Migrant Workers Article 14, UN Convention of the Protection of the Child Article 16, International Covenant on Civil and Political Rights, International Covenant on Civil and Political Rights Article 17; regional conventions including Article 10 of the African Charter on the Rights and Welfare of the Child, Article 11 of the American Convention on Human Rights, Article 4 of the African Union Principles on Freedom of Expression, Article 5 of the American Declaration of the Rights and Duties of Man, Article 21 of the Arab Charter on Human Rights, and Article 8 of the European Convention for the Protection of Human Rights and Fundamental Freedoms; Johannesburg Principles on National Security, Free Expression and Access to Information, Camden Principles on Freedom of Expression and Equality.
[3]Martin Scheinin, “Report of the Special Rapporteur on the promotion and protection of human rights and fundamental freedoms while countering terrorism,” p11, available at http://www2.ohchr.org/english/issues/terrorism/rapporteur/docs/A_HRC_13_37_AEV.pdf. See also General Comments No. 27, Adopted by The Human Rights Committee Under Article 40, Paragraph 4, Of The International Covenant On Civil And Political Rights, CCPR/C/21/Rev.1/Add.9, November 2, 1999, available at http://www.unhchr.ch/tbs/doc.nsf/0/6c76e1b8ee1710e380256824005a10a9?Opendocument.
[4]Communications metadata may include information about our identities (subscriber information, device information), interests, including medical conditions, political and religious viewpoints (websites visited, books and other materials read, watched or listened to, searches conducted, resources used), interactions (origins and destinations of communications, people interacted with, friends, family, acquaintances), location (places and times, proximities to others); in sum, logs of nearly every action in modern life, our mental states, interests, intentions, and our innermost thoughts.
[5]For example, in the United Kingdom alone, there are now approximately 500,000 requests for communications metadata every year, currently under a self-authorising regime for law enforcement agencies, who are able to authorise their own requests for access to information held by service providers. Meanwhile, data provided by Google’s Transparency reports shows that requests for user data from the U.S. alone rose from 8888 in 2010 to 12,271 in 2011.
[6]See as examples, a review of Sandy Petland’s work, ‘Reality Mining’, in MIT’s Technology Review, 2008, available at http://www2.technologyreview.com/article/409598/tr10-reality-mining/ and also see Alberto Escudero-Pascual and Gus Hosein, ‘Questioning lawful access to traffic data’, Communications of the ACM, Volume 47 Issue 3, March 2004, pages 77 - 82.
[7]Report of the UN Special Rapporteur on the promotion and protection of the right to freedom of opinion and expression, Frank La Rue, May 16 2011, available at http://www2.ohchr.org/english/bodies/hrcouncil/docs/17session/a.hrc.17.27_en.pdf
[8]The Global Network Initiative establishes standards to help the ICT sector protect the privacy and free expression of their users. See http://www.globalnetworkinitiative.org/
[9]As defined by international and regional conventions mentioned above.
[10]Where judicial review is waived in such emergency cases, a warrant must be retroactively sought within 24 hours.
[11]One example of such a report is the US Wiretap report, published by the US Court service. Unfortunately this applies only to interception of communications, and not to access to communications metadata. See http://www.uscourts.gov/Statistics/WiretapReports/WiretapReport2011.aspx. The UK Interception of Communications Commissioner publishes a report that includes some aggregate data but it is does not provide sufficient data to scrutinise the types of requests, the extent of each access request, the purpose of the requests, and the scrutiny applied to them. See http://www.intelligencecommissioners.com/sections.asp?sectionID=2&type=top.
Statement of Solidarity on Freedom of Expression and Safety of Internet Users in Bangladesh
Bangladeshi blogger Asif Mohiuddin was brutally attacked in a stabbing last evening. His condition is currently said to be critical. Violent attacks on mediapersons have led to at least four deaths in the past year. This trend is now extending to those writing online.
It is the duty of societies at large to ensure that principles we universally consider sacrosanct, such as the right to life and liberty and of freedom of expression are in fact ideas, and of the government to actively protect the rights guaranteed under the Constitution of Bangladesh and to ensure they are not just words on paper.
Article 39 of the Constitution of Bangladesh—and Article 19 of the Universal Declaration of Human Rights—guarantee both the freedom of thought and conscience, as well as the right of every citizen of freedom of speech and expression, and freedom of the press.
Article 32 of the Constitution of Bangladesh—and Article 3 of the Universal Declaration of Human Rights—guarantee that no person shall be deprived of life or personal liberty except by law.
The attack on Asif Mohiuddin constitutes a violation these fundamental principle by criminals, and we request the government to act decisively to show it will not tolerate such violations.
Reporters Without Borders note that "the ability of those in the media to work freely has deteriorated alarmingly in Bangladesh, which is now ranked 129th of 179 countries in the 2011-2012 World Press Freedom Index".
In general, the situation of those working as non-professional 'citizen journalists' is even worse. In a 2010 report, the UN Special Rapporteur wrote:
"Citizen journalists are by nature more isolated, they are more vulnerable to attack than professional journalists. However, citizen journalists enjoy less protection than their counterparts in traditional media, as they do not have the support of media organizations and networks, in particular the organizational resources, including lawyers and financial resources, which can help shield them from harassment."This reality of greater vulnerability is equally applicable to those who do not self-identify as 'citizen journalists', but use social media to express unpopular opinions.
Keeping this in mind, we call upon the government on Bangladesh to carry out swift investigations into this particular incident and bring the perpetrators to justice, and to grant greater legal support to citizen journalists and ensure better protections for all those who use the Internet as a means of expression.
Web of Sameness
Nishant Shah's column was published in the Indian Express on January 18, 2013.
As I contemplate the event, I see that the Web has become a space for coping with pain and mitigating the horror of our lives. I feel comforted, when I go online, and see people grieving for a woman they never knew, and demanding better conditions for all. As I look at these resolves for change, battle cries demanding justice, and angry responses directed at imagined and imaginary perpetrators of these crimes, I realise that I have heard it all before, over and over again.
“Not Again!” has been the refrain of the year. If life were a musical, this would have been the persistent chorus line of 2012. From fighting against censorship and violation of privacy by government and corporations to acts of hatred, or from ridiculing the map glitches on the iPhone to seeing the growing stronghold of authoritarian forces over the social Web, we have repeatedly rolled our digital sleeves, gnashed our fingers on the keyboards and shouted in political solidarity, “Not Again!”. While this show of protest, this robust expression of change holds a promise of how things will change for the better, it is also a refrain that has lost its bite. What does it mean, this ability to repeatedly say “Not Again!” only to experience these horrors in despairing cyclic patterns?
I want to see how the social Web and the new public spheres online might offer us outlets for emotions but not necessarily platforms for action. Some of the earliest critiques of the Web expressed the fear that given the extreme customisation of social networks, we might soon reside only in digital echo chambers. In the heavily informatised ages that we live in, it is not uncommon to set up specific groups that we belong to, identify friends that we talk with, mark people we follow, set up circles we share in, and configure filters that help us receive information that is tailor-made to suit our personalised preferences. Unfortunately, this quest for selective information sampling often means that we separate the digital spaces of life from the physical ones, without even realising it. We might be seamlessly navigating these two spaces, not really caring for the distinctions of “virtual reality” and “real life”, but in instances like these, it is easy to see how we shroud ourselves in echo chambers, never allowing voices to translate into the world of action.
You are sure to have been bombarded with tweets that have insightfully analysed the conditions of safety in our public spaces. And in all of this, like me, you must have been comforted thinking that there is still hope. But for every “like” you received on your status update, for every time your tweet got favourited or retweeted, for every time you found yourself agreeing with the social experts, you also separated yourself from the reality. Because the people who gave your opinions the attention, are actually people just like you. They are already on your side of things. Talking to them, exchanging ideas with them, calling for change side-by-side is like preaching to the choir, but it gives us a sense of having reached out. The voices in an echo chamber are not just repeated ad nauseum, but they are also not heard by anybody else on the outside, thus stifling the energy and passions that might have resulted in real change.
The Web also offers an easy separation of us versus them. As coping mechanisms and as a way of distancing ourselves from these events, the Web offers us a clear disavowal of guilt. The young man, who shot those children in the school, was mentally unstable. The laws that allowed him to purchase guns are because of the politicians and the arms industry. The student, who got raped in a bus, is the responsibility of the ‘rape capital’ Delhi. If we were in charge, these things would not have happened this way. But now they have happened, and so we will be angry, we will be shocked, we will tweet “Not Again!” and then quickly shift our ever-expanding attention to the burgeoning space of information online.
And then we will wait, for the next incident to happen — oh, not the same, but similar — and we will go through this process once again.
If I have to look into the future and hope that 2013 shall be the year of change, then I am hoping that the change will be from “Not Again” to a “Never Again”. We will have to learn how to use the energy, the power of the Web, the influence of the digital crowds on the digital commons, to produce a change that goes beyond the social network feeds.
I hope that the social Web matures. We have to make sure that the promise of change that the digital social network offers, does not die as armchair clicktivism that witnesses but does nothing to change the act that affects us.
TV versus Social Media: The Rights and Wrongs
Sunil Abraham's guest column was published in the Tribune on January 20, 2013.
Many in traditional media, especially television, look at social media with a mixture of envy and trepidation. They have been at the receiving end of various unsavoury characters online and consequently support regulation of social media. A common question asked by television anchors is "shouldn't they be subject to the same regulation as us?" This is because they employ the 'principle of equivalence', according to which speech that is illegal on broadcast media should also be illegal on social media and vice versa. According to this principle, criticising a bandh on national TV or in a newspaper op-ed or on social media should not result in jail time and, conversely, publishing obscene content, in either new or old media, should render you a guest of the state.
Given that Section 66-A of the Information Technology Act, 2000, places more draconian and arguably unconstitutional limits on free speech when compared to the regulation of traditional and broadcast media, those in favour of civil liberties may be tempted to agree with the 'principle of equivalence' since that will mean a great improvement from status quo. However, we must remember that this compromise goes too far since potential for harm through social media is usually very limited when compared to traditional media, especially when it comes to hate speech, defamation and infringement of privacy. A Facebook update or 'like' or a tweet from an ordinary citizen usually passes completely unnoticed. On rare occasion, an expression on social media originating from an ordinary citizen goes viral and then the potential for harm increases dramatically. But since this is the fringe case we cannot design policy based on it. On the other hand, public persons (those occupying public office and those in public life), including television journalists, usually have tens and hundreds of thousands friends and followers on these social networks and, therefore, can more consistently cause harm through their speech online. For most ordinary Netizens, everyday speech on social media has as much impact as graffiti in a public or residential toilet and therefore employing the 'principle of equivalence' will result in overregulation of new media.
Ideally speech regulation should address the asymmetries in the global attention economy by constantly examining the potential for harm. This applies to both 'speech about' public persons and also 'speech by' them. Since 'speech about' public persons is necessary for transparent and accountable governance and public discourse, such speech must be regulated less than 'speech about' ordinary citizens. Let us understand this using two examples: One, a bunch of school kids referring to a classmate as an idiot on a social network is bullying, but citizens using the very same term to criticise a minister or television anchor must be permitted. Two, an ordinary citizen should be allowed to photograph or video-record the acts of a film or sports star at a public location and upload it to a social network, but this exception to the right of privacy based on public interest will not imply that the same ordinary citizen can publish photographs or videos of other ordinary citizens. Public scrutiny and criticism is part of the price to be paid for occupying public office or public life. If speech regulation is configured to prevent damage to the fragile egos of public persons, then it would have a chilling effect on many types of speech that are critical in a democracy and an open society.
When it comes to 'speech by' those in public office or in public life - given the greater potential for harm - they should be held more liable for their actions online. For example, an ordinary citizen with less than 100 followers causes very limited harm to the reputation of a particular person through a defamatory tweet. However, if the very same tweet is retweeted by a television anchor with millions of followers, there can be more severe damage to that particular person's reputation.
Many in television also wish to put an end to anonymous and pseudonymous speech online. They would readily agree with Nandan Nilekani's vision of tagging all - visits to the cyber cafe, purchases of broadband connections and SIM cards and, therefore, all activities from social media accounts with the UID number. I have been following coverage of the Aadhaar project for the past three years. Often I see a 'senior official from the UIDAI' make a controversial point. If anonymous speech is critical to protect India's identity project then surely it is an important form of speech. But, unlike the print media, which more regularly uses anonymous sources for their stories, television doesn't see clearly the connection between anonymous speech and free media. This is because many of the trolls that harass them online often hide behind pseudonymous identities. Television forgets that anonymous speech is at the very foundation of our democracy, i.e., the electoral ballot.
Five Frequently Asked Questions about the Amended ITRs
Each question is discussed with reference to the text of the treaty, to the minutes of the plenary sessions (which are available via the ITU website), a little international law and a few references to other people’s comments on the treaty.
1. Do the ITRs apply to content on the internet?
Article 1.1 (a) has been amended to add the sentence “These Regulations do not address the content-related aspects of telecommunications”. Although some discussions about the International Telecommunication Regulations (ITRs) and content have ignored this altogether, others seem concerned about its interpretation.
The ITU Secretary General has issued a statement in which he has clarified that “The new ITR treaty does NOT cover content issues and explicitly states in the first article that content-related issues are not covered by the treaty”.
Commentators like Chuan-Zheng Lee however, continue to view the treaty with suspicion, on the basis that it is necessary to examine content in order to tell whether it is spam (Lee and Chaparro differ on this question). However, others like Eric Pfanner have pointed to this paragraph in their skepticism about the US refusal to sign.
Some highlights from the plenary session discussions
The Chairman proposed the addition to Article 1.1(a) at the tenth plenary session. He did this to address concerns that the ITRs text could be interpreted to apply to content on the Internet. The original formulation that he proposed was ‘These regulations do not address and cannot be interpreted as addressing content’. This text was suggested in the middle of an extended discussion on Article 5A.
Many countries were skeptical of this insertion. Sudan argued that content could not be avoided in telecommunication networks “because it will always be in transit.” The United Arab Emirates seemed concerned about international interference in states’ existing regulation of content, and said “maybe we could actually say this in the minutes of the meeting that this regulation should not be interpreted as on alteration to Member States content regulation”.
Concerns about what the term ‘content’ means and whether it would apply broadly were raised by more than one country, including Saudi Arabia. For instance, it was argued that the text proposed by the Chairman might interfere with parts of the treaty that require operators to send tariff information correspondence. More than one country that felt that the insertion of this text would impact several parts of the treaty, and that it would be difficult to determine what amounted to dealing with content. The primary issue appeared to be that the term ‘content’ was not defined, and it therefore remained unclear what was being excluded. In response to these concerns, the Chairman withdrew his proposal for the amendment excluding content.
However, several states then spoke up in favour of the Chairman’s proposal, suggesting that the proposed amendment to Article 1.1 influenced their acceptance of Article 5A (on security and robustness of networks – discussed in detail below). Brazil suggested that an answer to the definitional concerns may be found in the work by Study Group 17, which had a definition available.
Following this, the next day, at the twelfth plenary, the Chairman brought back the Article 1.1 amendment excluding content. He stated explicitly that this amendment might be the way to get Articles 5A and 5B approved. The text he read out was insertion of the words “to the exclusion of their content”, after ‘’services’ at the end of 1.1A. Interestingly however, the term ‘content’ was never defined.
At the next plenary session, Iran raised the objection that this phrase was overbroad, and proposed the following formulation instead: “These Regulations do not address the content-related aspects of telecommunications”. This formulation found its way into the amended ITRs as the treaty stands today.
2. Does Article 5A on network security legitimize surveillance of Internet content?
Article 5A deals with ‘security and robustness of networks’ and requires member states to “individually and collectively endeavour to ensure the security and robustness of international telecommunication networks...”. This may have given rise to concerns about interpretations that may extend the security of networks to malware or viruses, and therefore to content on the Internet. However, Article 5A has to be read with Article 1.1(a), and therefore must be interpreted such that it does not ‘address the content-related aspects of telecommunications’.
Some commentators continue to see Article 5A as problematic. Avri Doria has argued that the use of the word ‘security’ in addition to ‘robustness’ of telecommunication infrastructure suggests that it means Internet security. However Emma Llansó of the Centre for Democracy and Technology has noted that the language used in this paragraph is “ far too vague to be interpreted as a requirement or even a recommendation that countries surveil users on their networks in order to maintain security”. Llansó has suggested that civil society advocates make it clear to countries which attempt to use this article to justify surveillance, that it does not lend itself to such practices.
Some highlights from the plenary session discussions
Article 5A was one of the most controversial parts of the ITRs and was the subject of much debate.
On December 11th, in the Chairman’s draft that was being discussed, Article 5A was titled ‘security of networks’, and required members to endeavour to ensure the “security and robustness of international telecommunication networks”. The Chairman announced that this was the language that came out of Committee 5’s deliberations, and that ‘robustness’ was inserted at the suggestion of CEPT.
Several countries like Poland, Australia, Germany and the United States of America were keen on explicitly stating that Article 5A was confined to the physical or technical infrastructure, and either wanted a clarification that to this effect or use of the term ‘robustness’ instead of security. Many other countries, such as Russia and China, were strongly opposed to this suggestion and insisted that the term security must remain in the document (India was one of the countries that preferred to have the document use the term ‘security’).
It was in the course of this disagreement, during the tenth plenary session, that the Chairman suggested his global solution for Article 1.1 – a clarification that this would not apply to content. This solution was contested by several countries, withdrawn and then reinstated (in the eleventh plenary) after many countries explained that their assent to Article 5A was dependant on the existence of the Article 1 clarification about content (see above for details).
There was also some debate about whether Article 5A should use the term ‘robustness’ or the term ‘security’ (eg. The United States clarified that its preference was for the use of ‘resilience and robustness’ rather than security). The Secretary General referred to this disagreement, and said that he was therefore using both terms in the draft. The title of Article 5A was changed, in the eleventh plenary, to use both terms, instead of only referring to security.
3. Does Article 5B apply to spam content on the Internet?
The text of the amended treaty talks of ‘unsolicited bulk electronic communications’ and does not use the term ‘spam’[Article 5B says that ‘Members should endeavour to take necessary measures to prevent the propagation of unsolicited bulk electronic communications and minimize its impact on international telecommunication services’].If this phrase is read in isolation, it may certainly be interpreted as being applicable to spam. Commentators like Avri Doria have pointed to sources like Resolution 130 of the Plenipotentiary Conference of the International Telecommunication Union (Guadalajara, 2010) to demonstrate that ‘unsolicited bulk electronic communications’ ordinarily means spam. However, others like Enrique A. Chaparro argue that it cannot possibly extend to content on the Internet given the language used in Article 1.1(a). Chapparo has explained, that given the exclusion of content, Article 5B it authorizes anti-spam mechanisms that do not work on content.
Article 5B, which discusses ‘unsolicited bulk electronic communications’, must be read with Article 1, which is the section on purpose and scope of the ITRS. Article 1.1 (a) specifies that the ITRs “do not address the content-related aspects of telecommunications”. Therefore it may be argued that ‘unsolicited bulk electronic communications’ cannot be read as being applicable to content on the Internet.
However, many continue to be concerned about Article 5B’s applicability to spam on the Internet. Although some of them that their fear is that some states may interpret Article 5B as applying to content, despite the contents of Article 1.1(a), many have failed to engage with the issue in the context of Article 1.1(a).
Some highlights from the plenary session discussions
Article 5B is inextricably linked with the amendment to Article 1.1. Mexico asked specifically about what the proposed amendment to Article 1.1 would mean for Article 5B: “I’m referring to the item which we’ll deal with later, namely unsolicited bulk electronic communications. Could that be referred to as content, perhaps?”. The Chairman responded saying, “This is exactly will solve the second Article 5B, that we are not dealing with content here. We are dealing with measures to prevent propagation of unsolicited bulk electronic messages”.
The amendment to Article 1.1 was withdrawn soon after it was introduced. Before it was reintroduced, Sweden said (at the eleventh plenary) that it could not see how Article 5B could apply without looking into the content of messages. The United States agreed with this and went on state that the issue of spam was being addressed at the WTSA level, as well as by other organisations. It argued that the spam issue was better addressed at the technical level than by introducing it in treaty text.
The amendment excluding content was reintroduced during the twelfth plenary. The Chairman explicitly stated that it might be the way to get Articles 5A and 5B approved.
The word ‘spam’ was dropped from the ITRs in the eight plenary, and “unsolicited bulk electronic communications” was used instead. However, in the eleventh plenary, as they listed their reasons for not signing the newly-amended ITRs, Canada and the United States of America referred to ‘spam’ which suggests that they may have viewed the change as purely semantic.
4. Does the resolution on Internet Governance indicate that the ITU plans to take over the Internet?
Much controversy has arisen over the plenary resolution ‘to foster an enabling environment for the greater growth of the Internet’. This controversy has arisen partly thanks to the manner in which it was decided to include the resolution, and partly over the text of the resolution. The discussion here focuses on the text of the resolution and then describes the proceedings that have been (correctly) criticized.
The history of this resolution, as Wolfgang Kleinwächter has explained, is that it was part of a compromise to appease the countries which were taking positions on the ITU’s role in Internet governance, that were similar to the controversial Russian proposal. The controversial suggestions about Internet governance were excluded from the actual treaty and included instead in a non-binding resolution.
The text of the resolution instructs the Secretary General to “to continue to take the necessary steps for ITU to play an active and constructive role in the development of broadband and the multi-stakeholder model of the Internet as expressed in § 35 of the Tunis Agenda”. This paragraph is particularly controversial since of paragraph 35 of the Tunis Agenda says “Policy authority for Internet-related public policy issues is the sovereign right of States. They have rights and responsibilities for international Internet-related public policy issues.” Kleinwächter has pointed out that this selection leaves out later additions that have taken place with progression towards a multi-stakeholder model.
The resolution also resolves to invite member states to “to elaborate on their respective positions on international Internet-related technical, development and public-policy issues within the mandate of ITU at various ITU forums including, inter alia, the World Telecommunication/ICT Policy Forum, the Broadband Commission for Digital Development and ITU study groups”.
A little after its introduction, people began expressing concerns such as the Secretary General may treat the resolution as binding, While the language may raise cause for concern, it is important to note that resolutions of this nature are not binding and countries are free to opt out of them. Opinions vary about the intentions that have driven the inclusion of this resolution, and what it may mean for the future. However commentators like Milton Mueller have scoffed at these concerns, pointing out that the resolution is harmless and may have been a clever political maneuver to resolve the basic conflict haunting the WCIT, and that mere discussion of the Internet in the ITU harms no one.
Some highlights from the plenary session discussions
Egypt and Bulgaria suggested that the resolution refer to paragraph 55 of the Tunis agenda instead of paragraph 35, by inserted the following text “”Recognizing that the existing arrangements for Internet Governance have worked effectively to make the Internet the highly robust, dynamic and geographically diverse medium it is today, with the private sector taking the lead in day-to-day operations and with innovation and value creation at the edges.” The US was also quite insistent on this language (although it did also argue that this was the wrong forum to discuss these issues).
The Chairman was willing to include paragraph 55 in addition to paragraph 35 but Saudi Arabia objected to this inclusion. Finland suggested that the resolution should be removed since it was not supported by all the countries present and was therefore against the spirit of consensus. The Secretary General defended the resolution, suggesting both that it was harmless and that since it was a key component of the compromise, eliminating it would threaten the compromise. South Africa and Nigeria supported this stand.
It was during this debate that the procedural controversy arose. Late into the night, the Chairman said there was a long list of countries that wished to speak and said “I just wanted to have the feel of the room on who will accept the draft resolution”. He proceeded to have countries indicate whether they would accept the draft resolution or not, and then announced that the majority of the countries in the room were in favour of retaining the resolution. The resolution was then retained. Upon Spain’s raising the question, the Chairman clarified that this was not a vote. The next day, other countries raised the same question and the Chairman, while agreeing that the resolution was adopted on the basis of the ‘taking of temperature’ insisted that it was not a vote so much as an effort to see what majority of the countries wanted.
5. Does the human rights language used in the preamble, especially the part about states’ access to the Internet, threaten the Internet in any way?
The preamble says “Member States affirm their commitment to implement these Regulations in a manner that respects and upholds their human rights obligations”, and “These Regulations recognize the right of access of Member States to international telecommunication services”. The text of the preamble can be used as an interpretation aid since it is recognized as providing context to, and detailing the object and purpose of, a treaty. However if the meaning resulting from this appears to be ambiguous, obscure, absurd or unreasonable, then supplementary means such as the preparatory work for the treaty and the circumstances for its conclusion may also be taken into account.
Therefore anyone who is concerned about the impact of the text inserted in the preamble must (a) identify text within the main treaty that could be interpreted in an undesirable manner using the text in the preamble; and (b) consider preparatory work for the treaty and see whether it supports this worrying interpretation. For example, if there were concerns about countries choosing to interpret the term ‘human rights’ as subordinating political rights to economic rights, it would be important to take note of the Secretary General’s emphasis on the UDHR being applicable to all member states.
Initially, only the first insertion about ‘human rights obligations’ was part of the draft treaty. The second insertion, recognizing states’ rights followed after the discussion about human rights language. Some states argued that it was inconsistent to place human rights obligations on states towards their citizens, but to leave out their cross-border obligations. It was immediately after this text was voted into the draft, that the United States, the United Kingdom and other countries refused to sign the ITRs. This particular insertion is phrased as a right of states rather than that of individuals or citizens, which does not align with the language of international human rights. While it may not be strictly accurate to say that human rights have traditionally been individual centric (since collective rights are also recognized in certain contexts), it is certainly very unusual to treat the rights of states or governments as human rights.
Some highlights from the plenary session discussions
The United States of America and the Netherlands wanted to include language to state explicitly that states’ international human rights obligations are not altered in anyway. This was to clarify that the inclusion of human rights language was not setting the ITU up as a forum in which human rights obligations are debated. Malaysia objected to the use of human rights language in the preamble right at the outset, on the grounds that the ITRs are the wrong place for this, and that the right place is the ITU Constitution. It even pointed to the fact that jurisprudence is ever-evolving, to suggest that the meaning of human rights obligations might change over time. These were the two major perspectives offered towards the beginning of the discussion.
The Chairman underlined the fact that the Universal Declaration of Human Rights is already applicable to all UN countries. He argued that reflection of these principles in the ITRs would help build universal public faith in the conference.
The first traces of the states’ access rights can be seen in Cuba’s intervention at the ninth plenary – Cuba argued that limiting states’ access to public information networks amounted to infringement of human rights. At the fourteenth plenary, Nigeria proposed on behalf of the African group that the following text be added to the preamble “And recognize the right of access of all Member States to international telecommunication networks and services." Countries like China which had been ambivalent about the human rights language in the preamble, were happy with this move away from an individual-centric understanding of human rights, to one that sees states as representative of people.
The United States was express in its dissent, and said “human rights obligations go to the individual”. Sweden was also not happy with the proposal and argued that it moved away from well-established human rights language that affirmed existing commitments to drafting new human rights language.
It was an amended version of the African group proposal that finally found its way into the preamble. It was supported by many countries such as China, Nigeria and Sudan, who took the position that group rights are included within human rights, and that governments represent their citizens and therefore have rights on their behalf. This position was strenuously disputed by states like the USA, Switzerland, United Kingdom and Canada.
Data Retention in India
This research was undertaken as part of the 'SAFEGUARDS' project that CIS is undertaking with Privacy International and IDRC.
The Debate around Data Retention
According to the EU, data retention “refers to the storage of traffic and location data resulting from electronic communications (not data on the content of the communications)”.[1]
The debate around data retention has many sides, and walks a fine line of balancing necessity with proportionality. For example, some argue that the actual retention of data is not harmful, and at least some data retention is necessary to assist law enforcement in investigations. Following this argument, the abuse of information is not found in the retention of data, but instead is found by who accesses the data and how it is used. Others argue that any blanket or a priori data retention requirements are increasingly becoming disproportional and can lead to harm and misuse. When discussing data retention it is also important to take into consideration what type of data is being collected and by what standard is access being granted. Increasingly, governments are mandating that service providers retain communication metadata for law enforcement purposes. The type of authorization required to access retained communication metadata varies from context to context. However, it is often lower than what is required for law enforcement to access the contents of communications. The retention and lower access standards to metadata is controversial because metadata can encompass a wide variety of information, including IP address, transaction records, and location information — all of which can reveal a great deal about an individual.[2] Furthermore, the definition of metadata changes and evolves depending on the context and the type of information being generated by new technologies.
Data Retention vs. Data Preservation
Countries have taken different stances on what national standards for data retention by service providers should be. For example, in 2006 the EU passed the Data Retention Directive which requires European Internet Service Providers to retain telecom and Internet traffic data from customers' communications for at least six months and upto two years. The stored data can be accessed by authorized officials for law enforcement purposes.[3] Despite the fact that the Directive pertains to the whole of Europe, in 2010 the German Federal Constitutional Court annulled the law that harmonized German law with the Data Retention Directive.[4] Other European countries that have refused to adopt the Directive include the Czech Republic and Romania.[5] Instead of mandating the retention of data, Germany, along with the US, mandates the 'preservation' of data. The difference being that the preservation of data takes place through a specified request by law enforcement, with an identified data set. In some cases, like the US, after submitting a request for preservation, law enforcement must obtain a court order or subpoena for further access to the preserved information.[6]
Data Retention in India
In India, the government has established a regime of data retention. Retention requirements for service providers are found in the ISP and UASL licenses, which are grounded in the Indian Telegraph Act, 1885.
ISP License
According to the ISP License,[7] there are eight categories of records that service providers are required to retain for security purposes that pertain to customer information or transactions. In some cases the license has identified how long records must be maintained, and in other cases the license only states that the records must be made available and provided. This language implies that records will be kept.
According to the ISP License, each ISP must maintain:
- Users and Services: A log of all users connected and the service they are using, which must be available in real time to the Telecom Authority. (Section 34.12).
- Outward Logins or Telnet: A log of every outward login or telnet through an ISPs computer must be available in real time to the Telecom Authority. (Section 34.12).
- Packets: Copies of all packets originating from the Customer Premises Equipment of the ISP must be available in real time to the Telecom Authority. (Section 34.12).
- Subscribers: A complete list of subscribers must be made available on the ISP website with password controlled access, available to authorized Intelligence Agencies at any time. (Section 34.12).
- Internet Leased Line Customers: A complete list of Internet leased line customers and their sub-customers consisting of the following information: name of customer, IP address allotted, bandwidth provided, address of installation, date of installation/commissioning, and contact person with phone no./email. These must be made available on a password protected website (Section 34.14). The password and login ID must be provided to the DDG (Security), DoT HQ and concerned DDG(VTM) of DoT on a monthly basis. The information should also be accessible to authorized government agencies (Section 34.14).
- Diagram Records and Reasons: A record of complete network diagram of set-up at each of the internet leased line customer premises along with details of connectivity must be made available at the site of the service provider. All details of other communication links (PSTN, NLD, ILD, WLL, GSM, other ISP) plus reasons for taking the links by the customer must be recorded before the activation of the link. These records must be readily available for inspection at the respective premises of all internet leased line customers (Section 34.18).
-
Commercial Records: All commercial records with regard to the communications exchanged on the network must be maintained for a year (Section 34.23).
-
Location: The service provider should be able to provide the geographical location of any subscriber at a given point of time (Section 34.28(x).
- Remote Activities: A complete audit trail of the remote access activities pertaining to the network operated in India. These must be retained for a period of six months, and must be provided on request to the licensor or any other agency authorized by the licensor (Section 34.28 (xv).
UASL License
According to the UASL License[8], there are twelve categories of records that ISP’s are required to retain that pertain to costumer information or transactions for security purposes. In some cases the license has identified how long records must be maintained, and in other cases the license only states that the information must be provided and made available when requested. This language implies that records will be kept.
According to the license, service providers must maintain and make available:
- Numbers: Called/calling party mobile/PSTN numbers when required. Telephone numbers of any call-forwarding feature when required (Section 41.10).
- Interception records: Time, date and duration of interception when required (Section 41.10).
-
Location: Location of target subscribers. For the present, cell ID should be provided for location of the target subscriber when required (Section 41.10).
-
All call records: All call data records handled by the system when required (Section 41.10). This includes:
- Failed call records: Call data records of failed call attempts when required. (Section 41.10).
- Roaming subscriber records: Call data records of roaming subscribers when required. (Section 41.10)
- Commercial records: All commercial records with regards to the communications exchanged on the network must be retained for one year (Section 41.17).
- Outgoing call records: A record of checks made on outgoing calls completed by customers who are making large outgoing calls day and night to various customers (Section 41.19(ii)).
- Calling line Identification: A list of subscribers including address and details using calling line identification should be kept in a password protected website accessible to authorized government agencies (Section 41.19 (iv)).
-
Location: The service provider must be able to provide the geographical location of any subscriber at any point of time (Section 41.20(x)).
- Remote access activities: Complete audit trail of the remote access activities pertaining to the network operated in India for a period of six months (Section 41.20 (xv)).
RTI Request to BSNL and MTNL
On September 10, 2012, the Centre for Internet and Society sent an RTI to MTNL and BSNL with the following questions related to the respective data retention practices:
- Does MTNL/BSNL store the following information/data:
- Text message detail (To and from cell numbers, timestamps)
- Text message content (The text and/or data content of the SMS or MMS)
- Call detail records (Inbound and outbound phone numbers, call duration)
- Bill copies for postpaid and recharge/top-up billing details for prepaid
- Location data (Based on cell tower, GPS, Wi-Fi hotspots or any combination thereof)
- If it does store data then
- For what period does MTNL/BSNL store: SMS and MMS messages, cellular and mobile data, customer data?
- What procedures for retention does MTNL/BSNL have for: SMS and MMS messages, cellular and mobile data, and customer data?
- What procedures for deletion of: SMS and MMS messages, cellular and mobile data, and customer data?
- What security procedures are in place for SMS and MMS messages, cellular and mobile data, and customer data?
BSNL Response
BSNL replied by stating that it stores at least three types of information including:
- IP session information - connection start end time, bytes in and out (three years offline)
- MAC address of the modem/router/device (three years offline)
- Bill copies for post paid and recharge/top up billing details for prepaid. Billing information of post paid Broadband are available in CDR system under ITPC, prepaid voucher details (last six months).
MTNL Response
MTNL replied by stating that it stores at least () types of information including:
- Text message details (to and from cell number, timestamps) in the form of CDRs (one year)
- Call detail records including inbound and outbound phone numbers and call duration (one year)
- Bill copies from postpaid (one year)
- Recharge details for prepaid (three months)
- Location of the mobile number if it has used the MTNL GSM/3GCDMA network (one year)
It is interesting that BSNL stores information that is beyond the required time period required in both the ISP and the UASL licenses. The responses to the RTI showed that each service provider also stores different types of information. This could or could not be the actual case, as each question could have been interpreted differently by the responding officer.
Conclusion
The responses to the RTI from BSNL and MTNL are a step towards understanding data retention practices in India, but there are still many aspects about data retention in India which are unclear including:
- What constitutes a ‘commercial record’ which must be stored for one year by service providers?
- How much data is retained by service providers on an annual basis?
- What is the cost involved in retaining data? For the service provider? For the public?
- How frequently is retained information accessed by law enforcement? What percentage of the data is accessed by law enforcement?
- How many criminal and civil cases rely on retained data?
- What is the authorization process for access to retained records? Are these standards for access the same for all types of retained data?
Having answers to these questions would be useful for determining if the Indian data retention regime is proportional and effective. It would also be useful in determining if it would be meaningful to maintain a regime of data retention or switch over to a more targeted regime of data preservation.
Though it can be simple to say that a regime of data preservation is the most optimal choice as it gives the individual the greatest amount of immediate privacy protection,
A regime of data preservation would mean that all records would be treated like an interception, where the police or security agencies would need to prove that a crime was going to take place or is in the process of taking place and then request the ISP to begin retaining specific records. This approach to solving crime would mean that the police would never use retained data or historical data as part of an investigation – to either solve a case or to take the case to the next level. If Indian law enforcement is at a point where they are able to concisely identify a threat and then begin an investigation is a hard call to make. It is also important to note that though preservation of data can reduce the risk to individual privacy as it is not possible for law enforcement to track individuals based off of their historical data and access large amounts of data about an individual, preservation does not mean that there is no possibility for abuse. Other factors such as:
- Any request for preservation and access to records must be legitimate and proportional
- Accessed and preserved records must be used only for the purpose indicated
- Accessed and preserved records can only be shared with authorized authorities
- Any access to preserved records that do not pertain to an investigation must be deleted
These factors must be enforced through the application of penalties for abuse of the system. These factors can also be applied to not only a data preservation regime, but also a data retention regime and are focused on preventing the actual abuse of data after retained. That said, before an argument for either data retention or data preservation can be made for India it is important to understand more about data retention practices in India and use of retained data by Indian law enforcement and access controls in place.
[1]. European Commission – Press Release. Commission Takes Germany to Court Requesting that Fines be Imposed. May 31st 2012. Available at: http://bit.ly/14qXW6o. Last accessed: January 21st 2013
[2].Draft International Principles on Communications Surveillance and Human Rights: http://bit.ly/UpGA3D
[3]. European Commission – Press Release. Commission Takes Germany to Court Requesting that Fines be Imposed. May 31st 2012. Available at: http://bit.ly/14qXW6o. Last accessed: January 21st 2013.
[4]. European Commission – Press Release. Commission Takes Germany to Court Requesting that Fines be Imposed. May 31st 2012. Available at: http://bit.ly/14qXW6o. Last accessed: January 21st 2013.
[5]. Tiffen, S. Sweden passes controversial data retention directive. DW. March 22 2012. Available at: http://bit.ly/WOfzaX. Last Accessed: January 21st 2013.
[6]. Kristina, R. The European Union's Data Retention Directive and the United State's Data Preservation Laws: Fining the Better Model. 5 Shilder J.L. Com. & Tech. 13 (2009) available at: http://bit.ly/VoQxQ9. Last accessed: January 21st 2013
[7]. Government of India. Ministry of Communications & IT Department of Telecommunications. License Agreement for Provision of Internet Services.
[8]. Government of India. Ministry of Communications & IT Department of Telecommunications. License Agreement for Provision of Unified Access Services after Migration from CMTS. Amended December 3rd 2009.
MTNL RTI
 MTNL_RTI.pdf
—
PDF document,
162 kB (166734 bytes)
MTNL_RTI.pdf
—
PDF document,
162 kB (166734 bytes)
BSNL RTI
 BSNL_RTI.pdf
—
PDF document,
203 kB (208208 bytes)
BSNL_RTI.pdf
—
PDF document,
203 kB (208208 bytes)
RTI Application Reply
 Saiket-1.pdf
—
PDF document,
277 kB (284007 bytes)
Saiket-1.pdf
—
PDF document,
277 kB (284007 bytes)
A Comparison of Indian Legislation to Draft International Principles on Surveillance of Communications
This research was undertaken as part of the 'SAFEGUARDS' project that CIS is undertaking with Privacy International and IDRC.
The Centre for Internet and Society is contributing feedback to the drafting of the principles. The principles are still in draft form and the most recent version along with the preamble to the principles can be accessed at: http://necessaryandproportionate.net/
The Principles:
1. Principle - Legality: Any limitation to the right to privacy must be prescribed by law. Neither the Executive nor the Judiciary may adopt or implement a measure that interferes with the right to privacy without a previous act by the Legislature that results from a comprehensive and participatory process. Given the rate of technological change, laws enabling limitations on the right to privacy should be subject to periodic review by means of a participatory legislative or regulatory process.
Indian Legislation: In India there are two predominant legislations with subsequent Rules and Licenses that allow for access to communications by law enforcement and the government. Though the basic power of interception of communications are prescribed by law, the Rules and Licenses build off of these powers and create procedural requirements, and requirements for assistance.
- The Indian Telegraph Amendment Rules 2007: These Rules are grounded in section 419A of the Indian Telegraph Act and establish procedures and safeguards for the interception of communications.
- License Agreement for Provision of Unified Access Services After Migration from CMTS (UASL): This license is grounded in the Telegraph Act, and details what types of assistance service providers must provide to law enforcement and the government.
- License Agreement for Provision of Internet Services: This license is grounded in the Telegraph Act, and details what types of assistance service providers must provide to law enforcement and the government.
- The Information Technology Act, 2000
- Procedure and Safeguards for Interception, Monitoring, and Decryption of Information Rules 2009: These Rules were notified in 2009 and allow authorized governmental agencies to intercept, monitor, and decrypt information generated, transmitted, received, or stored in any computer resource.
- Procedure and safeguard for Monitoring and Collecting Traffic Data or Information Rules 2009: These Rules were notified in 2009 and allow authorized agencies to monitor and collect traffic data or information that is generated, transmitted, received or stored in any computer resource.
2. Principle - Legitimate Purpose: Laws should only allow access to communications or communications metadata by authorized public authorities for investigative purposes and in pursuit of a legitimate purpose, consistent with a free and democratic society.
Indian Legislation: In relevant Indian legislation there are no specific provisions requiring that access by law enforcement must be for a legitimate purpose and consistent with a free and democratic society. Instead, Indian legislation defines and lays out specific circumstances for which access would be allowed.
Below are the circumstances for which access is allowed by each Act, Rule, and License:
- On the occurrence of any public emergency
- In the interest of the public safety
- In the interests of the sovereignty and integrity of India
- The security of the state
- Friendly relations with foreign states
- Public order
- Preventing incitement to the commission of an offence
- In the interest of the sovereignty or integrity of India,
- Defense of India
- Security of the state
- Friendly relations with foreign states
- Public order
- Preventing incitement to the commission of any cognizable offence relating to the above
- For investigation of any offence
- Forecasting of imminent cyber incidents
- Monitoring network application with traffic data or information on computer resources
- Identification and determination of viruses or computer contaminant
- Tracking cyber security breaches or cyber security incidents
- Tracking computer resource breaching cyber security or spreading virus’s or computer contaminants
- Identifying or tracking of any person who has breached, or is suspected of having breached or being likely to breach cyber security.
- Undertaking forensic of the concerned computer resource as a part of investigation or internal audit of information security practices in the computer resource.
- Accessing stored information for enforcement of any provisions of the laws relating to cyber security for the time being in force.
- Any other matter relating to cyber security.
- Reasons defined in the Telegraph Act. (Section 41.20 (xix))
- National Security. (Section 41.20 (xvii))
- To counteract espionage, subversive act, sabotage, or any other unlawful activity. (Section 41.1)
- Trace nuisance, obnoxious or malicious calls, messages or communications transported through his/her equipment. (Section 40.4)
- In the interests of security. (Section 41.7)
- For security reasons. (Section 41.20 (iii))
- To counteract espionage, subversive act, sabotage, or any other unlawful activity. (Section 34.1)
- In the interests of security. (Section 34.4)
- For security reasons. (Section 34.28 (iii))
- Reasons defined in the Telegraph Act. (Section 35.2)
3. Principle - Necessity: Laws allowing access to communications or communications metadata by authorized public authorities should limit such access to that which is strictly and demonstrably necessary, in the sense that an overwhelmingly positive justification exists, and justifiable in a democratic society in order for the authority to pursue its legitimate purposes, and which the authority would otherwise be unable to pursue. The onus of establishing this justification, in judicial as well as in legislative processes, is on the government.
Indian Legislation: Relevant Indian legislation do not contain provisions mandating that access to communications must be demonstrably necessary, and do not give details of the criteria that authorizing authorities should use to determine if a request is a valid or not. Relevant Indian legislation does require that all directions contain reasons for the direction. Additionally, excluding the ITA Procedure and safeguard for Monitoring and Collecting Traffic Data or Information Rules, relevant Indian legislation requires that all other means for acquiring the information must be taken into consideration before a direction for access can be granted.
Below are summaries of the relevant provisions:
- TA Rules 2007: Any order for interception issued by the competent authority must contain reasons for the direction (Section 2). While issuing orders for direction, all other means for acquiring the information must be taken into consideration, and directions can only be issued if it is not possible to acquire the information by any other reasonable means (Section 3).
- ITA Interception and Monitoring Rules: Any direction issued by the competent authority must contain reasons for such direction (Section 7). The competent authority must consider the possibility of acquiring the necessary information by other means and the direction can be issued only when it is not possible to acquire the information any other reasonable means (Section 8).
- ITA Traffic Monitoring Rules: Any direction issued by the competent authority must contain reasons for the direction (Section 3(3)).
- UASL & ISP License: As laid out in the Telegraph Act and subsequent Rules.
4. Principle - Adequacy: Public authorities should restrain themselves from adopting or implementing any measure of intrusion allowing access to communications or communications metadata that is not appropriate for fulfillment of the legitimate purpose that justified establishing that measure.
Indian Legislation: In relevant Indian legislation there are provisions that require direction for access to be specific, but there are no provisions that specifically prohibit government agencies from collecting and accessing information that is not appropriate for fulfillment of the stated purpose of the direction.
5. Principle - Competent Authority: Authorities capable of making determinations relating to communications or communications metadata must be competent and must act with independence and have adequate resources in exercising the functions assigned to them.
Indian Legislation: In relevant Indian legislation it is required that directions for access to be authorized by "competent authorities". The most common authority for authorizing orders for access is the Secretary to the Government of India in the Ministry of Home Affairs, but authorization can also come from other officials depending on the circumstance. The fact that authorization for access to communications content is not from a judge has been a contested topic, as in many countries a judicial order is the minimum requirement for access to communication content. It is unclear from the legislation if adequate resources are assigned to the competent authorities.
Below are summaries of relevant provisions:
- The Secretary to the Government of India in the Ministry of Home Affairs at the Central Level
- The Secretary to the State Government in charge of the Home Department in the case of the State Government.
- In unavoidable circumstances an order for interception may only be made by an officer not below the rank of a Joint Secretary to the Government of India who has been authorized by the Union Home Secretary or the State Secretary.
- In remote areas or for operational reasons where obtaining prior directions for interception is not feasible the head or the second senior most officer of the authorized security agency at the Central level and the officers authorized in this behalf and not below the rank of Inspector of General Police. (Section 1(2)).
- ITA Interception and Monitoring Rules: Under the ITA Rules related to the interception, monitoring, and decryption of communications, the competent authorities for authorizing directions are:
- The Secretary in the Ministry of Home Affairs in case of the Central Government.
- The Secretary in charge of the Home Department, in case of a State Government or Union Territory.
- In unavoidable circumstances any officer not below the rank of the Joint Secretary to the Government of India who has been authorized by the competent authority.
- In remote areas or for operational reasons where obtaining prior directions is not feasible, the head or the second senior most officer of the security and law enforcement agency at the Central level or the officer authorized and not below the rank of the inspector General of Police or an officer of equivalent rank at the State or Union territory level. (Section 3).
- ITA Monitoring and Collecting Traffic Data Rules: Under the ITA Rules related to the monitoring and collecting of traffic data, the competent authorities who can issue and authorize directions are:
- The Secretary to the Government of Indian in the Department of Information Technology under the Ministry of Communications and Information Technology. (Section 2(d)).
- An employee of an intermediary may complete the following if it is in relation to the services that he is providing including: accessing stored information from computer resource for the purpose of implementing information security practices in the computer resource, determining any security breaches, computer contaminant or computer virus, undertaking forensic of the concerned computer resource as a part of investigation or internal audit. Accessing or analyzing information from a computer resource for the purpose of tracing a computer resource or any person who has contravened or is suspected of having contravened or being likely to contravene any provisions of the Act that is likely to have an adverse impact on the services provided by the intermediary. (Section 9 (2)).
- UASL & ISP License: As laid out in the Telegraph Act and subsequent Rules.
6. Principle - Proportionality: Public authorities should only order the preservation and access to specifically identified, targeted communications or communications metadata on a case-by-case basis, under a specified legal basis. Competent authorities must ensure that all formal requirements are fulfilled and must determine the validity of each specific attempt to access or receive communications or communications metadata, and that each attempt is proportionate in relation to the specific purposes of the case at hand. Communications and communications metadata are inherently sensitive and their acquisition should be regarded as highly intrusive. As such, requests should at a minimum establish a) that there is a very high degree of probability that a serious crime has been or will be committed; b) and that evidence of such a crime would be found by accessing the communications or communications metadata sought; c) other less invasive investigative techniques have been exhausted; and d) that a plan to ensure that the information collected will be only that information reasonably related to the crime and that any excess information collected will be promptly destroyed or returned. Neither the scope of information types, the number or type of persons whose information is sought, the amount of data sought, the retention of that data held by the authorities, nor the level of secrecy afforded to the request should go beyond what is demonstrably necessary to achieve a specific investigation.
Indian Legislation: In relevant Indian legislation there are no comprehensive provisions that ensure proportionality of the surveillance of communications but there are provisions that contribute to ensuring proportionality. These include provisions requiring: time frames for how long law enforcement can retain accessed and collected material, directions to be issued only after there are no other means for acquiring the information, requests to contain reasons for the order, the duration for which an order can remain in force to be limited, and requests to be for specified purpose based on a particular set of premises. All of these provisions are found in the Telegraph Rules issued in 2007 and the ITA Procedures and Safeguards for Interception, Monitoring, and Decryption of Information Rules. None of these requirements are found in the UASL or ISP licenses, and many are missing from the ITA Safeguards for Monitoring and Collecting Traffic Data or Information Rules.
Though the above are steps to ensuring proportionality, Indian legislation does not provide details of how the proportionality of requests would be measured as recommended by the principle. For example, it is not required that requests for access demonstrate that evidence of the crime would be found by accessing the communications or communications metadata sought, and that information only related directly to the crime will be collected. Furthermore, Indian legislation does not place restrictions on the amount of data sought, nor the level of secrecy afforded to the request.
Below is a summary of the relevant provisions:
- Service providers shall destroy record pertaining to directions for interception of message within two months of discontinuing the interception. (Section 19).
- Directions for interception should only be issued only when it is not possible to acquire the information by any other reasonable means. (Section 3).
- The interception must be of a message or class of message from and too one particular person that is specified or described in the order or one particular set of premises specified or described in the order. (Section 4).
- The direction for interception will remain in force for a period of 60 days, or 180 days if the directions are renewed. (Section 6).
- ITA Interception and Monitoring Rules:
- Any direction issued by the competent authority must contain reasons for such direction. (Section 7).
- The competent authority must consider all other possibilities of acquiring the information by other means, and the direction can only be issued when it is not possible to acquire the information by any other reasonable means. (Section 8).
- The direction of interception, monitoring, or decryption of any information generated, transmitted, received, or stored in any computer resource etc., as may be specified or described in the direction. (Section 9).
- The directions for interception, monitoring, or decryption will remain in force for a period of 60 days, or 180 days if the directions are renewed. (Section 10).
- ITA Traffic and Monitoring Rules:
- Any direction issued by the competent authority must contain reasons for such direction. (Section 3(3)).
- Every record including electronic records pertaining to such directions for monitoring or collection of traffic data shall be destroyed after the expiry of nine months by the designated officer. Except when the information is needed for an ongoing investigation, the person in charge of a computer resource shall destroy records within a period of six months of discontinuing the monitoring. (Section 8).
7. Principle - Due process: Due process requires that governments must respect and guarantee an individual’s human rights, that any interference with such rights must be authorized in law, and that the lawful procedure that governs how the government can interfere with those rights is properly enumerated and available to the general public.(9) While criminal investigations and other considerations of public security and safety may warrant limited access to information by public authorities, the granting of such access must be subject to guarantees of procedural fairness. Every request for access should be subject to prior authorization by a competent authority, except when there is imminent risk of danger to human life.(10)
Indian Legislation: In the relevant Indian legislation the only guarantee for due process is that every request for access must be subject to prior authorization by a competent authority.
- All orders for interception must be issued by the Secretary to the Government of India in the Ministry of Home Affairs.
- ITA Interception and Monitoring Rules:
- All orders for interception must be issued by the Secretary to the Government of India in the Ministry of Home Affairs.
- ITA Monitoring of Traffic Rules:
- The Secretary to the Government of India in the Department of Information Technology under the Ministry of Communications and Information Technology is the competent authority for authorizing orders.
8. Principle - User notification: Notwithstanding the notification and transparency requirements that governments should bear, service providers should notify a user that a public authority has requested his or her communications or communications metadata with enough time and information about the request so that a user may challenge the request. In specific cases where the public authority wishes to delay the notification of the affected user or in an emergency situation where sufficient time may not be reasonable, the authority should be obliged to demonstrate that such notification would jeopardize the course of investigation to the competent judicial authority reviewing the request. In such cases, it is the responsibility of the public authority to notify the individual affected and the service provider as soon as the risk is lifted or after the conclusion of the investigation, whichever is sooner.
Indian Legislation: In relevant Indian legislation there are no provisions that require the government or service providers to notify the user that a public authority has requested his or her communication data.
9. Principle - Transparency about use of government surveillance: The access capabilities of public authorities and the process for access should be prescribed by law and should be transparent to the public. The government and service providers should provide the maximum possible transparency about the access by public authorities without imperiling ongoing investigations and with enough information so that individuals have sufficient knowledge to fully comprehend the scope and nature of the law, and when relevant, challenge it. Service providers must also publish the procedure they apply to deal with data requests from public authorities.
Indian Legislation: In relevant Indian legislation there are no requirements that access capabilities of the government and the process for access must be transparent to the public. Nor are service providers required to publish the procedure applied to handle data requests from public authorities.
10. Principle - Oversight: An independent oversight mechanism should be established to ensure transparency of lawful access requests. This mechanism should have the authority to access information about public authorities' actions, including, where appropriate, access to secret or classified information, to assess whether public authorities are making legitimate use of their lawful capabilities, and to publish regular reports and data relevant to lawful access. This is in addition to any oversight already provided through another branch of government such as parliament or a judicial authority. This mechanism must provide – at minimum – aggregate information on the number of requests, the number of requests that were rejected, and a specification of the number of requests per service provider and per type of crime. (11)
Indian Legislation: In relevant Indian legislation there are requirements for a review committee to be established. The review committee must meet on a bi-monthly basis and review directions to ensure that they are in accordance with the prescribed law. Currently, it is unclear from the legislation if the review committees have the authority to access information about public authorities’ actions, and currently the review committee does not publish aggregate information about the number of requests, the number of requests that were rejected, and a specification of the number of requests per service provider and per type of crime. These standards are recommended by the principle.
The relevant provisions are summarized below:
- A review committee will be constituted by a state government that consists of a chief secretary, secretary of law, secretary to the state government. The review committee shall meet at least once in two months. If the committee finds that directions are not in accordance with the mandated provisions, then the committee can order the destruction of the directions. (Section 17). Any order issued by the competent authority must contain reasons for such directions and a copy be forwarded to the concerned review committee within a period of seven working days. (Section 2).
- ITA Interception and Monitoring Rules:
- Any direction issued by the competent authority must be forwarded to the review committee within a period of seven working days from issuing. The review committee is the same as constituted under rule 419A of the Indian Telegraph Rules, 1951. The review committee must meet bi-monthly and determine whether directions are in accordance with the ITA Act. If the review committee finds that the directions are not in accordance with the Act, it may issue an order for the destruction of the copies of accessed information and set aside the directions. (Section 22).
- ITA Traffic Monitoring Rules:
- Any direction issued by the competent authority must be forwarded to the review committee within a period of seven working days from issuing. The review committee is the same as constituted under rule 419A of the Indian Telegraph Rules, 1951. The review committee must meet bi-monthly and determine whether directions are in accordance with the ITA Act. If the review committee finds that the directions are not in accordance with the Act, it may issue an order for the destruction of the copies of accessed information and set aside the directions. (Section 7).
11. Principles - Integrity of communications and systems: It is the responsibility of service providers to transmit and store communications and communications metadata securely and to a degree that is minimally necessary for operation. It is essential that new communications technologies incorporate security and privacy in the design phases. In order, in part, to ensure the integrity of the service providers’ systems, and in recognition of the fact that compromising security for government purposes almost always compromises security more generally, governments shall not compel service providers to build surveillance or monitoring capability into their systems. Nor shall governments require that these systems be designed to collect or retain particular information purely for law enforcement or surveillance purposes. Moreover, a priori data retention or collection should never be required of service providers and orders for communications and communications metadata preservation must be decided on a case-by-case basis. Finally, present capabilities should be subject to audit by an independent public oversight body.
Indian Legislation: In relevant Indian legislation there are a number of security measures that must be put in place but these are predominantly actions that must be taken by service providers, and do not pertain to intelligence agencies. Furthermore, many provisions found in the ITA Procedure and Safeguards for Interception, Monitoring, and Decryption of Information Rules, and the ISP and UASL licenses include requirements for service providers to provide monitoring facilities and technical assistance, require information to be retained specifically for law enforcement purposes, and require service providers to comply with a-priori data retention mandates. In the ISP and UASL license, service providers are audited and inspected to ensure compliance with requirements listed in the license, but it unclear from the legislation if the access capabilities of government or governmental agencies are audited by an independent public oversight body. This standard is recommended by the principle.
Relevant provisions are summarized below:
Provisions requiring the provision of facilities, assistance, and retention:
- The intermediary must provide all facilities, co-operation for interception, monitoring, and decryption of information mentioned in the direction (Section 13(2)).
- If a decryption direction or copy is handed to the decryption key holder to whom the decryption direction is addressed by the nodal officer, the decryption key holder must disclose the decryption key or provide the decryption assistance. (Section 17).
- The intermediary must extend all facilities, co-operation and assistance in installation, removal and testing of equipment and also enable online access to the computer resource for monitoring and collecting traffic data or information. (Section 4(7)).
- The service provider cannot employ bulk encryption equipment in its network, and any encryption equipment connected to the licensee’s network for specific requirements must have prior evaluation an approval of the licensor. (Section 39.1).
- The service provider must provide all tracing facilities to trace nuisance, obnoxious or malicious calls, messages or communications transported through the equipment and network to authorized officers of the government for purposes of national security.(Section 40.4).
- Suitable monitoring equipment as may be prescribed for each type of system used will be provided by the service provider for monitoring as and when required by the licensor. (Section 41.7).
- The designated person of the Central/State Government as conveyed to the Licensor from time to time in addition to the licensor or its nominee shall have the right to monitor the telecommunication traffic in every MSC/Exchange/MGC/MG. The service provider must make arrangements for the monitoring of simultaneous calls by Government security agencies. In case the security agencies intend to locate the equipment at the service provider’s premises for facilitating monitoring, the service provider should extend all support in this regard including space and entry of the authorized security personnel. The interface requirements as well as features and facilities as defined by the licensor should be implemented by the service provider for both data and speech. Presently, the service provider should ensure suitable redundancy in the complete chain of monitoring equipment for trouble free operations of monitoring of at least 210 simultaneous calls for seven security agencies. (Section 41.10).
- The service provider must also make the following records available: called/calling party mobile/PSTN numbers, Time/date and duration of interception, location of target subscribers, telephone numbers if any call-forwarding feature has been invoked by the target subscriber, data records for even failed attempts, and call data record of roaming subscribers. (Section 41.10).
- The service provider shall provide the facility to carry out surveillance of Mobile Terminal activity within a specified area. (Section 41.11).
- The complete list of subscribers must be made available by the service provider on their website to authorized intelligence agencies. This list must be updated on a regular basis. Hard copies of the list must also be made available to security agencies when requested. (Section 41.14). The database of subscribers must also be made available to the licensor or its representatives. (Section 41.16).
- The service provider must maintain all commercial records with regard to the communications exchanged on the network. All records must be archived for at least one year. (Section 41.17).
- Calling Line Identification must be provided and the network should also support Malicious Call Identification. (Section 41.18).
- Information about bulk connections must be forwarded to the VTM Cell of DoT, DDG (Security) DoT, and any other officer authorized by the Licensor from time to time as well as Security Agencies on a monthly basis (Section 41.19).
- Subscribers having CLIR should be listed in a password protected website with their complete address and details so that authorized Government agencies can view or download for detection and investigation of misuse. (Section 41.19(iv)).
- The service provider must provide traceable identities of their subscribers. If the subscriber is roaming from another foreign company, the Indian Company must try to obtain traceable identities from the foreign company as part of its roaming agreement. (41.20 (ix)).
- On request by the licensor or any other agency authorized by the licensor, the licensee must be able to provide the geographical location (BTS location) of any subscriber at any point of time. (41.20 (x))
- Suitable technical devices should be made available at the Indian end to designated security agency/licensor in which a mirror image of the remote access information is available on line for monitoring purposes. (41.20 (xiv)).
- A complete audit trail of the remote access activities pertaining to the network operated in India should be maintained for a period of six months and provided on request to the licensor. (Section 41.20 (xv)).
- For monitoring traffic, the service provider should provide access of their network and other facilities as well as to books of accounts to the security agencies. (Section 41.20 (xx)).
- The ISP must ensure that Bulk Encryption is not deployed by ISPs. Individuals/groups /organizations can use encryption up to 40 bit key length without obtaining permission from the licensor. If encryption equipments higher than this limit are deployed, individuals/groups/organizations must obtain prior written permission from the licensor and deposit the decryption key. (Section 2.2(vii)).
- The ISP must furnish to the licensor/TRAI on demand documents, accounts, estimates, returns, reports, or other information. (Section 9.1).
- The ISP will provide tracing facilities to trace nuisance, obnoxious or malicious calls, messages or communications transported through his equipment and network when such information is necessary for investigations or detection of crimes and in the interest of national security. (Section 33.4).
- The ISP will provide the necessary facilities for continuous monitoring of the system, as required by the licensor or its authorized representatives. (Section 30.1).
- The ISP shall provide necessary facilities depending upon the specific situation at the relevant time to the Government to counteract espionage, subversive acts, sabotage or any other unlawful activity. (Section 34.1).
- In the interests of security, suitable monitoring equipment as may be prescribed for each type of system used, which will be provided by the licensee. (Section 34.4).
- The designated person of the Central/State Government or its nominee will have the right to monitor the telecommunication traffic. The ISP will make arrangements for monitoring simultaneous calls by Government security agencies. (Section 34.6).
- The ISP must install infrastructure in the service area with respect to: Internet telephony services offered by the ISP for processing, routing, directing, managing, authenticating the internet telephony calls including the generation of Call Details Record (CDR), called IP address, called numbers, date , duration, time and charges of internet telephony calls. (Section 34.7).
- ISPs must maintain a log of all users connected and the service that they are using (mail, telnet, http etc.). The ISPs must log every outward login or telnet through their computers. These logs as well as copies of all the packets originating from the Customer Premises Equipment of the ISP must be made available in real time to the Telecom Authority. (Section 34.8).
- The ISP should provide the facility to carry out surveillance of Mobile Terminal activity within a specified area. (Section 34.9).
- The complete list of subscribers must be made available by the ISP on their website so that intelligence agencies can obtain the subscriber list at any time. (Section 34.12).
- The list of Internet leased line customers and sub-costumers must be placed on a password protected website with the following information: Name of customer, IP address allotted, bandwidth provided, address of installation, date of installation, contact person with phone number and email. This information should be accessible to authorized Government agencies. (Section 34.13).
- Monitoring of high UDP traffic value and to check for cases where upstream UDP traffic is similar to downstream UDP traffic and monitor such customer monthly with physical verification and personal identity. (Section 34.15).
- The licensor will have access to the database relating to the subscribers of the ISP. The ISP must make available at any instant the details of the subscribers using the service. (Section 34.22).
- The ISP must maintain all commercial records with regard to the communications exchanged on the network for at least one year and will be destroyed unless directed otherwise. (Section 34.23).
- Every international gateway with a route/switch having a capacity of 2Mbps must be equipped with a monitoring Centre at the cost of the ISP. The cost of meeting the requirements of the security agencies, the cost of maintenance of the monitoring equipment and infrastructure must be borne by the ISP. (Section 34.27 (a(i)).
- Office space of 10 by 10 feet with adequate power supply and air-conditioning must be provided by the ISP free of cost. (Section 34.27 (a(ii)) One local exclusive telephone must be made available by the ISP at the monitoring centre at the cost of the ISP. (Section 34.27 (a(iii)).
- Each route/switch of the ISP should be connected by the LAN operating at the same speed as the router/switch; the monitoring equipment will be connected to this network. (Section 34.27 (a(v)).
- The ISP must provide traceable identity of their subscribers. In the case of roaming subscribers the ISP must try to obtain the traceable identity of roaming subscribers from the foreign company. (Section 34.27 (ix)).
- On request of the licensor or any other authorized agency, the ISP must be able to provide the geographical location of any subscriber (BTS location of wireless subscriber) at a given point of time. (Section 34.27 (x)).
- Suitable technical devices should be made available to designated security agencies in which a mirror image of the remote access information is available on line for monitoring purposes. (Section 34.27 (xiv)).
- A complete audit trail of the remote access activities pertaining to the network operated in India should be maintained for a period of six months and provided on request. (Section 34.27 (xv)).
- ISPs must provide access of their network and other facilities, as well as books to security agencies. (Section 34.27 (xx)).
12. Principle - Safeguards for international cooperation: In response to changes in the flows of information and the technologies and services that are now used to communicate, governments may have to work across borders to fight crime. Mutual legal assistance treaties (MLATs) should ensure that, where the laws of more than one state could apply to communications and communications metadata, the higher/highest of the available standards should be applied to the data. Mutual legal assistance processes and how they are used should also be clearly documented and open to the public. The processes should distinguish between when law enforcement agencies can collaborate for purposes of intelligence as opposed to sharing actual evidence. Moreover, governments cannot use international cooperation as a means to surveil people in ways that would be unlawful under their own laws. States must verify that the data collected or supplied, and the mode of analysis under MLAT, is in fact limited to what is permitted. In the absence of an MLAT, service providers should not respond to requests of the government of a particular country requesting information of users if the requests do not include the same safeguards as providers would require from domestic authorities, and the safeguards do not match these principles.
Indian Legislation: India currently has signed 32 MLAT treaties with other countries, each with its own provisions and conditions relating to access to information. The provisions of the Information Technology Act 2000 apply to any contravention of the Act that is committed outside of India, thus the Rules related to interception, monitoring, decryption etc. would apply to any contravention of the Act outside of India. The provisions of the Indian Telegraph Act only apply to communications within India, but the licenses do specify when information held by service providers cannot be transferred across borders.
Below is a summary of the relevant provisions:
13. Principle - Safeguards against illegitimate access: To protect individuals against unwarranted attempts to access communications and communications metadata, governments should ensure that those authorities and organizations who initiate, or are complicit in, unnecessary, disproportionate or extra-legal interception or access are subject to sufficient and significant dissuasive penalties, including protection and rewards for whistleblowers, and that individuals affected by such activities are able to access avenues for redress. Any information obtained in a manner that is inconsistent with these principles is inadmissible as evidence in any proceeding, as is any evidence derivative of such information.
Indian Legislation: Though relevant Indian legislation does provide penalty for unauthorized interception or access, the penalty applies only to service providers, and does not hold governmental agencies responsible. Currently there are no avenues of redress for the individual, and there are no protections or rewards for whistleblowers. Both of these safeguards are recommended by the principle.
The relevant provisions are summarized below:
- In order to maintain privacy of voice and data, monitoring must be done in accordance with the 2007 Rules established under the Indian Telegraph Act, 1885. (Section 41.20 (xix)).
- Any damage arising from the failure of the service provider to provider tracing assistance to the government for purposes of national security is payable by the service provider. (Section 40.4).
- In order to maintain the privacy of voice and data, monitoring can only be carried out after authorization by the Union Home Secretary or Home Secretaries of the State/Union Territories. (Section 34.28 (xix)).
- The ISP indemnifies the licensor against all actions brought against the licensor for breach of privacy or unauthorized interruption of data transmitted by the subscribers. (Section 8.4).
- Any damages that occur from non-compliance on the part of the ISP must be paid by the ISP. (Section 33.4).
14. Principle - Cost of surveillance: The financial cost of providing access to user data should be borne by the public authority undertaking the investigation. Financial constraints place an institutional check on the overuse of orders, but the payments should not exceed the service provider’s actual costs for reviewing and responding to orders, as such would provide a perverse financial incentive in opposition to user’s rights.
Indian Legislation: In India, the ISP and the UASL licenses specifically state that the cost of providing facilities must be borne by the service provider. Though the ITA Interception and Monitoring Rules do require intermediaries to provide facilities, it is not clear from the Rules where the burden of the cost will fall. Currently, there are no requirements that the cost of access to user data should be borne by the public authority undertaking the investigation. This standard is recommended by the principle.
Below are summaries of relevant provisions:
- Any damage arising from the failure of the service provider to provider tracing assistance to the government for purposes of national security is payable by the service provider. (Section 40.4).
- Suitable monitoring equipment as may be prescribed for each type of system used will be provided by the service provider for monitoring as and when required by the licensor. (Section 41.7).
- The hardware and software required for the monitoring of calls must be engineered, provided/installed, and maintained by the service provider at the service providers cost. However the respective Government instrumentality must bear the cost of the user end hardware and leased line circuits from the MSC/Exchange/MGC/MG to the monitoring centers to be located as per their choice in their premises. (Section 41.10).
- The service provider must ensure that the necessary provision (hardware/software) is available in their equipment for doing the Lawful Interception and monitoring from a centralized location. (Section 41.20 (xvi)).
- ISP License:
- Any damages that occur from non-compliance on the part of the ISP must be paid by the ISP. (Section 33.4).
- The hardware at the ISP end and the software required for monitoring of calls must be engineered, provided/installed, and maintained by the ISP. (Section 34.7).
- Every international gateway with a route/switch having a capacity of 2Mbps must be equipped with a monitoring Centre at the cost of the ISP. The cost of meeting the requirements of the security agencies, the cost of maintenance of the monitoring equipment and infrastructure must be borne by the ISP. (Section 34.27 (a(i)).
- Office space of 10 by 10 feet with adequate power supply and air-conditioning must be provided by the ISP free of cost. (Section 34.27 (a(ii)) One local exclusive telephone must be made available by the ISP at the monitoring centre at the cost of the ISP. (Section 34.27 (a(iii)).
Analyzing the Latest List of Blocked URLs by Department of Telecommunications (IIPM Edition)
Note: The URLs repeated in the block order has not been taken into consideration. Theb total number of URLs minus the repetition is 61.
Medianama has published the DoT order, dated February 14, 2013, on its website.
What has been blocked?
The block order contains seventy eight URLs. Seventy three URLs are related to the Indian Institute of Planning and Management (IIPM). The other five URLs contain the term “highcourt”. The order also contains links from reputed news websites and news blogs including The Indian Express, Firstpost, Outlook, Times of India, Economic Times, Kafila and Caravan Magazine, and satire news websites Faking News and Unreal Times. The order also directs blocking of a public notice issued by the University Grants Commission (UGC).
The block order does not contain links to any social media website. However, some content related to IIPM has been removed but it finds no mention in the block order. Pursuant to which order or direction such content has been removed remains unclear. For example, Google has removed search results for the terms <Fake IIPM> pursuant to Court orders and it carries the following notice:
"In response to a legal request submitted to Google, we have removed 1 result(s) from this page. If you wish, you may read more about the request at ChillingEffects.org."
Are there any mistakes in the order?
The direction issued by the DoT is once again inaccurate and mired with errors. In effect, the DoT has blocked sixty one unique URLs and the block order contains numerous repetitions. By its order the DoT has directed the ISPs to block an entire blog [http://iipmexposed.blogspot.in] along with URLs to various posts in the same blog.
Reasons for Blocking Websites
According to news reports, the main reason for blocking of websites by the DoT is a Court order issued by a Court in Gwalior. The reason for issuing such a block order might have been a court proceeding with respect to defamation and removal of defamatory content thereof. However, the reasons for blocking of domain names containing the term ‘high court’, which is not at all related to the IIPM Court case is unclear. The DoT by its order has also blocked a link in the website of a internet domain registrar which carried advertisement for the domain name [www.highcourt.com].
Are the blocks legitimate?
The block order may have been issued by the DoT under Rule 10 of the Information Technology (Procedure and Safeguards for Blocking for Access of Information by Public) Rules, 2009.
The Court order seems to be an interim injunction in a defamation suit. Generally, Courts exercise utmost caution while granting interim injunction in defamation cases. According to the Bonnard Rule (Bonnard v. Perryman, [1891] 2 Ch 269) in a defamation case, “interim injunction should not be awarded unless a defence of justification by the defendant was certain to fail at trial level.” Moreover, in the case of Woodward and Frasier, Lord Denning noted “that it would be unjust to fetter the freedom of expression, when actually a full trial had not taken place, and that if during trial it is proved that the defendant had defamed the plaintiff, then should they be liable to pay the damages.” The Delhi High Court in Tata Sons Ltd. v. Green Peace International followed the Bonnard Rule and the Lord Denning’s judgements and ruled against the award of interim injunction for removal of defamatory content and stated:
“The Court notes that the rule in Bonnard is as applicable in regulating grant of injunctions in claims against defamation, as it was when the judgment was rendered more than a century ago. This is because the Courts, the world over, have set a great value to free speech and its salutary catalyzing effect on public debate and discussion on issues that concern people at large. The issue, which the defendant’s game seeks to address, is also one of public concern. The Court cannot also sit in value judgment over the medium (of expression) chosen by the defendant since in a democracy, speech can include forms such as caricature, lampoon, mime parody and other manifestations of wit.”
Therefore, it appears that the Court order has moved away from the settled principles of law while awarding an interim injunction for blocking of content related to IIPM. It is also interesting to note that in Green Peace International, the Court also answered the question as to whether there should be different standard for posting or publication of defamatory content on the internet. It was observed by the Court that publication is a comprehensive term, ‘embracing all forms and medium – including the Internet’.
Blocking a Public Notice issued by a Statutory Body of Government of India
The block order mentions a URL which contains a public notice issued by University Grants Commission (UGC) related to the derecognition of IIPM as a University. The blocking of a public notice issued by the statutory body of the Government of India is unprecedented. A public notice issued by a statutory body is a function of the State. It can only be blocked or removed by a writ order issued by the High Court or the Supreme Court and only if it offends the Constitution. However, so far, ISPs such as BSNL have not enforced the blocking of this URL.
Implementation of the order by the ISPs
As pointed out in my previous blog post on blocking of websites, the ISPs have again failed to notify their consumers the reasons for the blocking of the URLs. This lack of transparency in the implementation of the block order has a chilling effect on freedom of speech.
Freedom of Expression Gagged
Click to read the original published in the Business Line.
Freedom of expression in India is under threat. This year we have the Tamil Nadu government’s ban on Vishwaroopam, the Ashis Nandy FIR, the smothering of Kashmir’s first all girls rock band’s music, and the removal of semi-nude paintings of Hindu deities from an art gallery upon the police’s ‘suggestion’. Another Rushdie-banning controversy is upon us, and yet another Facebook user’s arrest has made the news.
Clearly, our right to freedom of expression is under an ongoing siege. The onslaught comes in varied forms: bullying by members of society, informal government action with the overhanging threat of the law, and direct use of the law (and of a variety of legislations within it). Each form is encouraged, exacerbated even, by our problematic interpretation of freedom of expression principles. Our law allows a group of intolerant people to silence a speaker by creating a threat to public order or by threatening the speaker directly, and our state is proving utterly ineffectual in protecting speech from intolerance.
Instruments Deployed
India’s first Kashmiri all-girls band is tragic proof of horizontal attacks on speech – their music was silenced by the grandmufti’s declaring it ‘un-Islamic’, and the attendant social pressure that tends to follow. They were not protected from this horizontal attack. The Palghar incident also had echoes of horizontal pressure, which was used to directly bully Shaheen Dhada, via friends advising her to apologise and strangers slapping her, before the instrument of the law was used to bully her further.
The instrument of the law can be used in invisible, informal ways, as Bangalore’s Chitrakala Parishath incident illustrates. Here, the pressure of police ‘suggestion’, carrying the implied threat of the force of the law, was used to ensure that semi-nude paintings of Hindu deities were removed from an exhibition. It appears that this police ‘suggestion’ was motivated by the fear that those paintings could trigger law and order problems.
Vishwaroopam was banned using the law, specifically section 144 of the Code of Criminal Procedure, which empowers the government to issue orders “in urgent cases of nuisance or apprehended danger”. However, orders issued under section 144 would still need to observe the boundaries drawn for it in Article 19(2) of the Constitution.
Freedom and Public Order
Some may argue that controversial or offensive speech can legitimately be restricted since “public order” is one of the grounds for which our Constitution permits the restriction of the freedom of expression. However the original text of the Constitution did not include “public order” among its permissible grounds for restriction. This was inserted in the First Amendment of the Constitution, but was fortunately accompanied by the word ‘reasonable’ before restriction, thus ensuring that the freedom of expression can only be reasonably restricted under the exceptional circumstances listed in the Constitution.
This insertion of ‘public order’ came after the Supreme Court’s invalidation of government pre-censorship of speech on public order grounds in Romesh Thapar v. State of Madras (1950), declaring that the Constitution required that “nothing less than endangering the foundations of the State or threatening its overthrow could justify curtailment of the rights to freedom of speech and expression”. Therefore, Parliament amended the Constitution to expand the grounds on which the state could restrict speech, and included ‘public order’ among the expanded grounds. The trouble with this is that the intolerant are now able to create a public order problem to silence speakers.
The Supreme Court of India, in Babulal Parate vs State Of Maharashtra (1961) found that public order must be “maintained in advance in order to ensure it”, and ruled that restriction of Article 19 freedoms of expression and assembly in the interests of public order is permissible. However, all such restrictions must continue to satisfy the reasonability test laid down in the Constitution, providing our judiciary with the opportunity to ensure that intolerance does not continue to oppress speech.
The Heckler's Veto
The use of law to bully people into silence is not unique to India. Harry Kalven termed this ‘the hecklers’ veto’: if police action silences speakers for fear that the offended listeners might create a law and order problem, this effectively allows the listeners to veto what the speaker can say. There was a time when the heckler’s veto held sway in the United States and the United Kingdom. However, both countries’ legal principles have evolved to stop pandering to the intolerant, and it is time that India does the same.
Justice Hugo Black of the US Supreme Court, in his Feiner v. New York (1951) dissent, argued that the police must make all reasonable efforts to protect the speaker’s constitutional right to speak before interfering with this right. This dissenting opinion was later hailed as visionary. The US Supreme Court subsequently gradually recognised the evils of the heckler’s veto, which privileges and encourages intolerance. The United Kingdom also progressively narrowed its reading of the Public Order Act to ensure that speech is not restricted unless immediate violence is feared, and is now decriminalising insults which are not directed at a clearly identifiable victim.
The Indian Supreme Court’s judgment in the Rangarajan v. P. Jagjivan Ram (1989) echoes Justice Black’s denouncement of the heckler’s veto. It declares, “freedom of expression cannot be suppressed on account of threat of demonstration and processions or threats of violence. That would tantamount to …surrender to blackmail and intimidation. It is the duty of the State to protect the freedom of expression since it is a liberty guaranteed against the State. The State cannot plead its inability to handle the hostile audience problem”. However other judgments have shied away from confronting the fact that speech-related public order problems created by intolerance, not by speech.
Our legal system needs to take a firm, consistent stand against the heckler’s veto. We need to stop mirroring the evils of outdated law in fresh legislations like the Information Technology Act, and work instead to remove law and practices that institutionalise intolerance.
(The author teaches at National Law University, Delhi and is Fellow, Centre for Internet and Society.)
The Omnishambles of UID, shrouded in its RTI opacity
Surveillance Camp IV: Disproportionate State Surveillance - A Violation of Privacy
This article by Katitza Rodriguez and Elonnai Hickok was originally published by the Electronic Frontier Foundation on February 13, 2013.
States around the world are faced daily with the challenge of protecting their populations from potential and real threats. To detect and respond to them, many governments surveil communication networks, physical movements, and transactional records. Though surveillance by its nature compromises individual privacy, there are exceptional situations where state surveillance is justified. Yet, if state surveillance is unnecessary or overreaching, with weak legal safeguards and a failure to follow due process, it can become disproportionate to the threat—infringing on people's privacy rights.
Internationally, regulations concerning government surveillance of communications vary in approach and effectiveness, often with very weak or nonexistent legal safeguards. Some countries have strong regulations for the surveillance of communications, yet these regulations may be largely ineffective or unenforceable in practice. Other countries have no legal safeguards or legal standards differing vastly according to the type of communication data targeted. This is why, EFF organized at the end of last year a State Surveillance and Human Rights Camp in Brazil to build upon this discussion and focused on how states are facilitating unnecessary and disproportionate surveillance of communications in ways that lead to privacy violations.
State-Mandated Identity Verification
In 2012 the Constitutional Court in South Korea declared that country's "real-name identification system" unconstitutional. The system had mandated that any online portal with more than 100,000 daily users had to verify the identity of their users.[1]This meant that the individual has to provide their real name before posting comments online. The legal challenge to this system was raised by People's Solidarity for Participatory Democracy (PSPD)'s Public Law Center and Korean Progressive Network—Jinbonet among others.
Korea University professor Kyung-shin Park, Chair of PSPD's Law Center told EFF that portals and phone companies would disclose identifying information about six million users annually—in a country of only 50 million people. The South Korean Government was using perceived online abuses as a convenient excuse to discourage political criticism, professor Park told EFF:
The user information shared with the police most commonly has been used by the government to monitor the anti-governmental sentiments of ordinary people. All this has gone on because the government, the legislature, and civil society have not clearly understood the privacy implications of turning over identifying information of individuals.
The decision by the South Korean Constitutional Court to declare the "real identification system" unconstitutional was a win for user privacy and anonymity because it clearly showed that blanket mandates for the disclosure of identifying information, and the subsequent sharing of that data without judicial authorization, are a disproportionate measure that violates the rights of individuals.[2]
States Restrict Encryption and Demand Backdoors
Some States are seeking to block, ban, or discourage the use of strong encryption and other privacy enhancing tools by requiring assistance in decrypting information. In India service providers are required to ensure that bulk encryption is not deployed. Additionally, no individual or entity can employ encryption with a key longer than 40 bits. If the encryption equipments is higher than this limit, the individual or entity will need prior written permission from the Department of Telecommunications and must deposit the decryption keys with the Department.[3]The limitation on encryption in India means that technically any encrypted material over 40 bits would be accessible by the State. Ironically, the Reserve Bank of India issued security recommendations that banks should use strong encryption as higher as 128-bit for securing browser.[4]In the United States, under the Communications Assistance for Law Enforcement Act, telecommunication carriers are required to provide decryption assistance only if they already possess the keys (and in many communications system designs, there's no reason carriers should need to possess the keys at all). In 2011, the US Government proposed a bill that would place new restrictions on domestic development or use of cryptography, privacy software, and encryption features on devices. The bill has not been adopted.
Allowing only low levels of encryption and requiring service providers to assist in the decryption of communications, facilitates surveillance by enabling States easier access to data and preventing individuals from using crypto tools to protect their personal communications.
States Establish Blanket Interception Facilities
In Colombia, telecommunications network and service providers carrying out business within the national territory must implement and ensure that interception facilities are available at all times to state agencies as prescribed by law. This is to enable authorized state agencies to intercept communications at any point of time. In addition to providing interception facilities, service providers must also retain subscriber data for a period of five years, and provide information such as subscriber identity, invoicing address, type of connection on request, and geographic location of terminals when requested.
Though Colombia has put in place regulations for the surveillance of communications, these regulations allow for broad surveillance and do not afford the individual clear rights in challenging the same.
Conclusion
The examples above demonstrate that, although state surveillance of communications can be justified in exceptional instances, it leads to the violation of individual privacy when implemented without adequate legal safeguards. Clearly there is a need for international principles articulating critical and necessary components of due process for the surveillance of communications. Those strong legal safeguards are necessary not only in countries that don't have laws in place, but also in countries where laws are lacking and fail to adequately protect privacy. Last year, EFF organized the State Surveillance and Human Rights Camp to discuss a set of International Principles on State Surveillance of Communications, a global effort led by EFF and Privacy International, to define, articulate, and promote legal standards to protect individual privacy when the state carries out surveillance of communications.
[1].Constitutional Court's Decision 2010 Hunma 47, 252 (consolidated) announced August 28, 2012.
[2].The illegality of this practice was proved by a High Court decision handed down 2 months after the Constitutional Court's decision in August 2012. Seoul Appellate Court 2011 Na 19012, Judgment Announced October 18, 2012. This case was prepared and followed singularly by PSPD Public Interest Law Center.
[3].License Agreement for Provision of Internet Services Section 2.2 (vii)
[4].Reserve Bank of India. Internet Banking Guidelines. Section (f (2)).
BigDog is Watching You! The Sci-fi Future of Animal and Insect Drones
This research was undertaken as part of the 'SAFEGUARDS' project that CIS is undertaking with Privacy International and IDRC.
Just when we thought we had seen it all, the US Defence Advanced Research Projects Agency (DARPA) funded another controversial surveillance project which makes even the most bizarre sci-fi movie seem like a pleasant fairy-tale in comparison to what we are facing: animal and insect drones.
Up until recently, unmanned aerial vehicles (UAVs), otherwise called drones, depicted the scary reality of surveillance, as robotic pilot-less planes have been swarming the skies, while monitoring large amounts of data without people´s knowledge or consent. Today, DARPA has come up with more subtle forms of surveillance: animal and insect drones. Clearly animal and insect-like drones have a much better camouflage than aeroplanes, especially since they are able to go to places and obtain data that mainstream UAVs can not.
India´s ´DARPA´, the Defence Research and Development Organisation (DRDO), has been creating UAVs over the last ten years, while the Indian Army first acquired UAVs from Israel in the late 1990s. Yet the use of all UAVs in India is still poorly regulated! Drones in the U.S. are regulated by the Federal Aviation Administration (FAA), whilst the European Aviation Safety Agency (EASA) regulates drones in the European Union. In India, the Ministry of Civil Aviation regulates drones, whilst the government is moving ahead with plans to replace the Directorate General of Civil Aviation (DGCA) with a Civil Aviation Authority. However, current Indian aviation laws are vague in regards to data acquired, shared and retained, thus not only posing a threat to individual´s right to privacy and other human rights, but also enabling the creation of a secret surveillance state.
The DRDO appears to be following DARPA´s footsteps in terms of surveillance technologies and the questions which arise are: will animal and insect drones be employed in India in the future? If so, how will they be regulated?
BigDog/LS3
Apparently having UAVs flying above us and monitoring territories and populations without our knowledge or consent was not enough. DARPA is currently funding the BigDog project, which is none other than a drone dog, a four-legged robot equipped with a camera and capable of surveillance in disguise. DARPA and Boston Dynamics are working on the latest version of BigDog, called the Legged Squad Support System (LS3), which can carry 400 pounds of gear for more than 20 miles without refuelling. Not only can the LS3 walk and run on all types of surfaces, including ice and snow, but it also has ´vision sensors´ which enable it to autonomously maneuver around obstacles and follow soldiers in the battle field. The LS3 is expected to respond to soldiers' voice commands, such as 'come', 'stop' and 'sit', as well as serve as a battery charger for electronic devices.
BigDog/LS3 is undoubtedly an impressive technological advancement in terms of aiding squads with surveillance, strategic management and a mobile auxiliary power source, as well as by carrying gear. Over the last century most technological developments have manifested through the military and have later been integrated in societies. Many questions arise around the BigDog/LS3 and its potential future use by governments for non-military purposes. Although UAVs were initially used for strictly military purposes, they are currently also being used by governments on an international level for civil purposes, such as to monitor climate change and extinct animals, as well as to surveille populations. Is it a matter of time before BigDog is used by governments for ´civil purposes´ too? Will robotic dogs swarm cities in the future to provide ´security´?
Like any other surveillance technology, the LS3 should be legally regulated and current lack of regulation could create a potential for abuse. Is authorisation required to use a LS3? If so, who has the legal right to authorise its use? Under what conditions can authorisation be granted and for how long? What kind of data can legally be obtained and under what conditions? Who has the legal authority to access such data? Can data be retained and if so, for how long and under what conditions? Do individuals have the right to be informed about the data withheld about them? Just because it´s a ´dog´ should not imply its non-regulation. This four-legged robot has extremely intrusive surveillance capabilities which may breach the right to privacy and other human rights when left unregulated.
Humming Bird Drone
|
|
|---|
| Source: HighTech Edge |
TIME magazine recognised DARPA for its Hummingbird nano air vehicle (NAV) and named the drone bird one of the 50 best inventions of 2011. True, it is rather impressive to create a robot which looks like a bird, behaves like a bird, but serves as a secret spy.
During the presentation of the humming bird drone, Regina Dugan, former Director of DARPA, stated:
"Since we took to the sky, we have wanted to fly faster and farther. And to do so, we've had to believe in impossible things and we've had to refuse to fear failure."
Although believing in 'impossible things' is usually a prerequisite to innovation, the potential implications on human rights of every innovation and their probability of occurring should be examined. Given the fact that drones already exist and that they are used for both military and non-military purposes, the probability is that the hummingbird drone will be used for civil purposes in the future. The value of data in contemporary information societies, as well as government's obsession with surveillance for ´national security´ purposes back up the probability that drone birds will not be restricted to battlefields.
So should innovation be encouraged for innovation’s sake, regardless of potential infringement of human rights? This question could open up a never-ending debate with supporters arguing that it´s not technology itself which is harmful, but its use or misuse. However the current reality of drones is this: UAVs and NAVs are poorly regulated (if regulated at all in many countries) and their potential for abuse is enormous, given that ´what happens to our data happens to ourselves....who controls our data controls our lives.´ If UAVs are used to surveille populations, why would drone birds not be used for the same purpose? In fact, they have an awesome camouflage and are potentially capable of acquiring much more data than any UAV! Given the surveillance benefits, governments would appear irrational not to use them.
MeshWorms and Remote-Controlled Insects
 |
|---|
| Source: NY Daily News |
Think insects are creepy? Now we can have a real reason to be afraid of them. Clearly robotic planes, dogs and birds are not enough.
DARPA´s MeshWorm project entails the creation of earthworm-like robots that crawl along surfaces by contracting segments of their bodies. The MeshWorm can squeeze through tight spaces and mold its shape to rough terrain, as well as absorb heavy blows. This robotic worm will be used for military purposes, while future use for ´civil purposes´ remains a probability.
Robots, however, are not only the case. Actual insects are being wirelessly controlled, such as beetles with implanted electrodes and a radio receiver on their back. The giant flower beetle´s size enables it to carry a small camera and a heat sensor, which constitutes it as a reliable mean for surveillance.
Other drone insects look and fly like ladybugs and dragonflies. Researchers at the Wright State University in Dayton, Ohio, have been working on a butterfly drone since 2008. Former software engineer Alan Lovejoy has argued that the US is developing mosquito drones. Such a device could potentially be equipped with a camera and a microphone, it could use its needle to abstract a DNA sample with the pain of a mosquito bite and it could also inject a micro RFID tracking device under peoples´ skin. All such micro-drones could potentially be used for both military and civil purposes and could violate individuals´ right to privacy and other civil liberties.
Security vs. Privacy: The wrong debate
09/11 was not only a pioneering date for the U.S., but also for India and most countries in the world. The War on Terror unleashed a global wave of surveillance to supposedly enable the detection and prevention of crime and terrorism. Governments on an international level have been arguing over the last decade that the use of surveillance technologies is a prerequisite to safety. However, security expert, Bruce Schneier, argues that the trade-off of privacy for security is a false dichotomy.
Everyone can potentially be a suspect within a surveillance state. Analyses of Big Data can not only profile individuals and populations, but also identify ‘branches of communication’ around every individual. In short, if you know someone who may be considered a suspect by intelligence agencies, you may also be a suspect. The mainstream argument “I have nothing to hide, I am not a terrorist’ is none other than a psychological coping mechanism when dealing with surveillance. The reality of security indicates that when an individual’s data is being intercepted, the probability is that those who control that data can also control that individual’s life. Schneier has argued that privacy and security are not on the opposite side of a seesaw, but on the contrary, the one is a prerequisite of the other. Governments should not expect us to give up our privacy in exchange for security, as loss of privacy indicates loss of individuality and essentially, loss of freedom. We can not be safe when we trade-off our personal data, because privacy is what protects us from abuse from those in power. Thus the entire War on Terror appears to waged through a type of phishing, as the promise of ´security´ may be bait to acquire our personal data.
Since the 2008 Mumbai terrorist attacks, India has had more reasons to produce, buy and use surveillance technologies, including drones. Last New Year´s Eve, the Mumbai police used UAVs to monitor hotspots, supposedly to help track down revellers who sexually harass women. The Chennai police recently procured three UAVs from Anna University to assist them in keeping an eye on the city´s vehicle flow. Raj Thackeray´s rally marked the biggest surveillance exercise ever launched for a single event, which included UAVs. The Chandigarh police are the first Indian police force to use the ´Golden Hawk´ - a UAV which will keep a ´bird´s eye on criminal activities´. This new type of drone was manufactured by the Aeronautical Development Establishment (one of DRDO's premier laboratories based in Bangalore) and as of 2011 is being used by Indian law enforcement agencies.
Although there is no evidence that India currently has any animal or insect drones, it could be a probability in the forthcoming years. Since India is currently using many UAVs either way, why would animal and/or insect drones be excluded? What would prevent India from potentially using such drones in the future for ´civil purposes´? More importantly, how are ´civil purposes´ defined? Who defines ´civil purposes´and under what criteria? Would the term change and if so, under what circumstances? The term ´civil purposes´ varies from country to country and is defined by many political, social, economic and cultural factors, thus potentially enabling extensive surveillance and abuse of human rights.
Drones can potentially be as intrusive as other communications surveillance technologies, depending on the type of technology they´re equipped with, their location and the purpose of their use. As they can potentially violate individuals´ right to privacy, freedom of expression, freedom of movement and many other human rights, they should be strictly regulated. In Europe UAVs are regulated based upon their weight, as unmanned aircraft with an operating mass of less than 150kg are exempt by the EASA Regulation and its Implementation Rules. This should not be the case in India, as drones lighter than 150kg can potentially be more intrusive than other heavier drones, especially in the case of bird and insect drones.
Laws which explicitly regulate the use of all types of drones (UAVs, NAVs and micro-drones) and which legally define the term ´civil purposes´ in regards to human rights should be enacted in India. Some thoughts on the authorisation of drones include the following: A Special Committee on the Use of All Drones (SCUAD) could be established, which would be comprised of members of the jury, as well as by other legal and security experts of India. Such a committee would be the sole legal entity responsible for issuing authorisation for the use of drones, and every authorisation would have to comply with the constitutional and statutory provisions of human rights. Another committee, the Supervisory Committee on the Authorisation of the Use of Drones (lets call this ´SCAUD´), could also be established, which would also be comprised by (other) members of the jury, as well as by (other) legal and security experts of India. This second committee would supervise the first and it would ensure that SCUAD provides authorisations in compliance with the laws, once the necessity and utility of the use of drones has been adequately proven.
It´s not about ´privacy vs. security´. Nor is it about ´privacy or security´. In every democratic state, it should be about ´privacy and security´, since the one cannot exist without the other. Although the creation of animal and insect drones is undoubtedly technologically impressive, do we really want to live in a world where even animal-like robots can be used to spy on us? Should we be spied on at all? How much privacy do we give up and how much security do we gain in return through drones? If drones provided the ´promised security´, then India and all other countries equipped with these technologies should be extremely safe and crime-free; however, that is not the case.
In order to ensure that the use of drones does not infringe upon the right to privacy and other human rights, strict regulations are a minimal prerequisite. As long as people do not require that the use of these spying technologies are strictly regulated, very little can be done to prevent a scary sci-fi future. That´s why this blog has been written.
Analyzing Draft Human DNA Profiling Bill 2012
 DNA Working Draft 29.04.2012.pdf
—
PDF document,
207 kB (212695 bytes)
DNA Working Draft 29.04.2012.pdf
—
PDF document,
207 kB (212695 bytes)
Freedom of expression online Wilton Park event
 Participants list 110213.pdf
—
PDF document,
45 kB (46194 bytes)
Participants list 110213.pdf
—
PDF document,
45 kB (46194 bytes)
Don’t SLAPP free speech
Sunil Abraham's column with inputs from Snehashish Ghosh was published in Tehelka on February 3, 2013 (Issue 9 Volume 10)
Despite our best efforts, we have not managed to get a copy of the court order. Meanwhile, there has been a lot of speculation among Internet policy experts on Twitter. What is the title of the case? Which judge issued the order? Who is the affected party? Why have mainstream media houses like Outlook not been served notice by the court? Is the infamous Section 66A of the IT Act to be blamed? That is highly unlikely. News reports suggest that a lower court in Gwalior has issued an ad interim injunction in a defamation suit. Most experts agree that this is a SLAPP (Strategic Litigation Against Public Participation) suit, where a company uses the cost of mounting a legal defence to silence critics.
Bullies with deep pockets use the law in very creative ways, such as forum shopping, forum shifting and the use of proxies. Forum shopping can be best understood through the example of mining giant Fomento suing Goan blogger Sebastian Rodrigues for $1 billion at the Kolkata High Court, even though Goa would have been a more logical location. Though IIPM lost an earlier case against Careers360 before the Uttaranchal High Court, the offending URLs from that case are included in the latest block order, exemplifying successful forum shifting. The doctrine of ‘res subjudice’ does not permit courts to proceed in a matter which is “directly and substantially” similar to a previous suit between the same parties. Proxies are usually employed to circumvent this procedural doctrine.
Article 19(2) of our Constitution empowers the State to create laws that place eight types (depending on how you count) of reasonable restrictions on the freedom of speech and expression. One of these reasonable restrictions is defamation. Tort law on defamation in India has been mostly borrowed from common law principles developed in the UK, which include a series of exceptions where the law cannot be used. In the present context, the exceptions important for the IIPM case include: fair and bona fide comment and matter of public interest. In addition, Section 499 of the Indian Penal Code provides for 10 exceptions to defamation. The exceptions relevant to this case are: “first: imputation of truth which public good requires to be made or published”, “ninth: imputation made in good faith by person for protection of his or other’s interests” and “tenth: caution intended for good of person to whom conveyed or for public good”. The criminal law on defamation in India is based on robust legal principles, but for the sake of public interest it’d be best to do away with such a law as it has far-reaching, chilling effects on free speech.
On interim injunctions in defamation suits, the Delhi High Court set an important precedent protecting free speech in 2011. While applying the English principle — the Bonnard Rule — the court in Tata Sons Pvt Ltd versus Greenpeace International held that a higher standard should be adhered to while granting an interim injunction in a defamation suit, because such an injunction might impinge upon freedom of expression and thus potentially be in violation of the Indian Constitution. This century-old rule states that “until it is clear that an alleged libel is untrue… the importance of leaving free speech unfetter – ed is a strong reason in cases of libel for dealing most cautiously and warily with the granting of interim injunctions…”
In the same case, the Court rejected the argument that since it was published online and thus had wider reach and greater permanence, an injunction should be granted. It observed that “publication is a comprehensive term, embracing all forms and mediums — including the Internet”, thus ruling out special treatment for the Inter net in cases of defamation. That is good news for free speech online in India. Now let’s stick to it.
Research Initiative: Women in India's IT Industry
The recent events and subsequent discussions surrounding the brutal gang rape and murder of a young Delhi woman on a bus last December in Munirka, New Delhi, have prompted dialogue in mainstream discourses about the position of women in India, and have lead many to scrutinize the treatment of women within various spheres of Indian society. What has become increasingly apparent following the events of December 16th is that effective longterm change for Indian women cannot be achieved by harsher consequences or more rigorous transport regulations, but instead through widespread recognition of the routine discrimination faced by Indian women in their public, private and professional lives. The latter sphere is of particular interest to the Indian context, as although the last two decades have seen an unprecedented number of Indian women enter the formal workforce, issues of female economic empowerment tend to get downplayed when juxtaposed against the entirety of the system of discrimination and violence faced by women in India.
As a brief foray into the reality of female economic empowerment in India, CIS has decided to carry out a small though hopefully telling research project on some of the largest corporate players in the Indian IT industry. The aim of this research is to gain a better understanding of the state of female employment, gender equality and the qualitative experience of being a working woman in one of the most important and rapidly growing economic sectors in the country.
Using NASSCOM's annual industry ratings from 2007-2012,[1] we put together a list of the six software companies headquartered in India that appeared in the top five spots at least twice between the years 2007-2012. These companies are Tata Consultancy Services Ltd., Infosys Ltd., Wipro Ltd., HCL Tech Ltd., Tech Mahindra and Mahindra Satyam. Through formal requests for data and a handful of qualitative interviews, we will be gathering information from these companies and their employees that will eventually by compiled into a short report that will be publicly available on our website.
(A brief explanation of why we chose to use NASSCOM's industry list can be found at the end of this article,[2] along with some notes on the change of ownership of Mahindra Satyam and its merger with Tech Mahindra).[3]
Why the IT Industry?
In 2012, an international consulting and management firm called Booz & Company released “The Third Billion”, a global ranking of the level of economic empowerment attained by woman on 128 countries. The indicators used included equal pay for equal work, non-discrimination policies, the male-to-female-male employee ratio, and equality in terms of female managers and senior business leaders.[4] India rated quite poorly at spot 115.[5] Further, the International Labour Force recently reported that the rate of female participation in the total labour force[6] in India has fallen from 37% in 2004-05 to 29% in 2009-10, leaving India at the 11th lowest spot out of 131 countries.[7] Despite these declining rates, it was estimated in 2010 that approximately 5.5 million Indian women were entering the formal workforce each year at that period in time,[8] and though the aforementioned statistics likely indicate that a larger proportion of men are entering the formal workforce each year than women, this is a significant amount of employees, many of whom will be facing a unique set of challenges in the workplace simply because of their gender. In fact, research done by the Centre for Talent Innovation has found that 55% of female Indian employees routinely encounter such severe bias in the workplace that they disengage from their work or consider dropping out altogether.[9]
This is where the IT industry comes in. From an aggregate revenue of USD 3.9 billion in Fiscal Year (FY) 1998[10] to more than USD 100 billion in FY2012,[11] the Indian IT-BPO industry has been growing exponentially over the last 15 years, and it continues to be one of the fastest growing sectors in the Indian economy. Further, it has rapidly become one of the most economically significant industries in India in terms of share of total exports (approximately 25% for FY2012)[12] export revenue (USD 69.1 billion and growing by more than 16%)[13] and proportion of national GDP (from 1.2% in FY1998 to 7.5% in FY2012).[14] IT services alone account for more than half of the software and services exports in the industry, and is the fastest growing segment of the sector at 18%.[15] Further, NASSCOM estimates that the sector will create 230,000 jobs in FY2012,[16] increasing the number of individuals employed directly in India's IT-BPO industry to about 2.8 million individuals.[17] The industry is estimated to indirectly employ another 8.9 million people.[18]
Because the IT industry in India is such an important source of employment for young Indian professionals (the median age of IT-BPO employees in India was about 24[19] in 2011), and because an unprecedented amount of those young professionals are women (women made up 42% of India's college graduates in 2010, and that figure was expected to continue to rise),[20] IT companies have the potential to become leading examples of women-friendly employers. However, according to DataQuest's Best Employer Survey 2012, the percentage of women employed in the IT industry in India has actually decreased from 26% in 2010 to 22% in 2012[21] even though the number of jobs created in this sector continues to increase annually. Again, these statistics most likely point to a larger number of males available for employment than females (and therefore a larger proportion of men being employed), but they also show that the number of women employed in the IT sector is not significantly increasing (or even increasing at all).
Considering, then, how important the IT industry may be for the employment of young female professionals (and if it is not now, it will be soon), the responsibility to create nondiscriminatory and comfortable workplace environments should fall heavily on the largest and most economically significant companies in the software sector, as they have the opportunity to set precedents not only for the rest of the industry but for Indian employers as a whole.
How are these industry giants faring in terms of the treatment of their female employees?
To commence this research, I have collected some basic facts about the Board of Directors and executive management teams of the six Indian IT companies off of their websites and annual reports. This brief preliminary foray into the industry has revealed that although many of these companies promote gender equality in the workplace and women in senior positions of authority, the Indian software sphere continues to be almost entirely male-dominated.
The collected statistics on Board members and executive management teams are listed below. It bears keeping in mind that while the information on the Board of Directors may be quite reliable (depending on how recently each company has updated their website) and therefore appropriate to use as a tool of comparative analysis, the information on the executive management teams can be misleading, as each company appears to have a different criteria of what constitutes a senior management team (for example, Tata Consultancy Services lists two individuals, their CEO and CFO, as their executive management team, but Wipro Ltd. lists 24 individuals from a variety of different departments).
Because we were not certain of how recently each company had updated its website, we have prioritized the data on the Boards from their annual Investor's Reports over the information available on their websites.
Tata Consultancy Services Limited
TCS' annual report for the 2011-2012 fiscal year reports a 14 member Board of Directors with one female non-executive director. This woman is not Indian. The report also lists a 28-member strong management team with two female members, and their website lists
- Number of women on the Board: 1/14
- Number of women holding executive management positions: 2/30
Infosys Limited
Infosys Ltd. has 15 Board members: six executive members, none of which are women; one male chairperson; and eight non-executive independent members, one of whom is a woman, but not an Indian woman.
Further, Infosys lists 14 individuals in their executive management team,[22] one of whom is a woman. It is interesting to note that this female member is the group head of Human Resources as well as being one of five senior Vice Presidents.[23] Infosys also has an Executive Council made up of 13 members, including one Indian woman.
Number of women on the Board: 1/15
Number of women holding executive management positions: 1/14
Wipro Limited
Wipro's Board of Directors is made up of 12 men: one executive chairman, two executive directors, and nine independent directors.
As for their executive management team, the website lists 24 executive leaders, two of whom are women.[24] Wipro also has a Corporate Executive Council of six men.
- Number of women on Board: 0/12
- Number of women in executive management team: 2/23
HCL Tech Limited
HCL's Board has nine members, two of whom are executive members. The other seven members are listed as being independent, non-executive members. One of these non-executive members is a woman; she is not Indian.
On their website[25] they list 18 members of their leadership team, none of whom are female.
- Number of women on Board: 1/9
- Number of women holding executive management positions: 0/18
Tech Mahindra
On Tech Mahindra's Board of Directors sits a non-executive chairman, one executive member, six non-executive independent members, and three non-executive directors. None of these individuals are female. On their website, seven employees appear to make up the leadership team of this company, one of whom is a woman. Interestingly, this individual is also the head of HR.[26]
- Number of women on Board: 0/11
- Number of women holding executive management positions: 1/7
Mahindra Satyam
According to their 2011-2012 annual report, Mahindra Satyam's Board of Directors boosts 6 members: a male chairman, one male CEO, and four non-executive board members, one of whom is an Indian woman.
Further, there appears to be six members of the leadership team[27] including the CEO, none of whom are female.
- Number of women on Board: 1/6
- Number of women holding executive management positions: 0/6
Summary of Board of Director Data
- Number of female chairpersons in the 6 largest IT companies in India: 0/6
- Number of women seated on the Board of Directors of the top 6 IT companies in India: 4/67
- Executive (excluding chairmen/vice-chairmen): 0/14
- Non-Executive (excluding chairmen/vice-chairmen): 4/47
- Female Indian members: 1/4
- Number of female employees in senior management positions: 6/98
While these numbers may be sobering, they are not exceptionally low, or even below average. According to The Globe and Mail's 11th annual Board Games report on corporate governance, the percentage of Board seats held by women on Boards of Directors in the Indian corporate sector in 2012 was 5.3%, meaning that, at an approximately 6% of seats held by female members, our very small sample size is actually sitting just above the Indian average. However, when compared to the other BRIC countries at 5.1%, 5.9% and 8.5% respectively,[28] India is still lagging behind when it comes to having women in positions of senior authority in the corporate world.
Further, considering that these are the largest corporate IT companies in the industry, and the majority carry out activities across the globe, they probably have, on average, larger and more diverse Boards of Directors than our average mid- to large-sized Indian software company. Further, two out of six companies do not even have one female member on their Board. As for those remaining four, it is likely that these companies may be the exception and not the rule when it comes to the number of women on the Boards in the Indian IT.
As for executive management, the world average for the percentage of women in senior management roles was 21% in 2012, a meagre increase from the global average of 19% in 2004.[29] The same study that produced these figures also found that the proportion of women holding senior management positions in India was 14%, placing the data from our sample size way below the curve at approximately 6%. However, due to issues discussed earlier in this post, this figure is not an accurate representation of the executive management teams of all six companies; future research will hopefully provide us with more factual statistics.
This is not to say that the IT sector in India is the only industry that should be concerned with its low rates of female employment and attainment of seniority, nor should its industry giants be the only corporate entities publicly scrutinized in this manner. The economic empowerment of women in India is an on-going struggle that is played out in many spheres in the Indian society, including the non-profit sector. In fact, if we perform a similar breakdown of CIS' Board of Directors and staff, the results are comparable to those of the IT companies:
According to our 2011-2012 annual report, our Board of Directors boosts 8 members, two of whom are executive members of CIS' management team. One of these individuals is an Indian woman.
Further, of our 14 staff members, four are women.
[1]. NASSCOM. 2012. Industry Rankings: Top 20 Players in IT Services. [online] Retrieved from http://www.nasscom.org/industry-ranking on January 21st, 2013.
[2]. The NASSCOM industry ranking is a well-regarded annual ranking of the IT sector in India that is often used as a resource in various research initiatives and similar publications, and it appears to be widely accepted as a legitimate ranking by both those within the industry and by entities from other sectors. The ranking is determined using revenue information provided by each company for their activities in India, which we thought was a strong indicator of their significance to the industry and the Indian economic engine as a whole. Finally, NASSCOM carries out this ranking each year, which will allow us to use a similar methodology in choosing our research subjects should we choose to reproduce this research annually.
[3]. If you look at the NASSCOM list of top 20 for 2007-2008, you will see that a company called Satyam Computer Services. This company was taken over by the Mahindra Group in 2009, and was rebranded as Mahindra Satyam to reflect its new parent company. This is why Mahindra Satyam is included in our list, though it first appeared on the NASSCOM Industry Rankings for the 2011-2012 fiscal year; we counted the appearance of Satyam Computer Services in the fourth spot in the rankings for 2007-2008 as a point towards Mahindra Satyam.
Further, it was announced in March of 2012 that Mahindra Satyam and Tech Mahindra would be merging; however, this had not yet happened by the end of the 2012 fiscal year and therefore we will treat Mahindra Satyam and Tech Mahindra as separate and independent entities in this research project.
[4]. Aquirre, D., Hoteit, L., Rupp, C., & Sabbaugh, K. 2012. Empowering the Third Billion: Women and the World of Work in 2012. [pdf] Booz & Company. Accessible at: http://bit.ly/SXdZ6P
[5]. ibid.
[6]. The rate of female labour participation indicates the proportion of the female population above the age of 15 that supplies labour for the production of goods and services on the formal market in a given time period.
[7]. International Labour Organization. February 13, 2013. India: Why is Women's Labour Force Participation Dropping? [online] Retrieved from http://bit.ly/11EGYCM on February 22nd, 2013.
[8]. Hewlett, S. A., Fredman, C., Leader-Chivee, L., & Rashid, R. 2010. The Battle for Female Talent in India. New York: Center for Work-Life Policy.
[9]. Hewlett, S. A. November 1, 2012. “More Women in the Workforce Could Raise GDP by 5%.” Harvard Business Review. [online] Retrieved from http://bit.ly/YrxyFA February 23rd, 2013.
[10]. Embassy of India. 2007. India's Information Technology Industry. [online] Retrieved from http://www.indianembassy.org/indiainfo/india_it.htm on February 23rd, 2013.
[11]. NASSCOM. 2012. Indian IT-BPO Industry. [online] Retrieved from http://www.nasscom.in/indian-itbpo-industry on February 24th, 2013.
[12]. ibid.
[13]. ibid.
[14]. ibid.
[15]. NASSCOM. 2012. IT Services. [online] Retrieved from http://www.nasscom.in/it-services on February 25th, 2013.
[16]. NASSCOM. 2012. Indian IT-BPO Industry. [online] Retrieved from http://www.nasscom.in/indian-itbpo-industry on February 24th, 2013.
[17]. ibid.
[18]. ibid.
[19]. Business Standard. January 31, 2011. Employee Retention Key Challenge for IT, BPO Cos. [online] Retrieved from http://bit.ly/13sCizA on February 24th, 2013.
[20]. Hewlett, Sylvia A. & Rashid, Ripa. December 3, 2010. “India's Crown Jewels: Female Talent.” Harvard Business Review. [online] Retrieved from http://bit.ly/gpv7CQ on February 23rd, 2013.
[21]. Sharma, P. October 29, 2012. “Gender Inclusivity, Still a Key Challenge.” DataQuest. [online] Retrieved from http://bit.ly/TPkz1F on February 19th, 2013.
[22]. Information retrieved from: http://infy.com/cVfEwp
[23]. According to the Grant Thornton International Business Report for 2012, the majority of women employed in senior management positions are heads/directors of Human Resources (21%). It has been argued that women tend to get employed in Human Resources due to a perceived “natural transfer of skills”--meaning that women are believed to be pre-disposed to excel at Human Resources-related tasks and responsibilities simply because of the experiences and norms of their gender. For a more profound discussion of this phenomenon, please visit: http://www.hreonline.com/HRE/view/story.jhtml?id=533345673
[24]. Information retrieved from: http://bit.ly/13sBtXJ
[25]. Information retrieved from: http://bit.ly/Kdm0vP
[26]. Please see footnote 23
[27]. Information retrieved from: http://bit.ly/148kLsv
[28]. Information retrieved from: http://bit.ly/XVvpp3
[29]. Grant Thornton. 2012. “Women in Senior Management: Still Not Enough.” in Grant Thornton International Business Report 2012. Grant Thornton. [pdf] Accessible at: http://bit.ly/HCjKTG
Women in the IT Industry: Request for Data
Click to see the Letter of Survey Request and the Income Bracket Form
As introduced in an earlier blog, CIS has begun a short research project on female employees in the IT industry in India. This project aims to gather quantitative and qualitative data on women employed by the six largest Indian software companies in order to generate insight into whether or not these employers foster workplaces that are conducive to female economic empowerment. We have decided to gather some very basic quantitative data for this project by directly asking each of these companies to provide some information on data points that we deemed important indicators of women-friendly workplaces. This request has been carried out via post and, when possible, electronic mail.
In this letter of request, we have asked each of the companies to provide information on the number of women they employ, how much paid leave employees are allocated per month and per year, whether or not they have any complaints committees in place as per the Vishaka guidelines, and whether or not they offer any support for childcare or childcare services on their worksites.
Further, we also requested that they complete a form listing ascending monthly incomes (from below Rs. 19,999 to above Rs. 1.5 crore) by filling in how many female and male employees they employ in each income bracket. A copy of the letter and the form are attached to this blog post.
Each of these letters was addressed to the Chief Human Resources Officer (or equivalent title) at the corporate headquarters, and mailed as Registered Post, Acknowledgement Due on February the 19th, 2013. We plan to send two more copies of this letter on the same date for the next two months.
The contacts and addresses that these letters were sent to are listed below. All of this information was gathered from publicly available sources.
Tech Mahindra Ltd.:
Contact:
Sujitha Karnad - Senior Vice President: HR & QMG for IT Services
Address:
Tech Mahindra Limited, Department of Human Resources
Sharda Centre, Off Karve Road,
Pune 411004, Maharashtra
India
Mahindra Satyam:
Contact:
Hari Thalapalli - Chief Marketing Officer and Chief People Officer
Address:
Satyam Computer Services Limited, Department of Human Resources
Mahindra Satyam Technology Center
Survey No.62/1A, Qutubullapaur Mandal
Bahadurpally Village, RR Dist
Hyderabad 500043
HCL Technologies Ltd.:
Contact:
Prithvi Shergill - Chief Human Resources Officer
Address:
HCL Technologies Limited, Department of Human Resources
A-104, Sector 58, Noida
Uttar Pradesh, 201 303
India
Tata Consultancy Services Ltd.:
Contact:
Ajoyendra Mukherjee - Executive Vice President & Head, Global Human Resources
Address:
Tata Consultancy Services, Department of Human Resources
TCS House,
Raveline street,
Fort, Mumbai, 400 001
India
Infosys Ltd.:
Contact:
Nandita Gurjar - Group Head of Human Resources
Address:
Infosys Limited, Department of Human Resources
Electronics City, Hosur Road
Bangalore, 560 100
India
Wipro Ltd.:
Contact:
Pratik Kumar - Executive Vice President, Human Resources
Address:
Wipro Limited, Department of Human Resources
Doddakannelli
Sarjapur Road
Bangalore, 560 035
India
Further, emails were sent out and calls were made to the media contacts of each company requesting the contact information (email addresses in particular) of any relevant HR personnel and/or any individuals that may be able to provide us with the requested information. From the information gathered in this exercise, various Human Resources staff members from Wipro, HCL Technologies and TCS received the appeal to provide the requested information via email on the 11th of February.
We have not yet received any replies to either the email or post requests for information.
Letter of Survey Request
 Letter of Survey Request.pdf
—
PDF document,
44 kB (45193 bytes)
Letter of Survey Request.pdf
—
PDF document,
44 kB (45193 bytes)
Income Bracket Form
 Income Bracket Form.pdf
—
PDF document,
19 kB (19869 bytes)
Income Bracket Form.pdf
—
PDF document,
19 kB (19869 bytes)
Document Actions





